Extend Active Directory integration in Hybrid Cloud
In Microsoft Windows oriented hybrid cloud and multicloud environments, where some applications are dependent on directory services, extending and integrating Microsoft Active Directory (AD) with Oracle Cloud Infrastructure (OCI) is important for the performance and security.
AD is a Microsoft service often implemented as a framework for IT environments. AD stores information about objects on the network and makes this information easy for administrators and users to find and use (such as accounts, privileges, security policies, DNS). AD uses a structured data store as the basis for a logical, hierarchical organization of directory information.
Note:
This reference architecture builds upon AD knowledge. If AD is used in your organization, contact the system administrator for proper implementation on OCI.Architecture
This reference architecture describes how you can extend on-premises AD integration with OCI in a hybrid cloud environment.
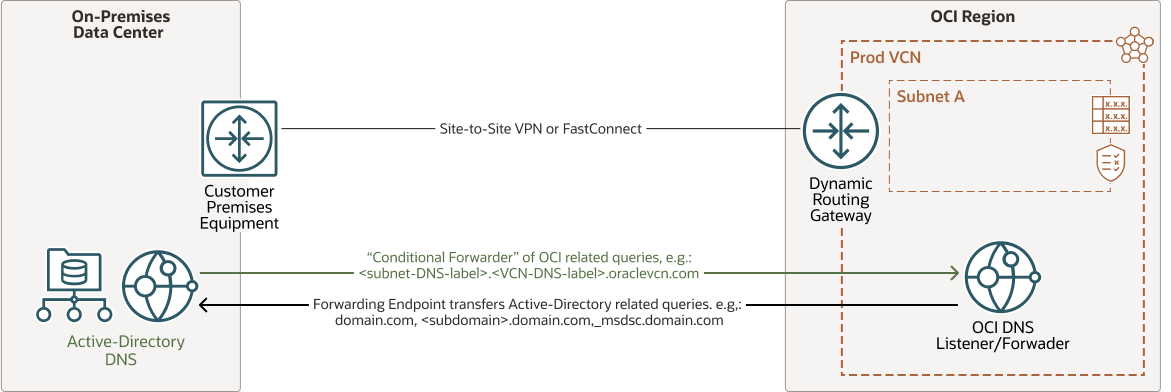
Integrating OCI and AD - DNS
AD relies on its DNS feature to provide services within a domain. DNS integration is a crucial part in extending AD environments on OCI. In order for new cloud based servers and services to reliably leverage certain AD features they must first be able to resolve DNS records managed by the domain and, in some cases, even domain-joined.
- DNS Forwarding: The process by which a particular set of DNS queries are
forwarded to a designated server for resolution according to the DNS domain name in
the query rather than being handled by the initial server that was contacted by the
client.
This process improves network performance and resilience. It provides a way to resolve name queries both inside and outside the network by passing on namespaces or resource records that aren't contained in the zone of a local DNS server to a remote DNS server for resolution.
When a DNS server is configured to use a forwarder, if it can't resolve a name query by using its local primary zone, secondary zone, or cache, it forwards the request to the designated forwarder.
- OCI DNS - VCN Resolver: Enables instances to resolve DNS hostnames (which you can assign) of other instances in the same VCN.
- OCI DNS - Endpoint: An endpoint is an assigned IP for the VCN resolver
to either forward or listen to (receive) DNS queries. A forwarding endpoint will
allow creation of rules to forward relevant queries to be resolved by the AD DNS,
while a listener will accept and resolve OCI related queries forwarded from AD DNS.
It is recommended that forwarding rules are created for all AD domains, including subdomains and SRV folders such as "
_msdsc". - Active Directory - DNS conditional forwarders: A set of DNS forwarding rules contained within the AD DNS server. For OCI integration, it is recommended that forwarding rules are created for all OCI-based domains, for example, the VCN DNS name, for private name resolution over FastConnect/VPN.
The following diagram illustrates this reference architecture.
integrate-oci-msft-ad_dns_base-oracle.zip
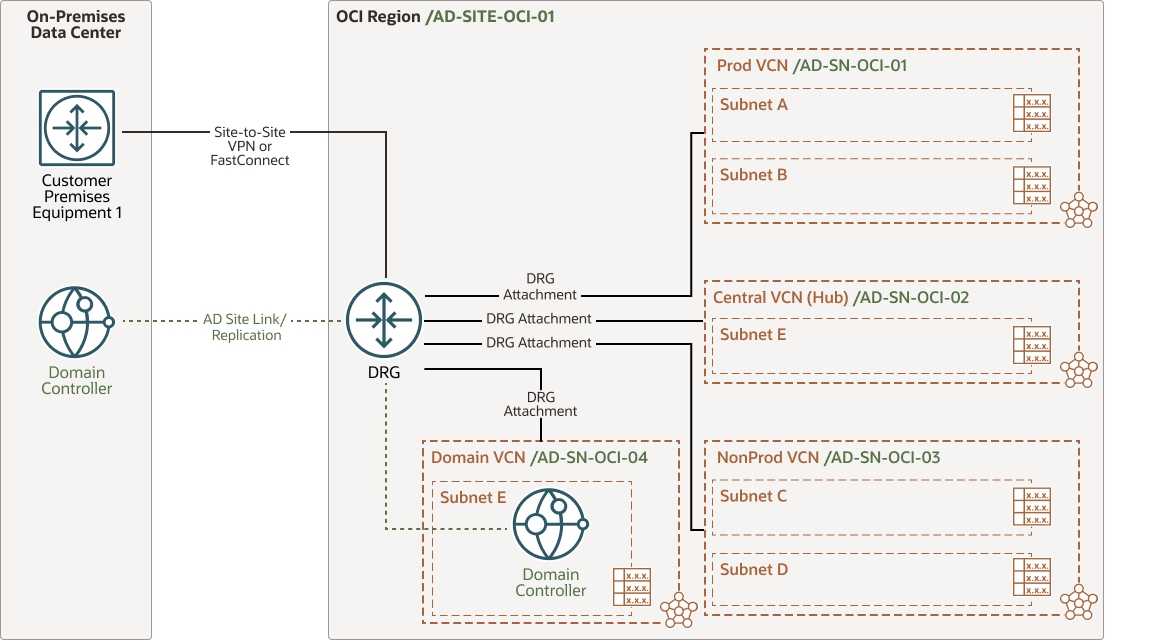
Integrating OCI and AD - Domain Extension
AD uses site topology to group resources into locations. A directory service site topology is a logical representation of your physical network that helps efficiently route client queries and AD replication traffic. Designing a site topology for AD Domain Services involves planning for domain controller placement and designing sites, subnets, site links, and site link bridges to ensure efficient query routing and traffic replication.
Site topology significantly affects the performance of your network and the ability of your users to access network resources. Applications and users leveraging AD services require access to a domain controller. To ensure consistent service, most organizations place regional domain controllers for all regional domains that are represented in a given location.
For maximum performance and reliability, it is recommended to extend AD to include OCI locations by creating relevant site representation for the subscribed regions, subnet representation for the deployed VCNs and implementation of OCI-based domain controllers.
- Domain Controller: The centerpiece of the Microsoft AD service. Responsible for allowing network access to domain resources. It authenticates users, stores user account and host information, and enforces policies for a domain. Domain controllers may be writable or read-only (RODC), but at least one writable domain controller is required per deployment.
- Site: AD objects that represent one or more TCP/IP subnets with highly reliable and fast network connections. Site information allows administrators to configure AD access and replication to optimize usage of the physical network. Site objects are associated with a set of subnets, and each domain controller in a forest is associated with an AD site according to its IP address. Sites can host domain controllers from more than one domain, and a domain can be represented in more than one site.
- Site Links: AD objects that represent logical paths that the Knowledge Consistency Checker (KCC) uses to establish a connection for AD replication. A site link object represents a set of sites that can communicate at uniform cost through a specified intersite transport.
- AD Subnet: A logical representation of a segment of a TCP/IP network to which a set of IP addresses are assigned. Subnets group computers in a way that identifies their physical proximity on the network. Subnet objects in AD identify the network addresses that are used to map computers to sites.
- Schema: A set of rules that defines the classes of objects and attributes contained in the directory, the constraints and limits on instances of these objects, and the format of their names.
- Global Catalog: Contains information about every object in the directory. This allows users and administrators to find directory information regardless of which domain in the directory actually contains the data.
The following diagram illustrates this reference architecture.
integrate-oci-msft-ad-arch-oracle.zip
The architecture has the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Site-to-Site VPN
Site-to-Site VPN provides IPSec VPN connectivity between your on-premises network and VCNs in Oracle Cloud Infrastructure. The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
Recommendations
- Domain Controllers
Consider deploying two or more domain controllers for high availability. If deploying more than one domain controller, consider deployment in separate availability domains.
- Sites
If multiple domain controllers are deployed in multiple availability domains, it is possible to treat each availability domain as its own AD site while configuring priority site links for internal OCI replication and availability.
- DNS
Once at least one domain controller is deployed on OCI, it is recommended to edit the DNS forwarding rules to resolve against the local OCI domain controller.
Considerations
When implementing this reference architecture, consider the following option.
- DNS
All AD domains should be forwarded, including subdomains and SRV folders such as
_msdsc. In some cases, further custom domains may exist (for example, if an internal domain collides with a public domain). It is recommended to export a list of all rules and match those on OCI with a redirect to the AD DNS.Routing as well as DNS forwarding is VCN-wide and is not dependent on domain-joining.