Document Information
Preface
Part I Introduction
1. Overview
2. Using the Tutorial Examples
Part II The Web Tier
3. Getting Started with Web Applications
4. JavaServer Faces Technology
5. Introduction to Facelets
6. Expression Language
7. Using JavaServer Faces Technology in Web Pages
8. Using Converters, Listeners, and Validators
9. Developing with JavaServer Faces Technology
10. JavaServer Faces Technology: Advanced Concepts
11. Using Ajax with JavaServer Faces Technology
12. Composite Components: Advanced Topics and Example
13. Creating Custom UI Components and Other Custom Objects
14. Configuring JavaServer Faces Applications
15. Java Servlet Technology
16. Uploading Files with Java Servlet Technology
17. Internationalizing and Localizing Web Applications
Part III Web Services
18. Introduction to Web Services
19. Building Web Services with JAX-WS
20. Building RESTful Web Services with JAX-RS
21. JAX-RS: Advanced Topics and Example
Part IV Enterprise Beans
22. Enterprise Beans
23. Getting Started with Enterprise Beans
24. Running the Enterprise Bean Examples
25. A Message-Driven Bean Example
26. Using the Embedded Enterprise Bean Container
27. Using Asynchronous Method Invocation in Session Beans
Part V Contexts and Dependency Injection for the Java EE Platform
28. Introduction to Contexts and Dependency Injection for the Java EE Platform
29. Running the Basic Contexts and Dependency Injection Examples
30. Contexts and Dependency Injection for the Java EE Platform: Advanced Topics
31. Running the Advanced Contexts and Dependency Injection Examples
Part VI Persistence
32. Introduction to the Java Persistence API
33. Running the Persistence Examples
34. The Java Persistence Query Language
35. Using the Criteria API to Create Queries
36. Creating and Using String-Based Criteria Queries
37. Controlling Concurrent Access to Entity Data with Locking
38. Using a Second-Level Cache with Java Persistence API Applications
Part VII Security
39. Introduction to Security in the Java EE Platform
40. Getting Started Securing Web Applications
Securing Web Applications
Specifying Security Constraints
Specifying a Web Resource Collection
Specifying an Authorization Constraint
Specifying a Secure Connection
Specifying Security Constraints for Resources
Specifying Authentication Mechanisms
HTTP Basic Authentication
Form-Based Authentication
Digest Authentication
Specifying an Authentication Mechanism in the Deployment Descriptor
Declaring Security Roles
Using Programmatic Security with Web Applications
Authenticating Users Programmatically
Checking Caller Identity Programmatically
Example Code for Programmatic Security
Declaring and Linking Role References
Examples: Securing Web Applications
To Set Up Your System for Running the Security Examples
The hello2_basicauth Example: Basic Authentication with a Servlet
Specifying Security for Basic Authentication Using Annotations
To Build, Package, and Deploy the hello2_basicauth Example Using NetBeans IDE
To Build, Package, and Deploy the hello2_basicauth Example Using Ant
To Run the hello2_basicauth Example
The hello1_formauth Example: Form-Based Authentication with a JavaServer Faces Application
Creating the Login Form and the Error Page
Specifying Security for the Form-Based Authentication Example
To Build, Package, and Deploy the hello1_formauth Example Using NetBeans IDE
To Build, Package, and Deploy the hello1_formauth Example Using Ant
To Run the hello1_formauth Example
41. Getting Started Securing Enterprise Applications
42. Java EE Security: Advanced Topics
Part VIII Java EE Supporting Technologies
43. Introduction to Java EE Supporting Technologies
44. Transactions
45. Resources and Resource Adapters
46. The Resource Adapter Example
47. Java Message Service Concepts
48. Java Message Service Examples
49. Bean Validation: Advanced Topics
50. Using Java EE Interceptors
Part IX Case Studies
51. Duke's Bookstore Case Study Example
52. Duke's Tutoring Case Study Example
53. Duke's Forest Case Study Example
Index
|
|
Overview of Web Application Security
In the Java EE platform, web components provide the dynamic extension capabilities for
a web server. Web components can be Java servlets or JavaServer Faces pages.
The interaction between a web client and a web application is illustrated in
Figure 40-1.
Figure 40-1 Java Web Application Request Handling 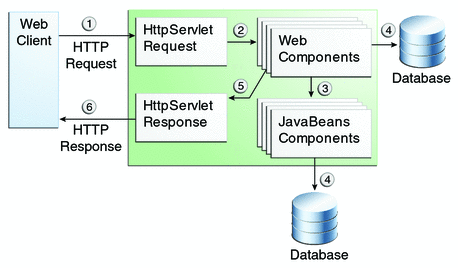 Certain aspects of web application security can be configured when the application is
installed, or deployed, to the web container. Annotations and/or deployment descriptors are used
to relay information to the deployer about security and other aspects of the
application. Specifying this information in annotations or in the deployment descriptor helps the
deployer set up the appropriate security policy for the web application. Any values
explicitly specified in the deployment descriptor override any values specified in annotations.
Security for Java EE web applications can be implemented in the following ways.
Declarative security: Can be implemented using either metadata annotations or an application’s deployment descriptor. See Overview of Java EE Security for more information.
Declarative security for web applications is described in Securing Web Applications.
Programmatic security: Is embedded in an application and can be used to make security decisions when declarative security alone is not sufficient to express the security model of an application. Declarative security alone may not be sufficient when conditional login in a particular work flow, instead of for all cases, is required in the middle of an application. See Overview of Java EE Security for more information.
Servlet 3.0 provides the authenticate, login, and logout methods of the HttpServletRequest interface. With the addition of the authenticate, login, and logout methods to the Servlet specification, an application deployment descriptor is no longer required for web applications but may still be used to further specify security requirements beyond the basic default values.
Programmatic security is discussed in Using Programmatic Security with Web Applications
Message Security: Works with web services and incorporates security features, such as digital signatures and encryption, into the header of a SOAP message, working in the application layer, ensuring end-to-end security. Message security is not a component of Java EE 6 and is mentioned here for informational purposes only.
Some of the material in this chapter builds on material presented earlier in
this tutorial. In particular, this chapter assumes that you are familiar with the
information in the following chapters:
Copyright © 2013, Oracle and/or its affiliates. All rights reserved. Legal Notices
|