Establish Multi-Cloud Private Network Connectivity Through Oracle Integration Cloud Service
When you need to integrate services or applications running on a private network—such as an Amazon Web Services VPC, Azure Vnet, Google Cloud Computing VPC—or an on-premises private network, with SaaS or on-premises enterprise applications, you can use Oracle Integration Cloud Service and a connectivity agent to establish private endpoint connectivity.
This architecture provides the necessary connectivity between multi-cloud private networks and Oracle's cloud services or applications without directing traffic through the public internet as part of its outbound integration from Oracle Integration Cloud Service.
Architecture
This reference architecture shows how to connect to a service or an application running on an AWS private network's Virtual Private Cloud (VPC) from Autonomous Transaction Processing through Oracle Integration Cloud Service, without requiring traffic routing through the public internet.
This scenario uses Oracle Integration Cloud Service connectivity agent to communicate with the AWS private service or application. The Oracle Integration Cloud Service connectivity agent is installed on an Oracle Cloud Infrastructure Compute instance on a private subnet of a VCN. The agent communicates with Oracle Integration Cloud Service through a service gateway on one side and with the service or application running on an AWS private network on the other side through a dynamic routing gateway (DRG) and FastConnect Private Peering or VPN.
The following diagram illustrates this reference architecture.
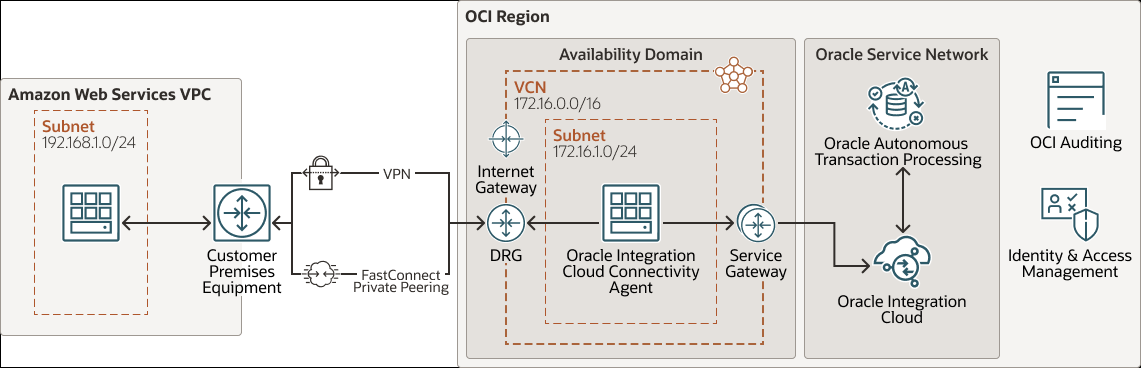
Description of the illustration multicloud-oic-arch.png
multicloud-oic-arch-oracle.zip
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Compartment
Compartments are cross-region logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize your resources in Oracle Cloud, control access to the resources, and set usage quotas. To control access to the resources in a given compartment, you define policies that specify who can access the resources and what actions they can perform.
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain shouldn't affect the other availability domains in the region.
- Virtual cloud network (VCN) and subnet
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Private Peering
Extends existing infrastructure by using private IP addresses.
- VPN Connect
Oracle Cloud Infrastructure VPN Connect is an IPsec VPN that enables you to create an encrypted connection between Oracle Cloud and your private IT infrastructure over the public Internet.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Autonomous Database
is a fully managed, preconfigured database environments that you can use for transaction processing and data warehousing workloads. You do not need to configure or manage any hardware, or install any software. Oracle Cloud Infrastructure handles creating the database, as well as backing up, patching, upgrading, and tuning the database.
- Autonomous Transaction Processing
Oracle Autonomous Transaction Processing is a self-driving, self-securing, self-repairing database service that is optimized for transaction processing workloads. You do not need to configure or manage any hardware, or install any software. Oracle Cloud Infrastructure handles creating the database, as well as backing up, patching, upgrading, and tuning the database.
- Oracle Integration Cloud
Service
With Oracle Integration Cloud, you have the power to integrate your cloud and on-premises applications, automate business processes, gain insight into your business processes, develop visual applications, use an SFTP-compliant file server to store and retrieve files, and exchange business documents with a B2B trading partner—all in one place.
- Oracle Integration Cloud
Service Connectivity Agent
Using the connectivity agent, you can create hybrid integrations and exchange messages between applications in private or on-premises networks and Oracle Integration Cloud.
- Backbone
Dedicated, secure network for interconnecting Oracle IaaS and PaaS services to Oracle SaaS running in the same or any other OCI Region.
- Customer-premises equipment (CPE)
An object that represents the network asset that lives in the on-premises network and establishes the VPN connection. Most border firewalls act as the CPE, but a separate device (like an appliance or a server) can be a CPE.
- AWS Virtual Private Cloud (Amazon Web Services VPC)
Enables you to launch AWS resources into a virtual network that you've defined. This virtual network closely resembles a traditional network that you'd operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
Recommendations
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
Use regional subnets.
- Restrict Access to an Oracle Integration Cloud
Service Instance
Restrict the networks that have access to your Oracle Integration Cloud Service instance by configuring an allowlist (formerly a whitelist). Only users from the specific IP addresses, Classless Inter-Domain Routing (CIDR) blocks, and virtual cloud networks that you specify can access the instance.
- Connectivity
When you deploy resources to Oracle Cloud Infrastructure, you might start small, with a single connection to your on-premises network. This single connection could be through FastConnect or through IPSec VPN. To plan for redundancy, consider all the components (hardware devices, facilities, circuits, and power) between your on-premises network and Oracle Cloud Infrastructure. Also consider diversity, to ensure that facilities are not shared between the paths.
- Use the Connectivity Agent in High Availability Environments
You can use the connectivity agent in high availability environments with Oracle Integration Cloud Service. You install the connectivity agent twice on different hosts. The connectivity agents can scale horizontally, thereby providing all the benefits of running multiple agents for an agent group. This results in increased performance and extends fail-over benefits.
Considerations
Consider the following points when deploying this reference architecture.
- Scalability
When creating Oracle Integration instances, administrators specify the number of message packs they plan to use for per instance.
- Resource limits
Consider the best practices, limits by service, and compartment quotas for your tenancy.
- Security
Use OCI Identity and Access Management (IAM) policies to control who can access your cloud resources and what operations can be performed. To protect the database passwords or any other secrets, consider using the OCI Vault service.
- Performance and cost
OCI offers Compute shapes that cater to a wide range of applications and use cases. Choose the shapes for your compute instances carefully. Select shapes that provide optimal performance for your load at the lowest cost. If you need more performance, memory, or network bandwidth, you can change to a larger shape.
- Availability
Consider using a high-availability option based on your deployment requirements and your region. The options include distributing resources across multiple availability domains in a region and distributing resources across the fault domains within an availability domain.
Fault domains provide the best resilience for workloads deployed within a single availability domain. For high availability in the application tier, deploy the application servers in different fault domains, and use a load balancer to distribute client traffic across the application servers.
- Monitoring and alerts
Set up monitoring and alerts on CPU and memory usage for your nodes, so that you can scale the shape up or down as needed.
Deploy
You can deploy this reference architecture on Oracle Cloud Infrastructure by performing below steps:
Explore More
Learn more about establishing multi-cloud private network connectivity through Oracle Integration Cloud Service.
Review these additional resources: