Firewall Secure Solution Scenarios
The following diagrams show possible scenarios of the operation, port usage, and relationship of the ACSLS components when used across a firewall. They are intended to be understood in with the text just presented (above). The “SSI" in the following diagrams is the network interface component of ACSLS that runs on the client-side of the communications. The CSI is the network interface component of ACSLS that runs on the ACSLS platform.
Note:
The ACSLS CSC Developer's Toolkit 2.3 (or later) and the new environment variables are required to support these scenarios.Firewall Security on ACSLS Server-Side Only
In this example, firewall security is implemented on the ACSLS server-side (CSI) only. The CSC Toolkit 2.3 (or later) and the new environment variables are not required to support this scenario.
Figure L-1 Firewall security on ACSLS Server-Side only
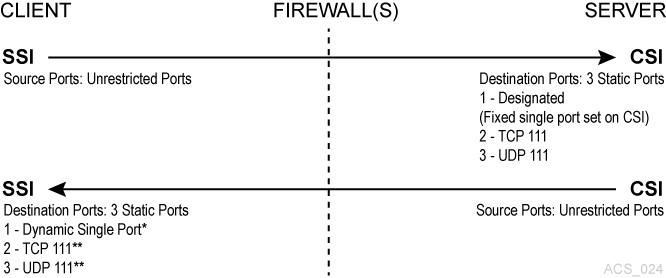
Description of "Figure L-1 Firewall security on ACSLS Server-Side only"
In this example, dynamic means that the port is selected by the SSI at startup from the range 1024-65535. The port is not designated by the user, nor is it typically the same port across new executions of the SSI (that is, from one instance of an SSI running process to the next).
The portmapper 111 port(s) on the SSI-side is only rarely queried by the CSI. It is only accessed by the CSI in the case where the return port number provided by the SSI in its request packet does not function (that is, results in a network interface failure) for sending the response packets back to the SSI. In this case, as a retry mechanism, the CSI queries the SSI-side portmapper for the port to use, which is registered with the portmapper under the SSI's program number.
To secure ACSLS behind a firewall, you need the following settings:
-
ACSLS: ACSLS must be restarted after any changes.
-
CSI_TCP_RPCSERVICE= TRUE -
CSI_UDP_RPCSERVICE= FALSE(However, this must be TRUE if you have any clients who use UDP to communicate with ACSLS)
-
CSI_USE_PORTMAPPER= ALWAYS (This could beIF_DUAL_LAN_NOT_ENABLED) -
CSI_FIREWALL_SECURE= TRUE -
CSI_INET_PORT= <1024-65535, not 50003> default 30031
-
-
Client SSI Settings - Environment variables that allow the client to run behind a firewall.
-
CSI_TCP_RPCSERVICE= TRUE -
CSI_UDP_RPCSERVICE= TRUE (could be FALSE) -
SSI_INET_PORT= 0This is a new environment variable with ACSLS CSC Developer's Toolkit 2.3 and not required for this scenario.
-
CSI_HOSTPORT= 0 or <1024-65535, not 50003> default 30031It is not needed if you are using a portmapper on the ACSLS server. If defined and not zero, this must match
CSI_INET_PORTon the ACSLS Server. This is a new environment variable with ACSLS CSC Developer's Toolkit 2.3 (or later) and not required for this scenario.
-
Configure your firewall to allow the client to send requests to the ACSLS server using the port specified by CSI_INET_PORT (on the ACSLS server) and CSI_HOSTPORT (on the client). Allow the client to access the portmapper (port 111) on the ACSLS server and ACSLS to access the portmapper (111) on the client.
Firewall Security on Client-Side Only
In this example, firewall security is implemented on the client-side (SSI) only. The CSC Toolkit 2.3 (or later) and the new environment variables are required to support this scenario.
Figure L-2 Firewall Security on Client-Side Only
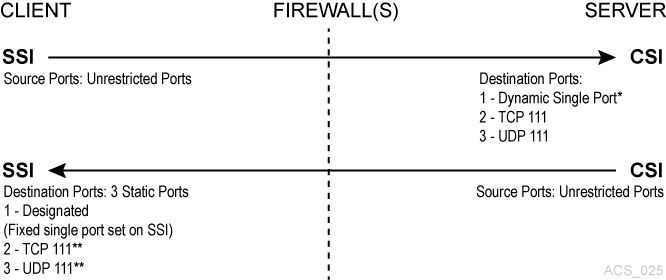
Description of "Figure L-2 Firewall Security on Client-Side Only"
In this example, dynamic means that the port is selected by the CSI at startup from the range 1024-65535, and the port is not designated by the user, nor is it typically the same port across new executions of the CSI (from one instance of an CSI running process to the next).
The portmapper 111 port(s) on the SSI-side is only rarely queried by the CSI. It is only accessed by the CSI, in the case, where the return port number provided by the SSI in its request packet does not function (that is, it results in a network interface failure) for sending the response packets back to the SSI. In this case, as a retry mechanism, the CSI queries the SSI-side portmapper for the port to use, which is registered with the portmapper under the SSIs' program number.
To secure the client system behind a firewall, you need the following settings:
-
ACSLS: ACSLS must be restarted after any changes.
-
CSI_TCP_RPCSERVICE= TRUE -
CSI_UDP_RPCSERVICE= FALSEIf you have any clients using UDP to communicate with ACSLS, this must be TRUE.
-
CSI_USE_PORTMAPPER= ALWAYS (This could beIF_DUAL_LAN_NOT_ENABLED) -
CSI_FIREWALL_SECURE= FALSE -
CSI_INET_PORT= 0
-
-
Client SSI Settings - Environment variables that allow the client to run behind a firewall.
-
CSI_TCP_RPCSERVICE= TRUE -
CSI_UDP_RPCSERVICE= FALSE (could be TRUE) -
SSI_INET_PORT= <1024 –65535, except 50001 and 50004>This is a new environment variable with ACSLS CSC Developer's Toolkit 2.3 (or later) and not required for this scenario.
-
CSI_HOSTPORT= 0 or <1024-65535, not 50003> default 30031Not needed if you are using a portmapper on the ACSLS server. If defined and not zero, this must match
CSI_INET_PORTon the ACSLS Server. This is a new environment variable with ACSLS CSC Developer's Toolkit 2.3 (or later) and not required for this scenario.
-
You must configure your firewall(s) to allow:
-
The client to send requests to the ACSLS server using the port specified by
CSI_INET_PORT(on the ACSLS server) andCSI_HOSTPORT(on the client). -
The client to access the portmapper (port 111) on the ACSLS serer.
-
The ACSLS server to send responses to the client using the port specified by
SSI_INET_PORTon the client. -
The ACSLS server to query the portmapper on the client using port 111.
Firewall Security on Both ACSLS Server and Client-Side with Portmapper
In this example, both the client (SSI) and the ACSLS server (CSI) are implementing Firewall-Secure APIs. The client and server are still relying on the portmapper for port identification. The CSC Toolkit 2.3 (or later) and the new environment variables are required to support this scenario.
Figure L-3 Firewall Security on both ACSLS Server and Client-Side with Portmapper
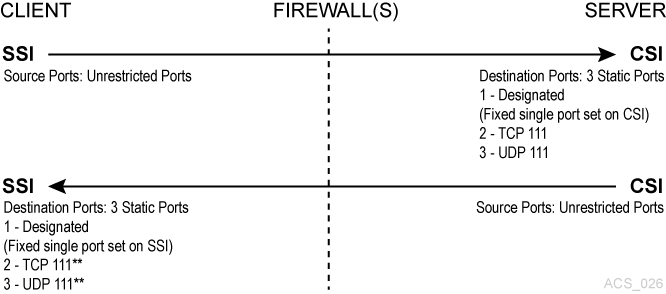
Description of "Figure L-3 Firewall Security on both ACSLS Server and Client-Side with Portmapper"
The portmapper 111 that port(s) on the SSI-side is only rarely queried by the CSI. It is only accessed by the CSI, in the case, where the return port number provided by the SSI in its request packet does not function (that is, it results in a network interface failure) for sending the response packets back to the SSI. In this case, as a retry mechanism, the CSI queries the SSI-side portmapper for the port to use, which is registered with the portmapper under the SSI's program number.
For firewalls protecting both the ACSLS server and the Client, you need the following settings:
-
ACSLS: ACSLS must be restarted after any changes.
-
CSI_TCP_RPCSERVICE= TRUE -
CSI_UDP_RPCSERVICE= FALSEHowever, this must be TRUE if you have any clients who use UDP to communicate with ACSLS.
-
CSI_USE_PORTMAPPER= ALWAYS (This could beIF_DUAL_LAN_NOT_ENABLED) -
CSI_FIREWALL_SECURE= TRUE -
CSI_INET_PORT= <1024-65535, not 50003> default 30031
-
-
Client SSI Settings - Environment variables that allow the client to run behind a firewall.
-
CSI_TCP_RPCSERVICE= TRUE -
CSI_UDP_RPCSERVICE= FALSE -
SSI_INET_PORT= <1024 –65535, except 50001 and 50004> -
CSI_HOSTPORT= <1024-65535, not 50003> default 30031This must match
CSI_INET_PORTon the ACSLS Server.
-
You must configure your firewall(s) to allow:
-
The client to send requests to the ACSLS server using the port specified by
CSI_INET_PORT(on the ACSLS server) andCSI_HOSTPORT(on the client). -
The client to access the portmapper (port 111) on the ACSLS serer.
-
The ACSLS server to send responses to the client using the port specified by
SSI_INET_PORTon the client. -
The ACSLS server to query the portmapper on the client using port 111.
Firewall Security on Both ACSLS Server and Client-Side without Portmapper
In this example, both Client (SSI) and ACSLS Server (CSI) have implemented the firewall-secure features. The client and server have enabled the “No Portmapper" feature. The CSC Toolkit 2.3 (or later) and the new environment variables are required to support this scenario.
Figure L-4 Firewall Security on both ACSLS Server and Client-Side without Portmapper
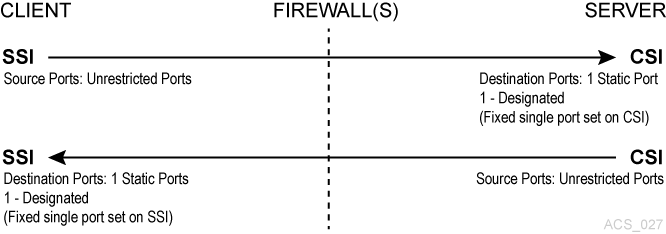
Description of "Figure L-4 Firewall Security on both ACSLS Server and Client-Side without Portmapper"
For the most secure configuration, you need the following settings:
-
ACSLS: ACSLS must be restarted after any changes.
-
CSI_TCP_RPCSERVICE= TRUE -
CSI_UDP_RPCSERVICE= FALSE -
CSI_USE_PORTMAPPER= NEVER -
CSI_FIREWALL_SECURE= TRUE -
CSI_INET_PORT= <1024-65535, not 50003> default 30031
-
-
Client SSI Settings - Environment variables that allow the client to run behind a firewall.
-
CSI_TCP_RPCSERVICE= TRUE -
CSI_UDP_RPCSERVICE= FALSE -
SSI_INET_PORT= <1024 –65535, except 50001 and 50004> -
CSI_HOSTPORT= <1024-65535, not 50003> default 30031This must match
CSI_INET_PORTon the ACSLS Server.
-
You must configure your firewall(s) to allow:
-
The client to send requests to the ACSLS server using the port specified by
CSI_INET_PORT(on the ACSLS server) andCSI_HOSTPORT(on the client). -
The ACSLS server to send responses to the client using the port specified by
SSI_INET_PORTon the client.