Deploy Multicloud Oracle Database Service for Microsoft Azure in a Hub and Spoke Topology
This reference architecture deploys Oracle Database Service for Microsoft Azure (ODSA) and FortiGate, Fortinet’s next generation firewall, in a hub and spoke topology in Microsoft Azure.
Oracle Cloud Infrastructure (OCI) offers best-in-class security and operational processes for multicloud and hybrid architectures, while Fortinet provides an enterprise-class cloud security solution that extends the Fortinet Security Fabric to include native integration with cloud service providers.
Together, they protect applications across multicloud environments by delivering scalable performance and by bringing advanced security orchestration and unified threat protection.
Architecture
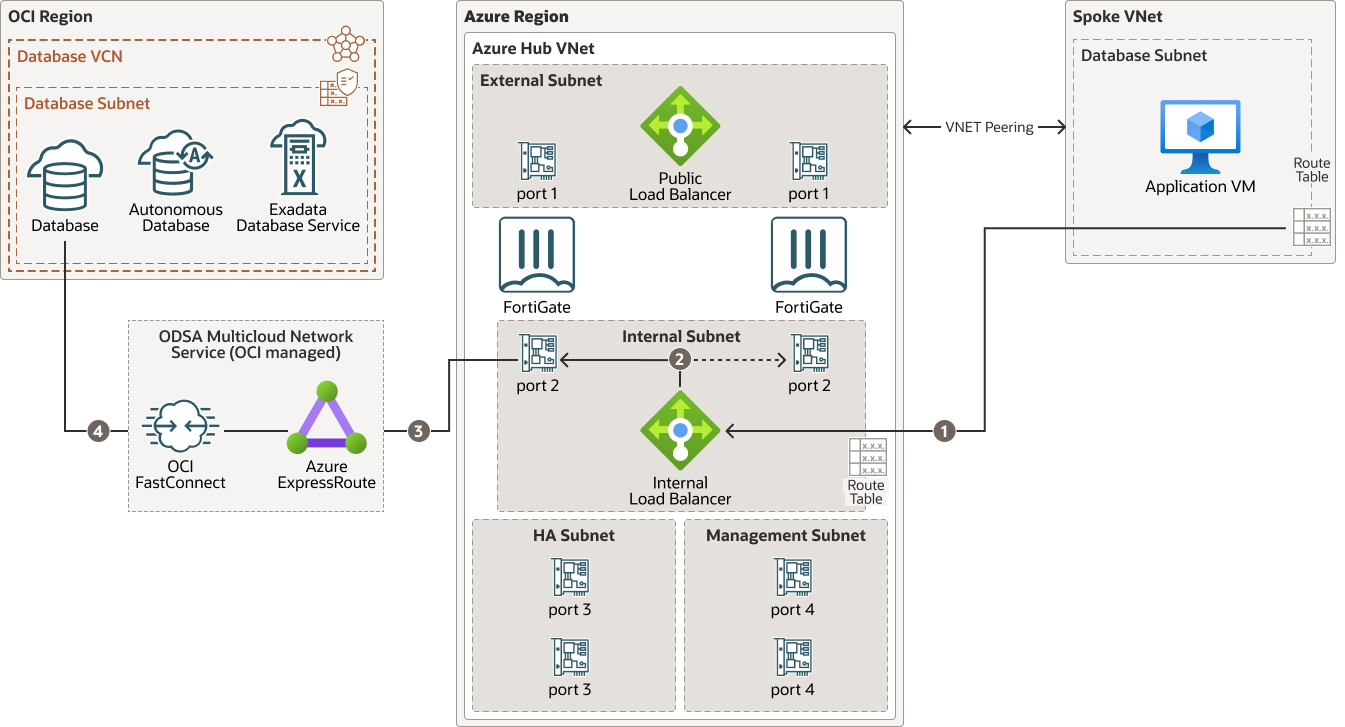
The Microsoft Azure network design uses a hub and spoke topology.
The hub virtual network is the central point of connectivity for traffic that enters and leaves the network (north-south traffic) and for traffic within the network (east-west traffic). This architecture provides a highly scalable and modular design for connecting multiple spokes.
The FortiGate Next-Generation firewalls are deployed in a high-availability (HA) active/standby scheme in the Azure hub to enforce security and traffic inspection. The database component of the Oracle Database Service for Microsoft Azure (ODSA) service is deployed in a VCN in Oracle Cloud Infrastructure (OCI).
The following diagram illustrates this reference architecture.
odsa-fortigate-azure-architecture-oracle.zip
East-West Traffic
Traffic from Azure spoke VNets to the ODSA database segment (east-west traffic) is routed to the FortiGate cluster for inspection through an internal load balancer and the trust interface.
The architecture diagram shows the traffic flow between the application virtual machine (VM) and ODSA:
- The application VM requests a connection to the database on OCI using specific database ports, such as SQL: TCP/1521. A route-table with user-defined-routes (UDR) is associated with the spoke subnet to handle default traffic in Azure. The connection request is forwarded to the frontend IP address of the internal load balancer which is part of the FortiGate active/passive deployment.
- The load balancer in Azure automatically directs traffic to the active VM of the FortiGate cluster. Port 2 is the FortiGate VM’s internal virtual network interface card (vNIC) which handles incoming trust traffic.
- Based on the configured firewall policy, FortiGate allows or rejects connection requests. If the traffic is allowed, packets are forwarded to the designated next-hop IP address. The next-hop IP address is configured as part of ODSA deployment and is specific to the particular ODSA customer deployment. Traffic routing is handled by the route table definition and by user defined routes (UDR).
- Packets are forwarded to the OCI database server over the ODSA network link.
Return traffic from ODSA database segment to Azure follows the reverse path.
ODSA requires policies with the following ports and protocols to be open:
| Component | Protocol | Port |
|---|---|---|
| Application tier | TCP/HTTPS | 443 |
| SSH port | TCP | 22 |
| Database tier | TCP | 1521–1522 |
| ONS and FAN port | TCP | 6200 |
| TCPS port | TCP | 2484 |
A route table for the spoke VNet configuration is required to manipulate default routing behavior. For specific destination CIDRs (ODSA_DB_CIDR in this example), traffic is forwarded to the next-hop IP address (ILB_FrontEnd_FortiGate_HA in this case). The same route-table can be associated with multiple subnets in the same or in different VNets.
Azure Route Table for spoke VNet UDR configuration:
| Destination IP Addresses | Next Hop Type | Next Hop Address |
|---|---|---|
| ODSA_DB_CIDR | Virtual appliance | ILB_FrontEnd_FortiGate_HA |
Azure Route Table for hub VNet UDR configuration:
| Destination IP Addresses | Next Hop Type | Next Hop Address |
|---|---|---|
| ODSA_DB_CIDR | Virtual appliance | ILB_FrontEnd_ODSA |
FortiGate route table:
| Destination IP Addresses | Next Hop Address |
|---|---|
| ODSA_DB_CIDR | Default gateway of trust subnet |
| APP_SPOKE_CIDR | Default gateway of trust subnet |
The architecture includes the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Virtual cloud network (VCN) and subnet
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Oracle Database Service for Microsoft
Azure
Oracle Database Service for Microsoft Azure (ODSA) allows you to easily integrate Oracle Cloud Infrastructure Database into your Azure cloud environment. ODSA uses a service-based approach and is an alternative to manually creating complex cross-cloud deployments for your application stacks.
- Available Oracle Database Systems
Oracle Database Service for Microsoft Azure offers the following products:
- Oracle Exadata Database Service: You can provision flexible Exadata systems that allow you to add database compute servers and storage servers to your system at any time after provisioning.
- Oracle Autonomous Database on shared Exadata infrastructure: Autonomous Database provides an easy-to-use, fully autonomous database that scales elastically, delivers fast query performance, and requires no database administration.
- Base Database: Using ODSA, you can deploy Oracle Enterprise Edition or Oracle Standard Edition 2 databases on virtual machine database systems. You can deploy single-node systems or 2-node RAC systems.
- ODSA Multicloud Link
A multicloud link is established between an OCI account and an Azure account to deploy Oracle Database service in OCI and an application in Azure. To perform basic database and infrastructure management tasks, you use the ODSA portal, which is an OCI interface. In the Azure portal, you can view database metrics and events. Metrics appear in Azure Application Insights, while events appear in Azure Log Analytics.
- ODSA Network Link
A network link is created using Oracle Interconnect for Microsoft Azure, a high performance, low-latency, low-jitter private tunnel connection for network traffic between OCI and Azure. Oracle has partnered with Azure to offer this connection in a designated set of OCI regions located around the world. When you sign up for ODSA, the service configures the private connection to your database resources as part of the account linking process.
- Azure VNet
Azure Virtual Network (VNet) is the fundamental building block for your private network in Azure. VNet enables many types of Azure resources, such as Azure virtual machines (VM), to securely communicate with each other, the internet, and on-premises networks.
- Virtual network interface card (VNIC)
The services in Azure data centers have physical network interface cards (NICs). Virtual machine instances communicate using virtual NICs (VNICs) associated with the physical NICs. Each instance has a primary VNIC that's automatically created and attached during launch and is available during the instance's lifetime.
- Azure Route table (User Defined Route – UDR)
Virtual route tables contain rules to route traffic from subnets to destinations outside a VNet, typically through gateways. Route tables are associated with subnets in a VNet.
- Fortinet FortiGate next-generation firewall
FortiGate is Fortinet's next-generation firewall. It provides network and security services such as threat protection, SSL inspection, and ultra-low latency for protecting internal segments and mission-critical environments. This solution is available for deployment directly form Oracle Cloud Marketplace and supports direct single root I/O virtualization (SR-IOV) for enhanced performance.
- Azure Load balancer
The Azure Load Balancing service provides automated traffic distribution from a single-entry point to multiple servers in the back end.
Deploy
To deploy Oracle Database Service for Microsoft Azure using Fortinet Security Fabric, perform the following high-level steps:
- Set up FortiGate high availability firewall in an Azure hub and spoke topology by selecting and installing a version of FortiGate:
- Set up Oracle Database Service for Microsoft
Azure (ODSA) by requesting a multicloud link at the following address. When you sign up for ODSA, the service configures the private connection to your database resources as part of the account linking process. You are prompted to provide a recognized organization name or an email address:
Request Oracle Database Service for Microsoft Azure multicloud link
- Deploy ODSA and establish the network link.
- Configure static routes on FortiGate.
- Configure the route table for the spoke subnet on Azure VNet.
- Create a firewall policy in FortiGate.
- Deploy the application server in the spoke VNet.
Explore More
Learn more about this reference architecture and about related reference architectures.
Oracle Cloud Infrastructure reference materials:
- Best practices framework for Oracle Cloud Infrastructure
- Oracle Cloud Infrastructure Security Overview
- Deploy FortiGate Firewalls and Secure your workloads on OCI (LiveLabs workshop)