Secure Your Workloads Running on Oracle Cloud Infrastructure With FortiGate
Oracle Cloud Infrastructure (OCI) offers best-in-class security technology and operational processes to secure its enterprise cloud services. However, security in the cloud is based on a shared responsibility model. Oracle is responsible for the security of the underlying infrastructure, such as data center facilities, hardware, and software to manage cloud operations and services. Customers are responsible for securing their workloads and configuring their services and applications securely to meet their compliance obligations.
Enterprises are turning to Oracle’s Generation 2 Cloud Infrastructure to build new applications, extend internal data centers, and ultimately take advantage of the elasticity of the public cloud. Those same enterprises are turning to Fortinet to help protect their applications and data in OCI.
Fortinet Adaptive Cloud Security solutions protect workloads and applications across on-premises data centers and cloud environments with multilayer security for cloud-based applications. The Fortinet Security Fabric spans data centers and clouds to provide a consolidated view of security posture, a single console for policy management and governance reporting, and event monitoring regardless of physical, virtual, or cloud infrastructure across private, public, and hybrid clouds.
Fortinet solutions are available in the Oracle Cloud Marketplace both as on demand and bring-your-own-license (BYOL) listings.
Architecture
This reference architecture illustrates how organizations can protect Oracle applications, like Oracle E-Business Suite and PeopleSoft, deployed in OCI using a FortiGate firewall and simplified design with a dynamic routing gateway (DRG).
To protect these traffic flows, Fortinet recommends segmenting the network using a hub and spoke topology, where traffic is routed through a transit hub and is connected to multiple distinct networks (spokes). Ensure that you have deployed a high availability FortiGate cluster. All traffic between spokes, whether to and from the internet, to and from on-premises, or to the Oracle Services Network, is routed through the hub and inspected with Fortinet’s FortiGate firewall that delivers next generation firewall capabilities for organizations of all sizes, with the flexibility to be deployed as a next-generation firewall, internal segmentation firewall, or virtual private network (VPN) gateway. It protects against cyber threats with high performance, security efficacy, and deep visibility.
Deploy each tier of your application in its own virtual cloud network (VCN), which acts as a spoke. The hub VCN contains a FortiGate active-passive, high-availability cluster, Oracle internet gateway, DRG, and Oracle Service Gateway.
This architecture can provide a highly scalable and modular design for connecting multiple spokes, where each spoke network represents one application’s tier, such as web, application, and database. It works in both one environment, such as production, test, and dev, and different infrastructures, such as regions, on-premises data center, and multicloud.
The hub VCN connects to the spoke VCNs through DRG. All spoke traffic uses route table rules to route traffic through the DRG to the hub using the VCN ingress route table to FortiGate firewall for inspection.
You can also manage the FortiGate firewall by using FortiManager. FortiManager’s Single Pane Management provides centralized management and provisioning strategy built around Fortinet’s Security Fabric that tightly integrates an organization’s network infrastructure and security architecture to apply access control, segmentation and consistent protection of devices, applications and users.
The following diagram illustrates this reference architecture.
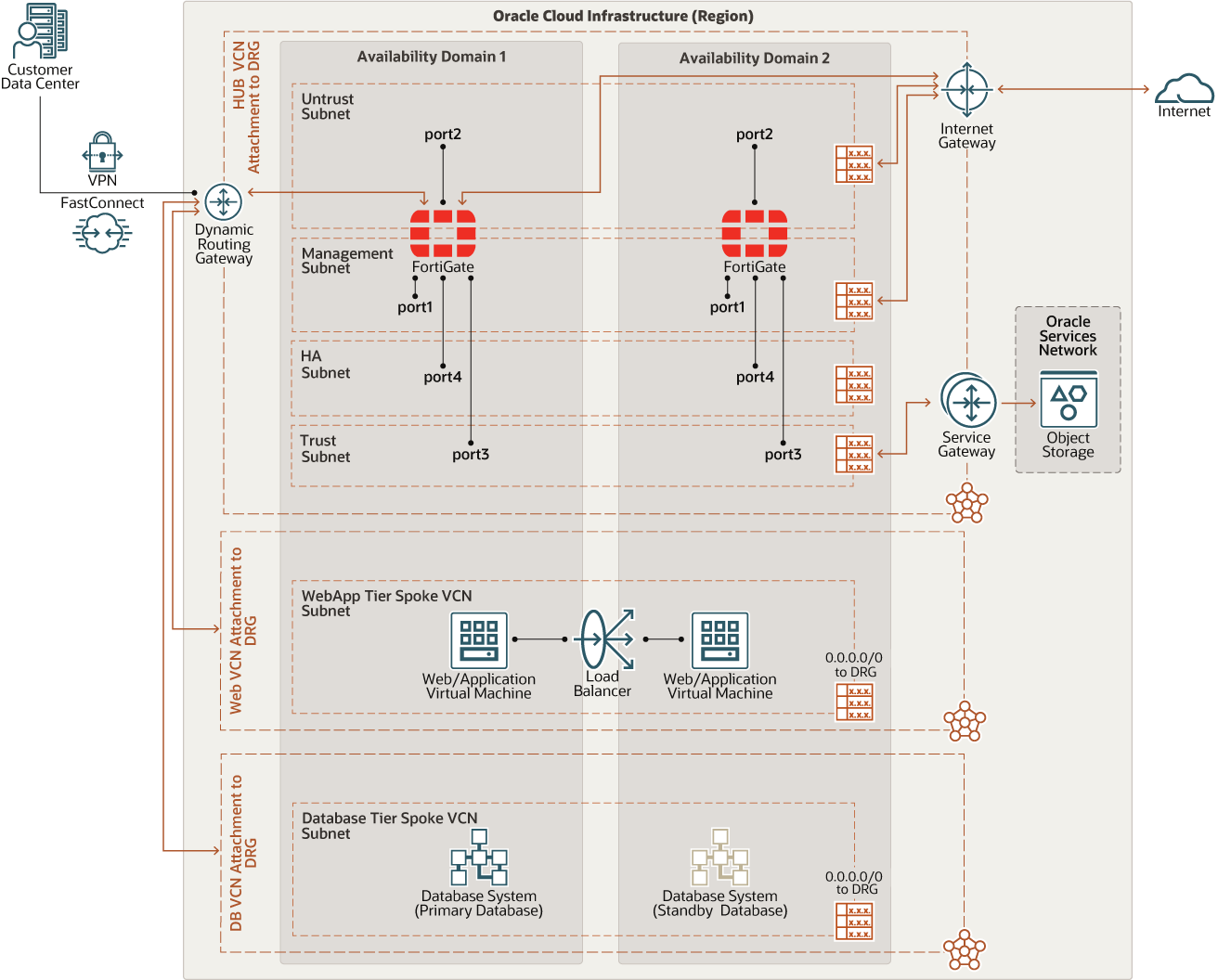
Description of the illustration fortigate-oci-arch.png
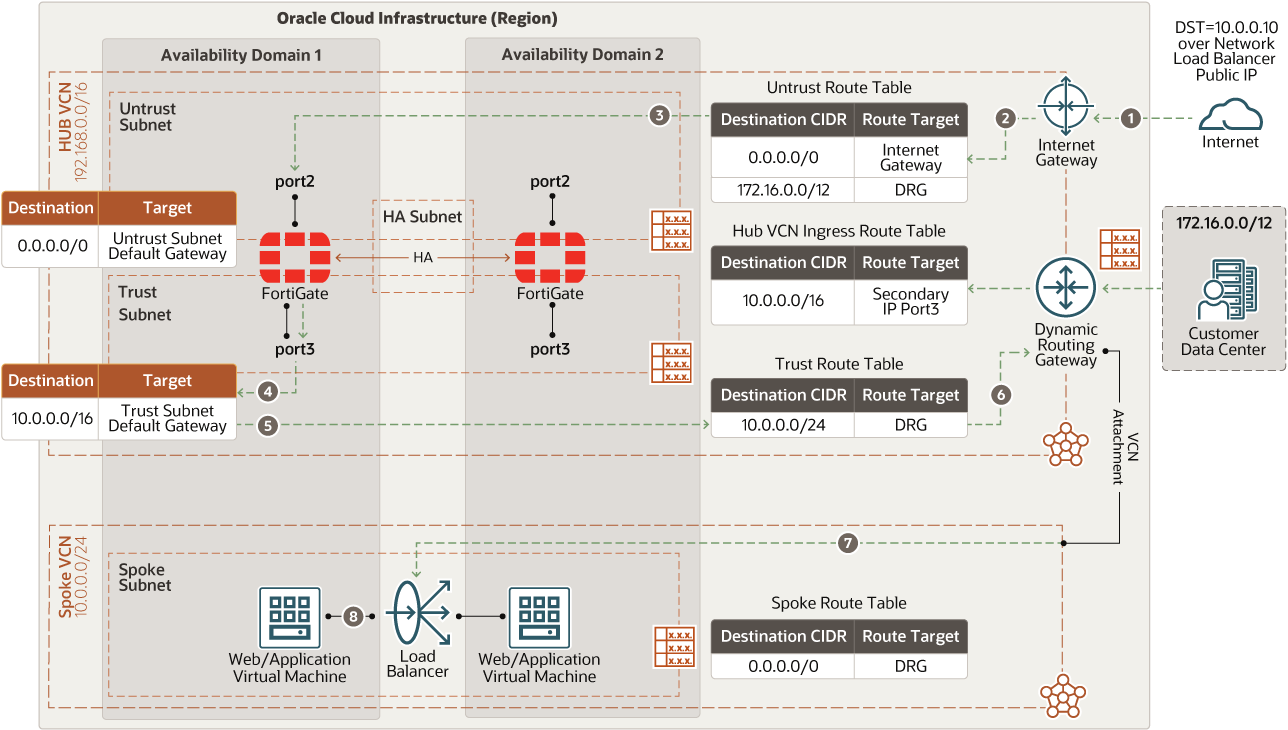
- North-south inbound traffic
The following diagram illustrates how north-south inbound traffic accesses the web application tier from the internet and from remote data centers.
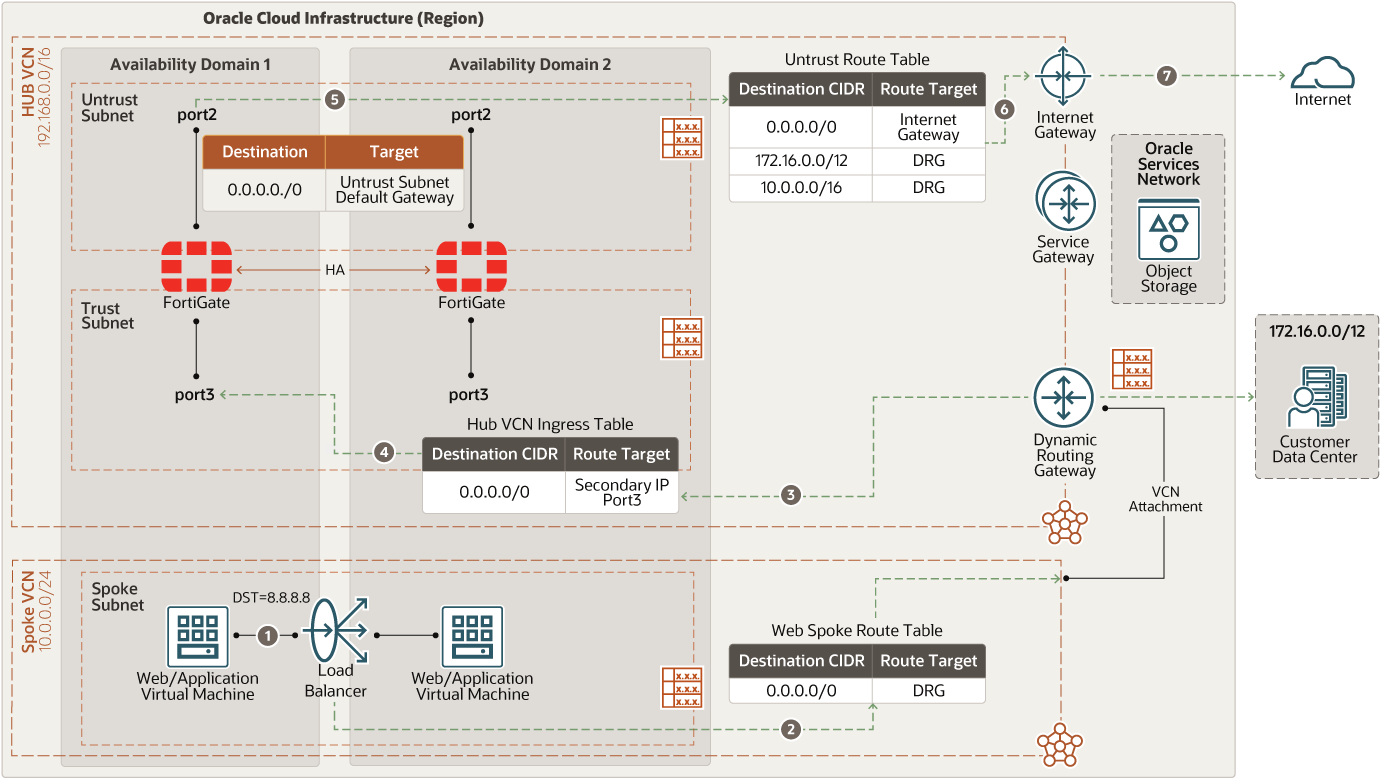
- North-south outbound traffic
The following diagram illustrates how outgoing connections from the web application and database tiers to the internet provide software updates and access to external web services.
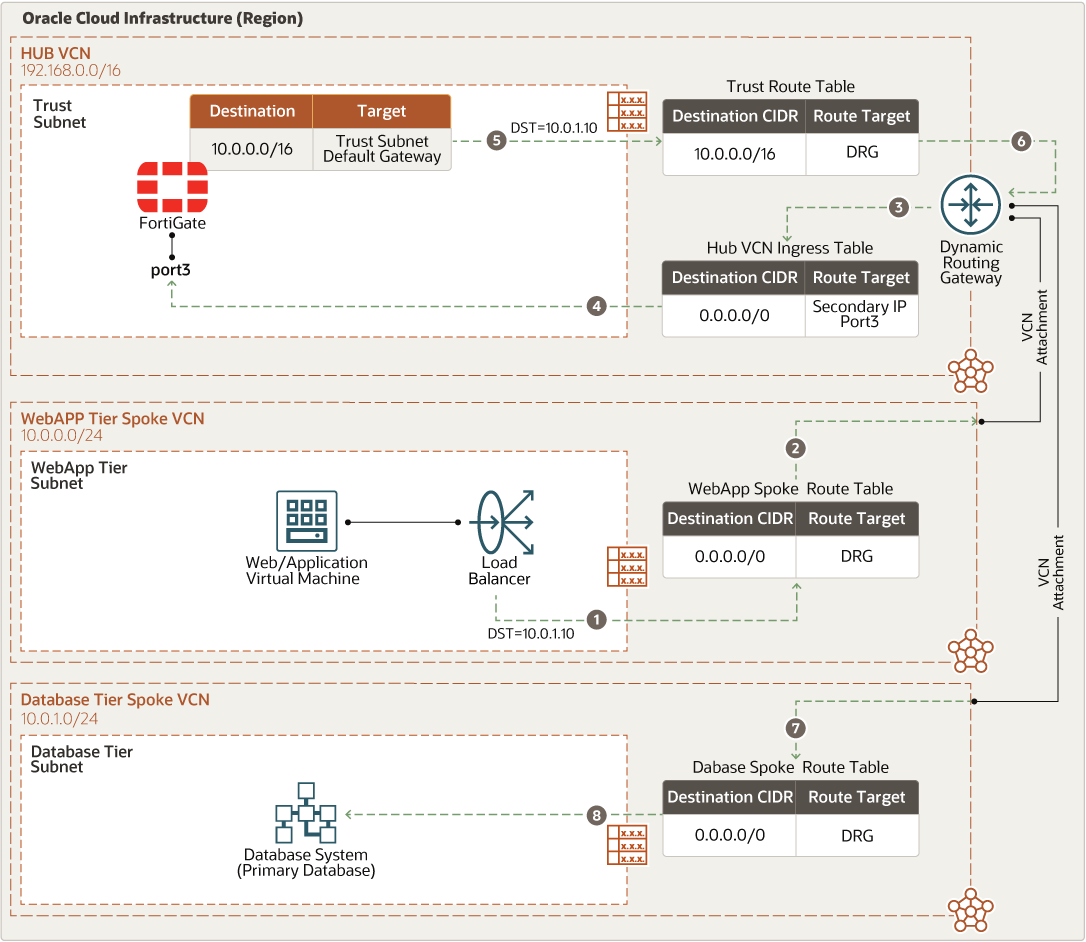
- East-west traffic (web to database)
The following diagram illustrates how traffic moves from the web application to the database tier.
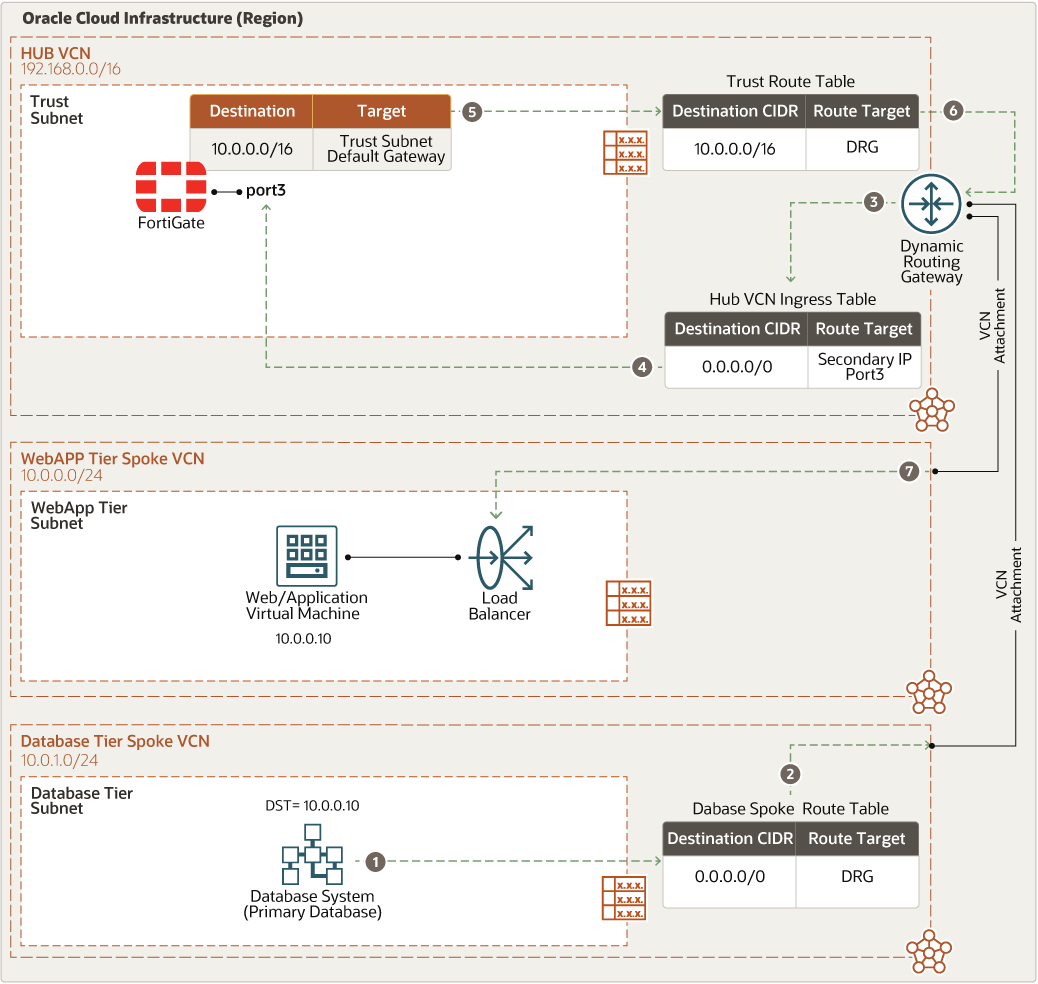
- East-west traffic (database to web)
The following diagram illustrates how traffic moves from the database tier to the web application.
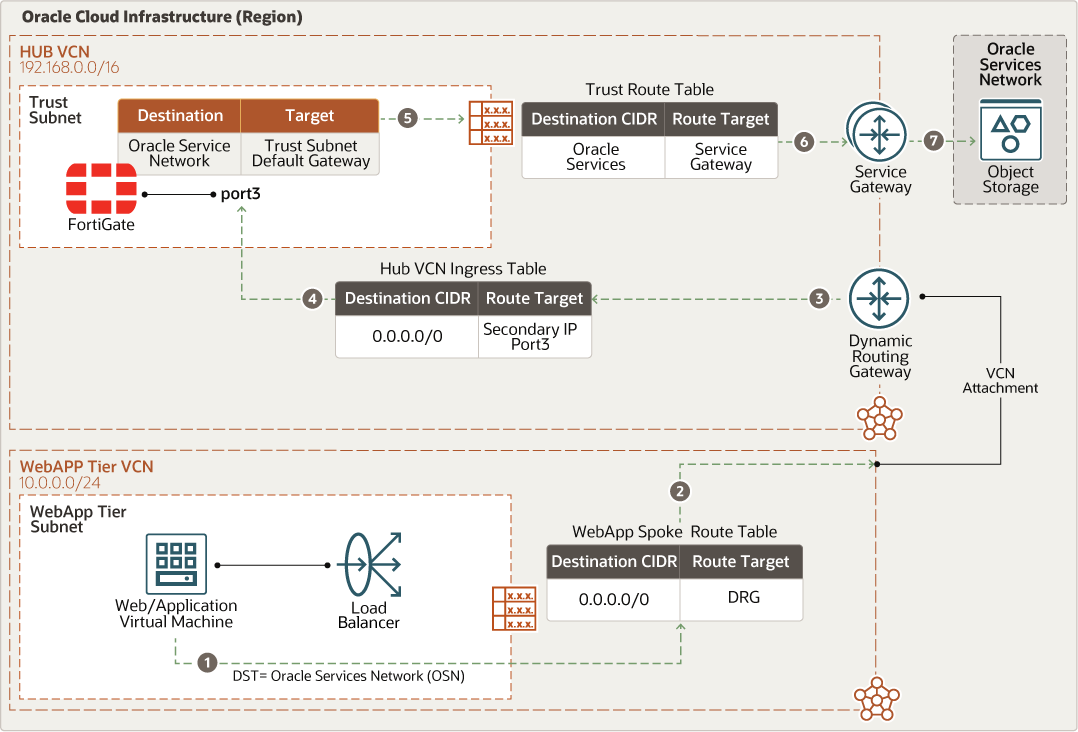
- East-west traffic (Web Application to Oracle Services Network)
The following diagram illustrates how traffic moves from the web application to the Oracle Services Network.
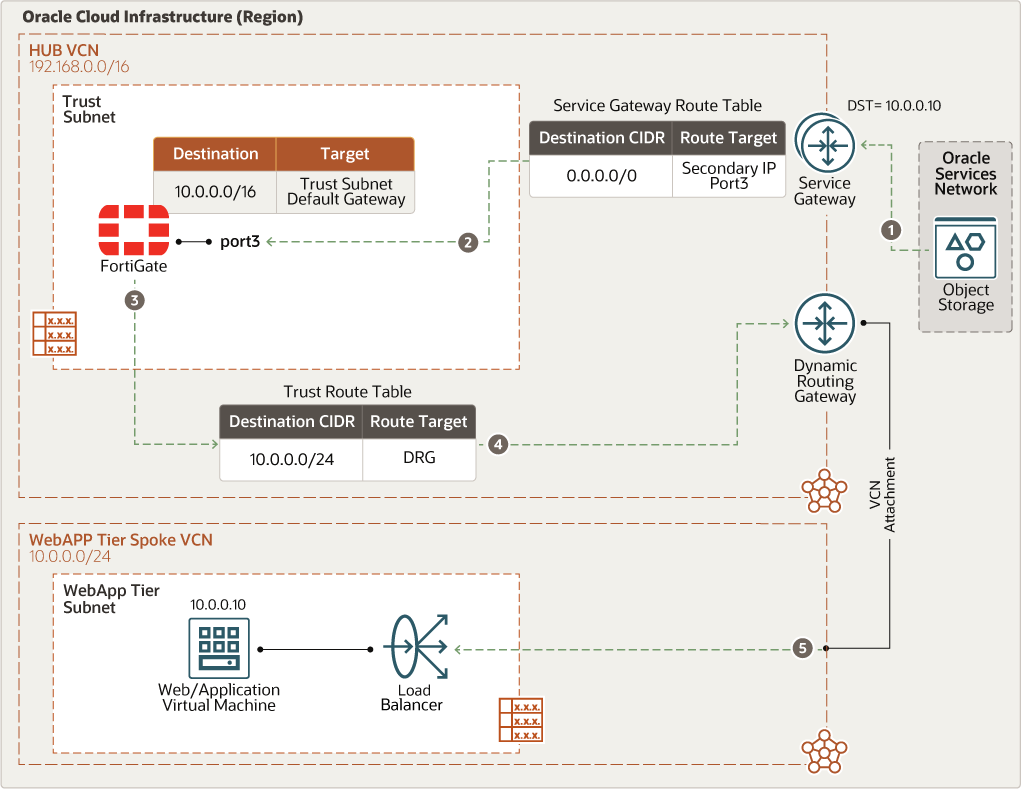
- East-west traffic (Oracle Services Network to Web Application)
The following diagram illustrates how traffic moves from the Oracle Services Network to the web application.
- Fortinet FortiGate next-generation firewall
Provides network and security services, such as threat protection, SSL inspection, and ultra-low latency, for protecting internal segments and mission-critical environments. It supports direct single root I/O virtualization (SR-IOV) for enhanced performance. FortiGate can be deployed directly from Oracle Cloud Marketplace.
- Fortinet FortiManager
Delivers single-pane-of-glass management across the network and provides real-time and historical views into network activity.
- Oracle E-Business Suite or PeopleSoft application tier
Composed of Oracle E-Business Suite or PeopleSoft application servers and the file system.
- Oracle E-Business Suite or PeopleSoft database tier
Composed of Oracle Database service , but not limited to Oracle Exadata Database Cloud service or Oracle Database.
- Region
An OCI region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnet
A VCN is a customizable, software-defined network that you set up in an OCI region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Hub VCN
The hub VCN is a centralized network where Fortinet FortiGate Firewall instances are deployed. It provides secure connectivity to all spoke VCNs, OCI services, public endpoints and clients, and on-premises data center networks.
- Application tier spoke VCN
The application tier spoke VCN contains a private subnet to host Oracle E-Business Suite or PeopleSoft components.
- Database tier spoke VCN
The database tier spoke VCN contains a private subnet for hosting Oracle databases.
- Load balancer
OCI Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the backend end.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Route table Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways. In the hub VCN, you have the following route tables:
- Management route table attached to the management subnet, which has a default route connected to internet gateway
- Untrust route table attached to the untrust subnet or default VCN for routing traffic from the hub VCN to internet or on-premises targets. This route table also has entries for each spoke VCNs CIDR block route through dynamic routing gateways.
- Trust route table attached to the trust subnet pointing to the CIDR block of the spoke VCNs through dynamic routing gateways
- High-availability route table attached to the high-availability subnet to the CIDR block where you want to send the traffic
- The hub VCN ingress route table is attached to hub VCN attachment to send any incoming traffic from spoke VCNs through the dynamic routing gateway to the FortiGate firewall trust interface floating IP
- For each spoke attached to the hub through dynamic routing gateways, a distinct route table is defined and attached to an associated subnet. That route table forwards all traffic (0.0.0.0/0) from the associated spoke VCN to dynamic routing gateways through the FortiGate firewall trust interface floating IP.
- Oracle service gateway route table attached to the Oracle service gateway for Oracle Service Network communication. That route forwards all traffic (0.0.0.0/0) to the FortiGate firewall trust interface floating IP.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
- NAT gateway
The NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between a VCN and a network outside the region, such as a VCN in another OCI region, an on-premises network, or a network in another cloud provider.
- Service gateway
The service gateway provides access from a VCN to other services, such as OCI Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- FastConnect
OCI FastConnect provides an easy way to create a dedicated, private connection between your data center and OCI. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Virtual network interface card (VNIC)
The services in OCI data centers have physical network interface cards (NICs). Virtual machine (VM) instances communicate using virtual NICs (VNICs) associated with the physical NICs. Each instance has a primary VNIC that's automatically created and attached during launch and is available during the instance's lifetime. DHCP is offered to the primary VNIC only. You can add secondary VNICs after instance launch. Set static IPs for each interface.
- Private IPs
A private IPv4 address and related information for addressing an instance. Each VNIC has a primary private IP, and you can add and remove secondary private IPs. The primary private IP address on an instance is attached during instance launch and doesn’t change during the instance’s lifetime. Secondary IPs also belong to the same CIDR of the VNIC’s subnet. The secondary IP is used as a floating IP because it can move between different VNICs on different instances within the same subnet. You can also use it as a different endpoint to host different services.
- Public IPs
The networking services define a public IPv4 address chosen by Oracle that's mapped to a private IP. Public IPs have the following types: Ephemeral: This address is temporary and exists for the lifetime of the instance. Reserved: This address persists beyond the lifetime of the instance. It can be unassigned and reassigned to another instance.
- Source and destination check
Every VNIC performs the source and destination check on its network traffic. Disabling this flag enables Fortinet FortiGate Firewalls to handle network traffic that's not targeted for the firewall.
- Compute shape
The shape of a compute instance specifies the number of CPUs and amount of memory allocated to the instance. The Compute shape also determines the number of VNICs and maximum bandwidth available for the Compute instance.
Recommendations
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
Use regional subnets. Attach your spoke VCNs as needed so you can send traffic to your hub VCN FortiGate firewalls. Define the to and from firewall route tables to each VCN attachment of dynamic routing gateways.
- Fortinet FortiGate Firewall
- Deploy an active-passive cluster and, if needed, add more instances.
- Whenever possible, deploy in distinct fault domains at a minimum or different availability domains.
- Ensure that MTU is set to 9000 on all VNICs.
- Use virtual function I/O (VFIO) interfaces.
- Fortinet FortiGate Firewall Management
- If you’re creating a deployment hosted in OCI, create a dedicated subnet for management.
- Use security lists or NSGs to restrict inbound access to ports 443 and 22 sourced from the internet for administration of the security policy and to view logs and events.
- Firewall policies
For the most up-to-date information on required security policies, ports, and protocols, refer to the firewall documentation in the Explore More section. Staying up to date ensures that you have configured required network address translation policies/security policies enabled on Fortinet FortiGate firewall instances.
Considerations
When securing Oracle E-Business Suite or PeopleSoft workloads on OCI using Fortinet FortiGate Firewall, consider the following factors:
- Performance
- Selecting the proper instance size, which is determined by the Compute shape, determines the maximum available throughput, CPU, RAM, and number of interfaces.
- Organizations need to know what types of traffic traverses the environment, determine the appropriate risk levels, and apply proper security controls as needed. Different combinations of enabled security controls impact performance.
- Consider adding dedicated interfaces for FastConnect or VPN services. Consider using large Compute shapes for higher throughput and access to more network interfaces.
- Run performance tests to validate the design can sustain the required performance and throughput.
- Security
Deploying Fortinet FortiManager in OCI allows for centralized security policy configuration and monitoring of all physical and virtual Fortinet FortiGate firewalls.
- Availability
Deploy your architecture to distinct geographic regions for greatest redundancy. Configure site-to-site VPNs with relevant organizational networks for redundant connectivity with on-premises networks.
- Cost
Fortinet FortiGate offers pay-as-you-go or bring-your-own-license (BYOL) listings in Oracle Cloud Marketplace, and FortiManager is available in BYOL listings in Oracle Cloud Marketplace.
Deploy
- Deploy using the stack in Oracle Cloud
Marketplace:
- Set up the required networking infrastructure as shown in the architecture diagram.
- Deploy the application (Oracle E-Business Suite or PeopleSoft) on your environment.
- Oracle Cloud Marketplace has multiple listings for different configurations and licensing requirements. For example, the following listings feature bring your own licensing (BYOL). For each listing you choose, click Get App and follow the on-screen prompts:
- Deploy using the Terraform code in GitHub:
- Go to GitHub.
- Clone or download the repository to your local computer.
- Follow the instructions in the
READMEdocument.
Explore More
Learn more about using FortiGate with Oracle Cloud Infrastructure.
Oracle Cloud Infrastructure reference materials: :
- Best practices framework for Oracle Cloud Infrastructure
- Oracle Cloud Infrastructure Security Overview
- Learn about deploying Oracle E-Business Suite on Oracle Cloud Infrastructure
- Learn about deploying PeopleSoft on Oracle Cloud Infrastructure
- Learn about using Dynamic Routing Gateway to Steer Traffic to Firewall
- Deploy FortiGate Firewalls and Secure your workloads on OCI Workshop