Deploy the Spring Boot Framework on Oracle Cloud Infrastructure with MySQL Database Service
Set up a multitier topology in the cloud that includes the Spring Boot framework for deploying a highly available application that uses a MySQL database.
Spring Boot is an open source, Java-based framework that you can use to create production grade applications. Spring Boot simplifies the deployment of applications with minimal configuration and customization and includes third-party libraries to streamline the process.
Architecture
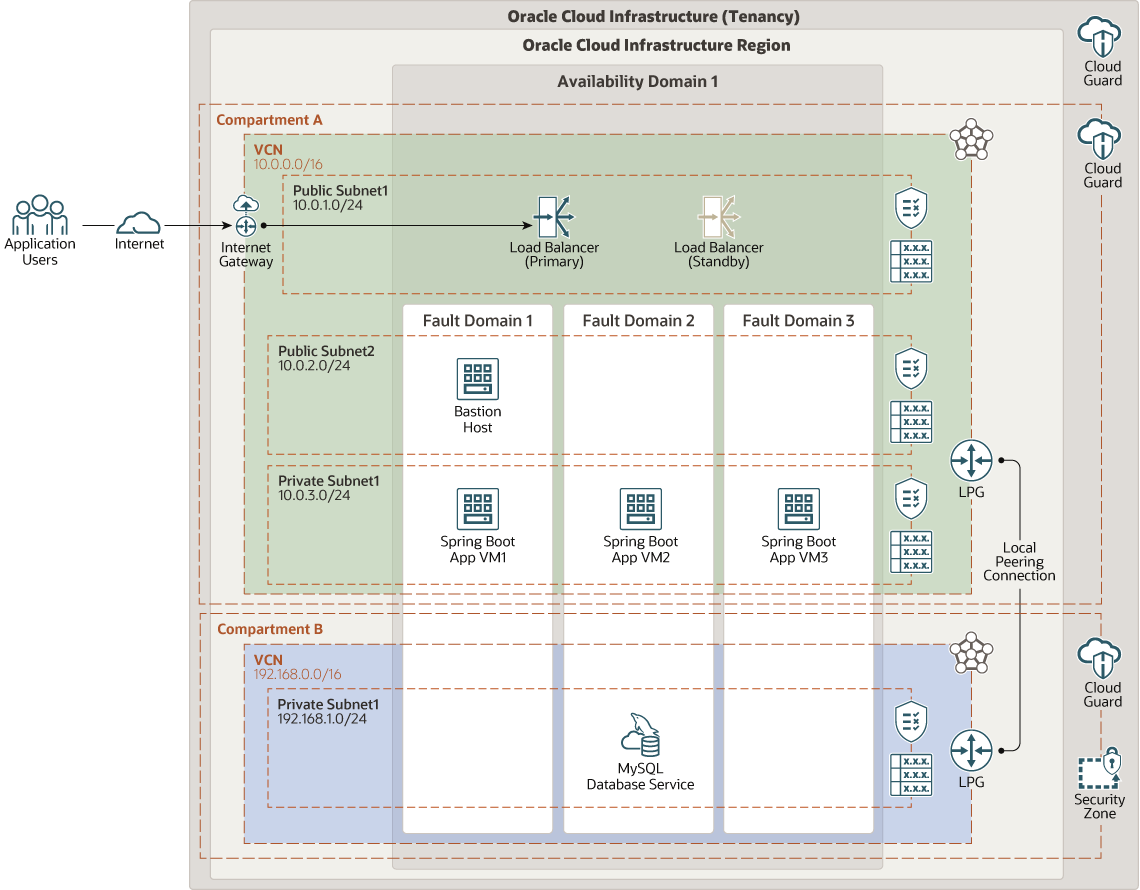
This multitier reference architecture includes the infrastructure resources and the Spring Boot framework used to deploy highly available applications on Oracle Cloud Infrastructure.
The architecture deploys a load balancer, a bastion host, three virtual machines (VMs) where the application is installed, and Oracle MySQL Database Service.
The architecture includes two compartments, both of which have Cloud Guard enabled to provide maximum security based on Oracle's security best practices. In addition, the compartment where Oracle MySQL Database Service is deployed is a security zone compartment.
Components are located in different subnets and fault domains to provide high availability. Oracle MySQL Database Service is accessed only through the bastion host and the application VMs are accessed through the load balancer.
The following diagram illustrates this architecture.
springboot-mysql-oci-oracle.zip
The architecture has the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domains
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Security lists
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Bastion
Choose between bastion host and Oracle Cloud Infrastructure Bastion options:
-
The bastion host is a compute instance that serves as a secure, controlled entry point to the topology from outside the cloud. The bastion host is provisioned typically in a demilitarized zone (DMZ). It enables you to protect sensitive resources by placing them in private networks that can't be accessed directly from outside the cloud. The topology has a single, known entry point that you can monitor and audit regularly. So, you can avoid exposing the more sensitive components of the topology without compromising access to them.
-
Oracle Cloud Infrastructure Bastion provides restricted and time-limited secure access to resources that don't have public endpoints and that require strict resource access controls, such as bare metal and virtual machines, Oracle MySQL Database Service, Autonomous Transaction Processing (ATP), Oracle Container Engine for Kubernetes (OKE), and any other resource that allows Secure Shell Protocol (SSH) access. With Oracle Cloud Infrastructure Bastion service, you can enable access to private hosts without deploying and maintaining a jump host. In addition, you gain improved security posture with identity-based permissions and a centralized, audited, and time-bound SSH session. Oracle Cloud Infrastructure Bastion removes the need for a public IP for bastion access, eliminating the hassle and potential attack surface when providing remote access.
-
- Load balancers
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Cloud Guard
You can use Oracle Cloud Guard to monitor and maintain the security of your resources in Oracle Cloud Infrastructure. Cloud Guard uses detector recipes that you can define to examine your resources for security weaknesses and to monitor operators and users for risky activities. When any misconfiguration or insecure activity is detected, Cloud Guard recommends corrective actions and assists with taking those actions, based on responder recipes that you can define.
- Security zone
Security zones ensure Oracle's security best practices from the start by enforcing policies such as encrypting data and preventing public access to networks for an entire compartment. A security zone is associated with a compartment of the same name and includes security zone policies or a "recipe" that applies to the compartment and its sub-compartments. You can't add or move a standard compartment to a security zone compartment.
- Local peering gateway (LPG)
An LPG enables you to peer one VCN with another VCN in the same region. Peering means the VCNs communicate using private IP addresses, without the traffic traversing the internet or routing through your on-premises network.
- Database
This architecture uses MySQL Database Service, which runs on an E-shape VM.
Recommendations
Your requirements might differ from the architecture described here. Use the following recommendations as a starting point.
- Cloud Guard
Clone and customize the default recipes provided by Oracle to create custom detector and responder recipes. These recipes enable you to specify what type of security violations generate a warning and what actions are allowed to be performed on them. For example, an Object Storage bucket can have visibility set to public.
Apply Cloud Guard at the tenancy level to cover the broadest scope and to reduce the administrative burden of maintaining multiple configurations.
You can also use the Managed List feature to apply certain configurations to detectors.
- Security Zones
For resources that require maximum security, Oracle recommends that you use security zones. A security zone is a compartment associated with an Oracle-defined recipe of security policies that are based on best practices. For example, the resources in a security zone must not be accessible from the public internet and they must be encrypted using customer-managed keys. When you create and update resources in a security zone, Oracle Cloud Infrastructure validates the operations against the policies in the security-zone recipe, and denies operations that violate any of the policies.
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
Use regional subnets.
- Security lists
Use security lists to define ingress and egress rules that apply to the entire subnet.
- Virtual machine
The VMs are distributed across multiple fault domains for high availability. Use VM.Standard.E3.Flex, four-core OCPU, 64-GB memory, and 4-Gbps network bandwidth (Oracle Linux 7).
- Bastion host
Use VM.Standard.E3.Flex shape with 1 OCPU and 2 Gig of RAM. Alternatively, use Oracle Cloud Infrastructure Bastion service.
- Load balancers
The load balancers distribute incoming traffic to the application VMs. When you create the load balancer, you can either select a predefined shape that provides a fixed bandwidth, or specify a custom (flexible) shape where you set a bandwidth range and let the service scale the bandwidth automatically based on traffic patterns. With either approach, you can change the shape at any time after creating the load balancer.
- Database service
Use VM.Standard.E2.8, which provides sufficient CPU and memory for the application.
Considerations
- Scalability
You can scale the application servers vertically by changing the shape of the compute instances. A shape with a higher core count provides more memory and network bandwidth. If you need more storage, increase the size of the block volumes attached to the application server.
- Availability
Fault domains provide the best resilience for workloads deployed within a single availability domain. For high availability in the application tier, deploy more application servers as needed.
- Cost
In the application tier, select the compute shape based on the cores, memory, and network bandwidth that your application needs. You can start with a four-core shape for the application server. If you need more performance, memory, or network bandwidth, you can change to a larger shape.
- Backups
Oracle Cloud Infrastructure automatically backs up MySQL database. The Oracle Cloud Infrastructure Object Storage bucket that you create stores manual backups and retains them for 60 days.
Oracle Cloud Infrastructure Block Volumes lets you create point-in-time backups of data on a block volume. You can restore these backups to new volumes at any time. You can also use the service to make a point-in-time, crash-consistent backup of a boot volume without application interruption or downtime. Boot and block volumes have the same backup capabilities.
- Security
For access control, use policies to restrict who can access your resources in the cloud and the actions that they can perform.
For network security, security lists and network security groups (NSG) use security rules to control traffic at the packet level. An NSG consists of a set of ingress and egress security rules that apply only to a set of VNICs of your choice in a single VCN. For example, you can choose to apply rules to all of the compute instances that act as web servers in the web tier of a multitier application in your VCN.
NSG security rules function the same as security list rules. However, for an NSG security rule's source or destination, you can specify an NSG instead of a CIDR block. So, you can easily write security rules to control traffic between two NSGs in the same VCN or traffic within a single NSG. When you create a database system, you can specify one or more NSGs. You can also update an existing database system to use one or more NSGs.
Deploy
To deploy this reference architecture, create the required resources in Oracle Cloud Infrastructure, and then install the Spring Boot Framework.
Change Log
This log lists only the significant changes:
| November 18, 2021 |
|
| June 28, 2021 | Updated the target for the Deploy button in the Deploy section. |
| February 8, 2021 |
Updated the Deploy section to deploy infrastructure resources using Terraform, either by clicking the Deploy button to automatically deploy resources through the Oracle Cloud Infrastructure Resource Manager, or by downloading the Terraform code and then using the Terraform command line interface to deploy the resources. Updated the load balancer recommendations to include either a predefined shape or a flexible shape where you set a bandwidth range and let the service scale the bandwidth automatically based on traffic patterns. |