Forensic Analysis of Network Traffic with VTAP
Virtual Test Access Point (VTAP) is an Oracle Cloud Infrastructure (OCI) feature that provides packet capture of your network traffic and collects the data required for sophisticated network analysis.
Packet capture has evolved over time. As a theory, it's the practice of capturing network traffic for review and analysis. In practical terms, this means capturing all possible data egress and ingress routes for any area showing suspicious activity.
VTAP provides an OCI native service for full network capture and analysis. In OCI, the source VTAP captures traffic based on a capture filter, encapsulates it with the VXLAN protocol, and mirrors it to the designated target. You can monitor and analyze the mirrored traffic in real time with standard traffic analysis tools, or you can store the traffic for more comprehensive forensic analysis at a later date.
Architecture
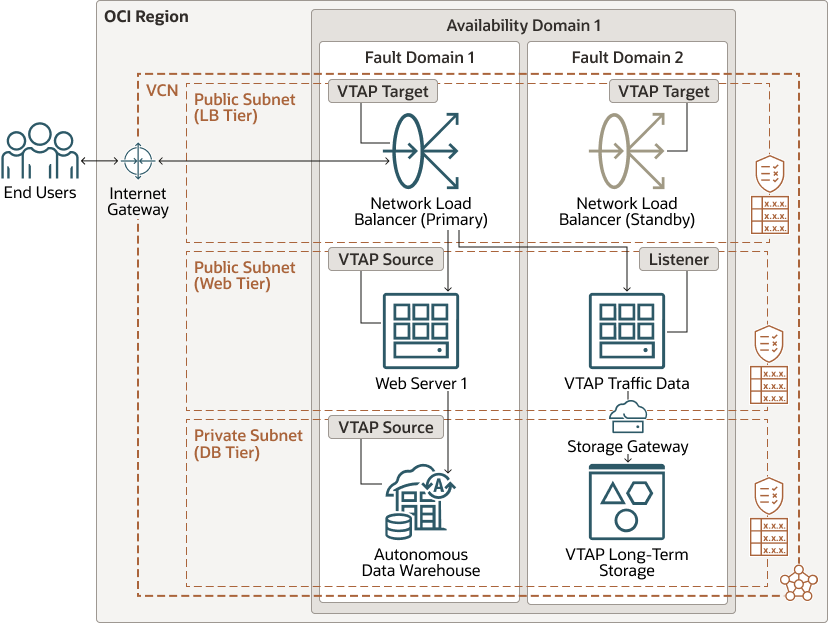
This architecture uses VTAP to capture network traffic for the virtual machine VNIC and the Autonomous Data Warehouse. VTAP data flows to the network load balancer and is routed to the VTAP Traffic Data compute instance.
The following diagram illustrates this reference architecture.
vtap-forensic-analysis-oracle.zip
VTAP can mirror traffic from the following sources:
- A single compute instance VNIC in a subnet
- A load balancer as a service (LBaaS)
- An OCI database
- An exadata VM cluster
- An Autonomous Data Warehouse, through a private endpoint
In this architecture, we are mirroring traffic from the web server VNIC and from the Autonomous Data Warehouse. VTAP captures all packets going through the VNIC.
VTAP traffic captures stream to the network load balancer, which directs it to a compute instance. A listener, such as a network forensics tool, picks up the stream and allows you to analyze the data and reconstruct client/server interactions, even when employed in a clustered topology. This gives forensic analysis teams a greater breadth of data with nearly instantaneous setup, as well as real time access and analysis.
From your forensics tool, you can also send the captured data to OCI Object Storage through the Storage Gateway. Storage Gateway then sets appropriate lifecycle and access policies on the data, ensuring that no data is modified, lost, or corrupted.
OCI Object Storage satisfies regulatory and legal requirements for long-term records retention, both in terms of high durability and high availability. You can also ensure that no data is manipulated during the forensic process by enabling policies such as object locking and immutable object and bucket types. You can use standard OCI File Storage to access the objects with other tools that require more traditional hierarchical file system layouts.
This reference architecture contains the following components.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domains
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Flexible Network Load Balancing service (Network Load Balancer)
The Network Load Balancer provides automated traffic distribution from one entry point to multiple backend servers in your virtual cloud network (VCN). It operates at the connection level and load balances incoming client connections to healthy backend servers based on Layer 3/Layer 4 (IP protocol) data.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
- Network address translation (NAT) gateway
A NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Autonomous Data
Warehouse
Oracle Autonomous Data Warehouse is a self-driving, self-securing, self-repairing database service that is optimized for data warehousing workloads. You do not need to configure or manage any hardware, or install any software. Oracle Cloud Infrastructure handles creating the database, as well as backing up, patching, upgrading, and tuning the database.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can seamlessly scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
Recommendations
- Traffic priority
Enable VTAP priority mode. This ensures monitored traffic and VTAP mirrored traffic are given equal priority. When you enable this mode, mirrored traffic might cause some of the monitored traffic to be dropped whenever the source is congested. If this packet loss is detected, you can either disable priority mode or upgrade the source shapes to accommodate more bandwidth.
- Forensics and auditing
Configure your object storage to ensure that your data can be audited reliably. Best practices include audit logs and using md5 sums to validate that your data has not been tampered with.
Considerations
When enabling VTAP data collection on your network, consider these setup options.
- VTAP Availability
The VTAP feature is being rolled out globally, but may not be immediately available in all geographies. We recommend you confirm that it is available for your region before you plan to use it.
- Cost
There is no charge for VTAP. However, VTAP increases the traffic on the VNIC, which does incur a charge. You can reduce the resources required by applying a VTAP capture filter that is specific to the application you're analyzing, such as HTTP/80 or HTTPS/443.