Integrate Next Generation Firewall (NGFW) Natively on Oracle Cloud
Preventing unauthenticated users from crashing devices remotely or from executing code is exactly what Fortinet's next generation firewall (NGFW) is designed to do.
Fortinet's security fabric spans both data centers and clouds to provide companies with a consolidated view of their security posture and to provide a single console for policy management, governance reporting, and event monitoring. The single console view spans physical, virtual, and cloud infrastructures including private, public, and hybrid clouds. This security fabric has recently been natively integrated with Oracle Cloud Infrastructure (OCI), providing companies with scalable performance, advanced security orchestration, and unified threat protection for the workloads they're running on OCI.
FortiGate NGFW provides companies with greater application control, web filtering, advanced threat detection, antivirus, intrusion prevention, virus outbreak protection service, content disarm and reconstruction, and anti-botnet security. You can find and deploy different configurations of the virtual FortiGate NGFW appliance from the Oracle Cloud Marketplace.
FortiGate deployments on OCI provide:
- Protection of north-south network traffic, while controlling, inspecting, and securing traffic outside of the OCI virtual cloud networks (VCNs). This protection covers traffic between an on-premise network to the VCN, as well as traffic flowing to and from the Internet.
- Protection of east-west network traffic, while controlling, inspecting, and securing traffic between OCI virtual cloud networks (VCNs).
Fortigate provides deep packet inspection (DPI), or packet sniffing, to examine the content of data packets on the network. Normal packet inspection examines only the packet's header. DPI involves examining not only the packet's header, but also the data the packet is carrying. With its DPI technology, FortiGate acts as a checkpoint for north-south or east-east traffic to verify whether the packets are safe to pass.
Architecture
You can deploy the FortiGate next generation firewall (NGFW) in an active-active configuration or in an active-passive configuration.
Either deployment option offers high-availability protection. The key considerations when selecting a deployment option are scalability, resiliency, and high availability. To scale vertically, choose the active-passive configuration, adding more OCPUs and RAM when needed. To scale horizontally, choose the active-active configuration, adding additional instances as needed.
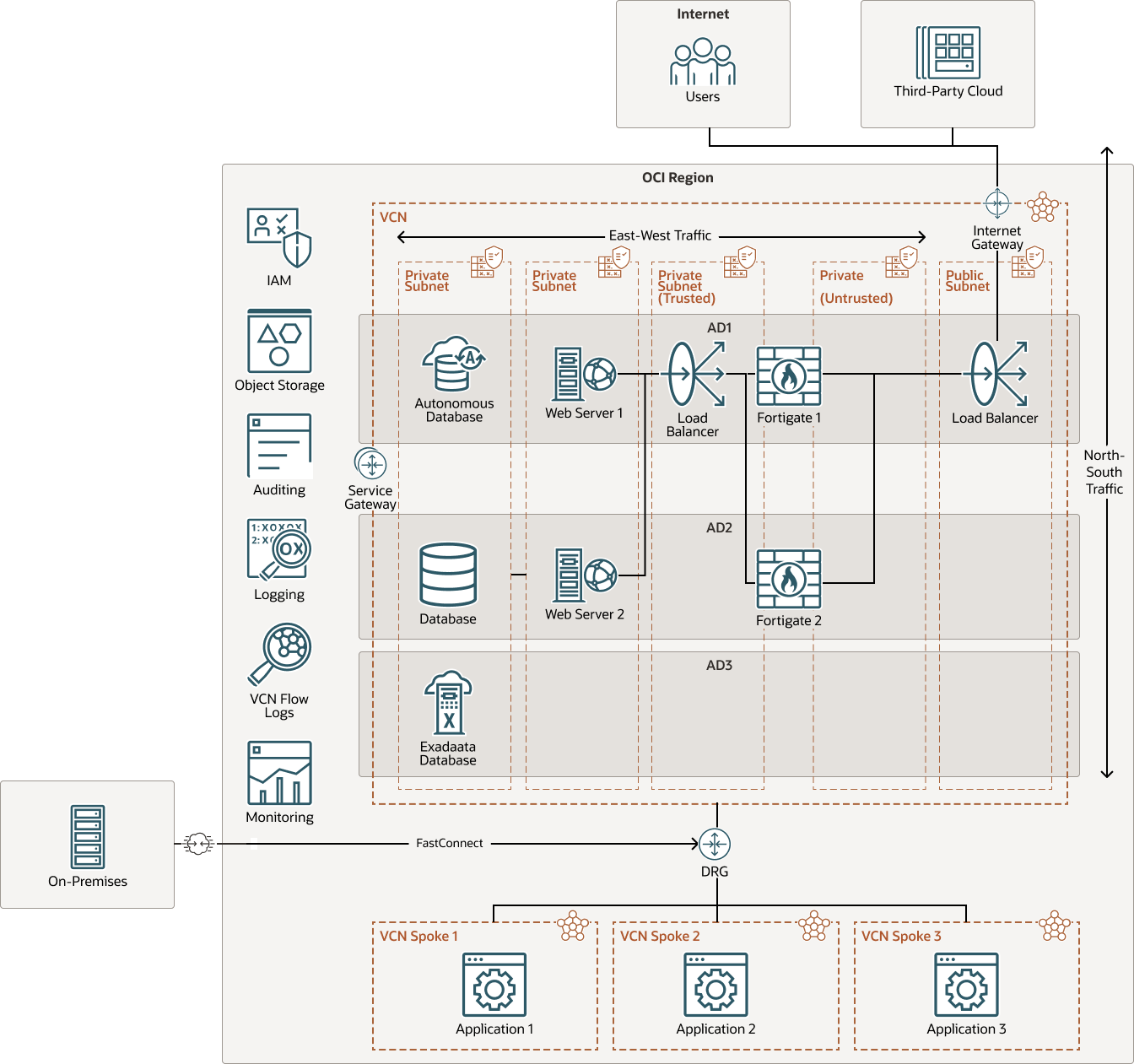
In a typical deployment architecture, the FortiGate instances are deployed in a "load balancer sandwich" architecture. For an active-active configuration, they are "sandwiched" between load balancers with two subnets. For an active-passive architecture, four ports are recommended: public (untrust), private (trust), heartbeat, and management ports. A hub virtual cloud network (VCN) contains the load balancer with a pair of FortiGate instances. The FortiGate instances straddle two subnets. A private (trust) and a public (untrust) subnet validate ingress traffic to the private network. The FortiGate instances are assigned two ports, one in a untrusted public subnet and one in a trusted private subnet. This arrangement provides a centralized network traffic analyzer in the hub of the network infrastructure. For high availability, you can deploy the FortiGate instances in different availability domains or fault domains, depending on the chosen region. You can also configure multiple FortiGate clusters to allow for multiregion configurations.
The following diagram illustrates a reference architecture in a single region with multiple availability domains.
fortinet-ngfw-oci-arch-oracle.zip
Multiple use cases are depicted from the diagram above:
- Inbound traffic (north-south) from the internet: Inbound traffic from the internet enters the VCN through an internet gateway. After load balancing, the traffic passes to a pair of FortiGate virtual instances. The FortiGate instances inspect the traffic, and if the traffic is safe and non-malicious, it passes the traffic to the application (north-south).
- Inbound traffic (north-south) from on-premises: On-premises network traffic connects by using Oracle Cloud Infrastructure FastConnect or an IPSec tunnel that follows the same path but enters the OCI region through a dynamic routing gateway (DRG). Then traffic passes to the load balancer, continues to the FortiGate instance, and then to the application.
- Internal traffic (east-west): After traffic leaves the spoke VCNs, it passes through the DRG and enters the load balancer in the hub VCN. The FortiGate instance validates the traffic before allowing it to move forward internally and determines whether it passes to a tiered application with a web front end, or to an application in another spoke VCN. FortiGate provides traffic validation from subnet to subnet in this use case.
FortiGate works in conjunction with OCI native security services, such as security lists and network security groups (NSGs). FortiGate provides traffic filtering by using firewall policies and inspects the traffic for known and unknown attacks much like IPS, antivirus, and web filtering technologies. Security lists and network security groups (NSGs) allow or stop traffic based on ports and protocols. This additional layer of security provides defense-in-depth to OCI architecture.
The architecture has the following components:
- Tenancy
A tenancy is a secure and isolated partition that Oracle sets up within Oracle Cloud when you sign up for Oracle Cloud Infrastructure. You can create, organize, and administer your resources in Oracle Cloud within your tenancy. A tenancy is synonymous with a company or organization. Usually, a company will have a single tenancy and reflect its organizational structure within that tenancy. A single tenancy is usually associated with a single subscription, and a single subscription usually only has one tenancy.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Compartment
Compartments are cross-region logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize your resources in Oracle Cloud, control access to the resources, and set usage quotas. To control access to the resources in a given compartment, you define policies that specify who can access the resources and what actions they can perform.
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can seamlessly scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- Identity and Access Management (IAM)
Oracle Cloud Infrastructure Identity and Access Management (IAM) is the access control plane for Oracle Cloud Infrastructure (OCI) and Oracle Cloud Applications. The IAM API and the user interface enable you to manage identity domains and the resources within the identity domain. Each OCI IAM identity domain represents a standalone identity and access management solution or a different user population.
- Audit
The Oracle Cloud Infrastructure Audit service automatically records calls to all supported Oracle Cloud Infrastructure public application programming interface (API) endpoints as log events. Currently, all services support logging by Oracle Cloud Infrastructure Audit.
- LoggingLogging is a highly scalable and fully managed service that provides access to the following types of logs from your resources in the cloud:
- Audit logs: Logs related to events emitted by the Audit service.
- Service logs: Logs emitted by individual services such as API Gateway, Events, Functions, Load Balancing, Object Storage, and VCN flow logs.
- Custom logs: Logs that contain diagnostic information from custom applications, other cloud providers, or an on-premises environment.
- Monitoring
Oracle Cloud Infrastructure Monitoring service actively and passively monitors your cloud resources using metrics to monitor resources and alarms to notify you when these metrics meet alarm-specified triggers.
Get Featured in Built and Deployed
Want to show off what you built on Oracle Cloud Infrastructure? Care to share your lessons learned, best practices, and reference architectures with our global community of cloud architects? Let us help you get started.
- Download the template (PPTX)
Illustrate your own reference architecture by dragging and dropping the icons into the sample wireframe.
- Watch the architecture tutorial
Get step by step instructions on how to create a reference architecture.
- Submit your diagram
Send us an email with your diagram. Our cloud architects will review your diagram and contact you to discuss your architecture.
Explore More
Learn more about the features of this architecture and about related architectures.