Deploy an Internet Sales Portal With an Oracle Cloud Infrastructure Landing Zone
To help federal, state, and local government agencies configure and secure their workloads in the cloud, Mythics has deployed a secure landing zone on Oracle Cloud Infrastructure (OCI) that meets the Center for Internet Security (CIS) benchmarks.
Using the OCI Landing Zone, Mythics can quickly customize, configure, and secure any environment within a few hours of creating the instance.
In its own OCI tenancy, Mythics deployed an internet sales portal that supports its marketing, sales, contracts, legal, accounting, and operations groups. Using APEX forms and wizards and a data warehouse that integrates with Oracle NetSuite, Mythics is now able to track and route internal approvals from each of these departments, generating hundreds of thousands of sales transactions and email workflow approval transactions each month.
By deploying its internet sales portal using the OCI Landing Zone, Mythics has:
- Increased performance and availability: Mythics is now able to quickly process transactions by using multiple compute cores, and also able to maintain high availability by using load balancers. Leveraging their disaster recovery capabilities, Mythics can quickly scale in or out on demand, even during seasonal bursts, such as a month-, quarter-, or year-end close.
- Automated complex security configurations: Mythics is able to quickly customize, configure, and secure its environment within a few hours of creating the instance.
- Created customizable security postures: Mythics can also reuse and modify the OCI Landing Zone templates and apply them to any public sector or commercial customer environment, running whatever type of workload on OCI.
Architecture
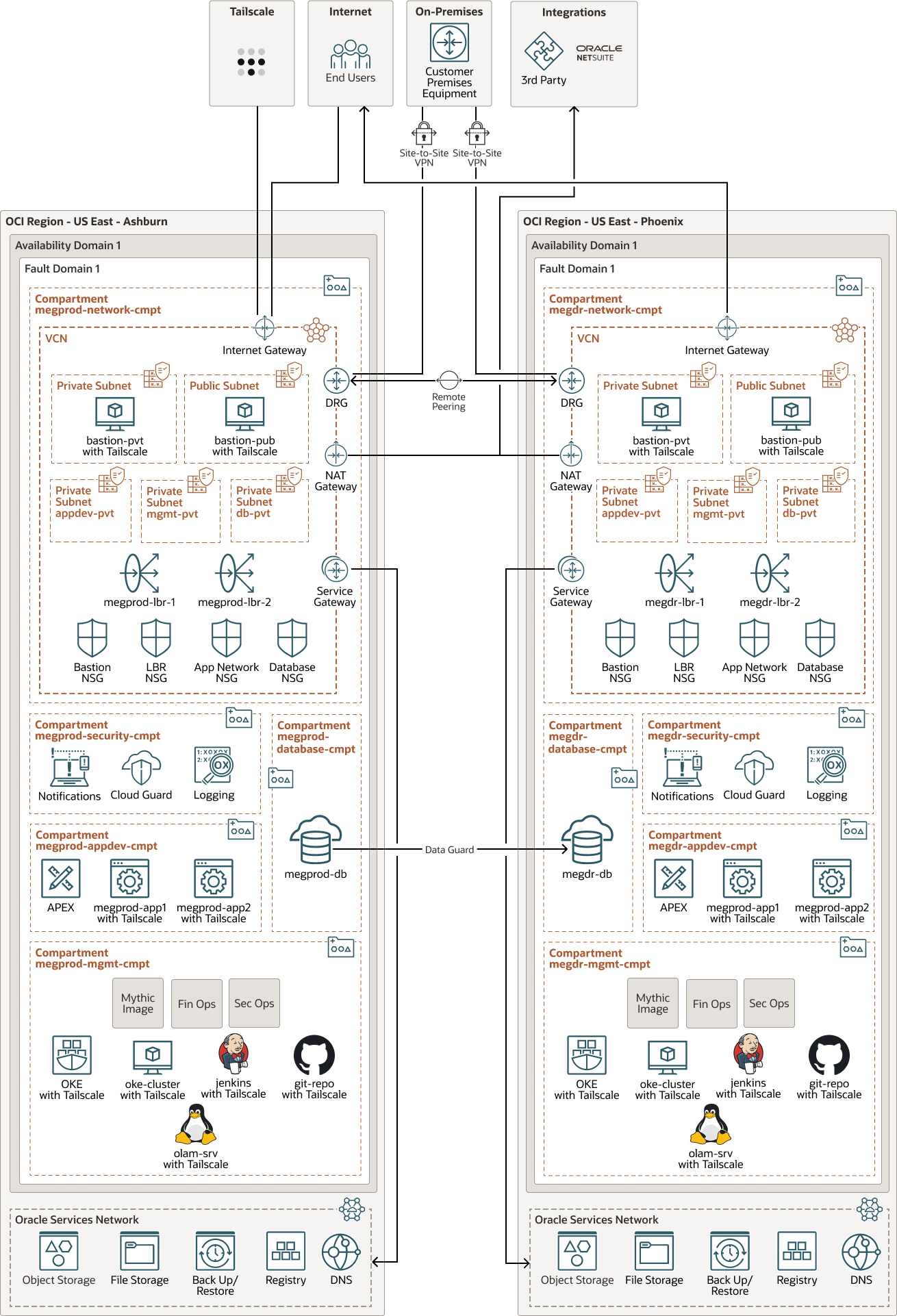
Mythics deployed an Oracle Cloud Infrastructure (OCI) Landing Zone to secure the environment for its internet sales portal.
Using the OCI Landing Zone template, Mythics automatically created a virtual cloud network (VCN), as well as multiple subnets, and compartments. The subnets were created with network isolation and segmentation, security lists, route tables, and network security groups (NSGs):
- appdev-pvt: A private subnet for application resources
- mgmt-pvt: A private subnet for management resources
- db-pvt: A private subnet for databases resources
- bastion-pvt: A private subnet for bastion host access
- bastion-pub: A public subnet for bastion host access
Mythics used compartments to group and control access to resources. Mythics implemented a least privilege access model by creating groups and policies and then assigning the appropriate permissions to control who can access the resources. The landing zone, by default, creates five compartments:
- megprod-network-cmpt: A compartment for network resources
- megprod-security-cmpt: A compartment for security resources that include, notifications, cloud guard, and logs
- megprod-appdev-cmpt: A compartment for APEX and application servers
- megprod-database-cmpt: A compartment for database servers
- megprod-mgmt-cmpt: A compartment for management resources
Mythics also used the OCI Landing Zone to automatically deploy security tools, such as Oracle Cloud Guard for security posture management, OCI Logging to consolidate logs, and OCI Notifications. Mythics then layers in their components, which include:
- APEX for low code application development of forms, wizards, and workflows
- Two virtual machine (VM) instances for application processes, load balanced for high availability
- Oracle Database Cloud Service running on virtual machines and a data warehouse for storing more than 200,000 current and historical sales transactions
- An OCI Kubernetes Engine (OKE) cluster to automate resource management
- Tools such as Jenkins, Git repository, and Oracle Linux Automation Manager (OLAM) included in their OKE cluster to automate software development, testing, deployment, and management
- Bastion hosts that provide access from a private subnet through the on-premises network and from a public subnet that's accessible from the internet
Users access the internet sales portal by using an internet gateway. Mythics developers and administrators manage the environment from an on-premises location by using Tailscale for added security. The on-premises network is connected by using VPN IPSec tunnels with the customer's on-premises equipment (CPE) connected to dynamic routing gateways (DRG). From the internet, Mythics developers access the environment by using Tailscale, which is a VPN service that secures devices and applications that are accessible anywhere. In addition to using groups, policies, and network rules, Tailscale allows Mythics to control edge network access, and thereby to fine-tune the exact level of access they grant. For example, Mythics developers can access the OKE cluster and application, while administrators can only access the application server instances, creating an additional security layer in the zero-trust access network.
NAT gateways are used for integrations with Oracle NetSuite. Oracle NetSuite CRM/ERP is updated every 15 minutes and is mined daily by a series of APEX dashboard and ad hoc reports. REST APIs are used as automation points, and push changes to NetSuite from the database. Additional integration points allow Mythics to use the application as a license orchestrator to manage large contracts through an unlimited license agreement (ULA).
For disaster recovery, the application is deployed in an active-passive configuration. US East Region-Ashburn is the primary region and US West Region-Phoenix is the disaster recovery (DR) site. The two regions are connected by using remote peering between the two DRGs. The load balancers redirect users to the DR site in case there is a failure in Ashburn. The database is replicated using Oracle Data Guard from Ashburn to Phoenix. File storage services and object storage are replicated from Ashburn to Phoenix. OCI native backup services are used to back up the infrastructure.
- Taking advantage of more platform-as-a-service (PaaS) options
- Migrating the database from Oracle Database Cloud Service running on virtual machines to Oracle Autonomous Database to relieve the Mythics teams from database operations and maintenance
The following diagram illustrates the networking and disaster recovery architecture:
mythics-oci-architecture-oracle.zip
The architecture has the following components:
- Tenancy
A tenancy is a secure and isolated partition that Oracle sets up within Oracle Cloud when you sign up for Oracle Cloud Infrastructure. You can create, organize, and administer your resources in Oracle Cloud within your tenancy. A tenancy is synonymous with a company or organization. Usually, a company will have a single tenancy and reflect its organizational structure within that tenancy. A single tenancy is usually associated with a single subscription, and a single subscription usually only has one tenancy.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Compartment
Compartments are cross-regional logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize, control access, and set usage quotas for your Oracle Cloud resources. In a given compartment, you define policies that control access and set privileges for resources.
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain shouldn't affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Site-to-Site VPN
Site-to-Site VPN provides IPSec VPN connectivity between your on-premises network and VCNs in Oracle Cloud Infrastructure. The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Network address translation (NAT) gateway
A NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and does not traverse the internet.
- Remote peering
Remote peering allows the VCNs' resources to communicate using private IP addresses without routing the traffic over the internet or through your on-premises network. Remote peering eliminates the need for an internet gateway and public IP addresses for the instances that need to communicate with another VCN in a different region.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Oracle Base Database Service
Oracle Base Database Service is an Oracle Cloud Infrastructure (OCI) database service that enables you to build, scale, and manage full-featured Oracle databases on virtual machines. Oracle Base Database Service uses OCI Block Volumes storage instead of local storage and can run Oracle Real Application Clusters (Oracle RAC) to improve availability.
- Data Guard
Oracle Data Guard and Oracle Active Data Guard provide a comprehensive set of services that create, maintain, manage, and monitor one or more standby databases and that enable production Oracle databases to remain available without interruption. Oracle Data Guard maintains these standby databases as copies of the production database by using in-memory replication. If the production database becomes unavailable due to a planned or an unplanned outage, Oracle Data Guard can switch any standby database to the production role, minimizing the downtime associated with the outage. Oracle Active Data Guard provides the additional ability to offload read-mostly workloads to standby databases and also provides advanced data protection features.
- Cloud Guard
You can use Oracle Cloud Guard to monitor and maintain the security of your resources in Oracle Cloud Infrastructure. Cloud Guard uses detector recipes that you can define to examine your resources for security weaknesses and to monitor operators and users for certain risky activities. When any misconfiguration or insecure activity is detected, Cloud Guard recommends corrective actions and assists with taking those actions, based on responder recipes that you can define.
- APEX Service
Oracle APEX is a low-code development platform that enables you to build scalable, feature-rich, secure, enterprise apps that can be deployed anywhere that Oracle Database is installed. You don't need to be an expert in a vast array of technologies to deliver sophisticated solutions. Oracle APEX includes built-in features such as user interface themes, navigational controls, form handlers, and flexible reports that accelerate the application development process.
- Notifications
The Oracle Cloud Infrastructure Notifications service broadcasts messages to distributed components through a publish-subscribe pattern, delivering secure, highly reliable, low latency, and durable messages for applications hosted on Oracle Cloud Infrastructure.
- LoggingLogging is a highly scalable and fully managed service that provides access to the following types of logs from your resources in the cloud:
- Audit logs: Logs related to events emitted by the Audit service.
- Service logs: Logs emitted by individual services such as API Gateway, Events, Functions, Load Balancing, Object Storage, and VCN flow logs.
- Custom logs: Logs that contain diagnostic information from custom applications, other cloud providers, or an on-premises environment.
- Kubernetes Engine
Oracle Cloud Infrastructure Kubernetes Engine (OCI Kubernetes Engine or OKE) is a fully managed, scalable, and highly available service that you can use to deploy your containerized applications to the cloud. You specify the compute resources that your applications require, and Kubernetes Engine provisions them on Oracle Cloud Infrastructure in an existing tenancy. OKE uses Kubernetes to automate the deployment, scaling, and management of containerized applications across clusters of hosts.
- Object storage
Oracle Cloud Infrastructure Object Storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- File storage
The Oracle Cloud Infrastructure File Storage service provides a durable, scalable, secure, enterprise-grade network file system. You can connect to a File Storage service file system from any bare metal, virtual machine, or container instance in a VCN. You can also access a file system from outside the VCN by using Oracle Cloud Infrastructure FastConnect and IPSec VPN.
- DNS
Oracle Cloud Infrastructure Domain Name System (DNS) service is a highly scalable, global anycast domain name system (DNS) network that offers enhanced DNS performance, resiliency, and scalability, so that end users connect to internet applications quickly, from anywhere.
- Registry
Oracle Cloud Infrastructure Registry is an Oracle-managed registry that enables you to simplify your development-to-production workflow. Registry makes it easy for you to store, share, and manage development artifacts, like Docker images. The highly available and scalable architecture of Oracle Cloud Infrastructure ensures that you can deploy and manage your applications reliably.
Explore More
Learn more about the features of this architecture and about related architectures.
See the following blog posts about Oracle Cloud Infrastructure Landing Zone: