Extend DoD accredited enclaves with Oracle Cloud for Government
Oracle Cloud for Government enables an all-domain advantage for the U.S. Department of Defense (DoD) with cloud innovation and resilience. The Defense Research and Engineering Network (DREN) has onboarded Oracle Cloud Infrastructure (OCI) as a Commercial Cloud Computing capability for DREN users, at classifications up to DoD IL5. There are two DREN cross-connects to the OCI Ashburn VA Region (East) and two cross-connects to the OCI Phoenix AZ Region (West).
DREN provides robust, high-capacity and low-latency network connectivity digital, imaging, video, and audio data transfer services, called ‘transports’, between defined service delivery points (SDPs). There are over 200 SDPs operating from inside military install bases called ‘Sites’ that connect over 500 currently active customers, comprised of Defense Labs, DoD Research, Development, Test and Evaluation (RDT&E), Acquisition Engineering (AE) communities, HPCMP (High Performance Computing Modernization Program) and including all five Defense Supercomputing Resource Centers (DSRCs).
- Support some of the world's largest computational projects.
- Deliver an aggregate of 4.5 billion processor hours of computing power per year, and over 40 petaFLOPS of computing capability via numerous HPC systems (supercomputers).
- Maintain mass storage archives with an aggregate storage capability in excess of 100 petabytes.
- Connect users to HPC systems via high-speed networks at speeds up to 40 gigabits/sec.
Architecture
This reference architecture describes how mission owners with DOD's DREN can leverage their existing infrastructure, services, processes, and accreditation by extending existing enclaves into Oracle Cloud. Use this architecture to explore, prototype, and pilot various applications in Oracle Cloud and gain operational experience to facilitate any requirements for Cloud-based development or test projects.
- A comprehensive portfolio of Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) capabilities. Oracle’s 2nd Generation architecture and infrastructure serves to enhance security, performance, and lower total cost of ownership compared to other cloud service providers. It provides the first natively bare metal server infrastructure combined with innovative security isolation enforcement through out-of-band network virtualization management.
- Introduction of improvements such as new generations of Intel, AMD, or ARM processors with faster core speeds, storage volumes with higher capacity and speed, and networks with lower latency. This includes specialized hardware like GPUs and RoCE networking that enable HPC and AI workloads or Exadata Cloud Service for extreme performance, high reliability relational database workloads.
- Use of open standards and open-source technologies to support the data management, integration and analytical workloads needed to enable DoD’s digital modernization. Oracle’s industry-unique cloud partnerships, including with VMWare through Oracle VMware Cloud Service, helps speed up cloud migrations with far less complexity.
- The only commercial cloud service provider offering both performance and management service level commitments.
- The “everything everywhere” policy highlighting the vision that the same services offered in our commercial cloud will exist in all Oracle regions. Pricing for Oracle Cloud services across ALL regions (including commercial, DoD and classified regions) is identical, eliminating any price uplift as mission owners move workloads for classified applications.
- Oracle FastConnect helps connect the DREN network to the Oracle Cloud network via reliable, dedicated, private, high-bandwidth connections. FastConnect customers pay a low flat fee monthly with no extra data ingress/egress charges, providing the lowest network costs in the industry.
- IP address space and DNS domain of local enclave (if possible) and extend CIDR (IP Space) to Oracle Cloud.
- Security structures implemented for the enclave and leverage existing security stack to Oracle Cloud by utilizing Bring Your Own License (BYOL).
- Infrastructure services used in the on-premises enclave. Any access outside the enclave is via existing enclave security stack using Oracle Cloud's Least Privilege Security Principle. Enclave accreditation is updated to reflect an additional "Site".
The following diagram illustrates this reference architecture.
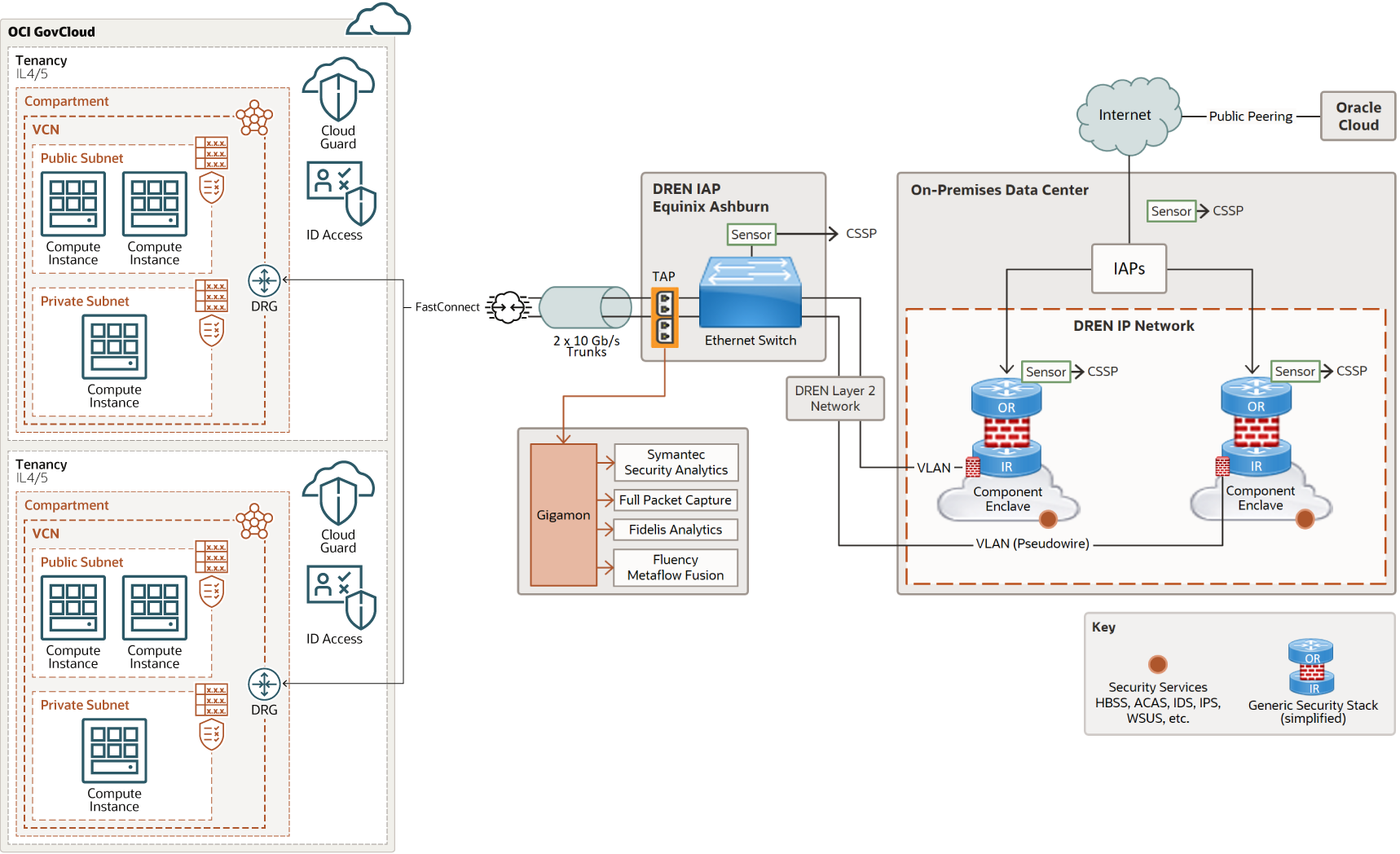
Description of the illustration oci-dod-dren-arch.png
- Mission owners can connect via DREN Cloud Access Points (CAPS) to Oracle Cloud for Government via OCI primary and secondary routers.
- The OCI Dynamic Routing Gateway (DRG 2.0) provides ingress to Mission Owners tenancy. DRGs can peer the mission owners tenancy to their on-premises network.
- Each enclave gets a dedicated VCN. All infrastructure, security services and processes are from the enclave. The only egress out of VCN is the VLAN to enclave (no other direct Internet, OCI, or Department of Defense information networks (DoDIN) access).
- Identity and Access Management (IAM) protects the mission owner’s tenancies across regions within a realm by applying policies on User Groups.
- A security list protects the routes at subnet level and adds to security of all resources within an individual subnet.
- Compartments add security and manageability for mission owners to isolate resources and limit access to resources by using IAM policies.
- A Network Security Group (NSG) secures the mission owner’s tenancy by applying custom rules to allow only ‘permitted’ traffic. NSGs are applied at the resources level.
The architecture has the following components:
- Tenancy
Oracle Government Cloud tenancy is a secure and isolated partition within OCI where you can create, organize, and administer your cloud resources.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Compartment
Compartments are cross-region logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize your resources in Oracle Cloud, control access to the resources, and set usage quotas. To control access to the resources in a given compartment, you define policies that specify who can access the resources and what actions they can perform. Compartments add security and managability for mission owners to isolate resources and limit access to resources via IAM policies.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Cloud Guard
You can use Oracle Cloud Guard to monitor and maintain the security of your resources in Oracle Cloud Infrastructure. Cloud Guard uses detector recipes that you can define to examine your resources for security weaknesses and to monitor operators and users for risky activities. When any misconfiguration or insecure activity is detected, Cloud Guard recommends corrective actions and assists with taking those actions, based on responder recipes that you can define.
- Security zone
Security zones ensure Oracle's security best practices from the start by enforcing policies such as encrypting data and preventing public access to networks for an entire compartment. A security zone is associated with a compartment of the same name and includes security zone policies or a "recipe" that applies to the compartment and its sub-compartments. You can't add or move a standard compartment to a security zone compartment.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Local peering gateway (LPG)
An LPG enables you to peer one VCN with another VCN in the same region. Peering means the VCNs communicate using private IP addresses, without the traffic traversing the internet or routing through your on-premises network.
Recommendations
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
- Security
Use Oracle Cloud Guard to monitor and maintain the security of your resources in Oracle Cloud Infrastructure proactively. Cloud Guard uses detector recipes that you can define to examine your resources for security weaknesses and to monitor operators and users for risky activities. When any misconfiguration or insecure activity is detected, Cloud Guard recommends corrective actions and assists with taking those actions, based on responder recipes that you can define.
For resources that require maximum security, Oracle recommends that you use security zones. A security zone is a compartment associated with an Oracle-defined recipe of security policies that are based on best practices. For example, the resources in a security zone must not be accessible from the public internet and they must be encrypted using customer-managed keys. When you create and update resources in a security zone, Oracle Cloud Infrastructure validates the operations against the policies in the security-zone recipe, and denies operations that violate any of the policies.
- Cloud Guard
Clone and customize the default recipes provided by Oracle to create custom detector and responder recipes. These recipes enable you to specify what type of security violations generate a warning and what actions are allowed to be performed on them. For example, you might want to detect Object Storage buckets that have visibility set to public.
Apply Cloud Guard at the tenancy level to cover the broadest scope and to reduce the administrative burden of maintaining multiple configurations. You can also use the Managed List feature to apply certain configurations to detectors.
- Security zones
Clone and customize the default recipes provided by Oracle to create custom detector and responder recipes. These recipes enable you to specify what type of security violations generate a warning and what actions are allowed to be performed on them. For example, you might want to detect Object Storage buckets that have visibility set to public.
Apply Cloud Guard at the tenancy level to cover the broadest scope and to reduce the administrative burden of maintaining multiple configurations.
You can also use the Managed List feature to apply certain configurations to detectors.
- Network security groups (NSGs)
You can use NSGs to define a set of ingress and egress rules that apply to specific VNICs. We recommend using NSGs rather than security lists, because NSGs enable you to separate the VCN's subnet architecture from the security requirements of your application.
Considerations
Consider the following points when deploying this reference architecture.
- Performance
FastConnect allows direct connectivity to OCI from your on-premises data centers via dedicated, private, and high-bandwidth connections. FastConnect provides an easy and economical way to create a dedicated and private connection with higher bandwidth options. If faster speeds are needed consider higher bandwidth. Port speeds are available in increments of 10 and 100 Gbps.
- Security
Leverage MacSec Encryption(MACSec) on FastConnect to protect network to network connections on Layer2. With MACSec enabled you get to choose AES encryption algorithm, 2 security keys are exchanged and verified between two connected networks, and then a secure bi-directional link is established. The vault service securely stores the encryption keys.