6 Managing Web Service Policies with Fusion Middleware Control
Fusion Middleware Control provides a convenient interface for managing the life cycle of Web service policies. From the user interface, you can create, validate, edit, enable, disable, export, and version Web service policies. You can also manage the use of assertion templates from the interface.
For information about Web services policies and how Oracle Web Services Manager (OWSM) uses policies to manage Quality of Service (QoS) for Web services, see "Overview of OWSM Policy Framework" in Understanding Oracle Web Services Manager.
This chapter includes the following sections:
-
Section 6.5, "Enabling or Disabling Policies and Assertions"
-
Section 6.7, "Advertising WS-Policy and WS-SecurityPolicy Versions"
6.1 Overview of Web Services Policy Management
In the 12.1.2 release, the predefined policies and assertion templates delivered with OWSM are read-only. If this is a new installation, then all of the policies and assertion templates that will be installed with OWSM will be read-only.
If you are installing into an existing OWSM environment, or if you are installing over an older release, then only new predefined policies and assertion templates will be read only. Any existing policies or assertion templates will not be overridden with the new read-only version.
Note:
In the next release of OWSM, all predefined documents will be read only and any existing policies and assertion templates will be overridden on installation. To avoid having your existing policies and templates overridden, you must migrate those documents before the next release. For details, see "Upgrading the Repository to 12c".
6.2 Managing Web Service Policies
You manage the Web service policies from the WSM Policies page. From this page you can search for specific policies or types of policies, view policies, create new policies, edit custom policies, delete custom policies, and import and export custom policies to or from the OWSM repository.
The following sections provide additional information:
6.2.1 Navigating to the WSM Policies Page
You manage the Web service policies from the WSM Policies page. From this page you can search for specific policies or types of policies, view policies, create new policies, edit custom policies, delete custom policies, and import and export policies to or from the OWSM repository.
To navigate to the WSM Policies page:
-
In the Target Navigation pane, expand WebLogic Domain and select the domain for which you want to see the policies.
-
From the WebLogic Domain menu, select Web Services, then WSM Policies.
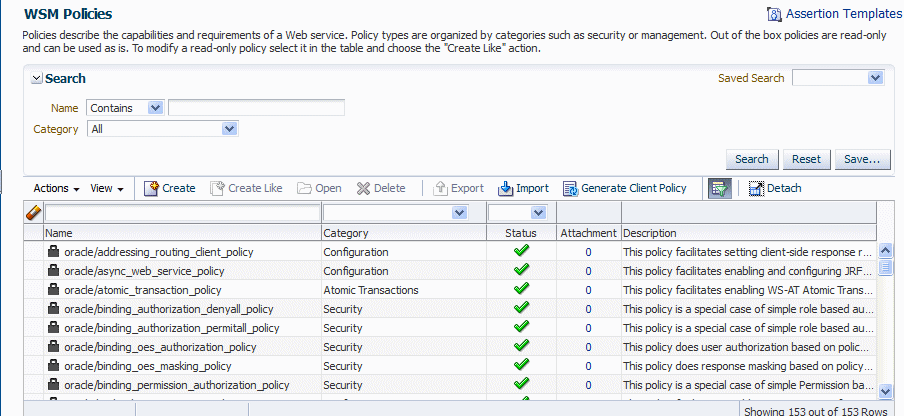
The WSM Policies page is displayed, as shown in Figure 6-1.
6.2.2 Searching for Policies in the WSM Policies Page
You can search for policies in the WSM Policies page using the advanced search feature, the Query by Example filter, or a combination of the two to refine the search. Details are provided in the following sections:
6.2.2.1 Using Advanced Search
In the WSM Policies page, you can reduce the number of policies that are returned by specifying the appropriate search criteria. To do so:
-
In the Search pane, specify the criteria to use in the search:
-
In the Name field, enter a policy name or part of a policy name and select the operator to use to refine the search. Available operators are Starts with, Ends with, Equals, and Contains. For example, to search for message protection policies only, select the Contains operator, and enter
messagein the Name field.You can use percent
%as a wildcard, any place in the name. Asterisk*is not recognized as a wildcard and is treated as plain text. Searches are case-insensitive. -
In the Category field, select the desired category.
Alternatively, you can select one of the previously saved searches from the Saved Search drop-down menu. The search parameters automatically populate the search fields. If the Run automatically option is specified for the saved search, it runs automatically and the results are displayed in the Policies table.
-
-
Optionally, refine the search using the Query By Example filter, as described in "Using the Query by Example Filter". Note that when you combine the two search types, the data entered into the Query By Example fields is appended using the AND operator to the data specified in the Search fields.
-
Click Search.
The Policies table is refreshed to include only those policies that match the specified search criteria. For example, using the example specified above for message protection policies only, if you did not refine the search using Query by Example, all message protection policies are shown in the list. If you used Query by Example to refine the search for client policies only, the list displayed includes only message protection client policies.
-
Optionally, click Save... to save the search criteria in the repository. Note that only the values specified in the Advanced Search fields are saved; the values specified in the Query By Example fields are not included in the saved searches.
In the Create Saved Search window, enter a name for the search in the Name field. To use this saved search as the default selection for future searches, select Set as default. To execute the search automatically when it is selected, select Run automatically. Click OK.
To modify previously saved searches, click Personalize... from the Saved Search drop-down menu. In the Personalize Saved Searches window, select the saved search from the drop-down menu, edit as required and click Apply. To delete a saved search click Delete. To duplicate a search, click Duplicate. Modify the duplicate as desired and click Apply. When you are finished editing all of the searches, click OK.
6.2.2.2 Using the Query by Example Filter
The Query by Example filter in the WSM Policies page allows you to query a specific field and filter the results displayed in the table quickly and easily.
-
If the search fields are not displayed at the top of the Policies table, click the Query by Example icon. A search field is displayed above the Name, Category, and Status columns.
-
Enter the search criteria in the field above the column in which you want to search. The value entered is interpreted as a "contains" expression. That is, the value is wrapped in
%value%, and will fetch all results that contain the value specified for that column. For example, to search for client policies only, enterclientin the search field above the Name column. -
If you are using the Query by Example filter separately (not in conjunction with the advanced search fields), press Enter.
The list of policies displayed in the table is filtered to display only the results that match the search criteria. Using the example specified in previous step, only client policies are displayed.
Notes:
The Query by Example search fields can be used in conjunction with the advanced search fields to further refine the search results, as described in "Using Advanced Search". When used together, the data entered into the Query By Example fields is appended using the AND operator to the data specified in the Search fields. You must use the Search button to get the combined results.
You need to manually clear the Query by Example search fields when you have completed the search.
6.2.3 Viewing the Details of a Web Service Policy
Use the following procedure to view the details of a Web service policy. Predefined policies from Oracle are read-only and cannot be modified. These policies are displayed in read-only mode. User-created policies are not read-only, and can be edited as described in "Editing a Web Service Policy".
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page".
Optionally, refine the list of policies displayed using Search, as described in "Searching for Policies in the WSM Policies Page".
-
Select the policy to be viewed from the list of policies and click Open. Alternatively, select Actions and then Open.
Figure 6-2 displays the Policy Details page for the
oracle/wss10_saml20_token_with_message_protection_service_policy.Figure 6-2 Policy Details Page with the General Tab Selected
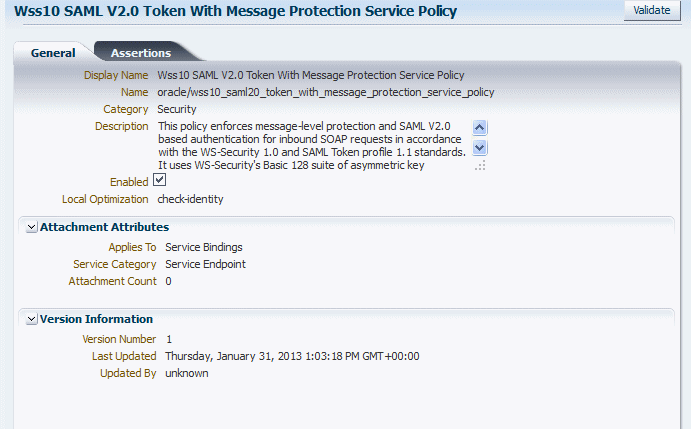
Description of "Figure 6-2 Policy Details Page with the General Tab Selected"
The Policy Details page contains two tabs:
-
The General tab (shown in Figure 6-2) displays information such as the policy name and display name, policy category, description, whether the policy is enabled, and the local optimization setting. The Attachment Attributes section provides details about the type of endpoints to which the policy can be attached, and the number of policy attachments. The Version Information section lists the version number of the policy, when it was last updated, and by whom. For user-created policies, you can also navigate to the Policy Version history page. For more information about policy versions, see "Versioning Web Service Policies".
-
The Assertions tab includes a table that lists all of the assertions contained in the policy. Select the assertion name in the table to view the assertion details. The content displayed varies depending on the assertion selected. Figure 6-3 displays the Assertions tab for the Wss10 SAML V2.0 Token With Message Protection Service Policy.
Figure 6-3 Policy Details Page with the Assertion Tab Selected
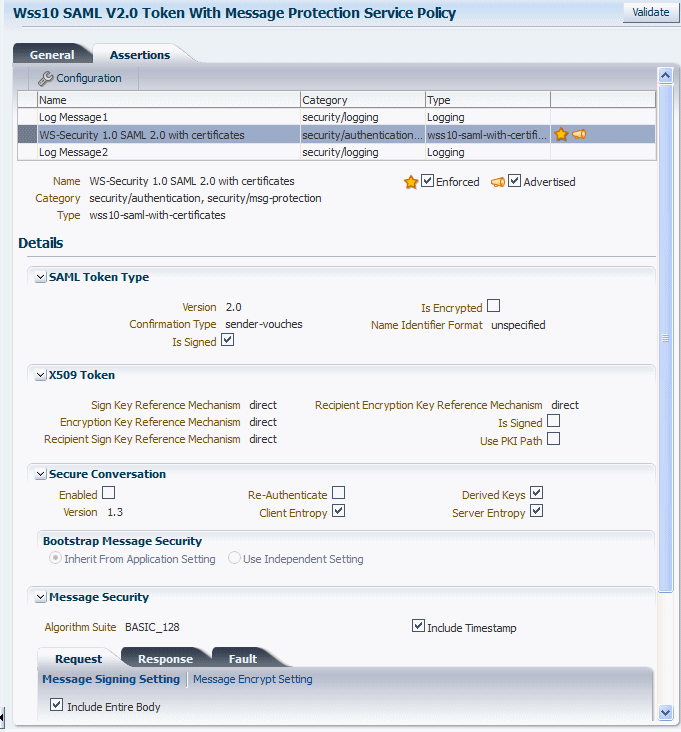
Description of "Figure 6-3 Policy Details Page with the Assertion Tab Selected"
-
6.2.4 Creating and Editing Web Service Policies
The following sections describe how to create and edit Web service policies:
6.2.4.1 Creating a New Web Service Policy
Use the following procedure to create a new policy using one or more assertion templates:
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page" and click Create. Alternatively, select Actions and then Create.
The Policy Details page includes two tabs: General and Assertions. The General tab is displayed by default.
-
On the General tab, optionally specify a unique name in the Display Name field to be used in the console to reference the policy. If you do not specify a display name, the policy name is used to reference the policy.
-
Enter a policy name in the Name field.
The policy name must include the directory in which the policy is located. For example, all predefined policies provided by Oracle are contained in the
oracle/directory, such asoracle/wss_http_token_service_policy.Notes:
Oracle recommends that you follow the policy naming conventions described in "Recommended Naming Conventions for Policies" in Understanding Oracle Web Services Manager.
You cannot edit the name of a policy once the policy is created. To change the policy name, you will need to clone the policy and assign it a different name.
-
Select the category to which the policy will belong from the Category drop-down menu.
Note:
You can create policies in the Security and Management categories only.
-
Optionally, enter a brief description for the policy.
-
Select the Enabled option to enable the policy, if desired. Note that a policy that is not enabled is not enforced at run time.
The Local Optimization setting is reserved for future use.
-
In the Attachment Attributes section of the page, specify the type of policy subjects to which the policy can be attached by selecting from the Applies To menu. If you select Service Bindings, then specify whether the policy can be attached to Web service endpoints, Web service clients, or both.
Note:
The SOA Components option on this menu is reserved for future use.
-
Select the Assertions tab, and click Add to add assertions to your policy. For more information, see "Adding Assertions to a Policy"
-
Optionally, add an OR group to the policy. Select the Add menu then select OR Group. Then click Add to add the desired assertions to the OR group.
An OR group enables you to define multiple security subcategory options, only one of which can be executed. For example, a subset can contain both a SAML Token and a Username Token security/authentication subcategory assertion, so a Web service application can use either one or the other, but not both.
For more information, see "Adding an OR Group to a Policy".
-
Configure the assertions as required by modifying the settings and configuration properties.
-
To edit the assertion settings, select the assertion and edit the settings in the Details section of the page.
-
To edit the configuration properties, click Configuration.
The list of configuration properties defined for the assertion are displayed.
Edit the configuration properties as described in "Editing the Configuration Properties in an Assertion Template" and click OK.
For details about the settings and configuration properties for each assertion template, see Chapter 19, "Predefined Assertion Templates."
-
-
When you have finished adding assertions to the policy, select the assertions in the table and use the Move Up and Move Down buttons to set the order in the policy. Assertions are invoked in the order in which they appear in the list.
-
Click Save to validate and save the policy.
If the policy is invalid, it is disabled as a precaution. After you correct the validation issues, you will have to enable the policy. For more information on policy validation, see "Validating Web Service Policies".
6.2.4.2 Cloning a Web Service Policy
You can create a new policy by cloning an existing Web service policy. For example, you can create a copy of one of the read-only predefined policies and edit it to suit your needs. You can also create a copy of a policy that you have created. Once the policy is created, you can treat it like any other user-created policy, adding or deleting assertions, and modifying existing assertions.
To clone a Web service policy:
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page".
-
Optionally, refine the list of policies displayed using Search, as described in "Using Advanced Search".
-
Select the policy to be cloned from the list of policies and click Create Like. Alternatively, select Actions and then Create Like.
Note:
You can clone policies in the Security and Management categories only.
The Policy Details page is displayed. The word Copy is appended to the name and display name of the cloned policy and, by default, this is the name assigned to the new policy.
It is recommended that you change the name of this new policy to be more meaningful in your environment.
Notes:
Oracle recommends that you follow the policy naming conventions described in "Recommended Naming Conventions for Policies" in Understanding Oracle Web Services Manager.
You cannot edit the name of a policy once the policy is created. To change the policy name, you will need to clone the policy and assign it a different name.
-
Modify the policy as required, including the assertions.
For details about adding assertions to the policy, see "Adding Assertions to a Policy".
For details about adding an OR group to the policy, see "Adding an OR Group to a Policy".
-
Click Save to validate and save the policy.
If the policy is invalid, it is disabled as a precaution. After you correct the validation issues, you will have to enable the policy. For more information on policy validation, see "Validating Web Service Policies".
6.2.4.3 Creating Custom Policies
You can create custom policies using custom assertions. For more information and procedures about how to create both custom assertions and policies, see "Creating Custom Assertions" in Developing Extensible Applications for Oracle Web Services Manager.
6.2.4.4 Editing a Web Service Policy
You can edit a user-created policy as described in this section.
Note:
The predefined policies that are provided with OWSM are read-only and cannot be edited. To edit a predefined policy you can clone it and then edit the cloned version.
The changes that you make to the policy take effect at the next polling interval for policy changes.
If you are using a database-based metadata repository, each time you save a change to your policy, a new version is created, and the older versions are retained. For more information about policy versioning, see "Versioning Web Service Policies".
To edit a Web service policy:
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page".
Optionally, refine the list of policies displayed using Search, as described in "Using Advanced Search".
-
Select the policy to be edited from the list of policies and click Open. Alternatively, select Actions and then Open.
The Policy Details page is displayed. For predefined policies, this page is read-only. However, for user-created policies, you can edit the policy from this page. For more information about the Policy Details page, see "Viewing the Details of a Web Service Policy".
-
Select the General tab and edit as follows:
-
Edit the display name and description, if desired. You cannot edit the policy name. To change the name of a policy, you will need to clone it and assign it a different name.
-
Edit the remaining fields on the tab as required, including enabling or disabling the policy, specifying local optimization, or modifying the type of policy subjects to which the policy can be attached.
-
-
Select the Assertions tab and edit as follows:
-
Modify the assertion settings and configuration properties as required. To modify the assertion settings, select the assertion in the table and edit the settings as required in the Details section of the page. To edit the configuration properties, click Configuration and edit the properties as required in the Configuration table.
-
Add assertions or OR groups as required, as described in "Adding Assertions to a Policy" and "Adding an OR Group to a Policy", respectively.
-
Delete assertions or OR groups as required. To do so, select the assertion or OR group in the table and click Delete.
For details about the assertions in each predefined policy, see Chapter 18, "Predefined Policies.".
-
-
Click Validate to validate the policy.
-
Click Save to save the changes.
6.2.5 Generating Client Policies from a WSDL
After you have configured a Web service, you can use the Web service WSDL to generate compatible client policies with the parameters required to call that service. Note that only assertions that are advertised in a policy can be used to generate equivalent client assertions in the client policy.
Note:
You must use the Oracle WSDL instead of the standard WSDL to generate the client policy. The URL for the Web service must be appended with ?orawsdl, instead of ?wsdl. Generating the policy increases the likelihood that the client policy will work with the service policy.
When you generate a client policy, it is populated with the client assertion that is the matching pair to the advertised service assertion. For example, if the service policy in the WSDL contained the oracle/ wss_http_token_service_template, then the generated client policy is populated with its counterpart, oracle/wss_http_token_client_template.
Before editing the policy, you must first save it. After you have made the desired changes to the policy, you can access it from the WSM Policies page.
You can also delete any generated policies that you do not need. For example, you may want to delete duplicates of already existing MTOM or Reliable Messaging policies.
To create a Web service client policy:
-
Determine the WSDL for the Web service for which you want to generate a Web service client policy.
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page" and click Generate Client Policy.
The Oracle WSDL page used to create the client policies is displayed.
-
In the Oracle WSDL URL field, enter the URL to the Web service WSDL using the following format:
Web_service_endpoint?orawsdl, whereWeb_service_endpointis the URL to the Web service, for examplehttp://my-host:port/jaxwsejb/Calculator?wsdl.Note:
You must use ?orawsdl, instead of ?wsdl, to get the WSDL that is used to generate the corresponding client policy.
The service policy information in the Oracle WSDL published for the Web service is used as the basis for generating the initial client policies.
-
If HTTP authentication is required, select Authentication and provide the username and password in the appropriate fields.
-
Click Fetch.
-
Select the service and port from the drop-down lists.
The service and port combination define the endpoint to which the policies can be attached in the orawsdl.
-
Click Generate Policies.
The client policies corresponding to the service policy specified in the wsdl for the service and port are listed in the Generated Policy Results table as shown in Figure 6-4.
Figure 6-4 Generate Client Policies from WSDL
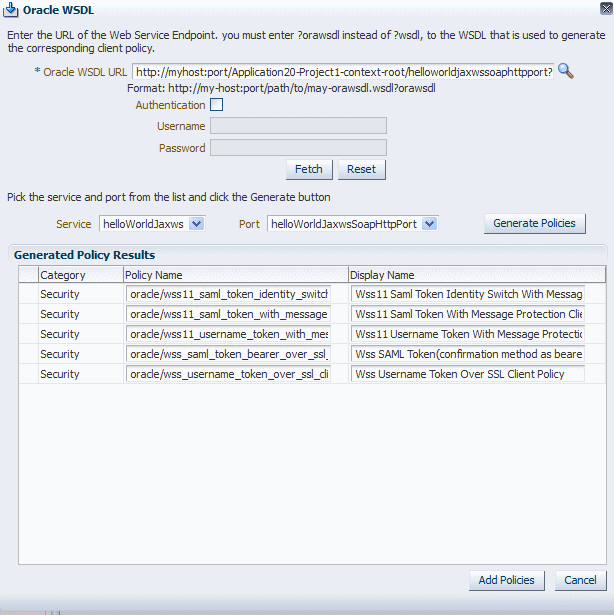
Description of "Figure 6-4 Generate Client Policies from WSDL"
-
Optionally, select the policy and display name in the Generated Policy Results table and edit as desired.
-
Click Add Policies.
The Generate Client Policies page is displayed.
The generated policies are listed in the table and their status is indicated as Not Saved.
-
Click Save All to save all the policies, or select individual policies and click Save.
Note:
You must save the policies before you can edit them.
-
To edit a policy, select the policy in the table and click Open.
-
In the Policy Details page, edit the policy as necessary.
-
Click Apply to save the changes to your policy.
-
You are returned to the Generated Client Policies page. Edit and save the other policies as needed.
Once the policy is saved, you can navigate to the WSM Policies page and find the policy in the list of policies.
6.2.6 Adding Assertions to a Policy
You can add assertions to a user-created policy during policy creation or editing. You cannot add assertions to the predefined policies provided with OWSM. The predefined policies are read-only and cannot be modified.
Each policy can contain only one assertion for each of the following categories: MTOM Attachments and Reliable Messaging. The policy can contain any number of assertions belonging to the Security category; however, the combination of assertions must be valid. For more information on valid assertions, see "Validating Web Service Policies".
To add an assertion to a policy:
-
Navigate to the Policy Details page for the policy to which you want to add assertions.
-
Select the Assertions tab.
-
Click Add or select Assertion from the Add menu.
The Add Assertion page is displayed. The assertions available for that policy are displayed in the Search Results table, organized by Display Name. Optionally, use the View menu to display the Template Name column, or to change the order of the columns.
-
Select an assertion from the table, or provide search parameters in the Name and Category fields and click Search. The results that match the search criteria are displayed in the Search Results table.In the Search Results table, select the assertion or assertions to be added to the policy and click Add Selected. To add all the listed assertions to the policy, click Add All.
The selected assertions are displayed in the Selected Assertion Templates table. The assertions are displayed using the Template Display Name. Optionally, use the View menu to display the Template Name column, or to change the order of the columns.
-
In the Selected Assertion Templates table, optionally edit the names for the added assertions in the Assertion Name field.
-
Review the selections in the Selected Assertion Templates table. To remove one or more assertions from this table, click Remove Selected or Remove All. When you have confirmed the assertion selection, click Add Assertion.
The added assertions are listed in a table in the Assertion tab.
For details about the OWSM assertion templates, see Chapter 19, "Predefined Assertion Templates.".
-
To configure the assertion, select the assertion and edit the settings as required in the Details section of the page.
-
To edit the configuration properties, click Configuration.
The list of configuration properties defined for the assertion are displayed.
-
Edit the Configuration properties and click OK.
For details about the configuration properties for each assertion template, see Chapter 19, "Predefined Assertion Templates."
Note that you can edit only the Value, and Description fields. The Name, Type, and Default Value property settings defined in the assertion template cannot be changed, and are displayed as read only. For details about these properties, see "Editing the Configuration Properties in an Assertion Template".
-
When you have finished adding assertions to the policy, select the assertions in the table and use Move Up and Move Down buttons to set the order in the policy. Assertions are invoked in the order in which they appear in the list.
-
When you are done, click Save to save the policy.
6.2.7 Adding an OR Group to a Policy
You can create an OR group, consisting of one or more assertions, enabling a single policy to accept multiple types of security tokens. A client can enforce any one of the policies that are defined in the OR group. For more information, see "Defining Multiple Policy Alternatives (OR Groups)" in Understanding Oracle Web Services Manager.
You can add only one OR group to a policy. Once you have added an OR Group, the OR Group option is greyed out.
You add an OR group from the Policy Details page.
Note:
If you add an OR group instead of an assertion as the first item in the empty assertions table, any assertions that you continue to add are automatically added to the OR group. If, however, an assertion already existed in the policy before the OR group was added, then you can add assertions inside or outside the OR group depending upon the current selected row in the assertions table.
To add an OR group to a policy:
-
Navigate to the Policy Details page for the policy to which you want to add the OR group.
-
Select the Assertions tab.
-
Select OR Group from the Add menu.
An OR Group row is added to the assertions table.
-
Select the OR Group row in the assertions table.
Click Add or select Assertion from the Add menu. Note that OR Group is not available as an option.
The Add Assertion search page is displayed.
-
Select one or more assertions from the Search Results table, or provide search parameters in the Name and Category fields and click Search. The results that match the search criteria are displayed in the Search Results table.
For details about the OWSM assertion templates, see Chapter 19, "Predefined Assertion Templates."
-
In the Search Results table, select the assertion or assertions to be added to the OR Group and click Add Selected. The selected assertions are displayed in the Selected Assertion Templates table.
-
In the Selected Assertion Templates table, optionally provide display names for the added assertions in the Assertion Name field.
Review the selections in the Selected Assertion Template table. To remove one or more assertions from this table, click Remove Selected or Remove All. When you have confirmed the assertion selection, click Add Assertion.
The added assertions are listed under the OR Group in the list of assertions in the Assertion tab.
Note:
The values for the WS-Policy attributes
attachToandcategorylimit the assertions that are valid within the current policy. All assertions within an OR group must be compatible with theattachToandcategoryattribute values in order to be considered. For more information about WS-Policy attributes, see "wsp:Policy".-
To add additional assertions to the OR group, repeat steps 5 through 9.
-
Configure the assertions as required by modifying the settings and configuration properties.
-
To edit the assertion settings, select the assertion and edit the settings in the Details section of the page.
-
To edit the configuration properties, click Configuration.
The list of configuration properties defined for the assertion are displayed.
Edit the configuration properties as described in "Editing the Configuration Properties in an Assertion Template" and click OK.
For details about the settings and configuration properties for each assertion template, see Chapter 19, "Predefined Assertion Templates."
-
-
When you have finished adding assertions to the OR group, select the assertions and use Move Up and Move Down to order them as needed. Assertions are considered for invocation in the order that they appear on the list.
-
To delete an assertion from the OR group, select the assertion and click Delete. To delete the entire OR group, select the OR group and click Delete.
-
When you are done, click Save to save the policy.
6.2.8 Importing Web Service Policies
Follow the procedure in this section to import one or more user-created policies into the OWSM repository. Once the policies are imported, you can attach them to Web services and make changes to them. For more information on importing Web service policies, see "Understanding the Different Mechanisms for Importing and Exporting Policies".
Notes:
The policy name you import must not already exist in the repository.
Be aware that "policy name" and "file name" are different. The policy name is specified by the name attribute of the policy content; the file name is the name of the policy file. You might find it convenient for the two names to match, but it is not required.
You cannot prefix the name of a policy with oracle_. Otherwise, you will receive exceptions when you try to use the policy.
To import one or more Web service policies:
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page".
-
Click Import.
You are prompted to provide the name of a zip archive file containing the policies to be imported.
Note:
The policies to be imported must use the following directory structure in the zip archive:
META-INF/policies/directory/policyname -
In the Import window, enter the path and file name for the zip archive file in the File Upload field, or click Browse to navigate to the directory where the policies archive file is located, then select the zip archive file to be imported.
-
Click Import.
If an error is encountered with one of the policies, the import process stops. For example, if there are five policies to be imported and an error is encountered in the third one, the first two will be imported but the remaining policies will not.
An information window is displayed listing the policies that were imported. Click OK to close the window.
The imported policies are added to the list of policies in the WSM Policies page.
6.2.9 Exporting Web Service Policies
You may want to export a policy to copy it from a development environment to a production environment, or to simply view the policy in another tool or application. You can export Web service policies that you have created as described in "Creating and Editing Web Service Policies". Predefined policies cannot be exported because the same read-only version of the policy will exist in the target environment. Once the policy is exported, you can import it to another repository, attach it to Web services, make changes to it, and so forth.
For more information about exporting Web service policies, see "Understanding the Different Mechanisms for Importing and Exporting Policies".
Use the following procedure to export a policy from the OWSM repository:
-
Navigate to the WSM Policies page, as described in "Navigating to the WSM Policies Page".
-
Optionally, refine the list of policies displayed using Search, as described in "Searching for Policies in the WSM Policies Page".
-
Select the policy or policies to be exported from the list of policies and click Export.
The policies are added to a zip archive file named
policyexport.zipby default. -
Specify a file name for the archive file, if desired, then select a location in your local directory to which you want to save the zip file and click Save.
The directory structure for each policy is maintained in the archive file using the following structure:
META-INF/policies/directory/policynamewhere
directory/policynameare the values you provided when you created the policy.
6.2.10 Versioning Web Service Policies
Whenever a change to a user-created policy is saved, a new version of the policy is automatically created and the version number is incremented. The Policy Manager maintains the history of these changes, enabling you to go back to an earlier version.
Note:
Version control does not apply to the Oracle predefined policies because they are read only and cannot be modified.
Policy versioning requires that you use a database-based OWSM Repository. If you are using a file-based repository, versioning information is not maintained or displayed.
For example, you might find it useful to create two different versions of a policy, perhaps one with logging and one without, and alternate between them. As another example, you might have an occasional need to use a policy such as oracle/binding_authorization_denyall_policy policy with selected roles to temporarily lock down access to a Web service.
By using the versioning feature, you can reuse multiple versions of a policy without having to recreate them every time you need them.
You can also delete any version of the policy, except the active policy, from the Policy Version history table by selecting the policy and clicking Delete.
You cannot edit the policy from the Policy Version history page. You must edit a policy from the Policy Details page.
The following sections describe versioning in more detail:
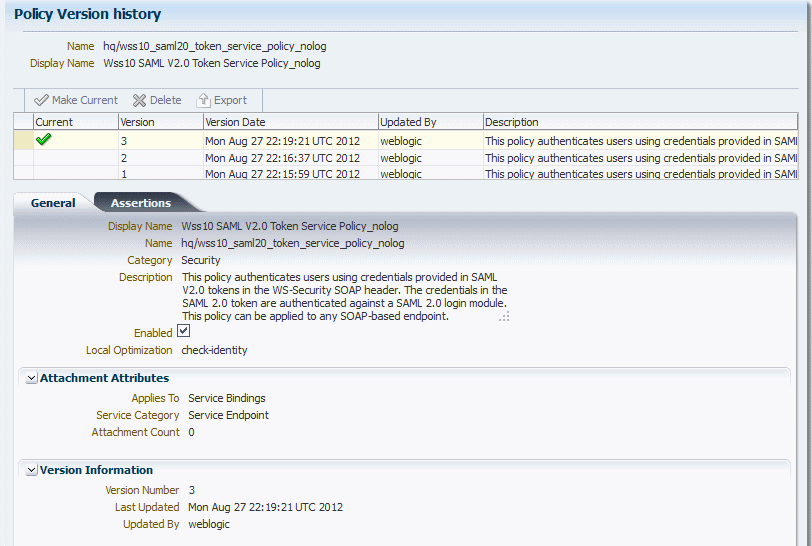
6.2.10.1 Viewing the Version History of a Web Service Policy
You can view the version history for a Web service policy from the Policy Version history page, which you can access from the Policy Details page.
To view the version history for a policy:
-
Navigate to the Policy Details page for the policy as described in "Viewing the Details of a Web Service Policy".
-
Select the General tab for the policy, if it is not already selected.
-
In the Version Information section of the page, click Versioning History.
The Policy Version history for the page is displayed, as shown in Figure 6-5. The policy versions appear in order in the version history table at the top of the page. The currently active policy has the highest version number, and is the only policy that can be attached to a policy subject. However, you can make an earlier version of a policy the active version.
6.2.10.2 Changing the Current Version of a Policy
Use the following procedure to change the current version of the policy:
-
In the Version Information section of the policy detail page, click Versioning History to display the Policy Version history page.
-
In the policy version table, select the version to be made current and click Make Current.
The selected policy version becomes the current active policy and the current version number is incremented by 1. The earlier version of the policy is retained.
6.2.10.3 Deleting Versions of a Web Service Policy
Use the following procedure to delete earlier versions of a policy. You can delete all versions except the active policy version. To delete all versions of the policy, including the active version, see "Deleting a Web Service Policy".
-
In the Version Information section of the policy detail page, click Versioning History to display the Policy Version history page.
-
In the policy version table, select the version or versions to be deleted and click Delete.
-
In the Confirm Policy Version Deletion box, click OK.
The selected policy version(s) is deleted from the OWSM Repository and the Policy History table.
6.2.10.4 Exporting a Version of a Policy
Use the following procedure to export a version of the policy:
-
In the Version Information section of the policy detail page, click Versioning History to display the Policy Version history page.
-
In the policy version table, select the version to be made exported and click Export.
You are prompted to open or save the file.
-
Select Save File and click OK.
-
Navigate to the local directory to which you want to save the file and update the filename as desired.
-
Click Save.
6.2.11 Deleting a Web Service Policy
Before you delete a policy, Oracle recommends that you verify that the policy is not attached to any policy subjects. If you try to delete a policy that is attached to a subject, you will receive a warning. You will not be prevented from deleting an attached policy. However, the Web service request will fail the next time the subject to which the policy is attached is invoked.
You can see the policy subjects that are attached to a policy by doing a policy dependency analysis. For more information, see "Analyzing Policy Usage".
Note:
Only user-created policies can be deleted. The predefined policies delivered with OWSM are read only and cannot be edited or deleted.
When you delete a policy, the active policy and all previous versions of the policy are deleted. To retain the active policy version and delete only the previous versions of the policy, see "Deleting Versions of a Web Service Policy".
To delete a user-created Web service policy:
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page".
Optionally, refine the list of policies displayed using Search, as described in "Using Advanced Search".
-
From the WSM Policies page, select the policy to be deleted from the list of policies and click Delete. Alternatively, select Actions and then Delete.
-
A dialog box appears asking you to confirm the deletion. Click Delete.
6.3 Validating Web Service Policies
There are restrictions on the type and number of policy assertions that are permitted in a Web service policy. A policy can contain only assertions that belong to a single category. Therefore, you cannot combine a Security assertion with an MTOM assertion in the same policy. The policy type is determined by the category of the assertion. Therefore, a policy containing a security assertion is a security policy, a policy containing a management assertion is a management policy, and so on. Security assertions are further categorized into subcategories: authentication, logging, message protection (msg-protection), and authorization.
There are restrictions on the number and type of assertions you can have in a policy. The restrictions are as follows:
-
MTOM and Reliable Messaging policies can contain only one assertion.
-
A security policy can contain multiple security assertions; however, there can be only one assertion from the following subcategories in a policy: encryption, signing, and authentication.
-
Some assertions contain both authentication and message protection. For example, if you view the
oracle/wss11_username_token_with_message_protection_service_policy, you will see that the second assertion falls into two categories: security/authentication and security/msg-protection, as shown in Figure 6-6.Figure 6-6 Security Assertion with Two Subcategories
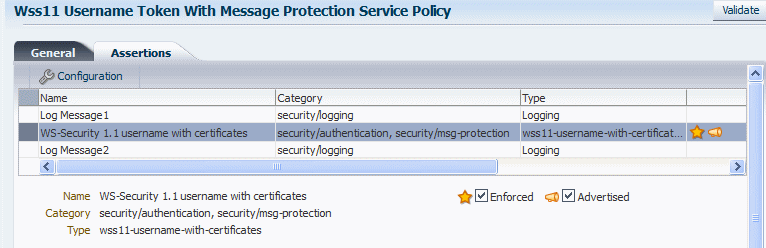
Description of "Figure 6-6 Security Assertion with Two Subcategories"
-
A security policy can contain any number of security_log_template assertions. For example, if you view any of the predefined security policies, you will see two logging assertions included.
Oracle recommends that you create one policy for authentication and message protection, and a second policy for authorization. If you create a policy that contains both an authentication and an authorization assertion, then the authentication assertion must precede the authorization assertion.
When you create a new policy or edit a user-created policy, the validation process checks to see that your policies meet these requirements. If the validation fails during policy creation, the policy is created but is marked as disabled.
To validate a policy,
-
On the Policy Details page of the policy being viewed or edited, click Validate.
If the validation is successful, the
Policy is Validmessage appears.If the validation is not successful, the resulting error message describes the problem. Make the necessary corrections, then revalidate the policy.
-
Once the policy validates successfully, click Save to save the policy.
6.4 Managing Policy Assertion Templates
OWSM includes a set of predefined assertion templates that you can use to construct policies. For additional information, see "Building Policies Using Policy Assertions" in Understanding Oracle Web Services Manager. The predefined assertion templates are read only and cannot be modified, but you can clone them to create new assertion templates, if needed, to satisfy a specific requirement.
If the functionality you require, such as support for a non-standard security token, is not provided out of the box, OWSM allows you to define custom policy assertions. For details, see Developing Extensible Applications for Oracle Web Services Manager.
You can add one or more assertions to a user-created policy as described in "Adding Assertions to a Policy". You cannot add assertions to the predefined policies that are provided with OWSM because they are read-only and cannot be modified. Assertions are executed in the order in which they are listed in the policy.
For details about the predefined assertion templates, see Chapter 19, "Predefined Assertion Templates."
The following sections provide more detail about managing policy assertion templates:
-
Searching for an Assertion Template in the Assertion Templates Page
-
Editing the Configuration Properties in an Assertion Template
6.4.1 Navigating to the Assertion Templates Page
You can manage your assertion templates at the domain level from the Assertion Templates page. From this page, you can copy, edit, and delete, import, and export assertion templates.
Navigate to the Assertion Templates page as follows:
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page".
-
In the upper right-hand corner of the page, click Assertion Templates.
6.4.2 Searching for an Assertion Template in the Assertion Templates Page
You can search for assertion templates in the Assertion Templates page using the advanced search feature, the Query by Example filter, or a combination of the two to refine the search. Details are provided in the following sections:
6.4.2.1 Using Advanced Search
In the Assertion Templates page, you can reduce the number of assertion templates that are returned by specifying the appropriate search criteria. To do so:
-
Navigate to the Assertion Templates page as described in "Navigating to the Assertion Templates Page".
-
In the Search pane, specify the criteria to use in the search:
-
In the Assertion Name field, enter an assertion template name or part of a name and select the operator to use to refine the search. Available operators are Starts with, Ends with, Equals, and Contains. For example, to search for message protection assertion templates only, select the Contains operator, and enter
messagein the Assertion Name field.You can use percent
%as a wildcard, any place in the name. Asterisk*is not recognized as a wildcard and is treated as plain text. Searches are case-insensitive. -
In the Category field, select the category to which the assertion template belongs. The options are: All, Management, Security, Reliable Messaging, MTOM Attachments, WS-Addressing, Make Connection, Atomic Transactions, Configuration, and SOAP Over JMS Transport.
Alternatively, you can select one of the previously saved searches from the Saved Search drop-down menu. The search parameters automatically populate the search fields. If the Run automatically option is specified for the saved search, it runs automatically and the results are displayed in the assertion templates table.
-
-
Optionally, refine the search using the Query By Example filter, as described in "Using the Query by Example Filter". Note that when you combine the two search types, the data entered into the Query By Example fields is appended using the AND operator to the data specified in the Search fields.
-
Click Search.
The Assertion Templates table is refreshed to include only those assertion templates that match the specified search criteria. If you did not refine the search using Query by Example, all message protection assertion templates are shown in the list. If you refined the search for client assertion templates only using Query by Example, the list displayed includes only client message protection assertion templates.
-
Optionally, click Save... to save the search criteria in the repository. Note that only the values specified in the Advanced Search fields are saved; the values specified in the Query By Example fields are not included in the saved searches.
In the Create Saved Search window, enter a name for the search in the Name field. To use this saved search as the default selection for future searches, select Set as default. To execute the search automatically when it is selected, select Run automatically.
To modify previously saved searches, click Personalize... from the Saved Search drop-down menu. In the Personalize Saved Searches window, select the saved search from the drop down menu and edit as required. Click Apply. When you are finished editing all of the searches, click OK.
6.4.2.2 Using the Query by Example Filter
The Query by Example filter allows you to query a specific field and filter the results displayed in the table quickly and easily.
-
If the search fields are not displayed at the top of the Assertion Templates table, click the Query by Example icon. A search field is displayed above the Display Name, Category, and Name columns.
-
Enter the search criteria in the field above the column in which you want to search. The value entered is interpreted as a "contains" expression. That is, the value is wrapped in
%value%, and will fetch all results that contain the value specified for that column. For example, to search for client assertion templates only, enterclientin the search field above the Name column. -
If you are using the Query by Example filter separately (not in conjunction with the advanced search fields), press Enter.
The list of assertion templates displayed in the table is filtered to display only the results that match the search criteria. Using the example specified in step 2, only client assertion templates are displayed.
Notes:
The Query by Example search fields can be used in conjunction with the advanced search fields to further refine the search results, as described in "Using Advanced Search". When used together, the data entered into the Query By Example fields is appended using the AND operator to the data specified in the Search fields. You must use the Search button to get the combined results.
You need to manually clear the Query by Example search fields when you have completed the search.
6.4.3 Viewing the Details of an Assertion Template
Use the following procedure to view the details of an assertion template. Predefined assertion templates from Oracle are read-only and cannot be modified. These assertion templates are displayed in read-only mode. User-created assertion templates are not read-only, and can be edited as described in
To view the assertion template details:
-
Navigate to the Assertion Templates page as described in "Navigating to the Assertion Templates Page".
Optionally, refine the list of assertion templates displayed using Search, as described in "Using Advanced Search".
-
Select the assertion template to be viewed from the list of assertion templates and click Open. Alternatively, select Actions and then Open.
Figure 6-7 displays the Assertion Template Details page for the Wss10 SAML V2.0 Token with Message Protection service Assertion Template.
Figure 6-7 Assertion Template Details Page
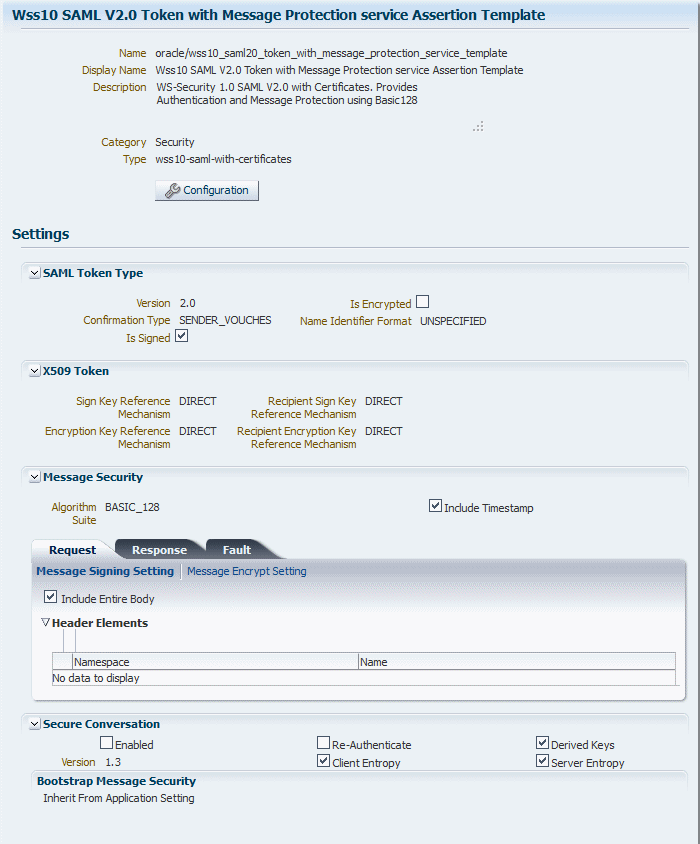
Description of "Figure 6-7 Assertion Template Details Page"
-
Review the details of the assertion template.
General information about the assertion template is provided at the top of the page. Click Configuration to view the configuration properties for the template. The Settings section of the page displays the settings specific to that template. For details about the settings and configuration properties for each of the predefined assertion templates, Chapter 19, "Predefined Assertion Templates."
6.4.4 Naming Conventions for Assertion Templates
The same naming conventions used to name predefined policies are used to name the assertion templates. The predefined assertion templates begin with the directory name oracle/ and are identified with the suffix _template at the end; for example, oracle/wss10_message_protection_service_template.
It is recommended that you follow the recommended naming conventions, and keep any assertion templates that you create in a directory that is separate from the oracle directory where the predefined assertion templates are located. You can organize your assertion templates at the root level, in a directory other than oracle, or in subdirectories.
For more information about the naming conventions for predefined policies, see "Recommended Naming Conventions for Policies" in Understanding Oracle Web Services Manager.
6.4.5 Cloning an Assertion Template
You can create a new assertion template using an existing template as the base. Select the assertion template that most closely matches the desired behavior, make a copy of it using the Create Like feature, then make any changes required to get the new behavior.
To clone a Web service policy:
-
Navigate to the Assertion Templates page as described in "Navigating to the Assertion Templates Page".
-
Optionally, refine the list of assertion templates displayed using Search, as described in "Searching for an Assertion Template in the Assertion Templates Page".
-
Select the assertion template to be cloned from the list of assertion templates and click Create Like. Alternatively, select Actions and then Create Like.
The Assertion Template Details page is displayed.
-
Edit the name and display name for the assertion template and, optionally, enter a brief description.
The word Copy is appended to the name and display name of the cloned assertion template and, by default, this is the name assigned to the new assertion template.
It is recommended that you change the name of this new assertion template to be more meaningful in your environment. For more information, see "Naming Conventions for Assertion Templates".
Notes:
You cannot edit the name of an assertion template after it is created. To change the assertion template name, you will need to clone the assertion template and assign it a different name.
-
Modify the assertion template settings and configuration properties as required. For details about the settings and configuration properties in each of the predefined assertion templates, see Chapter 19, "Predefined Assertion Templates." For details about modifying the configuration properties, see "Editing the Configuration Properties in an Assertion Template"
-
Click Save to save the new assertion template.
6.4.6 Editing an Assertion Template
You can edit a user-created assertion template as described in the following procedure.
Note:
The predefined assertion templates that are provided with OWSM are read-only and cannot be edited. To edit a predefined template you can clone it and then edit the cloned version.
-
Navigate to the Assertion Templates page as described in "Navigating to the Assertion Templates Page".
Optionally, refine the list of assertion templates displayed using Search, as described in "Using Advanced Search".
-
Select the assertion template to be edited from the list of assertion templates and click Open. Alternatively, select Actions and then Open.
-
Edit the display name and description, if desired. You cannot edit the assertion template name. To change the name of an assertion template you will need to clone it and assign it a different name. and assertion template as required and click Save.
-
Edit the settings as required.
For details about the settings and configuration properties for each of the predefined assertion templates, see Chapter 19, "Predefined Assertion Templates."
-
Click Configuration to edit the configuration properties.
To delete a property, select the property in the table and click Delete.
-
Click OK to accept the configuration property changes.
-
Click Save to save the assertion template.
6.4.7 Editing the Configuration Properties in an Assertion Template
If you have cloned one of the predefined assertion templates, you can modify the configuration properties to match your environment. For example, properties that are configurable in assertion templates include csf-key, saml.issuer.name, keystore.recipient.alias, and role, among others.
Note:
You cannot modify the configuration properties in the predefined assertion templates because they are read-only and cannot be modified.
When you clone an assertion template, or edit a cloned assertion template, you can configure the following settings for each property:
-
Description—Description of the property.
-
Value—Current value.
-
Default—Default value. This value is used if the Value field is not set.
-
Type—Can be one of the following:
-
Constant—Property cannot be overridden.
-
Required—Property is required and can be overridden.
-
Optional—Property is optional and can be overridden.
-
To configure the properties:
-
In the assertion template being cloned or edited, click Configuration.
The Configuration window displays the list of properties for the template.
-
Select the property from the list and modify the fields as required. Note that the Name of an existing property cannot be changed.
-
Add or delete configuration properties as required.
To add a configuration property, click Add. In the blank row that appears, provide a name for the property. The remaining fields are optional. However, if you select Type required, then you must provide a value for the property.
To delete a configuration property, select the property in the table and click Delete.
-
When you have finished changing the configuration properties, click OK.
-
Click Save to save the changes in the assertion template.
Note:
When you add an assertion to a policy, as described in "Adding Assertions to a Policy", you can modify the Value, Default, and Description configuration properties to match your environment. The Name and Type configuration properties defined in the assertion template cannot be changed, and are not editable fields in the table.
6.4.8 Exporting an Assertion Template
You can export one or more assertion templates that you have created as described in "Cloning an Assertion Template". Predefined assertion templates can not be exported because the same read-only version of the template will exist in the target environment. After you have exported the assertion templates, you can then copy them to a new directory if desired, or import them into another repository.
To export one or more assertion templates:
-
Navigate to the Assertions Templates page, as described in "Navigating to the Assertion Templates Page".
-
Optionally, refine the list of assertion templates displayed using Search, as described in "Searching for an Assertion Template in the Assertion Templates Page".
-
Select the assertion template or templates to be exported from the list of assertion templates and click Export.
The assertion templates are added to a zip archive file named
assertiontemplatesexport.zipby default. -
Specify a file name for the archive file, if desired, then select a location in your local directory to which you want to save the zip file and click Save.
The directory structure for each assertion template is maintained in the archive file using the following structure:
META-INF/assertiontemplates/directory/assertiontemplatenamewhere
directory/assertiontemplatenameare the values you provided when you created the assertion template.
6.4.9 Importing an Assertion Template
Follow the steps in this section to import a zip archive containing one or more user-created assertion templates. You can use this feature in combination with Export to move one or more assertion templates between different repositories. Once the assertion template is imported, you can add it to Web service policies and make changes to it.
-
Navigate to the Assertions Templates page, as described in "Navigating to the Assertion Templates Page".
-
Click Import.
You are prompted to provide the name of a zip file containing the assertion templates to be imported.
Note:
The assertion templates to be imported must use the following directory structure in the zip archive:
META-INF/assertiontemplates/directory/assertiontemplatename -
In the Import window, enter the path and file name for the zip file in the File Upload field, or click Browse to navigate to the directory where the assertion template zip file is located, then select the zip file to be imported.
-
Click Import.
If an error is encountered with one of the assertion templates, the import process stops. For example, if there are five assertion templates to be imported and an error is encountered in the third one, the first two will be imported but the remaining assertion templates will not.
An information window is displayed listing the assertion templates that were imported. Click OK to close the window.
The imported assertion templates are added to the list of assertion templates on the Assertion Templates page.
6.4.10 Deleting an Assertion Template
Follow the steps in this section to delete an assertion template that you created or imported. The predefined assertion templates delivered with OWSM are read-only and cannot be deleted.
-
Navigate to the Assertions Templates page, as described in "Navigating to the Assertion Templates Page".
-
Optionally, refine the list of assertion templates displayed using Search, as described in "Searching for an Assertion Template in the Assertion Templates Page".
-
Select the assertion template to be deleted from the list of assertion templates and click Delete.
You are prompted to confirm that you want to delete the assertion template.
-
Confirm your selection and click Delete.
The selected assertion template is deleted from the list of assertion templates on the Assertion Templates page.
6.5 Enabling or Disabling Policies and Assertions
The following sections describe the different methods for enabling or disabling policies, or assertions within a policy:
6.5.1 Enabling or Disabling a Policy for all Policy Subjects
When you create a policy, it is enabled by default unless it has validation errors. A user-created policy can be globally enabled or disabled from the Policy Details page. You can enable or disable the policy from one central location, and it will be enabled or disabled for any policy subject to which it is attached.
Note:
You cannot disable a predefined policy from Oracle for all policy subjects. These policies are read-only and cannot be modified. You can, however, disable policy references to an individual subject. For more information, see "Enabling or Disabling Directly Attached Policies Using Fusion Middleware Control".
When you disable a policy from the Policy Details page, the policy continues to be attached to the policy subjects, but the policy is not enforced. You may want to temporarily disable a policy if you discover that there is a problem with the policy that is causing all requests to a Web service to fail. Once the problem is corrected, you can globally enable the policy.
Before disabling a policy, you may want to click Usage Analysis Link (see "Analyzing Policy Usage") to see the policy subjects to which the policy is attached. The change to the policy takes effect at the next polling interval for policy changes.
You may also selectively enable or disable a policy for a specific policy subject rather than for all policy subjects. For more information, see "Enabling or Disabling Directly Attached Policies Using Fusion Middleware Control".
To enable or disable a user-created Web service policy for all policy subjects:
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page".
Optionally, refine the list of policies displayed using Search, as described in "Using Advanced Search".
-
Select the policy to be edited from the list of policies and click Open. Alternatively, select Actions and then Open.
The Policy Details page is displayed. For predefined policies, this page is read-only. However, for user-created policies, you can edit the policy from this page. For more information about the Policy Details page, see "Viewing the Details of a Web Service Policy".
-
Select the General tab if it is not already selected.
-
Select or deselect the Enabled box to enable or disable the policy, respectively.
-
Click Save.
6.5.2 Enabling or Disabling Assertions Within a Policy
Rather than enable or disable an entire policy as described in "Enabling or Disabling a Policy for all Policy Subjects", you may wish to enable or disable one or more of the assertions that are contained within a policy. This provides a more fine-grained level of control over the assertions that are executed.
Note:
You cannot disable an assertion in a predefined policy from Oracle. These policies are read-only and cannot be modified. To disable an assertion in a predefined policy, you need to clone it and then edit the cloned version.
For example, if you created a policy based on one of the read-only predefined Web service security policies, it contains an instance of the Security Log Assertion Template (oracle/security_log_template), to capture the entire SOAP message before and after the primary security assertion is executed. By default, the log assertion is not enforced. You must enable it in order for the SOAP message to be logged in message logs. (It is recommended that the logging assertion be enabled for debugging and auditing purposes only. For more information about logging, see "Diagnosing Problems Using Logs" in Administering Web Services.
To enable or disable one or more assertions within a policy:
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page".
Optionally, refine the list of policies displayed using Search, as described in "Using Advanced Search".
-
Select the policy to be edited from the list of policies and click Open. Alternatively, select Actions and then Open.
The Policy Details page is displayed. For predefined policies, this page is read-only. However, for user-created policies, you can edit the policy from this page. For more information about the policy details page, see "Viewing the Details of a Web Service Policy".
-
Select the Assertions tab.
-
Select the assertion in the table and select or deselect the Enforced box to enable or disable the assertion within the policy, respectively.
-
Click Save.
6.6 Analyzing Policy Usage
Note:
The policy usage feature described in this section requires that you use a database-based OWSM Repository. If you are not using a database-based repository, policy usage information is not available.
Policies are created and managed at the domain level. The central management of policies gives you the ability to reuse policies and attach them to multiple policy subjects. Any change to a policy (for example, editing a policy or deleting a policy) affects all policy subjects to which the policy is attached. Therefore, before making any changes to your policies, Oracle recommends you do a usage analysis to see which subjects are using a particular policy.
Note:
The usage analysis simply identifies which policy subjects will be affected; it does not define the effect of the change. You need to evaluate the change on each of the policy subjects and determine if you should proceed.
-
Navigate to the WSM Policies page as described in "Navigating to the WSM Policies Page".
Optionally, refine the list of policies displayed using Search, as described in "Using Advanced Search".
The Attachment Count column of the Policies table shows the number of subjects to which a policy is attached.
-
Click the number in the Attachment column for the selected policy to display the Usage Analysis page.
The Policy Subject List is filtered by subject type. The table displays a list of the policy subjects, of the selected type, to which the policy is attached. Valid policy subjects include OWSM Repository Documents and the subject types listed in "Understanding Policy Subjects" in Understanding Oracle Web Services Manager. Note that the Policy Subject List summary table displays fields that are relevant to the selected policy subject type only.
The total number of policy subjects to which the policy is attached is shown at the bottom of the page in the Attachment Count field.
-
To view the other policy subjects to which the policy is attached, select the subject type from the Subject Type menu.
The Subject Type menu provides an attachment count for each subject type to which the policy is attached.
-
In cases where multiple domains share the same OWSM Repository to store OWSM metadata, you can specify whether you want to view policy subjects in the Local Domain or in all domains in the enterprise. To view the policy subjects for all domains in the enterprise, select Enterprise in the View Option field.
Please note:
-
Both enabled and disabled policy references are included in the policy usage count. For information about disabling a policy reference, see "Enabling or Disabling Directly Attached Policies Using Fusion Middleware Control" and "Enabling or Disabling a Policy for all Policy Subjects".
-
You must invoke an ADF DC client to display an accurate policy usage count.
6.7 Advertising WS-Policy and WS-SecurityPolicy Versions
For a standard WSDL (?wsdl) file, you can publish different version combinations for WS-Policy and WS-SecurityPolicy. For example, http://localhost:8080/abc?wsdl&wsp=1.5&wssp=1.2 returns a WSDL with the following policy versions published: WS-Policy 1.5 and WS-SecurityPolicy 1.2.
Note:
For an Oracle WSDL (?orawsdl), you cannot advertise different version combinations for WS-Policy and WS-SecurityPolicy. For ?orawsdl, the policy is advertised with the following versions only: WS-Policy 1.2 and WS-SecurityPolicy 1.1 with Oracle extensions.
Table 6-1 lists the valid version combinations.
Table 6-1 Policy Advertisement
| Version Combination | Description |
|---|---|
|
?wsdl |
WS-Policy 1.2 and WS-SecurityPolicy 1.1 |
|
?wsdl&wsp=1.5 |
WS-Policy version 1.5 and WS-SecurityPolicy 1.3 |
|
?wsdl&wssp=1.2 |
WS-Policy versions 1.5 and WS-SecurityPolicy 1.2 |
|
?wsdl&wssp=1.3 |
WS-Policy versions 1.5 and WS-SecurityPolicy 1.3 |
|
?wsdl&wsp=1.5&wssp=1.2 |
WS-Policy 1.5 and WS-SecurityPolicy 1.2 |
|
?wsdl&wsp=1.5&wssp=1.3 |
WS-Policy 1.5 and WS-SecurityPolicy 1.3 |
|
?wsdl&wsp=1.2&wssp=1.2 |
WS-Policy 1.2 and WS-SecurityPolicy 1.2 |