Secure Oracle E-Business Suite Workloads with Fortinet Security Fabric
Move or extend Oracle E-Business Suite workloads to the cloud using Fortinet Security Fabric to augment the native security options provided by Oracle Cloud Infrastructure without significant configuration, integration, or business process changes.
Security in the cloud is based on a shared responsibility model. Oracle is responsible for the security of the underlying infrastructure, such as data center facilities, and hardware and software to manage cloud operations and services. Customers are responsible for securing their workloads and configure their services and applications securely to meet their compliance obligations.
Oracle Cloud Infrastructure offers best-in-class security technology and operational processes to secure its enterprise cloud services. Fortinet provides an enterprise-class cloud security solution that extends the Fortinet Security Fabric to include native integration with Oracle Cloud Infrastructure.
Together, they protect applications across on-premises data centers and cloud environments delivering scalable performance and bringing advanced security orchestration and unified threat protection.
Architecture
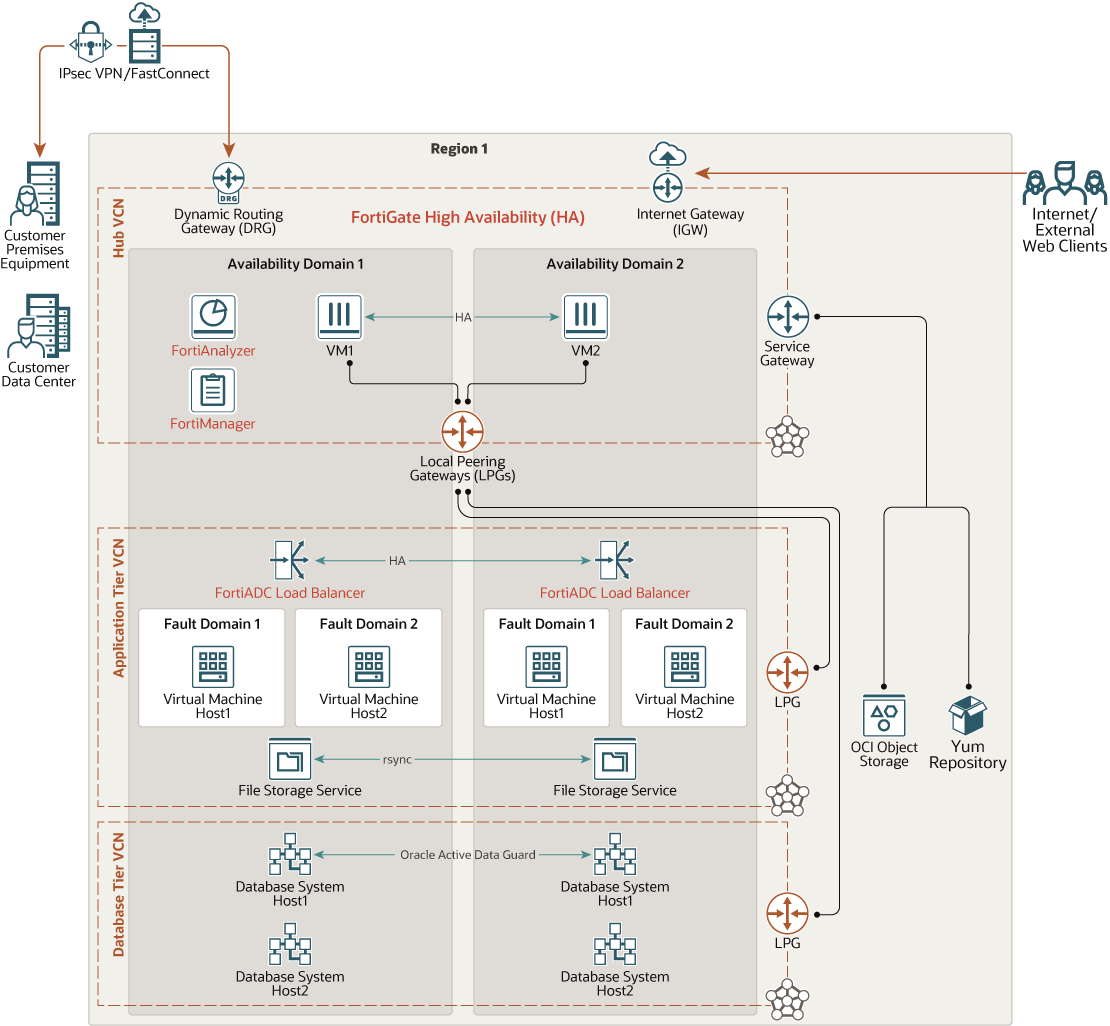
This architecture deploys Oracle E-Business Suite workloads in the cloud using Fortinet Security Fabric in a hub and spoke network topology to augment the native security options provided by Oracle Cloud Infrastructure.
The hub-spoke topology is a networking pattern that connects a centralized network (the hub) to multiple directed connected networks (the spokes). Traffic between these networks flows through a highly available FortiGate Next-Generation firewall to enforce security and traffic inspection through a centralized location. The hub virtual cloud network (VCN) is the central point of connectivity for traffic that enters and leaves the network (north-south traffic) and for traffic within the network (east-west traffic). Each tier of the Oracle E-Business Suite architecture is deployed on its own spoke VCN, allowing micro segmentation with more layers of protection because every packet moving between different tiers can be inspected and secured.
This architecture provides a highly scalable and modular design for connecting multiple spokes where each spoke network typically represents one specific application tier such as application, database, and so on. You can use the architecture with different environments, such as development, test, and production and with different infrastructures, such as regions, on-premises data centers, and multiple clouds.
The following diagram illustrates this reference architecture.
ebs-fortinet-oci-architecture.zip
You can implement the hub and spoke topology in different ways:
-
Leverage transit-routing with local peering gateways (LPG) to connect spoke VCNs with the hub VCN.
Each Spoke VCN should have a route rule to forward all traffic to the LPG, and within the LPG you should have another route rule that forwards the traffic to the untrust IP address of FortiGate (floating IP) attached to the hub VCN.
-
Attach each FortiGate virtual network interface card (VNIC) into each spoke VCN.
Each Spoke VCN should have a route rule to forward all the traffic to FortiGate VNIC private IP address attached to the Spoke VCN.
Consider that any traffic within each VCN (where the destination IP is within the VCN CIDR range) should not get inspected by FortiGate as Oracle Cloud Infrastructure automatically forwards all packets whose destination is the VCN itself directly through the internal Oracle Cloud Infrastructure subnet default gateway to the destination IP.
North-South Inbound Traffic
Inbound traffic which originates from either the internet or from an on-premises network connects to a public IP address hosted on the untrust or WAN interface of the FortiGate firewall. The public IP address (reserved or ephemeral) is a NAT IP address managed by Oracle that is associated with a secondary private IP address within the untrust subnet on Oracle Cloud Infrastructure. The secondary private IP address (floating IP) is statically assigned to the untrust interface on FortiGate. If failover occurs, the floating IP moves to another host along with the public IP address.
After packet inspection, the inbound traffic leaves FortiGate through the trust interface. The destination address is the FortiADC virtual IP address deployed in the application tier spoke VCN. FortiADC balances the traffic between the active Oracle E-Business Suite application servers based on load balancer policies. Because this traffic is within the VCN, the packet goes directly to the destination host. The ingress traffic flows in the following pattern:
- FortiGate hub VCN: From the FortiGate untrust VNIC to the FortiGate trust VNIC to the Oracle Cloud Infrastructure trust subnet default gateway to the LPG on the trust subnet.
- Application tier spoke VCN: From the LPG on the application tier subnet to the Oracle Cloud Infrastructure FortiADC subnet default gateway to the FortiADC VNIC to the Oracle E-Business Suite application servers.
For multiple environments inspected through the same firewall, you can assign multiple secondary IP addresses to both untrust and trust interfaces (VNICs). Each private IP should be used as the source address which can be mapped to one specific target application or environment in your firewall policies. Alternatively, you can set up a destination NAT policy with port forwarding in the FortiGate pointing to different virtual IPs or ports that can represent each individual destination application or environment.
North-South Outbound Traffic
Outbound traffic from the FortiGate hub VCN is routed through the internet gateway.
Outbound traffic from spoke VCNs to any destination is routed from the spoke VCN LPG to the peered LPG in the hub VCN. Once the packet reaches the hub VCN, the route associated with the LPG forwards the traffic to the FortiGate floating IP in the trust interface. From there, after inspection, FortiGate routes the packet to the untrust subnet default gateway. Based on the trust subnet route table, it continues to the internet or to on-premises through the internet gateway.
East-West Traffic
Oracle recommends segmenting networks at the VCN level instead of the subnet level to be able to inspect East-West traffic because all traffic within the VCN CIDR block is automatically routed through the internal Oracle Cloud Infrastructure subnet default gateway and this route can't be overwritten.
East-West traffic from any spoke VCN is routed from the spoke VCN LPG to the peered LPG in the hub VCN and then to the FortiGate floating IP in the trust interface. FortiGate inspects the incoming traffic and, based on the FortiGate firewall policies, it sets the destination address to either the destination host in the spoke VCN or back to the source host that sent the packet. The traffic leaves FortiGate through the trust interface and is sent through the default gateway in the trust subnet which forwards the packet to the LPG peered to the destination spoke database or application VCN.
The architecture has the following components:
- Fortinet FortiGate next-generation firewall
FortiGate is Fortinet's next-generation firewall and it provides network and security services such as threat protection, SSL inspection, and ultra-low latency for protecting internal segments and mission-critical environments. This solution is available for deployment directly form Oracle Cloud Marketplace and supports direct single root I/O virtualization (SR-IOV) for enhanced performance.
- Fortinet FortiAnalyzer
FortiAnalyzer is an optional component deployed in the FortiGate subnet that provides data-driven enterprise security insights with centralized network logging, analytics and reporting.
- Fortinet FortiManager
FortiManager is an optional component deployed in the FortiGate subnet that delivers single-pane-of-glass management across the network and provides real-time and historical views into network activity.
- Fortinet FortiADC
Distributes traffic across multiple geographic regions and dynamically rewrites content based on policy routing to ensure application and server load balancing, compression, caching, HTTP 2.0 and HTTP PageSpeed optimizations.
- Oracle E-Business Suite application tier
Composed of Fortinet FortiADC load balancer and Oracle E-Business Suite application servers and file system.
- Oracle E-Business Suite database tier
Composed of Oracle Database, but not limited to Oracle Exadata Database Cloud service or Oracle Database services.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnet
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Hub VCN
The hub VCN is a centralized network where FortiGate must be deployed and can provide connectivity to all spoke VCNs, Oracle Cloud Infrastructure services, public endpoints and clients, and on-premises data center networks. It is typically composed of the following subnets:
- Management subnet: Public subnet where primary VNIC for FortiGate is attached and is responsible for FortiGate control plane operations and general management activity.
- Untrust subnet: Public subnet containing FortiGate VNIC attachment which acts as the gateway or endpoint for ingress traffic communication from either the public internet or the customer on-premise data center.
- Trust subnet: Private subnet containing FortiGate VNIC attachment which forwards traffic to the LPG attached to the hub VCN and then forwards the traffic to the proper spoke VCN. It also receives ingress packets from spoke VCNs.
- High availability (HA) subnet: Private subnet containing FortiGate VNIC attachment dedicated for heartbeat or high availability traffic.
- Application tier spoke VCN
The application tier spoke VCN contains a private subnet to host Oracle E-Business Suite components and the Fortinet FortiADC load balancer.
- Database tier spoke VCN
The database tier spoke VCN contains a private subnet for hosting Oracle databases.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
- Network address translation (NAT) gateway
A NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Local peering gateway (LPG)
An LPG enables you to peer one VCN with another VCN in the same region. Peering means the VCNs communicate using private IP addresses, without the traffic traversing the internet or routing through your on-premises network.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- VPN Connect
VPN Connect provides site-to-site IPSec VPN connectivity between your on-premises network and VCNs in Oracle Cloud Infrastructure. The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Virtual network interface card (VNIC)
The services in Oracle Cloud Infrastructure data centers have physical network interface cards (NICs). Virtual machine instances communicate using virtual NICs (VNICs) associated with the physical NICs. Each instance has a primary VNIC that's automatically created and attached during launch and is available during the instance's lifetime. DHCP is offered to the primary VNIC only. You can add secondary VNICs after instance launch. You should set static IPs for each interface.
- Private IPs
A private IPv4 address and related information for addressing an instance. Each VNIC has a primary private IP and you can add and remove secondary private IPs. The primary private IP address on an instance is attached during instance launch and doesn’t change during the instance’s lifetime. Secondary IPs should also belong to the same CIDR of the VNIC’s subnet. The secondary IP is used as a floating IP because it can move between different VNICs on different instances within the same subnet. You can also use it as a different endpoint to host different services.
- Public IPs
The networking services define a public IPv4 address chosen by Oracle that's mapped to a private IP.
- Ephemeral: This address is temporary and exists for the lifetime of the instance.
- Reserved: This address persists beyond the lifetime of the instance. It can be unassigned and reassigned to another instance.
- Source and destination check
Every VNIC performs the source and destination check on its network traffic. Disabling this flag enables FortiGate to handle network traffic that's not targeted for the firewall.
- Compute shape
The shape of a compute instance specifies the number of CPUs and amount of memory allocated to the instance. The compute shape also determines the number of VNICs and maximum bandwidth available for the compute instance.
Recommendations
Use the following recommendations as a starting point to deploy Oracle E-Business Suite workloads on Oracle Cloud Infrastructure using Fortinet Security Fabric.
- Oracle E-Business Suite high-availability
-
Application server redundancy: Each tier contains redundant instances of Oracle E-Business Suite application servers that you can enable for various services, such as application services, batch services, or other services, to provide high availability.
-
Fault tolerance: Server nodes in each tier are deployed to different availability domains in regions with multiple availability domains. On single-availability domain regions, you can deploy server nodes into different fault domains. All instances are configured with logical host names and receive traffic from the load balancer.
-
Database redundancy: For performance and high-availability requirements, Oracle recommends that you use two-node Oracle real application cluster (RAC) database systems on Oracle Cloud Infrastructure Compute at a minimum or Oracle Database Exadata Cloud Service in Oracle Cloud Infrastructure.
-
- FortiGate high-availability
To maintain session replication and resume communication if interrupted, deploy FortiGate in active-passive high availability mode, and disable the source and destination check on the secondary VNICs for both trust and untrust interfaces. Create a dedicated interface and subnet for high-availability or heartbeat traffic.
Secondary IPs are used during the failover event. FortiGate makes calls to Oracle Cloud APIs to move these IPs from the primary to the secondary FortiGate host.
- FortiADC high-availability
Deploy FortiADC in active-active-VRRP high-availability mode, which is based on the concept of virtual router redundancy protocol (VRRP) but not the protocol itself. This mode allows configuration sync and session sync, similarly to other high-availability modes. Enable the Skip source/destination check option on the secondary VNICs for the internal interface.
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
Use a regional subnet.
Verify the maximum number of LPGs per VCN in your service limits, in case you want to extend this architecture for multiple environments and applications.
- Security lists
Use security lists to define ingress and egress rules that apply to the entire subnet.
By default, security rules are stateful, which is a mechanism used to indicate that you want to use connection tracking that matches that rule. Thus, the response of the traffic is tracked and automatically allowed back to the originating host, regardless of the egress rules.
Since FortiGate next-gen firewall inspects all traffic, you don’t need to enforce strict rules through the security lists. They can be eventually used as a second barrier of protection, but it isn’t required. Only for managing FortiGate configuration, you create a security list to allow SSH and HTTPS traffic or any additional service that might be required. For all the remaining traffic across the hub and spoke VCNs that goes through the firewall, modify the default security lists to allow ingress and egress traffic for all ports and protocols.
- FortiGate firewall policies
A firewall policy is a compartmentalized set of instructions that control the traffic flow going through the firewall. These instructions control where the traffic goes, how it’s processed, if it’s processed, and even whether it’s allowed to pass through the FortiGate. When the firewall receives a connection packet, it analyzes the packet’s source address, destination address, and service by port number. It also registers the incoming and outgoing interface. There’s also an accept or deny action associated with the policy. If the action is accept, the policy permits communication sessions. Otherwise, the policy action blocks communication sessions.
Oracle E-Business Suite requires policies with the following ports and protocol to be open:
Component Protocol Port Application tier VCN: Web Server TCP/HTTPS 443 Application web entry port TCP 8000 WebLogic admin server TCP 7001, 7002 Database tier: TNSListener TCP 1521–1522 MWA Telnet (If using MWA) TCP 10200–10205 MWA Dispatcher (If using MWA) TCP 10800 Oracle Cloud Infrastructure Email (If using Oracle email delivery) TCP 25 or 587 File Storage service (FFS)
if applicable
TCP
UDP
111, 2048, 2049, and 2050
111 and 2048
For example, for monitoring East-West traffic, you can create a policy on FortiGate trust interface to allow traffic between application and database tiers.
You can also create a policy with the destination NAT pointing to a virtual IP address to allow or restrict access to Oracle E-Business Suite from specific source IP address or networks.
- FortiGate static routes policies
Create a static route on FortiGate for each spoke VCN (destination) and set the gateway IP to the trusted subnet default gateway address, the first host IP address in the trust subnet CIDR.
For outbound connections, create a static route on FortiGate for outbound traffic and set the gateway IP to the untrusted subnet default gateway address, the first host IP address in the untrust subnet CIDR.
- Oracle Cloud Infrastructure VCN route tables
Create the following route tables for North-South and East-West traffic inspection:
VCN Name Destination Target Type Target Default Route table for subnet FortiGate FortiGate_Untrust-mgmt_route_table 0.0.0.0/0 Internet gateway <FortiGate VCN Internet Gateway> untrusted
management
FortiGate FortiGate_Trust-route_table <WebApp_Tier VCN CIDR> Local peering gateway <LPG-WebApp_Tier> FortiGate FortiGate_Trust-route_table <DB_Tier VCN CIDR> Local peering gateway <LPG-DB_Tier> FortiGate LPG–route_table 0.0.0.0/0 Private IP <FortiGate Trust VNIC Private IP (floating IP)> N/A WebApp_Tier Default route table 0.0.0.0/0 N/A <LPG-WebApp_Tier-to-Hub> N/A DB_Tier Default route table 0.0.0.0/0 N/A <LPG-DB_Tier-to-Hub> N/A - Oracle Cloud
Infrastructure VCN local peering gateways
Create the following local peering gateways (LPG) to allow North-South and East-West communication:
-
FortiGate VCN LPG setup:
Name Route Table Peer Advertised CDIR Cross-Tenancy LPG-WebApp_Tier LPG-route_table WebApp_Tier VCN CIDR No LPG-DB_Tier LPG-route_table DB_Tier VCN CIDR No - WebApp-Tier VCN LPG setup:
Name Route Table Peer Advertised CDIR Cross-Tenancy LPG-WebApp_Tier-to-Hub N/A 0.0.0.0/0 No - Database-Tier VCN LPG setup:
Name Route Table Peer Advertised CDIR Cross-Tenancy LPG-DB-Tier-to-Hub N/A 0.0.0.0/0 No
-
- FortiADC server load balancing
FortiADC must be deployed within the same VCN as the application tier in high-availability mode. It should be configured with a specific persistence method, using HTTP headers and cookies, so users can maintain a persistent session state with application servers. Using the persistence type “Insert Cookie” specifies the FortiADC to insert a cookie within the HTTP header. This cookie creates a FortiADC session ID with the client and ensures that all subsequent requests are forwarded to the same back-end Oracle E-Business Suite application server. After creating the persistence of type “Insert Cookie,” associate it with the virtual servers configuration.
Considerations
When deploying Oracle E-Business Suite workloads in the cloud using Fortinet Security Fabric to augment the native security options provided by Oracle Cloud Infrastructure, consider the following:
- Performance
FortiGate is a key component in this architecture and the selection, of the FortiGate model, Compute shape, and launch options can impact the performance of the workload. Verify the list of models with their respective specs in the FortiGate data sheet.
- Security
For high availability, FortiGate use either Oracle Cloud Infrastructure IAM Dynamic groups or API signing keys for making the API calls if failover occurs. Setup policies based on your security and compliance requirements.
- Availability
To ensure higher availability whenever there’s multiple availability domains in the region, deploy each host of your cluster on a different availability domain. Otherwise, select different fault domains to increase availability, based on your anti-affinity rules. This rule is valid for both Fortinet and Oracle products.
- Cost
Fortinet FortiGate and FortiADC are available in the Oracle Cloud Marketplace. Fortinet FortiGate is available as a bring-your-own-license (BYOL) or paid offering. Fortinet FortiADC is available only as BYOL.
Deploy
Explore More
Learn more about the features of this architecture and about related resources.