Learn About Deploying and Configuring Oracle Essbase to Use an Oracle Autonomous Database
If you're considering moving Oracle Essbase instances from on-premises or Oracle Analytics Cloud – Essbase to Essbase on Oracle Cloud Infrastructure, then deploy Essbase using the Oracle Cloud Marketplace listing and migrate your data. Essbase delivers instant value and greater productivity for your business users, analysts, modelers, and decision-makers, across all lines of business within your organization.
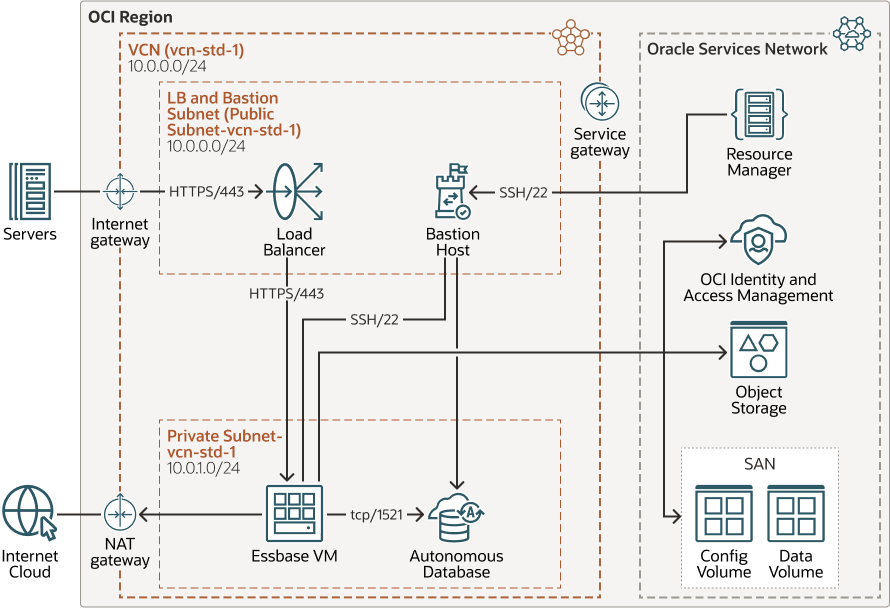
Architecture
Use this Essbase deployment architecture as an example, and to determine the appropriate security and access requirements for your organization.
The architecture consists of a virtual cloud network, load balancer, application, and Oracle Autonomous Database that are required to run Essbase on Oracle Cloud Infrastructure (OCI). These hosts are placed in separate virtual machines. You can deploy a few instances in a public subnet and a few instances in a private subnet. This type of deployment is useful when the deployment includes internet-facing and non-internet facing endpoints. For example, if you place the bastion host in a public subnet, then the bastion host is assigned a public IP address, and you can access it over the internet.
You can set up a public load balancer on the internet-facing application instances, instead of placing the application servers that serve external traffic in a public subnet. The load balancer instances that are in the public subnet receive requests and forward them to the Essbase server. You can access the instances in private subnets over port 22 through the bastion host. To do this, enable ssh-agent forwarding, which allows you to connect to the bastion host, and then access the next server by forwarding the credentials from your computer. You can also access the instances in the private subnet by using dynamic SSH tunneling.
Instances in the private subnet may optionally require outbound connection to the Internet to download application patches and for external integrations. For this purpose, use a Network Address Translation (NAT) gateway in your VCN. With a NAT gateway, the hosts in the private subnet can initiate connections to the Internet and receive responses, but won’t receive inbound connections initiated from the Internet.
You can integrate Essbase with OCI Identity and Access Management to set up security and access. Your Service Administrator can then log in to the Essbase web interface to provision other users.
The automatic and on-demand database backups to Oracle Cloud Infrastructure Object Storage can be configured using the OCI Console. The backup of application can be configured by using the policy-based backup feature of Oracle Cloud Infrastructure Block Volumes.
Description of the illustration essbase-deployment-cloud.png
essbase-deployment-cloud-oracle.zip
- Bastion Host: You can use this host as a jump server to access the instances in the private subnet.
- Load Balancer: The Oracle Cloud Infrastructure Load Balancing instance redirects the HTTP(S) traffic to the Essbase VM.
- Essbase Compute VM: Contains instances of the Essbase application server.
- Autonomous Database: Contains an Oracle Autonomous Database instance, which is used by the Essbase instance for its repository schemas.
| Component | Sample Name | CIDR | Details |
|---|---|---|---|
| VCN | vcn-std-1 | 10.0.0.0/16 | VCN where all Essbase stack components are deployed. |
| Subnet (Public) | Public Subnet-vcn-std-1 | 10.0.0.0/24 | Both load balancer and bastion hosts are deployed in this subnet which has a public IP address. |
| Subnet (Private) | Private Subnet-vcn-std-1 | 10.0.1.0/24 | Subnet for the Oracle Autonomous Database database and Essbase VM. |
About Required Services and Roles
This solution requires the following products and services:
- Oracle Cloud Infrastructure (OCI)
- Oracle Essbase
- OCI Identity and Access Management
- Oracle Cloud Infrastructure Resource Manager
- Oracle Cloud Infrastructure Load Balancing
- Oracle Autonomous Database
These are the roles needed for each service.
| Role | Required to... |
|---|---|
| Oracle Cloud Infrastructure administrator | Create the following:
|
| Essbase administrator | Set up the following:
|