Rehost Mainframe COBOL Workloads to Kubernetes Clusters in Oracle Cloud Using Tuxedo ART
Modernize your mainframe workloads and make them more agile, open, and cost-effective by rehosting to Kubernetes clusters in Oracle Cloud. Take advantage of cutting-edge technologies, such as machine learning and in-memory databases to gain deeper insights into your customers and operations.
Architecture
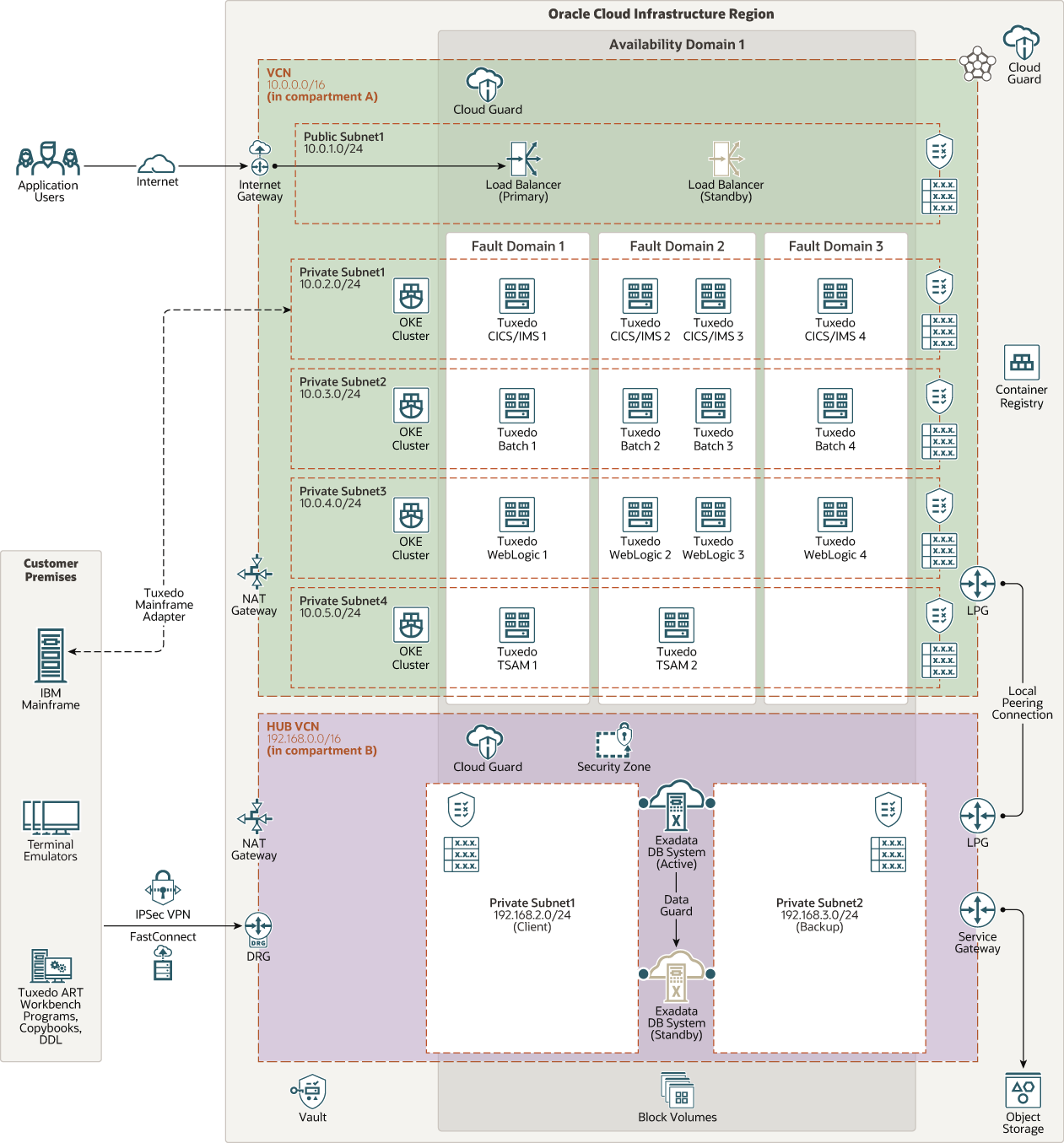
This architecture shows mainframe applications migrated to containers managed by Oracle Cloud Infrastructure Container Engine for Kubernetes (OKE). The data tier consists of an active-standby pair of quarter-rack Exadata DB systems.
The Tuxedo Application Rehosting (ART) Workbench helps you simplify and accelerate mainframe rehosting by automating the migration of code and data. Built on advanced language processing technology used in large-scale migrations, the workbench integrates the tools required to adapt COBOL code, DB2 SQL, and transform job control language (JCL). It also includes data-migration tools, which perform complete analysis of data definitions and access to generate data schemas and logical access modules. These tools create data unload, reload, and validation tools for automated migration of VSAM data sets, flat files, and DB2 tables from the mainframe.
A load balancer provides access from the public internet to your applications. For private connectivity with your on-premises deployment, you can use Oracle Cloud Infrastructure FastConnect or IPSec VPN.
The following diagram illustrates this reference architecture.
The architecture has the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
All the resources in this architecture are deployed in a single region.
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
All the resources in this architecture are deployed in a single availability domain.
- Fault domains
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
To ensure high availability, the middle-tier resources in this architecture are distributed across all the fault domains in the availability domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
The architecture has two VCNs:- One of the VCNs has a public subnet for the load balancer, and two private subnets for the middle tier.
- The other VCN has a single private subnet for the data tier.
This VCN also serves as a hub network, for transit routing of private connections from the on-premises data center to the other VCN.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- IPSec VPN
VPN Connect provides site-to-site IPSec VPN connectivity between your on-premises network and VCNs in Oracle Cloud Infrastructure. The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
This architecture includes a public load balancer.
- Security lists
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Route tables
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Local peering gateway (LPG)
An LPG enables you to peer one VCN with another VCN in the same region. Peering means the VCNs communicate using private IP addresses, without the traffic traversing the internet or routing through your on-premises network.
The two VCNs in this architecture are interconnected privately using LPGs.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
In this architecture, the VCN that's used for the load balancer has an internet gateway.
- NAT gateway
The NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
Both the VCNs in this architecture have a NAT gateway.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
The VCN that's used for the data tier in this architecture has a DRG to enable private connectivity to your on-premises data center using FastConnect or VPN Connect.
- Tuxedo Mainframe Adapter (TMA)
You can use TMA for connectivity between the cloud and the on-premises mainframe. This connectivity is private and uses the transit routing feature of Oracle Cloud Infrastructure. FastConnect or IPSec VPN traffic is routed through the DRG of the data-tier VCN, which serves as the hub for the spoke VCN that’s used for the Tuxedo middle tier.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
The VCN that's used for the data tier in this architecture has a service gateway.
- Block volumes
With block storage volumes, you can create, attach, connect, and move storage volumes, and change volume performance to meet your storage, performance, and application requirements. After you attach and connect a volume to an instance, you can use the volume like a regular hard drive. You can also disconnect a volume and attach it to another instance without losing data.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- Vault
Oracle Cloud Infrastructure Vault enables you to centrally manage the encryption keys that protect your data and the secret credentials that you use to secure access to your resources in the cloud.
- Cloud guard
You can use Oracle Cloud Guard to monitor and maintain the security of your resources in the cloud. Cloud Guard examines your resources for security weakness related to configuration, and monitors operators and users for risky activities. When any security issue or risk is identified, Cloud Guard recommends corrective actions and assists you in taking those actions, based on security recipes that you can define.
- Security zones
Security zones ensure Oracle's security best practices from the start by enforcing policies such as encrypting data and preventing public access to networks for an entire compartment. A security zone is associated with a compartment of the same name and includes security zone policies or a "recipe" that applies to the compartment and its sub-compartments. You can't add or move a standard compartment to a security zone compartment.
In this architecture, the compartment containing the databases is a security zone.
- OKE clusters
Oracle Cloud Infrastructure Container Engine for Kubernetes is a fully managed, scalable, and highly available service that you can use to deploy your containerized applications to the cloud. You specify the compute resources that your applications require, and Container Engine for Kubernetes provisions them on Oracle Cloud Infrastructure in an existing tenancy. Container Engine for Kubernetes uses Kubernetes to automate the deployment, scaling, and management of containerized applications across clusters of hosts.
You can launch the OKE nodes with shapes that meet your resource requirements: CPU, memory, network bandwidth, and storage. The architecture has multiple OKE nodes that host the following components. For high availability, the OKE nodes are distributed across all the fault domains in the availability domain and across two private subnets.-
Four OKE nodes each for Tuxedo CICS/IMS and Tuxedo Batch servers.
Oracle Tuxedo Application Runtime for CICS and Batch runs IBM mainframe applications rehosted to Oracle Tuxedo with no change to business logic. The runtime helps online and batch mainframe applications run unchanged, preserving decades of investment in business logic and data and providing the following features:- CICS programming models and services
- COBOL containers
- 3270 BMS support
- Standard JCL functions and common utilities
- Access to migrated VSAM, DB2
- Flat-file data
- Remote access to mainframe DB2
Oracle Tuxedo Application Runtime for IMS runs IBM mainframe applications rehosted to Oracle Tuxedo with no change to business logic. It provides IMS MPP and BMP environments, and 3270 MFS screen support. It supports IMS components on multiple machines, similar to IMSplex.
-
Two OKE nodes for Oracle Tuxedo System and Application Monitor (TSAM).
Effective management of the application stack is critical to lowering the total cost of ownership of your enterprise mission-critical applications. Oracle Tuxedo System and Application Monitor Plus (TSAM Plus) provides application performance management, service level management, and operations automation capabilities, which you can use to improve the performance and availability of Tuxedo applications. Using a single console, you manage and monitor all the products in the Tuxedo family.
-
Four OKE nodes for Oracle WebLogic Tuxedo Connectors.
The WebLogic Tuxedo Connector provides interoperability between WebLogic Server applications and Tuxedo services. The connector allows WebLogic Server clients to invoke Tuxedo services and Tuxedo clients to invoke WebLogic Server Enterprise Java Beans (EJBs) in response to a service request.
-
- Exadata DB systems
Exadata Cloud Service enables you to leverage the power of Exadata in the cloud. You can provision flexible X8M systems that allow you to add database compute servers and storage servers to your system as your needs grow. X8M systems offer RoCE (RDMA over Converged Ethernet) networking for high bandwidth and low latency, persistent memory (PMEM) modules, and intelligent Exadata software. X8M systems can be provisioned using an shape equivalent to a quarter rack X8 system, and then database and storage servers can be added at any time after provisioning.
This architecture has an active-standby pair of Exadata DB systems. They are attached to two private subnets for client and backup traffic. Oracle Data Guard is used for data synchronization and failover.
Recommendations
Use the following recommendations as a starting point to plan your architecture in Oracle Cloud. Your requirements might differ from the architecture described here.
- Cloud guard
Clone the Oracle-provided default recipes to create custom detector and responder recipes. In your recipes, you can specify the type of security issues to be detected and the response for each detected issue type. For example, you might consider a publicly visible bucket in Oracle Cloud Infrastructure Object Storage as a security risk that should be detected and fixed.
Oracle recommends that you enable Cloud Guard at the tenancy level, covering the broadest scope. With this approach, you can reduce the administrative burden of maintaining separate security configurations for individual compartments.
You can also use the managed list feature to make it easier to set the scope for your security monitoring and response rules.
For more information, see the Cloud Guard documentation.
- Security zones
A security-zone compartment enforces strict preconfigured security policies that can’t be modified. For example, any data in a security zone must be encrypted using customer-managed keys that you manage in the Oracle Cloud Infrastructure Vault service.
Oracle recommends that you use a security-zone compartment for resources that require a private subnet. You can't create public subnets in a security-zone compartment.
For more information, see the Security Zones documentation.
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
- OKE clusters
If you create the clusters using the web console, use the Custom Create option so that you can specify a VCN and subnet for deployment. Use a Flex shape, which allows you to customize the processor and memory resources while creating or resizing the nodes. For a large deployment, you can use bigger OKE clusters.
- Container registry
Oracle manages the registry, so you don’t have to choose the size or any other options. Oracle recommends that you create a private registry, as a security best practice.
- Database
This architecture uses quarter-rack Exadata DB systems. If you need more processing power, you can enable extra cores in multiples of two. Depending on the database workloads and the processing power needed, you can scale up the database.
- Load balancer
Use the 100-Mbps shape.
- Object storage
Use Oracle Cloud Infrastructure Object Storage for storing database backups. Create your buckets in a security-zone compartment so that their visibility is guaranteed to be private.
- Block volumes
Start with a size of 50 GB and the balanced performance option. You can scale the size and tune the performance option based on your business needs.
Considerations
When you design the topology for rehosting mainframe workloads in Oracle Cloud, consider the following factors:
- Scalability
-
Application tier:
You can scale the application servers vertically by changing the shape of the compute instances. A shape with a higher core count provides more memory and network bandwidth. If you need more storage, increase the size of the block volumes attached to the application server.
-
Database tier:
You can scale the databases vertically by enabling more cores for the Exadata DB system. You can add OCPUs in multiples of two for a quarter rack. The databases remain available during a scaling operation. If your workload outgrows the available CPUs and storage, you can migrate to a larger rack.
-
- Availability
For workloads deployed within a single availability domain, you can ensure resilience by distributing the resources across the fault domains as shown in this architecture. If you plan to deploy your workload in a region that has more than one availability domain, you can distribute the resources across multiple availability domains.
In the data tier, use Oracle Data Guard for data synchronization and failover between the primary and standby databases.
- Cost
-
Application tier:
Select compute shapes based on the cores, memory, and network bandwidth that your applications need. You can start with a four-core shape for the application servers. If you need more performance, memory, or network bandwidth, you can change to a larger shape.
-
Database tier:
Every OCPU that you enable on the Exadata rack needs licensing for Oracle Database Enterprise Edition and the database options and management packs that you plan to use.
-
- Backups
-
Application:
Oracle Cloud Infrastructure automatically backs up autonomous databases and retains the backups for 60 days. You can restore and recover your database to any point in time during the retention period. You can also create manual backups to supplement the automatic backups. The Oracle Cloud Infrastructure Object Storage bucket that you create stores manual backups and retains them for 60 days.
-
Database:
The Oracle Cloud Infrastructure Block Volumes service lets you create point-in-time backups of data on a block volume. You can restore these backups to new volumes at any time.
You can also use the service to make a point-in-time, crash-consistent backup of a boot volume without application interruption or downtime. Boot and block volumes have the same backup capabilities.
-
- Security
-
Access control:
Use Oracle Cloud Infrastructure Identity and Access Management policies to restrict who can access your resources in the cloud and the actions that they can perform.
-
Network security:
The Networking service offers two virtual firewall features that use security rules to control traffic at the packet level: security lists and network security groups (NSG). An NSG consists of a set of ingress and egress security rules that apply only to a set of VNICs of your choice in a single VCN. For example, you can choose all the compute instances that act as web servers in the web tier of a multitier application in your VCN.
NSG security rules function the same as security list rules. However, for an NSG security rule's source or destination, you can specify an NSG instead of a CIDR block. So, you can easily write security rules to control traffic between two NSGs in the same VCN or traffic within a single NSG. When you create a database system, you can specify one or more NSGs. You can also update an existing database system to use one or more NSGs.
-