PayPal: Essbase and Analytics Deployment on Oracle Cloud
To help modernize its financial planning and analytics systems, and "get itself out of the data center business," online payment platform, PayPal, moved its on-premises Hyperion Essbase application to Oracle Cloud Infrastructure (OCI).
PayPal also deployed Oracle Analytics Cloud to provide a visualization tool for Essbase users, an Oracle Autonomous Transaction Processing database to log the Essbase schemas, and Oracle Cloud Infrastructure Identity and Access Management to manage user access.
Since moving to the Oracle Cloud, PayPal's financial teams are able to run predictive analytics, model what-if scenarios, and create advanced ad hoc reports on demand, as well as load and retrieve data more than 30% faster, run calculation scripts 50% faster, and reduce 21 on-premises servers down to just 10 cloud servers.
Architecture
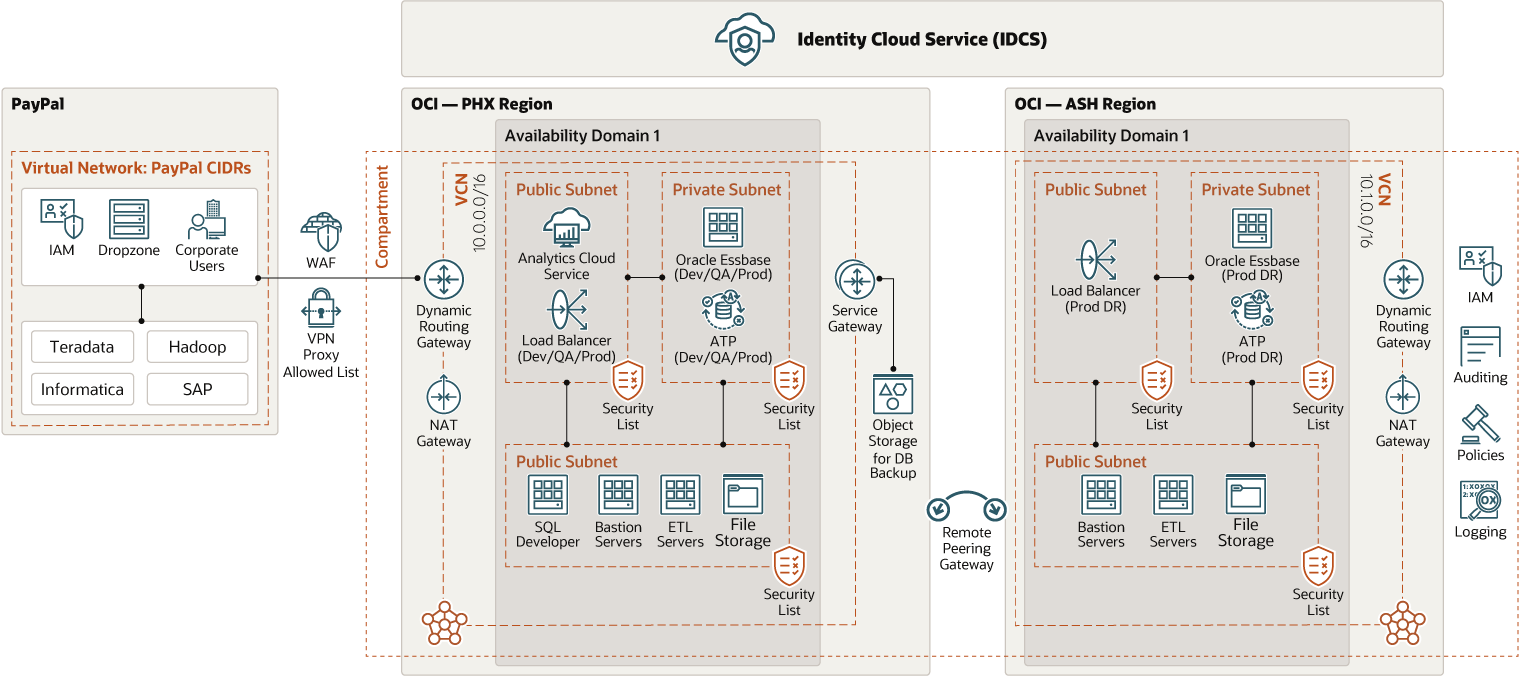
PayPal runs its primary production environment in the US-Phoenix Oracle Cloud region and its disaster recovery environment in the US-Ashburn Oracle Cloud region.
Both the primary and disaster recovery environments communicate using remote peering connections, which allow network traffic to flow swiftly between the two environments. PayPal directs all of its network traffic from and to its internal network through VPN FastConnect.
While PayPal's development and quality assurance (QA) environments exist in the same virtual cloud networks (VCNs) and subnets as its production environment, only developers can access the development environment. An Oracle SQL Developer instance queries Oracle Autonomous Transaction Processing (ATP) instances, which houses the Oracle Essbase schemas. The primary ATP production instance features backups to object storage through the service gateway.
Using DropZone, a home-grown Secure-FTP server, PayPal transfers data from its on-premises data warehouse to Essbase in Oracle Cloud Infrastructure (OCI), with all the data transfers being audited, checked for encryption, and logged. Essbase users can connect to services provided in the OCI network and can use Oracle Analytics Cloud to run self-service visualizations. Oracle Cloud Infrastructure File Storage is shared across all application and bastion servers.
The following diagram illustrates this reference architecture.
paypal-essbase-oac-oci-oracle.zip
The implementation in each OCI region belongs to a distinct compartment, each having its own VCN. The production VCN and the failover VCN are connected by remote peering using dynamic routing gateways (DRGs).
Each VCN has three subnets:
- Public Subnet 1 contains Oracle Cloud Infrastructure Load Balancing, and Oracle Analytics Cloud (OAC). OAC is running in the primary VCN only.
- Public Subnet 2 is where a bastion server, ETL servers, Oracle Cloud Infrastructure File Storage and an Oracle SQL Developer server are running. The Oracle SQL Developer server is only running in the primary VCN.
- Private Subnet 1 is where PayPal runs its Essbase servers, and an Oracle Autonomous Transaction Processing (ATP) database, both of which are replicated in the disaster recovery (DR) site.
At the center of PayPal's architecture is Oracle Identity Cloud Service (IDCS), which manages security, roles, access, and application assignments for the entire OCI footprint.
- Security implementations include an IP allowed list, Oracle Cloud Infrastructure Web Application Firewall, Oracle IDCS groups, IDCS applications, and filtering at the Essbase cube level.
-
The IP allowed list is a key part of the design, ensuring that only the users who are connected to the PayPal network can access the applications.
- PayPal's production environment is only accessible through SSO, and each subnet has its own IP allowed list.
- Audits are performed monthly to verify roles and controls. When someone changes jobs, the event triggers the user to confirm whether the roles and access still apply to the new job.
The architecture has the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Compartment
Compartments are cross-region logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize your resources in Oracle Cloud, control access to the resources, and set usage quotas. To control access to the resources in a given compartment, you define policies that specify who can access the resources and what actions they can perform.
- Identity and access management (IAM)
Oracle Cloud Infrastructure Identity and Access Management (IAM) enables you to control who can access your resources in Oracle Cloud Infrastructure and the operations that they can perform on those resources.
- Monitoring
Oracle Cloud Infrastructure Monitoring service actively and passively monitors your cloud resources using metrics to monitor resources and alarms to notify you when these metrics meet alarm-specified triggers.
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Web Application Firewall (WAF)
Oracle Cloud Infrastructure Web Application Firewall (WAF) is a payment card industry (PCI) compliant, regional-based and edge enforcement service that is attached to an enforcement point, such as a load balancer or a web application domain name. WAF protects applications from malicious and unwanted internet traffic. WAF can protect any internet facing endpoint, providing consistent rule enforcement across a customer's applications.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- VPN Connect
VPN Connect provides site-to-site IPSec VPN connectivity between your on-premises network and VCNs in Oracle Cloud Infrastructure. The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
- Network address translation (NAT) gateway
A NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Remote peering
Remote peering allows the VCNs' resources to communicate using private IP addresses without routing the traffic over the internet or through your on-premises network. Remote peering eliminates the need for an internet gateway and public IP addresses for the instances that need to communicate with another VCN in a different region.
- Compute
The Oracle Cloud Infrastructure Compute service enables you to provision and manage compute hosts in the cloud. You can launch compute instances with shapes that meet your resource requirements for CPU, memory, network bandwidth, and storage. After creating a compute instance, you can access it securely, restart it, attach and detach volumes, and terminate it when you no longer need it.
- Bastion host
The bastion host is a compute instance that serves as a secure, controlled entry point to the topology from outside the cloud. The bastion host is provisioned typically in a demilitarized zone (DMZ). It enables you to protect sensitive resources by placing them in private networks that can't be accessed directly from outside the cloud. The topology has a single, known entry point that you can monitor and audit regularly. So, you can avoid exposing the more sensitive components of the topology without compromising access to them.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can seamlessly scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- File storage
The Oracle Cloud Infrastructure File Storage service provides a durable, scalable, secure, enterprise-grade network file system. You can connect to a File Storage service file system from any bare metal, virtual machine, or container instance in a VCN. You can also access a file system from outside the VCN by using Oracle Cloud Infrastructure FastConnect and IPSec VPN.
- Analytics
Oracle Analytics Cloud is a scalable and secure public cloud service that empowers business analysts with modern, AI-powered, self-service analytics capabilities for data preparation, visualization, enterprise reporting, augmented analysis, and natural language processing and generation. With Oracle Analytics Cloud, you also get flexible service management capabilities, including fast setup, easy scaling and patching, and automated lifecycle management.
- Autonomous Transaction
Processing
Oracle Autonomous Transaction Processing is a self-driving, self-securing, self-repairing database service that is optimized for transaction processing workloads. You do not need to configure or manage any hardware, or install any software. Oracle Cloud Infrastructure handles creating the database, as well as backing up, patching, upgrading, and tuning the database.
Get Featured in Built and Deployed
Want to show off what you built on Oracle Cloud Infrastructure? Care to share your lessons learned, best practices, and reference architectures with our global community of cloud architects? Let us help you get started.
- Download the template (PPTX)
Illustrate your own reference architecture by dragging and dropping the icons into the sample wireframe.
- Watch the architecture tutorial
Get step by step instructions on how to create a reference architecture.
- Submit your diagram
Send us an email with your diagram. Our cloud architects will review your diagram and contact you to discuss your architecture.