Learn About Securing and Monitoring Oracle IDCS
Oracle Functions is a serverless, highly scalable, fully managed Functions-as-a-Service platform built on Oracle Cloud Infrastructure and powered by the open-source Fn Project engine. Developers can use Oracle Functions to write and deploy code that delivers business value without worrying about provisioning or managing the underlying infrastructure. Oracle Functions is container-native, with functions packaged as Docker container images.
Architecture
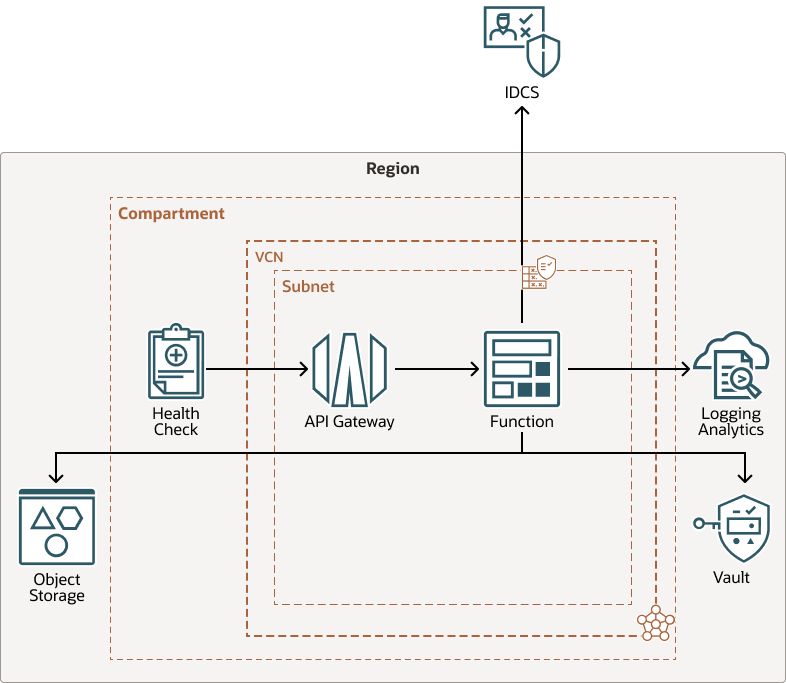
Description of the illustration secure-monitor-idcs-arch.png
secure-monitor-idcs-arch-oracle.zip
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Compartment
Compartments are cross-region logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize your resources in Oracle Cloud, control access to the resources, and set usage quotas. To control access to the resources in a given compartment, you define policies that specify who can access the resources and what actions they can perform.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- API Gateway
The API Gateway service enables you to publish APIs with private endpoints that are accessible from within your network, and which you can expose to the public internet if required. The endpoints support API validation, request and response transformation, CORS, authentication and authorization, and request limiting.
- Function
Oracle Functions is a fully managed, multitenant, highly scalable, on-demand, Functions-as-a-Service (FaaS) platform. It is powered by the Fn Project open source engine. Functions enable you to deploy your code, and either by calling it directly or by triggering it in response to events. Oracle Functions uses Docker containers hosted in the Oracle Cloud Infrastructure Registry.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can seamlessly scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- Oracle Log Analytics
Oracle Log Analytics is a fully managed SaaS regional service that provides collection, indexing, enrichment, query, visualization, and alerting for logs from any IT component running on on-premises, Oracle Cloud Infrastructure, or 3rd party cloud.
- Vault
The Vault is a key management service used to encrypt passwords and client secrets
Before You Begin
Review Deployment and Usage Recommendations
- Log Groups
Define multiple log groups to provide correct access permissions to different teams and avoid sharing sensitive data.
- Cost Management
Oracle Log Analytics service is charged on the volume of data in active and archival storage. In order to allow troubleshooting of day-to-day issues and receive the benefits of anomaly detection, pattern detection, and other machine learning capabilities, Oracle recommends that you use an active storage period of 90 days and moving logs older than 90 days to archival storage. Logs from archival stored can be quickly recalled on demand.
Review Deployment and Usage Considerations
When designing a highly available application stack in the cloud, consider the following factors:
- Performance
Query performance is based on time-range and the number of operations such as filters, group-by, and so on. For better query performance, Oracle recommends that you enrich logs with specific labels and fields at the time of ingestion.
- Security & RBAC.
Customize log source definitions to filter any personally identifiable information (PII) data, and enable geolocation enrichment. Availability: Oracle Log Analytics is a fully managed highly available SaaS service. Deploy The Oracle Log Analytics app is available as a stack in Oracle Cloud Marketplace.
Prepare IDCS Application OAuth for API Call
To call the IDCS API by using a Client ID/Secret, you need to create a custom application in IDCS and generate a Client ID/Secret. Be sure to record the IDCS URL, client ID, and secret.
Prepare the OCI Environment
Next, you need to prepare the OCI environment by ensuring you have the appropriate permissions and have the necessary resources to complete the tasks.
- Permission to manage the following types of resources in your Oracle Cloud
Infrastructure tenancy:
- VCNs
- Internet gateways
- Route tables
- Security lists
- Subnets
- Functions
- API Gateways
- Health Checks
- Enough Quota to create the following resources:
- 1 VCN
- 1 Subnets
- 1 Internet Gateway
- 1 Route rules
- 1 Function
- 1 Dynamic group
- 1 Policy
- 1 API Gateway
- 1 Health check
Learn About the Oracle-defined Dashboards
Understand the IDCS Audit Logs Dashboard
The IDCS Audit Logs dashboard summarizes audit information, by using widgets, in a single pane with charts and visualizations, based on your selection of the time range. This gives you a broad view of the various application and user activities over the selected time period.
- A total of (for application)
The number of application events and user events.
- Application events
A chart depicting the periodic record of application events
- A total of (for user)
The number of application events and user events.
- User events
A chart depicting the periodic record of user events
- Events by application by type
A tree map visualization of events grouped by event type for each application.
- Events by user by type
A tree map visualization of events grouped by event type for each user
- Repartition by application
A pie chart showing the distribution of the count of events grouped by applications.
- Repartition by event type (for application)
A pie chart grouping the count of events by event type only for the application events.
- Repartition by user
A pie chart showing the distribution of the number of events, grouped by users.
- Repartition by event type (for user)
A pie chart showing the count of events grouped by event type only for the user events.
Understand the IDCS Admin Governance Dashboard
- Link visualization of the events involving successful or failed admin action of user grouped by event type and user. Each bubble in the chart represents a group of events of a specific type by a particular user. This visualization is helpful in identifying anomalous activities.
- Tree map visualization of the events involving successful or failed admin action of user grouped by event type and user. For each user, a set of rectangles representing successful admin action events is displayed. The visualization is helpful in viewing each user’s admin activities.
- A stacked histogram view of the count of matching events distributed over the selected time period. The different colors in each bar represent the events for different users.
- A tabular analysis of events where roles were granted to specific users for specific applications.