2 About a Typical Enterprise Deployment
It is essential to understand the components of a typical enterprise deployment topology.
This chapter provides information on Enterprise Deployment Topology diagram.
- Diagram of a Typical Enterprise Deployment
This diagram shows all the components of a typical enterprise deployment, including the Web tier, application tier and data tier. All enterprise deployments are based on these basic principles. - About the Typical Enterprise Deployment Topology Diagram
A typical enterprise deployment topology consists of a Hardware Load Balancer (LBR), Web Tier, Application Tier, and Data Tier. You can obtain detailed information on these components in this section.
Parent topic: Understanding an Enterprise Deployment
2.1 Diagram of a Typical Enterprise Deployment
This diagram shows all the components of a typical enterprise deployment, including the Web tier, application tier and data tier. All enterprise deployments are based on these basic principles.
All Oracle Fusion Middleware enterprise deployments are designed to demonstrate the best practices for installing and configuring an Oracle Fusion Middleware production environment.
A best practices approach starts with the basic concept of a multi-tiered deployment and standard communications between the different software tiers.
Figure 2-1 shows a typical enterprise deployment, including the Web tier, application tier and data tier. All enterprise deployments are based on these basic principles.
For a description of each tier and the standard protocols used for communications within a typical Oracle Fusion Middleware enterprise deployment, see Understanding the Typical Enterprise Deployment Topology Diagram.
Figure 2-1 Typical Enterprise Deployment Topology Diagram
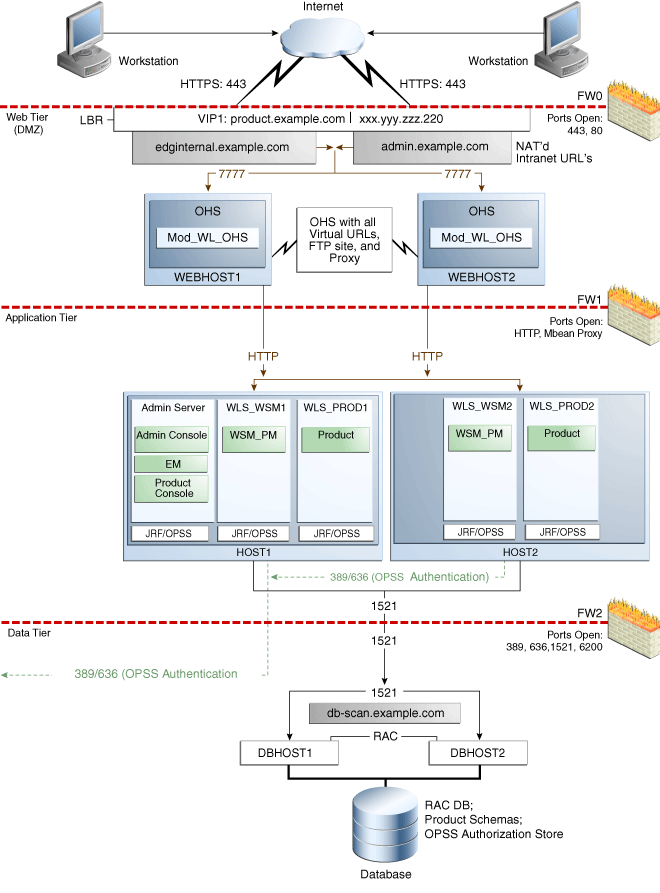
Description of "Figure 2-1 Typical Enterprise Deployment Topology Diagram"
2.2 About the Typical Enterprise Deployment Topology Diagram
A typical enterprise deployment topology consists of a Hardware Load Balancer (LBR), Web Tier, Application Tier, and Data Tier. You can obtain detailed information on these components in this section.
2.2.1 Understanding the Firewalls and Zones of a Typical Enterprise Deployment
The topology is divided into several security zones, which are separated by firewalls:
-
The Web tier (or DMZ), which is used for the hardware load balancer and Web servers (in this case, Oracle HTTP Server instances) that receive the initial requests from users. This zone is accessible only through a single virtual server name defined on the load balancer.
-
The application tier, which is where the business and application logic resides.
-
The data tier, which is not accessible from the Internet and reserved in this topology for the highly available database instances.
The firewalls are configured to allow data to be transferred only through specific communication ports. Those ports (or in some cases, the protocols that will need open ports in the firewall) are shown on each firewall line in the diagram.
For example:
-
On the firewall protecting the Web tier, only the HTTP ports are open: 443 for HTTPS and 80 for HTTP.
-
On the firewall protecting the Application tier, HTTP ports, and MBean proxy port are open.
Applications that require external HTTP access can use the Oracle HTTP Server instances as a proxy. Note that this port for outbound communications only and the proxy capabilities on the Oracle HTTP Server must be enabled.
-
On the firewall protecting the data tier, the database listener port (typically, 1521) must be open.
The LDAP ports (typically, 389 and 636) are also required to be open for communication between the authorization provider and the LDAP-based identity store.
The ONS port (typically, 6200) is also required so the application tier can receive notifications about workload and events in the Oracle RAC Database. These events are used by the Oracle WebLogic Server connection pools to adjust quickly (creating or destroying connections), depending on the availability and workload on the Oracle RAC database instances.
For a complete list of the ports you must open for a specific Oracle Fusion Middleware enterprise deployment topology, see the chapter that describes the topology you want to implement, or refer to the Enterprise Deployment Workbook for the topology you are implement. For more information, see Using the Enterprise Deployment Workbook .
2.2.2 Understanding the Elements of a Typical Enterprise Deployment Topology
The enterprise deployment topology consists of the following high-level elements:
-
A hardware load balancer that routes requests from the Internet to the Web servers in the Web tier. It also routes requests from internal clients or other components that are performing internal invocations within the corporate network.
-
A Web tier, consisting of a hardware load balancer and two or more physical computers that host the Web server instances (for high availability).
The Web server instances are configured to authenticate users (via an external identity store and a single sign-on server) and then route the HTTP requests to the Oracle Fusion Middleware products and components running in the Application tier.
The Web server instances also host static Web content that does not require application logic to be delivered. Placing such content in the Web tier reduces the overhead on the application servers and eliminates unnecessary network activity.
-
An Application tier, consisting of two or more physical computers that are hosting a cluster of Oracle WebLogic Server Managed Servers, and the Administration Server for the domain. The Managed Servers are configured to run the various Oracle Fusion Middleware products, such as Oracle SOA Suite, Oracle Service Bus, Oracle WebCenter Content, and Oracle WebCenter Portal, depending on your choice of products in the enterprise deployment.
-
A data tier, consisting of two or more physical hosts that are hosting an Oracle RAC Database.
2.2.3 Receiving Requests Through Hardware Load Balancer
The following topics describe the hardware load balancer and its role in an enterprise deployment.
2.2.3.1 Purpose of the Hardware Load Balancer (LBR)
The following topics describe the types of requests handled by the hardware load balancer in an enterprise deployment.
2.2.3.1.1 HTTP Requests from the Internet to the Web server instances in the Web tier
The hardware load balancer balances the load on the Web tier by receiving requests to a single virtual host name and then routing each request to one of the Web server instances, based on a load balancing algorithm. In this way, the load balancer ensures that no one Web server is overloaded with HTTP requests.
For more information about the purpose of specific virtual host names on the hardware load balancer, see Summary of the Typical Load Balancer Virtual Server Names.
Note that in the reference topology, only HTTP requests are routed from the hardware load balancer to the Web tier. Secure Socket Layer (SSL) requests are terminated at the load balancer and only HTTP requests are forwarded to the Oracle HTTP Server instances. This guide does not provide instructions for SSL configuration between the load balancer and the Oracle HTTP Server instances or between the Web tier and the Application tier.
The load balancer provides high availability by ensuring that if one Web server goes down, requests will be routed to the remaining Web servers that are up and running.
Further, in a typical highly available configuration, the hardware load balancers are configured such that a hot standby device is ready to resume service in case a failure occurs in the main load balancing appliance. This is important because for many types of services and systems, the hardware load balancer becomes the unique point of access to make invocations and, as a result, becomes a single point of failure (SPOF) for the whole system if it is not protected.
2.2.3.1.2 Specific internal-only communications between the components of the Application tier
In addition, the hardware load balancer routes specific communications between the Oracle Fusion Middleware components and applications on the application tier. The internal-only requests are also routed through the load balancer, using a unique virtual host name.
2.2.3.2 Summary of the Typical Load Balancer Virtual Server Names
In order to balance the load on servers and to provide high availability, the hardware load balancer is configured to recognize a set of virtual server names. As shown in the diagram, the following virtual server names are recognized by the hardware load balancer in this topology:
-
wcc.example.com- This virtual server name is used for all incoming traffic.Users enter this URL to access the Oracle Fusion Middleware product you have deployed and the custom applications available on this server. The load balancer then routes these requests (using a load balancing algorithm) to one of the servers in the Web tier. In this way, the single virtual server name can be used to route traffic to multiple servers for load balancing and high availability of the Web servers instances.
-
wccinternal.example.com- This virtual server name is for internal communications only.The load balancer uses its Network Address Translation (NAT) capabilities to route any internal communication from the Application tier components that are directed to this URL. This URL is not exposed to external customers or users on the Internet. Each product has specific uses for the internal URL, so in the deployment instructions, we prefix it with the product name.
-
admin.example.com- This virtual server name is for administrators who need to access the Oracle Enterprise Manager Fusion Middleware Control and Oracle WebLogic Server Administration Console interfaces.This URL is known only to internal administrators. It also uses the NAT capabilities of the load balancer to route administrators to the active Administration Server in the domain.
For the complete set of virtual server names you must define for your topology, see the chapter that describes the product-specific topology.
2.2.3.3 HTTPS versus HTTP Requests to the External Virtual Server Name
Note that when you configure the hardware load balancer, a best practice is to assign the main external URL (for example, http://myapplication.example.com) to port 80 and port 443.
Any request on port 80 (non-SSL protocol) should be redirected to port 443 (SSL protocol). Exceptions to this rule include requests from public WSDLs. For more information, see Configuring Virtual Hosts on the Hardware Load Balancer.
2.2.4 Understanding the Web Tier
The Web tier of the reference topology consists of the Web servers that receive requests from the load balancer. In the typical enterprise deployment, at least two Oracle HTTP Server instances are configured in the Web tier. The following topics provide more detail.
2.2.4.1 Benefits of Using Oracle HTTP Server Instances to Route Requests
A Web tier with Oracle HTTP Server is not a requirement for many of the Oracle Fusion Middleware products. You can route traffic directly from the hardware load balancer to the WLS servers in the Application Tier. However, a Web tier does provide several advantages, which is why it is recommended as part of the reference topology:
-
The Web tier provides DMZ public zone, which is a common requirement in security audits. If a load balancer routes directly to the WebLogic Server, requests move from the load balancer to the application tier in one single HTTP jump, which can cause security concerns.
-
The Web tier allows the WebLogic Server cluster membership to be reconfigured (new servers added, others removed) without having to change the Web server configuration (as long as at least some of the servers in the configured list remain alive).
-
Oracle HTTP Server delivers static content more efficiently and faster than WebLogic Server; it also provides FTP services, which are required for some enterprise deployments, as well as the ability to create virtual hosts and proxies via the Oracle HTTP Server configuration files.
-
Oracle HTTP Server provides HTTP redirection over and above what WebLogic Server provides. You can use Oracle HTTP Server as a front end against many different WebLogic Server clusters, and in some cases, control the routing via content based routing.
-
Oracle HTTP Server provides the ability to integrate single sign-on capabilities into your enterprise deployment. For example, you can later implement single sign-on for the enterprise deployment, using Oracle Access Manager, which is part of the Oracle Identity and Access Management family of products.
-
Oracle HTTP Server provides support for WebSocket connections deployed within WebLogic Server.
For more information about Oracle HTTP Server, see Introduction to Oracle HTTP Server in Oracle Fusion Middleware Administering Oracle HTTP Server.
2.2.4.2 Configuration of Oracle HTTP Server in the Web Tier
Starting with Oracle Fusion Middleware 12c, the Oracle HTTP Server software can be configured in one of two ways: as part of an existing Oracle WebLogic Server domain or in its own standalone domain. Each configuration offers specific benefits.
When you configure Oracle HTTP Server instances as part of an existing WebLogic Server domain, you can manage the Oracle HTTP Server instances, including the wiring of communications between the Web servers and the Oracle WebLogic Server Managed Servers using Oracle Enterprise Manager Fusion Middleware Control. When you configure Oracle HTTP Server in a standalone configuration, you can configure and manage the Oracle HTTP Server instances independently of the application tier domains.
For this enterprise deployment guide, the Oracle HTTP Server instances are configured as separate standalone domains, one on each Web tier host. You can choose to configure the Oracle HTTP Server instances as part of the application tier domain, but this enterprise deployment guide does not provide specific steps to configure the Oracle HTTP Server instances in that manner.
For more information, see About Oracle HTTP Server in Oracle Fusion Middleware Installing and Configuring Oracle HTTP Server.
2.2.4.3 About Mod_WL_OHS
As shown in the diagram, the Oracle HTTP Server instances use the WebLogic Proxy Plug-In (mod_wl_ohs) for proxying HTTP requests from Oracle HTTP Server to the Oracle WebLogic Server Managed Servers in the Application tier.
For more information, see What are Oracle WebLogic Server Proxy Plug-Ins? in Oracle Fusion Middleware Using Oracle WebLogic Server Proxy Plug-Ins 12.2.1.1.
2.2.5 Understanding the Application Tier
The application tier consists of two physical host computers, where Oracle WebLogic Server and the Oracle Fusion Middleware products are installed and configured. The application tier computers reside in the secured zone between firewall 1 and firewall 2.
The following topics provide more information.
2.2.5.1 Configuration of the Administration Server and Managed Servers Domain Directories
Unlike the Managed Servers in the domain, the Administration Server uses an active-passive high availability configuration. This is because only one Administration Server can be running within an Oracle WebLogic Server domain.
In the topology diagrams, the Administration Server on HOST1 is in the active state and the Administration Server on HOST2 is in the passive (inactive) state.
To support the manual fail over of the Administration Server in the event of a system failure, the typical enterprise deployment topology includes:
-
A Virtual IP Address (VIP) for the routing of Administration Server requests
-
The configuration of the Administration Server domain directory on a shared storage device.
In the event of a system failure (for example a failure of HOST1), you can manually reassign the Administration Server VIP address to another host in the domain, mount the Administration Server domain directory on the new host, and then start the Administration Server on the new host.
However, unlike the Administration Server, there is no benefit to storing the Managed Servers on shared storage. In fact, there is a potential performance impact when Managed Server configuration data is not stored on the local disk of the host computer.
As a result, in the typical enterprise deployment, after you configure the Administration Server domain on shared storage, a copy of the domain configuration is placed on the local storage device of each host computer, and the Managed Servers are started from this copy of the domain configuration. You create this copy using the Oracle WebLogic Server pack and unpack utilities.
The resulting configuration consists of separate domain directories on each host: one for the Administration Server (on shared storage) and one for the Managed Servers (on local storage). Depending upon the action required, you must perform configuration tasks from one domain directory or the other.
For more information about structure of the Administration Server domain directory and the Managed Server domain directory, as well as the variables used to reference these directories, see Understanding the Recommended Directory Structure for an Enterprise Deployment.
There is an additional benefit to the multiple domain directory model. It allows you to isolate the Administration Server from the Managed Servers. By default, the primary enterprise deployment topology assumes the Administration Server domain directory is on one of the Application Tier hosts, but if necessary, you could isolate the Administration Server further by running it from its own host, for example in cases where the Administration Server is consuming high CPU or RAM. Some administrators prefer to configure the Administration Server on a separate, dedicated host, and the multiple domain directory model makes that possible.
2.2.5.2 About the Node Manager Configuration in a Typical Enterprise Deployment
Starting with Oracle Fusion Middleware 12c, you can use either a per domain Node Manager or a per host Node Manager. The following sections of this topic provide more information on the impact of the Node Manager configuration on a typical enterprise deployment.
Note:
For general information about these two types of Node Managers, see Overview in Oracle Fusion Middleware Administering Node Manager for Oracle WebLogic Server.
About Using a Per Domain Node Manager Configuration
In a per domain Node Manager configuration—as opposed to a per host Node Manager configuration—you actually start two Node Manager instances on the Administration Server host: one from the Administration Server domain directory and one from the Managed Servers domain directory. In addition, a separate Node Manager instance runs on each of the other hosts in the topology.
The Node Manager controlling the Administration Server uses the listen address of the virtual host name created for the Administration Server. The Node Manager controlling the Managed Servers uses the listen address of the physical host. When the Administration Server fails over to another host, an additional instance of Node Manager is started to control the Administration Server on the failover host.
The key advantages of the per domain configuration are an easier and simpler initial setup of the Node Manager and the ability to set Node Manager properties that are unique to the Administration Server. This last feature was important in previous releases because some features, such as Crash Recovery, applied only to the Administration Server and not to the Managed servers. In the current release, the Oracle SOA Suite products can be configured for Automated Service Migration, rather than Whole Server Migration. This means the Managed Servers, as well as the Administration Server, can take advantage of Crash Recovery, so there is no need to apply different properties to the Administration Server and Managed Server domain directories.
Another advantage is that the per domain Node Manager provides a default SSL configuration for Node Manager-to-Server communication, based on the Demo Identity store created for each domain.
About Using a Per Host Domain Manager Configuration
In a per-host Node Manager configuration, you start a single Node Manager instance to control the Administration Server and all Managed Servers on a host, even those that reside in different domains. This reduces the footprint and resource utilization on the Administration Server host, especially in those cases where multiple domains coexist on the same machine.
A per-host Node Manager configuration allows all Node Managers to use a listen address of ANY, so they listen on all addresses available on the host. This means that when the Administration Server fails over to a new host, no additional configuration is necessary. The per host configuration allows for simpler maintenance, because you can update and maintain a single Node Manager properties file on each host, rather than multiple node manager property files.
The per-host Node Manager configuration requires additional configuration steps. If you want SSL for Node Manager-to-Server communication, then you must configure an additional Identity and Trust store, and it also requires using Subject Alternate Names (SAN), because the Node Manager listens on multiple addresses. Note that SSL communications are typically not required for the application tier, because it is protected by two firewalls.
2.2.5.3 About Using Unicast for Communications within the Application Tier
Oracle recommends the unicast communication protocol for communication between the Managed Servers and hosts within the Oracle WebLogic Server clusters in an enterprise deployment. Unlike multicast communication, unicast does not require cross-network configuration and it reduces potential network errors that can occur from multicast address conflicts as well.
When you consider using the multicast or unicast protocol for your own deployment, consider the type of network, the number of members in the cluster, and the reliability requirements for cluster membership. Also consider the following benefits of each protocol.
Benefits of unicast in an enterprise deployment:
-
Uses a group leader that every server sends messages directly to. This leader is responsible for retransmitting the message to every other group member and other group leaders, if applicable.
-
Works out of the box in most network topologies
-
Requires no additional configuration, regardless of the network topology.
-
Uses a single missed heartbeat to remove a server from the cluster membership list.
Benefits of multicast in an enterprise deployment:
-
Multicast uses a more scalable peer-to-peer model where a server sends each message directly to the network once and the network makes sure that each cluster member receives the message directly from the network.
-
Works out of the box in most modern environments where the cluster members are in a single subnet.
-
Requires additional configuration in the router(s) and WebLogic Server (that is., Multicast TTL) if the cluster members span more than one subnet.
-
Uses three consecutive missed heartbeats to remove a server from the cluster membership list.
Depending on the number of servers in your cluster and on whether the cluster membership is critical for the underlying application (for example in session-replication intensive applications or clusters with intensive RMI invocations across the cluster), each model may behave better.
Consider whether your topology is going to be part of an Active-Active disaster recovery system or if the cluster is going to traverse multiple subnets. In general, unicast will behave better in those cases.
For more information see the following resources:
-
Configuring Multicast Messaging for WebLogic Server Clusters in Oracle Fusion Middleware High Availability Guide
-
One-to-Many Communication Using Unicast in Oracle Fusion Middleware Administering Clusters for Oracle WebLogic Server
2.2.5.4 Understanding OPSS and Requests to the Authentication and Authorization Stores
Many of the Oracle Fusion Middleware products and components require an Oracle Platform Security Services (OPSS) security store for authentication providers (an identity store), policies, credentials, keystores, and for audit data. As a result, communications must be enabled so the Application tier can send requests to and from the security providers.
For authentication, this communication is to an LDAP directory, such as Oracle Internet Directory (OID) or Oracle Unified Directory (OUD), which typically communicates over port 389 or 636. When you configure an Oracle Fusion Middleware domain, the domain is configured by default to use the WebLogic Server Authentication provider. However, for an enterprise deployment, you must use a dedicated, centralized LDAP-compliant authentication provider.
For authorization (and the policy store), the location of the security store varies, depending upon the tier:
-
For the application tier, the authorization store is database-based, so frequent connections from the Oracle WebLogic Server Managed Servers to the database are required for the purpose of retrieving the required OPSS data.
-
For the Web tier, the authorization store is file-based, so connections to the database are not required.
For more information about OPSS security stores, see the following sections of Oracle Fusion Middleware Securing Applications with Oracle Platform Security Services:
2.2.6 About the Data Tier
In the Data tier, an Oracle RAC database runs on the two hosts (DBHOST1 and DBHOST2). The database contains the schemas required by the Oracle WebCenter Content components and the Oracle Platform Security Services (OPSS) policy store.
You can define multiple services for the different products and components in an enterprise deployment to isolate and prioritize throughput and performance accordingly. In this guide, one database service is used as an example. Furthermore, you can use other high availability database solutions to protect the database:
-
Oracle Data Guard; for more information, see the Introduction to Oracle Data Guard in Oracle Data Guard Concepts and Administration.
-
Oracle RAC One Node; for more information, see Overview of Oracle RAC One Node in Oracle Real Application Clusters Administration and Deployment Guide.
These solutions above provide protection for the database beyond the information provided in this guide, which focuses on using an Oracle RAC Database, given the scalability and availability requirements that typically apply to an enterprise deployment.
For more information about using Oracle Databases in a high availability environment, see Database Considerations in Oracle Fusion Middleware High Availability Guide.