Implement Message-Level Encryption in Oracle Integration Using OCI Vault
Message-Level Encryption (MLE) is a security technique used to protect the confidentiality and integrity of a message during transmission. It involves using encryption algorithms to scramble the contents of a message so that only the intended recipient, with the decryption keys, can read it.
Rest API are stateless by architecture, meaning the server is not maintaining a session and has no information about the client. In the request, the client needs to send all the information to allow the server to respond. When working with Rest API and security, the focus is on authentication, authorization and confidentiality.
For authentication and authorization, there are protocols and best practices that vary from API Keys, Basic Authentication, JWT Token, to oAuth. For confidentiality, you can enable Transport Level Security (TLS), the process of securing communication over a network by encrypting traffic. This is why most Rest APIs enforce HTTPS rather than simple HTTP. All these have their own pros and cons, and are supported by Oracle Integration out of the box.
While network-level security meets requirements most of the time, there are times when enforcing message or payload-level encryption is required (for example, when it includes sensitive information, such as: personal identification information [PII], credit card numbers, bank account details, medical records, or the like). This is why many payment gateways (Visa, MasterCard, government entities) enforce MLE for Rest APIs containing sensitive data.
Oracle Integration provides out-of-the-box features to meet authentication, authorization, and TLS. MLE can be achieved by using OCI Vault.
Architecture
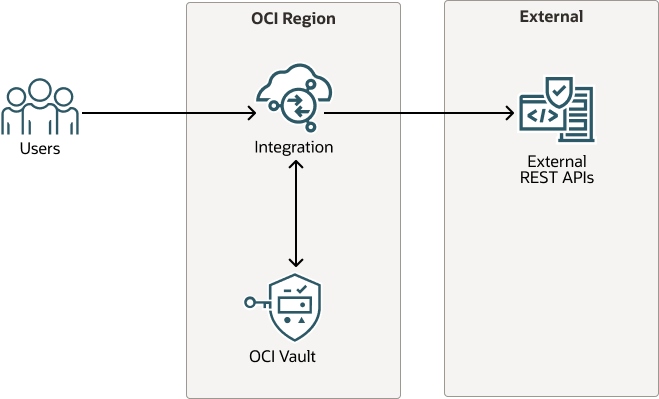
This reference architecture demonstrates how to use OCI Vault to achieve MLE in Oracle Integration.
OCI Vault is an encryption management service that stores and manages encryption keys and secrets to securely access resources. It provides APIs to allow managing keys as well as signing, encrypting, and decrypting data using these keys.
When working with cryptography, there are two fundamental types of systems to secure data.
- Symmetric cryptography uses the same (private) key for encryption and decryption. The sender and receiver must have the same secret key, which they use to encrypt and decrypt the data. This means that if someone intercepts the key, they can decrypt the data.
- Asymmetric cryptography on the other hand, uses two different keys: a public key and a private key. The sender uses the recipient's public key to encrypt the data, and the recipient uses their private key to decrypt it. The private key is kept secret and never shared, which makes it much more secure than symmetric cryptography.
Symmetric cryptography has the advantage of speed, but is less secure since it uses the same key for both encryption and decryption. Asymmetric cryptography, while slower, is more secure because the private key used for decryption is never shared and can only be accessed by the recipient.
OCI Vault supports these key shape algorithms.
| Key Shape Algorithm | Description |
|---|---|
| Advanced Encryption Standard (AES) | AES keys are symmetric keys that you can use to encrypt data. |
| Rivest-Shamir-Adleman (RSA) | RSA keys are asymmetric keys, also known as key pairs, consisting of a public key and a private key that you can use to encrypt data in transit, to sign data, and to verify the integrity of signed data. |
| Elliptic curve cryptography digital signature algorithm (ECDSA) | ECDSA keys are asymmetric keys that you can use to sign data and to verify the integrity of signed data. |
At times, you need to use both symmetric and asymmetric. For example, a customer shares their RSA public key with you; you generate and use an AES private key to encrypt the data; and you encrypt the private key with the customer's RSA public key, which you send in the payload. As the customer has not shared their RSA private key, only they can decrypt the data, first by decrypting the AES key and then using it to decrypt the payload. This is done when your payload size is larger than an RSA key can encrypt.
OCI Vault allows you to import or create your own master encryption keys. When you use imported key material, you remain responsible for the key material while allowing OCI Vault to use a copy of it. See Explore More for information on importing keys.
OCI Vault provides a number of APIs that can be used by Oracle Integration. See Explore More for the vault key management API. Here are some of the APIs that are used commonly in message level encryption scenarios.
| API | Description |
|---|---|
| Encrypt | Encrypts data using encryption details provided as part of the request. |
| Decrypt | Decrypts data using decryption details provided as part of the request. |
| Sign | Creates a digital signature for a message or message digest by using the private key of a public-private key pair, also known as an asymmetric key. |
| Verify | Verifies a digital signature that was generated by the sign operation by using the public key of the same asymmetric key that was used to sign the data. If you want to validate the digital signature outside of the service, you can do so by using the public key of the asymmetric key. |
When working in Oracle Integration, and you have to encrypt the payload before sending the request to a Rest API, you can use OCI Vault. If you are working with symmetric cryptography, you can receive the AES private key, upload it on OCI Vault, and use OCI Vault APIs to encrypt the data and send this encrypted data to the Rest API. If you require asymmetric cryptography, you can receive the RSA public key, upload it on OCI Vault and use the OCI Vault APIs to encrypt the data and send this encrypted data to the Rest API. Similarly, if you want to enforce Rest APIs in Oracle Integration to have encrypted payload, you can create keys, share with your clients, and use OCI Vault APIs to decrypt the data and verify. Also you can combine both keys when you need to use both asymmetric and symmetric cryptography.
The following diagram illustrates this reference architecture.
oci-vault-architecture-oracle.zip
The architecture has the following components:
- Oracle Integration
Oracle Integration provides a comprehensive set of tools and services to help organizations integrate their various applications, services, and data sources, both on-premises and in the cloud. Oracle Integration offers a range of features including pre-built connectors for integrating with various popular applications such as Oracle Fusion, Salesforce, SAP, Workday and many more, as well as custom connectors for integrating with other applications and services. It also provides an intuitive visual interface for designing, testing, and deploying integrations, making it easy for users to create complex integration workflows without requiring coding skills.
- Oracle Cloud Infrastructure Vault
OCI Vault is a secure and scalable key management service offered by Oracle Cloud Infrastructure (OCI). It provides a centralized location for managing cryptographic keys and secrets used to secure OCI resources and applications. OCI Vault offers a range of features, including key generation and storage, secure distribution of keys, encryption, and decryption. It allows users to manage their own keys or use OCI-managed keys. Users can also rotate their keys regularly to ensure maximum security.
OCI Vault also offers rich set of Rest APIs to manage vaults and keys.
Considerations
Consider the following points when implementing this reference architecture.
- Security
Use Oracle Cloud Infrastructure Identity and Access Management (IAM) policies to control who can access your cloud resources and what operations can be performed. Assign least privilege access for IAM users and groups to resource types.
- Service limits
Consider the limits and quotas for the OCI services used in the topology. See Explore More.