Create an Oracle Cloud Infrastructure API Gateway
You'll need to set up an API Gateway and configure it with a dynamic group and a policy.
Create an Oracle Cloud Infrastructure API Gateway
Create an API gateway to handle your REST API traffic.
You can create the gateway within Oracle Cloud Infrastructure. Note that you cannot deploy the API deployment file (API Gateway defines its APIs using a JSON file called API Deployments) until you’ve deployed the function, because you will need the function's OCID. This is only available after the function has been deployed and remains the same for redeployments.
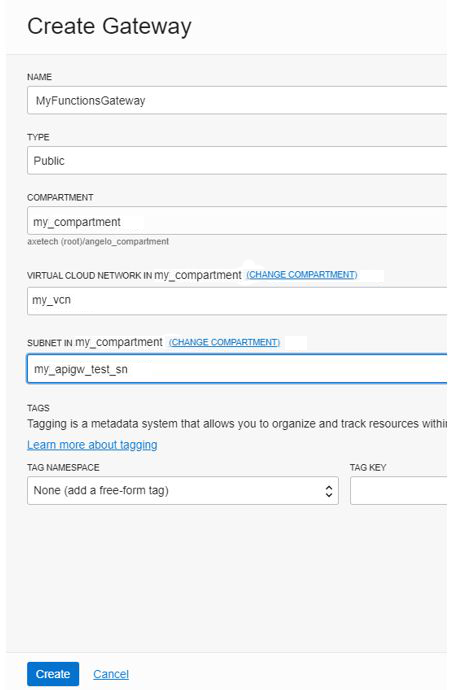
When creating the API gateway in the cloud console, ensure it is created as a public gateway and associated with a VCN. For example:
Create a Dynamic Group
You need a dynamic group for API Gateway.
Dynamic groups allow you to group Oracle Cloud Infrastructure computer instances as "principal" actors (similar to user groups). You can then create policies to permit instances to make API calls against Oracle Cloud Infrastructure services. When you create a dynamic group, rather than adding members explicitly to the group, you instead define a set of matching rules to define the group members. For example, a rule could specify that all instances in a particular compartment are members of the dynamic group. The members can change dynamically as instances are launched and terminated in that compartment.
Create a Policy in Your Compartment
A dynamic group has no permissions until you write at least one policy that gives that dynamic group permission to either the tenancy or a compartment.
A Policy is an Oracle Cloud Infrastructure Identity and Access Management (IAM) document that specifies who has what type of access to your resources. When writing a policy, you can specify the dynamic group by using either the unique name or the dynamic group's OCID. However, even if you specify the dynamic group name in the policy, IAM internally uses the OCID to determine the dynamic group.