Enable OCI Vulnerability Scanning to Protect Your Hosts
To ensure the hosts you deploy to Oracle Cloud Infrastructure (OCI) are free of vulnerabilities today and in the future, you should enable the Vulnerability Scanning service (VSS) and, in each of your regions, create targets for all your VM and Bare Metal instances.
Use VSS's reporting features to review the current risk levels of your hosts in each region, or view these findings and take actions with Cloud Guard.
Once the hosts have been scanned, you can sort and filter to find the most impacted hosts or find the hosts they are in charge of. The service will gather the latest Common Vulnerabilities and Exposures (CVE) from the open-source feeds from the National Vulnerability Database - NVD and RedHat. It then matches this data against the installed packages on the hosts to allow the service to report on the security risk and provide links to National Vulnerability Database (NVD) with details of what patches need to occur.
The Common Vulnerability Scoring Systems (CVSS) base scores of each matched CVE are mapped to risk levels (Critical, High, Medium, Low and None) used in Oracle Cloud Guard. This matching mirrors the way NVD maps the CVSS v3.0 ratings to risk severity.
All findings will flow to the event and logging streams and for use by other systems, for example, a SIEM. You can also view the findings in Cloud Guard, where you can decide which risk level should be marked as a problem against a host or which open ports should also be a problem against a host.
Architecture
This architecture describes how VSS can provide critical information about your hosts and their targets.
VSS scans your hosts by using our plugin, which runs quietly on each host with the Oracle Cloud Agent. The service also pings all the public IPs to gather port information, allowing VSS to gather these findings for reporting from our service and forwards them to logging, events, and Cloud Guard.
Oracle Cloud Infrastructure Registry (OCIR) will leverage the VSS container scanner engine to find vulnerable packages in use by the images scanned. Currently this container scanning can only be turned on and viewed in OCIR.
VSS is not actively scanning your hosts until you perform the configuration steps listed under Enablement in the "Considerations" topic. You can target your hosts for scanning as described here.
This architectural diagram illustrates how to configure Vulnerability Scanning regionally and then view the problems in Cloud Guard in a global region.
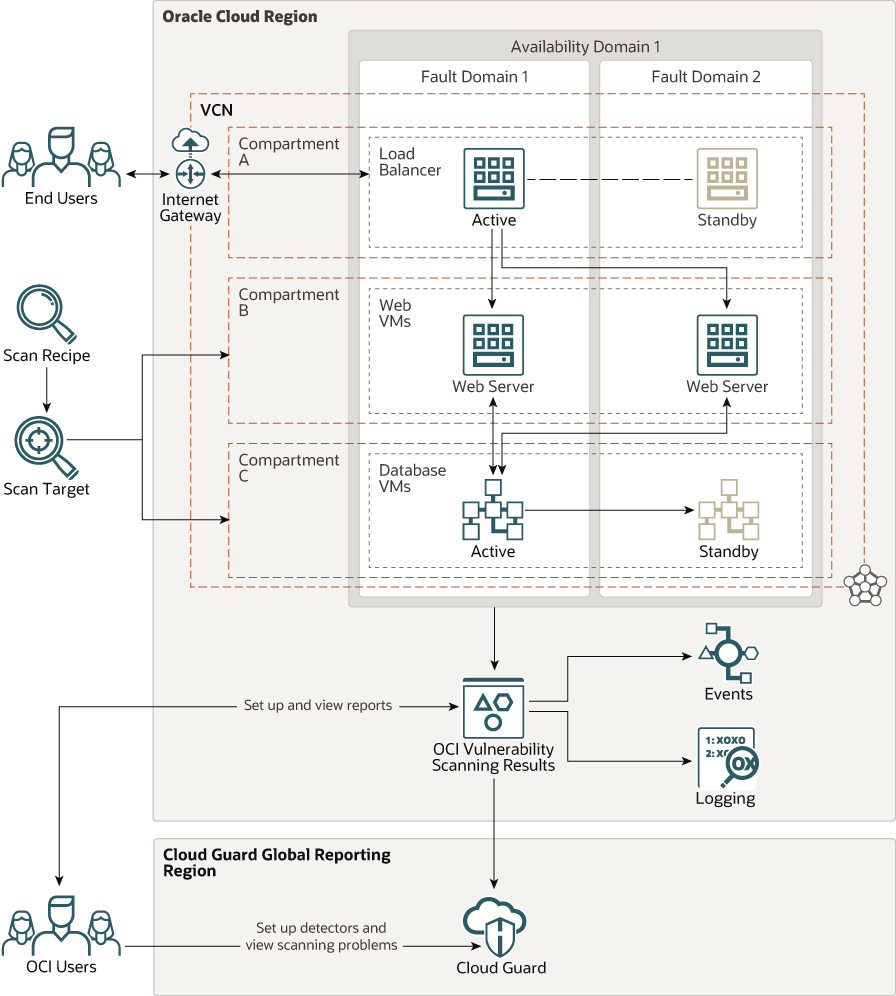
Description of the illustration vulnerability_scan_arch.png
The OCI customer creates targets to scan all Compute instances in compartments B and C. Those Virtual Machines (VMs) are periodically scanned for CVEs, CIS benchmarks and open ports. Customers can then view the findings using the Scanning Service's reports or in the Cloud Guard regional reporting console. Typically, DEV and QA teams want to view the results of their specific compartments before they deploy their applications to the production compartment. This allows them to patch all of their servers in the pre-production compartments, test that everything is working correctly and verify that the vulnerabilities are resolved before the application is released to the production servers. The operations group will typically monitor the problems in Cloud Guard from all regions and then notify the various teams that they need to take corrective actions on their compartments as they find serious problem that need attention.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domains
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Scan Recipes
Use scan recipes to define the amount and type of scanning that you want to occur against your hosts. By default, scanning is performed daily and utilizes the host's agent to look for detailed problems.
- Scan TargetsUse scan targets to define where you want the scanning to occur; either all hosts inside a compartment and all its sub-compartment or a set of specific hosts. The Scanning Service will support these OCI Compute base images:
- Oracle Linux
- CentOS
- Ubuntu
- Windows ServerOracle Linux, CentOS, Ubuntu and Windows Server
- Cloud Guard
Use Oracle Cloud Guard to monitor and maintain the security of your resources in OCI. You define the detector recipes that Cloud Guard uses to examine your resources for security weaknesses and to monitor operators and users for risky activities. When any misconfiguration or insecure activity is detected, Cloud Guard recommends corrective actions and assists with taking those actions, based on responder recipes that you can define.
Recommendations
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
- Scan Recipe
When you create a scan recipe, enable agent-based scanning (default) so that VSS has access to all the host information possible; otherwise VSS can only inspect information about open ports on your public IPs.
- Scan TargetCreate a target for your entire tenancy by specifying your root compartment. This automatically includes all resources in the root compartment and all sub-compartments.
Note:
If you create targets for specific compartments and/or specific Compute instances, VSS will not scan any new compartments and instances unless you explicitly add them to targets.
Considerations
When enabling VSS, consider the following
- Performance
Hosts and ports are scanned at least once a day.
- Security
Learn about vulnerabilities, open ports and poor configurations on your hosts as soon as possible. Use the VSS console to track the trends while also getting alerts from Cloud Guard.
- Availability
VSS is available in all regions.
- Cost
There is no cost for using the OCI plugin on every host and port scanning of your public facing IPs.
- Limits
By default you can create up to 100 scan recipes and 200 scan targets. If you have a need beyond these sizes then you will need to talk to customer service about possibly increasing your scanning limits.
- EnablementVSS is available to be used in all regions, but customers will need to enable a few things to get their hosts scanned. Once the following steps are completed, customers will then monitor for vulnerabilities and poor configurations in VSS or GC. The customer will need to:
- Create IAM policies that allow the Scanning service to run our plugin and gather information about the Compute instances.
- Create IAM policies that allow their administrators to create and manage scan recipes and targets.
- Create one or more Scan Recipes.
- Create one or more Scan Targets.
- Configure the scanning detectors in Cloud Guard so that
users are notified about host vulnerabilities.
- Configure the CVE risk level that translates to a problem in Cloud Guard and what the risk level should be for that given problem.
- Specify which open ports should be considered a problem in Cloud Guard and what the risk level should be for that given problem.
-
IAM PoliciesVSS needs these IAM polices:
allow group Your Group to manage vss-family in tenancy allow service vulnerability-scanning-service to read compartments in tenancy allow service vulnerability-scanning-service to manage instances in tenancy allow service vulnerability-scanning-service to read vnics in tenancy allow service vulnerability-scanning-service to read vnic-attachments in tenancy