Set up WordPress with MySQL Database and Matomo Analytics using Arm-based Ampere A1 Compute resources
Take advantage of the flexibility and cost benefits of hosting your WordPress web pages and blogs using Arm-based Ampere A1 compute shapes in the Oracle Cloud Free Tier on Oracle Cloud Infrastructure.
The user-friendly features of the WordPress platform helps make it one of the most popular content management systems (CMS). Combine WordPress with the following to make it as powerful and fast as it is friendly:
- Arm-based Ampere A1 compute for balanced performance and optimal price point with containerized workloads and web applications
- MySQL Database for open-source storage of relational data for content and analytics
- Matomo analytics for open-source, client-owned data analytics
Architecture
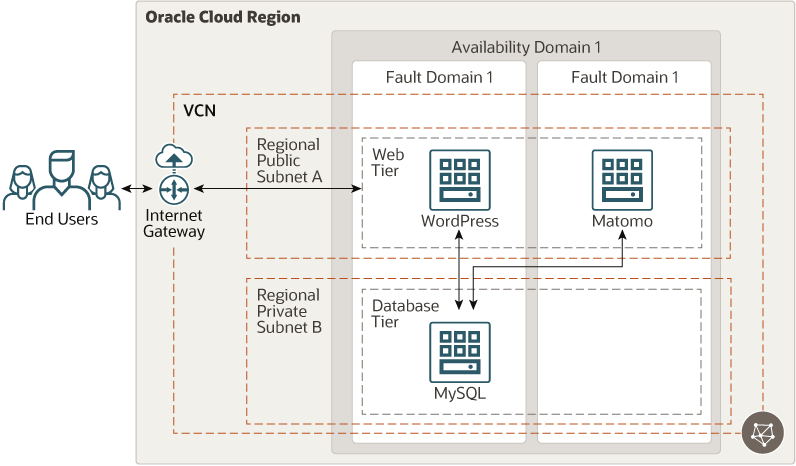
This reference architecture includes the Terraform code to deploy a WordPress content management system, Matomo analytics, and MySQL Database on Oracle Cloud Infrastructure.
The following diagram illustrates this architecture.
The architecture has the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domains
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Network security group (NSG)
NSGs act as virtual firewalls for your cloud resources. With the zero-trust security model of Oracle Cloud Infrastructure, all traffic is denied, and you can control the network traffic inside a VCN. An NSG consists of a set of ingress and egress security rules that apply to only a specified set of VNICs in a single VCN.
- MySQL Database
In this reference architecture, MySQL Database is deployed on a virtual machine, not in a cluster, and is used to host the content information for WordPress and Matomo analytics.
- WordPress
WordPress content management system (CMS) enables you to build a fully functional blog site or a general-purpose website. This architecture uses a regular compute instance to deploy the WordPress CMS engine.
- Compute
The Oracle Cloud Infrastructure Compute service enables you to provision and manage compute hosts in the cloud. You can launch compute instances with shapes that meet your resource requirements for CPU, memory, network bandwidth, and storage. After creating a compute instance, you can access it securely, restart it, attach and detach volumes, and terminate it when you no longer need it.
- Matomo
Matomo is a web analytics platform that you can use to collect and analyze information from your WordPress implementation.
Recommendations
Your requirements might differ from the architecture described here. Use the following recommendations as a starting point.
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
Use regional subnets.
- Security lists
Use security lists to define ingress and egress rules that apply to the entire subnet.
- Virtual machine
The virtual machines (VMs) are distributed across multiple fault domains for high availability. Use VM.Standard.A1.Flex, 1 OCPU, 6 GB memory, and 1-Gbps network bandwidth.
- Compute shapes
This architecture uses an Oracle Linux 8 OS image with an Ampere A1 shape for WordPress CMS, Matomo, and MySQL. If your application’s resource needs are different, you can choose a different shape.
- MySQL Database
In this architecture, WordPress CMS stores the relational data in MySQL Database. We recommend using the latest version of MySQL.
Considerations
When deploying WordPress on Oracle Cloud Infrastructure, consider the following for scalability, security, and availability:
- WordPress scalability
You can scale your WordPress CMS by using the instance pool and autoscaling features.
Instance pools let you provision and create multiple compute instances based on the same configuration within the same region.
Autoscaling lets you automatically adjust the number of compute instances in an instance pool based on performance metrics, such as CPU utilization. Autoscaling helps you provide consistent performance for users during periods of high demand and helps you reduce your costs during periods of low demand.
- Application availability
Fault domains provide the best resilience within an availability domain. If you need higher availability, consider using multiple availability domains or multiple regions.
- Security policies
Use policies to restrict who can access which of your Oracle Cloud Infrastructure resources and how they can access them.
- Network security
The Networking service offers two virtual firewall features that use security rules to control traffic at the packet level: security lists and network security groups (NSGs). An NSG consists of a set of ingress and egress security rules that apply only to a set of VNICs of your choice in a single VCN. For example, you can choose all the compute instances that act as web servers in the web tier of a multitier application in your VCN.
NSG security rules function the same as security list rules. However, for an NSG security rule's source or destination, you can specify an NSG instead of a CIDR block. So, you can easily write security rules to control traffic between two NSGs in the same VCN or traffic within a single NSG. When you create a database system, you can specify one or more NSGs. You can also update an existing database system to use one or more NSGs.
Deploy
The Terraform code for this reference architecture is available on GitHub. You can pull the code into Oracle Cloud Infrastructure Resource Manager with a single click, create the stack, and deploy it. Alternatively, you can download the code from GitHub to your computer, customize the code, and deploy the architecture by using the Terraform command line interface (CLI).