Migrate Mainframe Applications to Oracle Cloud Infrastructure (OCI)
Mainframe computers remain part of the primary computing infrastructure for some of the largest organizations around the world.
Companies started using mainframes for running critical bulk data processing applications, such as census tabulation, enterprise resource planning, industry and consumer statistics, and large-scale transaction processing. Organizations from banking, to scientific research and vaccine development all use mainframes. While mainframes offer great reliability and availability, there are also some limitations. For example, it is very hard to keep the mainframe computers up to date with the latest security patches, and to keep pace with modern technologies and the deployment frequencies required to run new generations of applications.
Oracle Cloud Infrastructure (OCI) can help you move your mainframe applications to the cloud and to realize the benefits of cloud computing, such as simplified infrastructure management and scaling, automated security patching, and automated approaches to deploying and updating the mainframe applications in an agile way. OCI provides the tools and resources needed to migrate your mainframe applications to the cloud and to re-platform or re-factor them as required for your businesses needs.
Architecture
Migrate your mainframe applications to Oracle Cloud Infrastructure (OCI) by using high availability (HA) and disaster recovery (DR) architectures.
Both architectures provide the tools and resources you need to migrate your mainframe applications to the cloud so that your customer and administrator users can use the mainframe application for business, administration, and operations purposes.
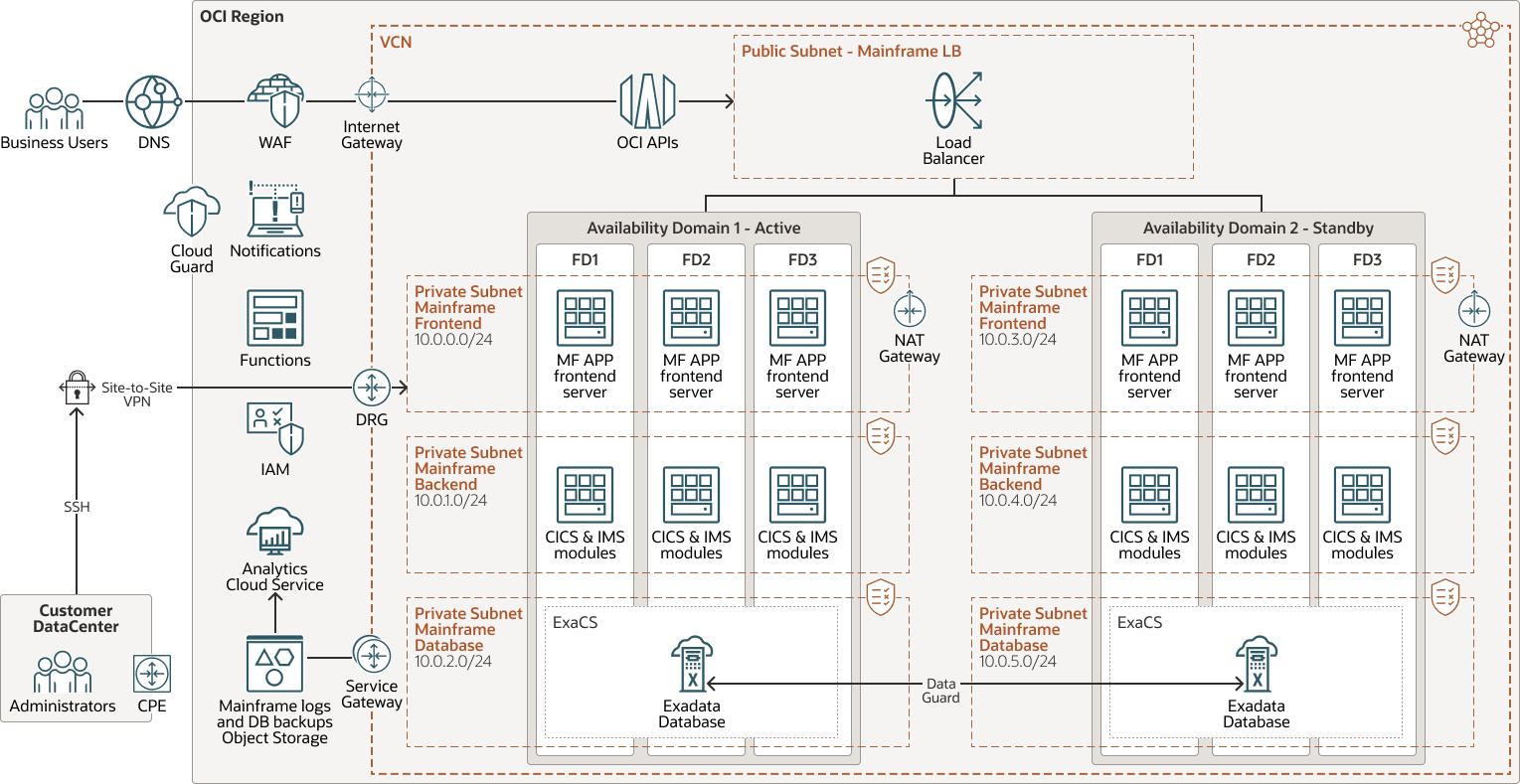
The following diagram illustrates the high availability (HA) architecture:
The high availability architecture deploys the application in multiple fault domains in the same region. This ensures that the mainframe application is always available even if one of the fault domains is unavailable for some reason. Organizations can deploy a standby instance in the second availability domain of the same region to increase resilience.
The architecture diagram illustrates multiple user access flows. Business users access the application by using endpoints exposed through the OCI API Gateway. These endpoints are protected by Oracle Cloud Infrastructure Web Application Firewall which ensures that the front-end security is applied to the mainframe application by default. The user request is forwarded to the load balancer, which forwards the request to the multitier application. Each of the three tiers of the application is hosted in a different subnet to make sure that the correct security port is opened as required by the application. The data stored in databases is pulled from a separate subnet to ensure proper security.
Administration users, responsible for operating the mainframe application on OCI, access the application servers by using secure shell (SSH) and site-to-site virtual private network (VPN) or Oracle Cloud Infrastructure FastConnect. This creates a secure tunnel that connects the customer premises equipment (CPE) in the customer data center with the dynamic routing gateway (DRG) on OCI. Using this path, administrators access compute instances on OCI from the data center machines. This access is required to make sure that all operations tasks such as patching, application upgrade, OS security upgrades, and other tasks are done easily and on time.
OCI Automated Refactoring helps convert the complete legacy application stack and its data layer into a modern, Java-based application while preserving functional equivalence. Oracle’s ZFS and Oracle Cloud Infrastructure Block Volumes provide storage, if needed, and connect with on-premises storage systems by using the appropriate networking. All code is migrated to Java by using automated assessment and conversion. The code is then hosted on an OCI cluster of compute instances based either on virtual machine (VM) or bare metal (BM) architectures.
Oracle Cloud Infrastructure DevOps helps ensure all the components are deployed in an agile way. All of the components are deployed by using Terraform and maintained by using Ansible. This showcases how you can leverage automation on OCI and follow the Infrastructure-as-Code (IaC) approach to make the mainframe application more agile and easier to maintain.
The following diagram illustrates disaster recovery (DR) architecture:
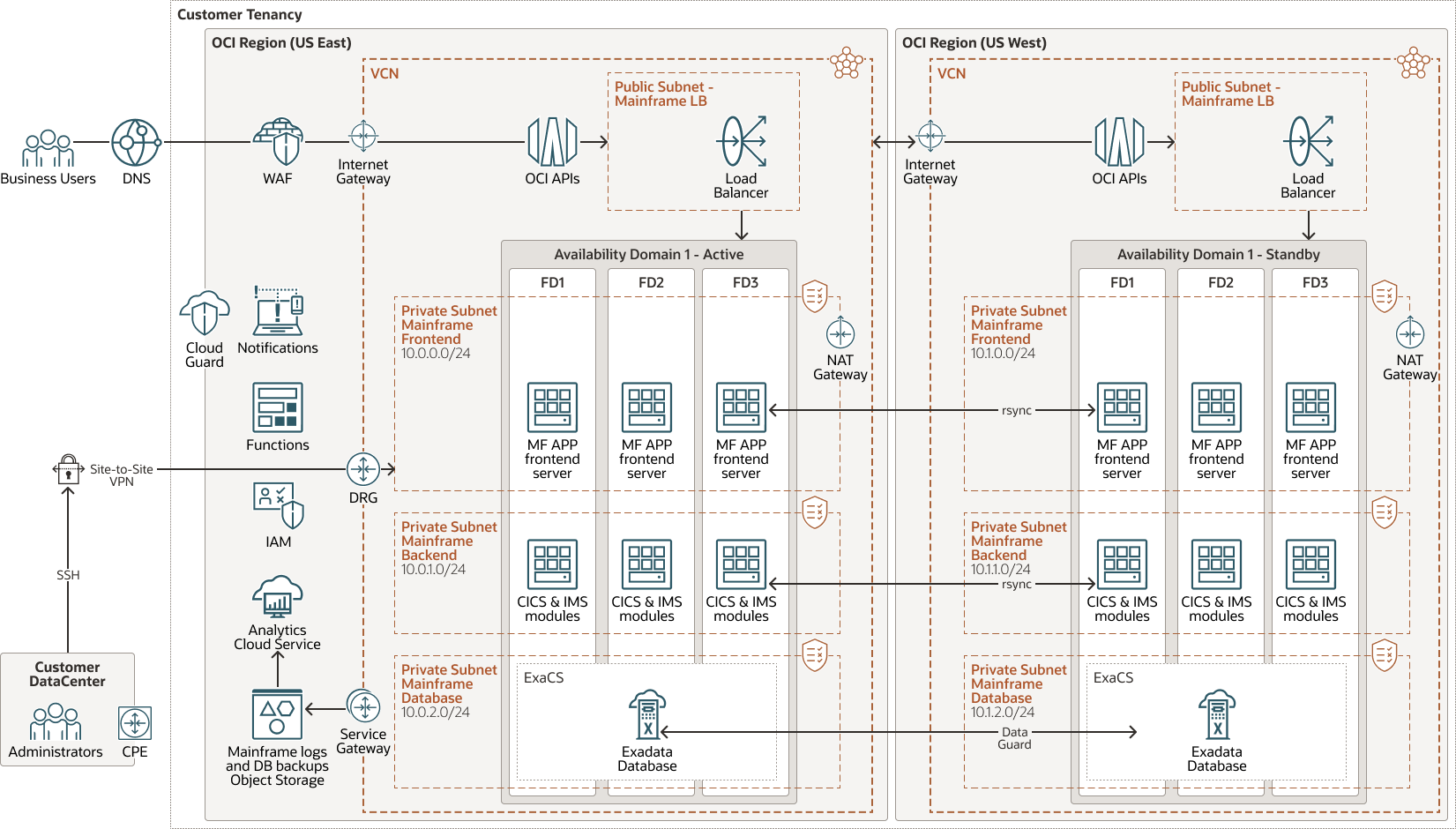
Description of the illustration mainframe-app-multiregion.png
mainframe-app-multiregion-oracle.zip
The disaster recovery architecture deploys the application in multiple OCI regions. This ensures that the mainframe application is available if one of the regions becomes unavailable for some reason such as a natural disaster. Optionally placing resources in multiple fault domains helps ensure that the architecture is also safe in the event of rack-level hardware failure in the cloud data center, and that the mainframe applications can run continuously for many years with zero-downtime.
The architecture has the following components:
- Tenancy
A tenancy is a secure and isolated partition that Oracle sets up within Oracle Cloud when you sign up for Oracle Cloud Infrastructure. You can create, organize, and administer your resources in Oracle Cloud within your tenancy. A tenancy is synonymous with a company or organization. Usually, a company will have a single tenancy and reflect its organizational structure within that tenancy. A single tenancy is usually associated with a single subscription, and a single subscription usually only has one tenancy.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Compartment
Compartments are cross-region logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize your resources in Oracle Cloud, control access to the resources, and set usage quotas. To control access to the resources in a given compartment, you define policies that specify who can access the resources and what actions they can perform.
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Site-to-Site VPN
Site-to-Site VPN provides IPSec VPN connectivity between your on-premises network and VCNs in Oracle Cloud Infrastructure. The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- Network address translation (NAT) gateway
A NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Web Application Firewall (WAF)
Oracle Cloud Infrastructure Web Application Firewall (WAF) is a payment card industry (PCI) compliant, regional-based and edge enforcement service that is attached to an enforcement point, such as a load balancer or a web application domain name. WAF protects applications from malicious and unwanted internet traffic. WAF can protect any internet facing endpoint, providing consistent rule enforcement across a customer's applications.
- Compute
The Oracle Cloud Infrastructure Compute service enables you to provision and manage compute hosts in the cloud. You can launch compute instances with shapes that meet your resource requirements for CPU, memory, network bandwidth, and storage. After creating a compute instance, you can access it securely, restart it, attach and detach volumes, and terminate it when you no longer need it.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can seamlessly scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- Notifications
The Oracle Cloud Infrastructure Notifications service broadcasts messages to distributed components through a publish-subscribe pattern, delivering secure, highly reliable, low latency, and durable messages for applications hosted on Oracle Cloud Infrastructure.
- Functions
Oracle Cloud Infrastructure Functions is a fully managed, multitenant, highly scalable, on-demand, Functions-as-a-Service (FaaS) platform. It is powered by the Fn Project open source engine. Functions enable you to deploy your code, and either call it directly or trigger it in response to events. Oracle Functions uses Docker containers hosted in Oracle Cloud Infrastructure Registry.
- LoggingLogging is a highly scalable and fully managed service that provides access to the following types of logs from your resources in the cloud:
- Audit logs: Logs related to events emitted by the Audit service.
- Service logs: Logs emitted by individual services such as API Gateway, Events, Functions, Load Balancing, Object Storage, and VCN flow logs.
- Custom logs: Logs that contain diagnostic information from custom applications, other cloud providers, or an on-premises environment.
- Exadata Database Service
Oracle Exadata Database Service enables you to leverage the power of Exadata in the cloud. You can provision flexible X8M and X9M systems that allow you to add database compute servers and storage servers to your system as your needs grow. X8M and X9M systems offer RDMA over Converged Ethernet (RoCE) networking for high bandwidth and low latency, persistent memory (PMEM) modules, and intelligent Exadata software. You can provision X8M and X9M systems by using a shape that's equivalent to a quarter-rack X8 and X9M system, and then add database and storage servers at any time after provisioning.
Recommendations
Your requirements might differ from the architecture described here.
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
- Cloud Guard
Clone and customize the default recipes provided by Oracle to create custom detector and responder recipes. These recipes enable you to specify what type of security violations generate a warning and what actions are allowed to be performed on them. For example, you might want to detect Object Storage buckets that have visibility set to public.
Apply Cloud Guard at the tenancy level to cover the broadest scope and to reduce the administrative burden of maintaining multiple configurations.
You can also use the Managed List feature to apply certain configurations to detectors.
- Disaster Recovery (DR)
A standby DR instance in a different OCI region is recommended for enterprise applications. The DR strategy must be consistent across the 3-tiers in order to meet SLA and data durability requirements. The DR Oracle Exadata Database Service on Dedicated Infrastructure is synchronized with production by using Oracle Data Guard. The standby Oracle Exadata Database Service on Dedicated Infrastructure is a transactionally consistent copy of the primary database. Oracle Data Guard automatically synchronizes the databases by transmitting and applying redo data from the primary database to the standby. In the event of a disaster in the primary region, Oracle Data Guard automatically fails over to the standby database in the secondary region. Front-end load balancers are deployed either in a standby mode for network load balancers or with high availability by using Oracle Cloud Infrastructure Load Balancing.
Considerations
When implementing this reference architecture, consider the following options.
- Performance
Oracle Cloud Infrastructure Compute, Oracle Exadata Database Service, and other important services are highly scalable. Consider adjusting the number of compute and storage resources based on the size and requirement of mainframe application.
- Security
Use policies to restrict who can access the Oracle Cloud Infrastructure (OCI) resources. For Oracle Cloud Infrastructure Object Storage, encryption is enabled by default and can’t be turned off. All access to functions deployed in Oracle Cloud Infrastructure Functions is controlled through Oracle Cloud Infrastructure Identity and Access Management (IAM), which allows both function management and function invocation privileges to be assigned to specific users and user groups. It is recommended that you store secrets and sensitive data, such as such as API keys and auth tokens that are used for authorization with OCI services, in Oracle Cloud Infrastructure Vault.
- Availability
Oracle ensures high availability of Oracle Cloud Infrastructure Compute, Oracle Exadata Database Service and other cloud native and fully managed services. For workloads deployed within a single availability domain, you can ensure resilience by distributing the resources across the fault domains as shown in this architecture. If you plan to deploy your workload in a region that has more than one availability domain, you can distribute the resources across multiple availability domains.
- Scalability
You can scale the application servers vertically by changing the shape of the compute instances. A shape with a higher core count provides more memory and network bandwidth. If you need more storage, increase the size of the block volumes attached to the application server. You can scale the databases vertically by enabling more cores for the Oracle Exadata Database Service. You can add OCPUs in multiples of two for a quarter rack. The databases remain available during a scaling operation. If your workload outgrows the available CPUs and storage, you can migrate to a larger rack.