About Governance
Governance is a set of well-planned rules and processes that you create, monitor, and amend as necessary. It enables organizations to control costs, improve efficiency, and eliminate security risks.
As organizations move to the cloud and support multi-cloud environments, the network is no longer the perimeter. Organizations need a comprehensive plan to onboard and implement security controls including protective and detective controls. The governance model provides a structure to design and improve cloud security, ensure compliance, and reduce costs.
This solution playbook helps you get started with the foundational concepts, the thought process, and the kind of decisions you must make to design a governance model specific to your organizational goals. It uses specific examples to explain how to set up your governance model. Your organization's goals will drive the design of your governance model.
Governance Model
Using a governance model enables organizations to define a structured process for enforcing security and compliance that can be mirrored, modified, or changed based on your organizational requirements.
Creating an effective governance model includes decisions around the provisioning, administration, stewardship, and offboarding of cloud resources. You can use a manual process to configure the workflow. As the governance model matures, you can configure automated workflows and infrastructure-as-code Terraform stack to deploy the governance model.
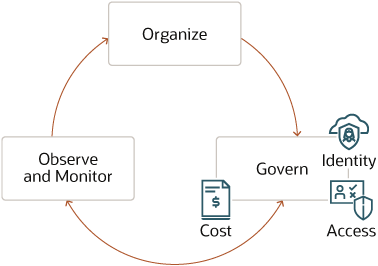
Description of the illustration oci-governance-model.png
The process to implement a governance model is cyclic and iterative. You begin with organizing resources followed by implementing governance that includes identity, access, and cost governance. Finally, you set up processes to observe and monitor security controls. As you detect issues with the model, you feed the data back into the model to improve it.
Organize
You organize your resources and workloads to set up the foundation of an effective governance model.
Govern
You govern your resources and workloads by managing who gets access to which resources. You can manage access to resources using an identity and access provisioning system.
Observe and Monitor
You continuously observe and monitor your resources to ensure the governance model is working to meet your organizational goals. You will require certain essential services such as Cloud Guard, and OCI Logging and Audit services to observe and detect any issues that need to be fixed.
Establishing a governance model provides your organization with a starting point and helps identify improvements needed. It also helps identify the consequences and the risks that will be associated with the model. You apply the governance model at various stages of your Oracle Cloud Infrastructure (OCI) governance implementation.
To enforce cloud governance, security architects must do the following:
- Define and enforce access to resources such as compartments
- Define OCI Identity and Access Management (IAM) policies and tagging
- Observe, monitor, and detect issues using services such as Cloud Guard, OCI Logging, and Log Analytics
- Manage costs by defining service limits, budgets, and usage quotas
- Monitor performance to control costs and prevent costs from going over budget
- Use the Audit service to ensure compliance to defined governance policies
Governance Model Values
Learn about the core values and benefits of an effective governance model. Apply these values as best practices to optimize the usage of OCI resources such as performance monitoring, visibility, cost forecasting, security, and compliance to help your organization save time and money.
Better Management
Set distinct boundaries between teams and the resources they own. Existing models that used centralized governance models experienced reduced agility which worked against the interests of cloud computing goals. With a combination of resource organization and access control, you can achieve both agility and flexibility with governance.
Cloud Visibility
In order to validate prevention controls and act on probable failures, you must first detect them. Cloud visibility provides the ability to monitor and proactively react to activities on the cloud. That means you can identify security threats, inefficient resource utilization, or malicious activities on the cloud. The following are the benefits of cloud visibility:
-
Performance Tracking
Enable autoscaling to dynamically scale resource usage. Track the performance of your resources to proactively identify and act on detected issues such as underutilized resources or autoscaling failures.
-
Security
Identify spot security lapses and take corrective action proactively.
-
Manage Costs
Being unaware of unused capacity may cost your organization a significant amount of money over time. Discover underutilized resources to reduce wastage in your cloud deployment, and enable your organization to reduce costs. Adjust resources to enhance organizational efficiency and scale capacity only when the need arises.
Predictable Cost
Plan your expenses to ensure success in both on-premises and cloud deployments. Manage your costs through estimation and planning by setting up budgets to track actual usage against the plan. Create budgets to get notified when the cost is nearing your usage quota and ensure that costs don't exceed an approved budget. Here are a few commonly used patterns to enforce budget constraints:
- Associate a budget with an organizational unit to receive automatic cost and usage report notifications when usage nears the approved budget.
- Perform forecasting and budget planning while monitoring your spend on the dashboard.
Better Security
While educating cloud users in cloud security is a key step in reducing the number of security breaches, 95 percent of all cloud breaches can be traced to human errors. By reducing the reliance on humans for ensuring cloud security, cloud governance significantly improves your security posture against online threats.
New and emerging cyberthreats require businesses to rethink their approach to cloud security, data protection, consumer privacy protection, and user authentication. Cloud governance policies for authenticating or monitoring access can configure and manage the security protocols and tailor them to your business needs.
Compliance Implementation
Cloud governance plays a critical role in enforcing regional compliance requirements. A well-designed third-party cloud governance solution can keep all your sensitive corporate data private and also comply to regional compliance laws such as HIPAA or FedRAMP. It also supports data protection laws such as CCPA in California, or GDPR in international markets such as the EU which impose strict customer data privacy and security compliance requirements on businesses.