13 Managing Security for Records
For information on administering Oracle WebCenter Content system security, including system-level roles, permissions, accounts, and ACLs, see Administering Oracle WebCenter Content.
This chapter includes the following topics:
13.1 Understanding Records Security
Multiple layers of security are available to control access to content. System security combined with security permissions and privileges for users allow you to customize the security easily. The intersection of all security mechanisms in place are used to determine user privileges with the strictest setting prevailing.
This section discusses the following topics:
13.1.1 Retention Management in an Organization
Figure 13-1 shows a typical retention management structure in an organization.
Figure 13-1 Typical Retention Management Organization
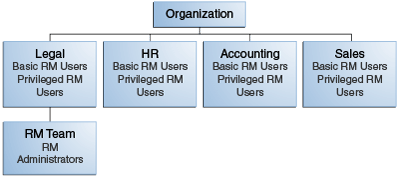
Description of "Figure 13-1 Typical Retention Management Organization"
Most people in the various departments of an organization can file content or check in content items, search for items, and view them. These are basic Records Users.
A much smaller group of people is typically granted rights to perform some additional functions not allowed for basic users (for example, altering classifications or creating triggers or retention schedules). These are people with the Records Officer right.
A very limited number of people are administrators, who are typically responsible for setting up and maintaining the management infrastructure. Records Administrators have the widest range of rights to perform management tasks. For example, they can usually perform all and disposition actions, including those assigned to others. The administrators are often in the legal department of an organization, which can drive the efforts for effective and efficient management.
The software comes with predefined management roles called rma, rmalocalrecordsofficer, and rmaadmin, designated in the documentation as Records User, Records Officer, and Records Administrator. Each of these standard roles provides a default set of permissions and rights, which coincide with the typical responsibilities of basic users, privileged users, and administrators, respectively. These roles can easily be modified to suit specific management needs. New roles can be created with assigned management rights or different management rights can be given to existing roles.
Users without specific rights can still apply life cycles to content items.
Note:
Record management consists of more than just software. You also need to have the appropriate organizational structures and policies in place in your organization.
13.1.2 General Security Settings
Overall security settings are configured on the Configure Retention Settings page. The default values on that page are based on the installation level that was chosen. Security preferences set on that page are in addition to those provided with Oracle WebCenter Content. PCM security is set using the Records security measures.
Note:
After a production environment is underway, it is recommended that the security settings for ACLs and other default settings not be changed. Doing so can cause unforeseen consequences.
To configure what security settings are enabled, choose Records then Configure then Settings.
-
To use Access Control List Security, select ACL-based security.
-
To activate the default security, select Default Content Server security on Categories, Folders, and Triggers.
-
(Required for DOD 5015.2 compliance): To use supplemental markings, select Supplemental Marking. To make users match all supplemental markings, select User must match all Supplemental Markings. To allow a user to match only one supplemental marking, deselect the check box.
-
To create custom security fields, select Custom Security Fields.
-
To use classified security, select Classified Security.
When done, click Submit Update.
13.1.2.1 Security Groups
A security group defines security for a group of content. Oracle WebCenter Content: Records is shipped with a predefined security group called RecordsGroup. This group defines security for a group of content designated as that being tracked and/or retained.
Users with the predefined Records User, Records Officer, or Records Administrator roles have read and write permission (RW) to the RecordsGroup security group. Users with the Records Administrator role have read, write, delete, and admin permission (RWDA) to this security group.
Note:
Even though the default Records User and Records Officer roles appear to be identical, they are not. The default Records Officer role has subadministrator access to certain administrator functions that the default Records User role does not (for example, creating triggers and folders).
13.1.2.2 Aliases
When the product software is enabled, several aliases are created to help administrators manage large groups of people. Although the aliases are created, no default users are added to those groups. An administrator should add users as needed to the following alias lists:
-
OffSiteRequestReviewGroup
-
ReservationGroup
-
RmaReviewersGroup
Several default aliases are also created if the FOIA/PA functionality is enabled. Default users are added to those alias lists but the users themselves are not created automatically. An administrator will need to create those users and assign appropriate permissions to them:
-
FOIAOfficers
-
FOIAProcessors
-
FOIASpecialists
-
JAG
13.1.2.3 Access Control Lists (ACLs)
Note:
Enabling or disabling ACLs affects existing ACL settings system-wide. For example, if ACLs are enabled in Oracle WebCenter Content and the Records system is configured to one of the DoD settings (which re-enables ACLs), the Oracle WebCenter Content ACLs are overridden. And if the Typical or Minimal Record settings are used, ACLs are disabled because ACL-based security is not enabled by default for those options. It is enabled by default for the DoD options.
ACLs control user and group access permissions for triggers, categories, and record folders. ACLs can be assigned for each category, folder, and trigger.
Be aware that searching for items takes more time when using ACLs as well as other security features, such as custom security fields and supplemental markings. When possible, use the default Oracle WebCenter Content security features and consider disabling ACLs for faster search retrieval performance.
Note that ACLs in the Records system behave differently than those in Oracle WebCenter Content in the following ways:
-
Oracle WebCenter Content administrative users or users with the RWDA rights assigned to them have no automatic rights in the Records system. All users must have rights defined for them when using ACLs in the Records system.
-
Oracle WebCenter Content: Records ACLs are hierarchical. If ACLs are enabled only in the Records system (and not in Oracle WebCenter Content), then ACLs are defined only on categories and folders, not directly on content. ACL rights are propagated down to content based on all rights assigned to the parent category or folder.
The UseEntitySecurity configuration variable is used to enable Oracle WebCenter Content ACL functionality. Set that variable to true to enable that feature.
The SpecialAuthGroups configuration variable is used to determine what security groups can be used with ACLs. For example, SpecialAuthGroups=Private, RecordsGroup enables those security groups to be used with ACLs. By default, RecordsGroup is set as the SpecialAuthGroup value when Oracle WebCenter Content: Records is enabled.
13.1.2.3.1 Setting ACLs During Software Use
ACLs for individual users and groups and aliases can be adjusted while setting up elements of the Records system. Not all procedures allow the setting of all three types of permissions. The following procedure can be followed to adjust ACLs regardless of which type of permission are being set (user, group, or alias).
- In the Group, User, or alias permission section of the Access Control Edit Section of the page in use, begin typing the user name of the person to add. A list appears and the user can be selected. Or type two asterisks (**) in the name field or group field. A list of users and groups appears.
- Scroll to the name to use and click Add User, Add Alias or Add.
- To the right of the name is a grouping of permissions. Click on a permission to add or remove it.
- To remove a user or group from the permissions box, click the X next to the name.
13.1.3 Security Roles and Definitions
The following security elements are used to define user roles and permissions:
-
Predefined user roles. Each role comes with a default set of permissions and rights, but these can be modified to suit specific needs. These include the following roles:
-
rma, generally assigned to basic users. It allows them to perform basic management tasks. In this documentation, Records User is a term used to designate the person given this role.
-
rmalocalrecordsofficer, generally assigned to users who need access to additional functionality (for example, creating triggers or folders, and modifying content attributes). In this documentation, Records Officer is a term used to designate a person given this role. In previous versions of this product, this was the Records Privileged role.
-
rmaadmin, generally assigned to administrators who set up and maintain the infrastructure and environment. In this documentation, Records Administrator is a term used to designate the person given this role.
-
pcmrequestor, generally assigned to users who have all the permissions of basic users without a PCM role but are also granted additional rights to perform some functions not allowed for basic users (for example, making reservations for physical items). Users with the pcmrequestor role have read and write permissions (RW) for the special RecordsGroup security group. In this documentation, PCM Requestor is a term used to designate a person given this role.
-
pcmadmin, generally assigned to administrators who are responsible for setting up and maintaining the physical content management infrastructure and environment. These users have the widest range of rights to perform physical content management tasks (for example, setting up the storage space, editing and deleting reservations, and printing user labels). Users with the PCM Administrator role have read, write, delete, and admin permissions (RWDA) for the special RecordsGroup security group. In this documentation, PCM Administrator is a term used to designate a person given this role.
-
-
Rights control access to functions assigned to user roles. The predefined roles have a default set of rights assigned to them, but the rights can be modified to restrict or expand their access to functions.
-
Security groups define security on a group of content. This software comes with a predefined security group called RecordsGroup. Users with the predefined Records User or Records Officer roles have read and write permission (RW) to the RecordsGroup security group. Users with the Records Administrator role have read, write, delete, and admin permission (RWDA) to this security group.
-
Access control lists (ACLs) manage the security model on dispositions (ACLs are an optional feature available during configuration).ACLs can be assigned to folders, triggers, and retention categories. ACLs are used to control user and group access permissions for triggers, categories, and folders. The ACL can be assigned for each category, folder, and trigger that is created.
13.1.4 Rights and Roles for Records Tasks
Rights define what actions users can perform on content items. This section describes the default rights and roles for tasks involved in using Records. The default roles are rma (User), rmalocalrecordsofficer (Officer), and rmaadmin (Admin).
To assign rights to user roles:
- Choose Admin Applets from the Administration menu.
- Click the User Admin icon and choose Security then Permissions by Role from the menu.
- Click the role to review or modify.
- Click Edit RMA Rights then set the appropriate rights by selecting check boxes on the various tabs.
- Click OK when done.
13.1.4.1 Triggers
The following table describes the default rights assigned to the default roles for tasks involving triggers.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
View information about triggers |
Admin.Triggers or Admin.RecordManager |
X |
X |
|
|
Create a trigger |
Admin.Triggers |
X |
X |
|
|
Edit a trigger |
Admin.Triggers |
X |
X |
|
|
Delete a trigger |
Admin.Triggers and Delete permission for the trigger's security group. The Delete permission is not granted by default. |
X |
X |
13.1.4.2 Periods
The following table describes the default rights assigned to the default roles for tasks involving periods.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
View information about periods |
Admin.Triggers or Admin.RecordManager |
X |
X |
|
|
Create a period |
Admin.RecordManager |
X |
||
|
Edit a custom period |
Admin.RecordManager |
X |
||
|
Delete a custom period |
Admin.RecordManager |
X |
13.1.4.3 Supplemental Markings
The following table describes the default rights assigned to the default roles for tasks involving supplemental markings.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
View information about supplemental markings |
Admin.Triggers or Admin.RecordManager |
X |
X |
|
|
Enable/disable supplemental markings |
Admin.RecordManager |
X |
||
|
Create/edit a supplemental markings |
Admin.RecordManager |
X |
||
|
Delete a supplemental marking |
Admin.RecordManager |
X |
13.1.4.4 Security Classifications
The following table describes the default rights assigned to the default roles for tasks involving security classifications.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
View information about classifications |
Admin.RecordManager and Admin.SecurityClassifications |
X |
||
|
Enable/disable classifications |
Admin.RecordManager and Admin.SecurityClassifications |
X |
||
|
Create/edit a classification |
Admin.RecordManager and Admin.SecurityClassifications |
X |
||
|
Delete a classification |
Admin.RecordManager and Admin.SecurityClassifications |
X |
||
|
Reorder security classifications |
Admin.RecordManager and Admin.SecurityClassifications |
X |
13.1.4.5 Custom Security Fields
The following table describes the default rights assigned to the default roles for tasks involving security classifications.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
View information about a custom security field |
Admin.Triggers or Admin.RecordManager |
X |
X |
|
|
Enable/disable custom security fields |
Admin.RecordManager |
X |
||
|
Create/edit a custom security field |
Admin.RecordManager |
X |
||
|
Delete a custom security field |
Admin.RecordManager |
X |
13.1.4.6 Custom Category or Folder Metadata Fields
The following table describes the default rights assigned to the default roles for tasks involving custom metadata fields.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Create/edit a custom metadata field |
Admin.RecordManager |
X |
||
|
Delete a custom metadata field |
Admin.RecordManager |
X |
13.1.4.7 Classification Guides
The following table describes the default rights assigned to the default roles for tasks involving classification guides.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
View information about classification guides |
Admin.ClassificationGuide |
X |
X |
|
|
Create/edit a classification guide |
Admin.ClassificationGuide |
X |
X |
|
|
Delete a classification guide |
Admin.ClassificationGuide |
X |
X |
|
|
View information about classification topics |
Admin.ClassificationGuide |
X |
X |
|
|
Create/edit a classification topic |
Admin.ClassificationGuide |
X |
X |
|
|
Delete a classification topic |
Admin.ClassificationGuide |
X |
X |
13.1.4.8 Freezes
The following table describes the default rights assigned to the default roles for tasks involving freezes.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
View information about freezes |
Admin.RecordManager |
X |
||
|
Create/edit a freeze |
Admin.RecordManager |
X |
||
|
Delete a freeze |
Admin.RecordManager and Delete permission for the freeze's security group. The Delete permission is not granted by default. |
X |
||
|
Send email notification about a freeze |
Admin.RecordManager |
X |
13.1.4.9 Series
The following table describes the default rights assigned to the default roles for tasks involving series.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Browse and view information about freezes |
Series.Read |
X |
X |
X |
|
Create/edit a series |
Series.Create, Series.Edit |
X |
||
|
Delete a series |
Series.Delete |
X |
||
|
Hide/unhide a series |
Series.Hide, Series.Unhide |
X |
||
|
Move a series |
Series.Move |
X |
13.1.4.10 Categories
The following table describes the default rights assigned to the default roles for tasks involving retention categories.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Browse and view information about retention categories, including disposition instructions |
Category.Read |
X |
X |
X |
|
Create/edit a retention category |
Category.Create, Category.Edit |
X |
||
|
Edit the review information for a retention category |
Category.Edit.Review |
X |
||
|
Delete a category |
Category.Delete |
X |
||
|
Apply disposition instructions to specific records in a category |
Category.Edit |
X |
||
|
Move a category |
Category.Move |
X |
13.1.4.11 Folders
The following table describes the default rights assigned to the default roles for tasks involving folders.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Browse and view information about folders |
Folder.Read |
X |
X |
X |
|
View the life cycle of a folder, the review history of a folder and the metadata history of a folder |
Folder.Read |
X |
X |
X |
|
Create a folder |
Folder.Create |
X |
X |
|
|
Edit a folder if author of the folder |
Folder.EditIfAuthor |
X |
||
|
Edit a folder if not author of the folder |
Folder.Edit |
X |
||
|
Edit the review information for a folder |
Folder.Edit.Review |
X |
X |
|
|
Delete a folder |
Folder.Delete |
X |
||
|
Move a folder |
Folder.Edit |
X |
||
|
Close/unclose a folder |
Folder.Open/Folder.Close |
X |
X |
|
|
Freeze/unfreeze a folder |
Folder.Freeze/Folder.Unfreeze |
X |
||
|
Cancel or expire a folder |
Folder.Edit |
X |
X |
|
|
Rescind or make a folder obsolete |
Folder.Edit |
X |
X |
|
|
Undo a folder's obsolescence status |
Folder.Edit |
X |
X |
|
|
Undo a folder's cutoff status |
Folder.UndoCutoff |
X |
||
|
Review a folder |
Admin.PerformPendingReviews |
X |
X |
|
|
Mark a folder as reviewed |
Folder.Edit |
X |
X |
|
|
Set dates (activation, expiration, delete, and approval) for a folder |
Folder.Edit |
X |
X |
|
|
Assign or remove supplemental markings on a folder |
Folder.Edit |
X |
X |
|
|
Apply a disposition rule to one or many folders |
Category.Edit |
X |
13.1.4.12 Content
The following table describes the default rights assigned to the default roles for tasks involving content.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Create or check in an item |
Record.Create |
X |
X |
X |
|
Search for an item |
Record.Read |
X |
X |
X |
|
Link items |
Record.CreateLink |
X |
X |
X |
|
Unlink items |
Record.Unlink |
X |
X |
|
|
Download a content item for viewing |
Record.Read |
X |
X |
X |
|
View information about content |
Record.Read |
X |
X |
X |
|
View the life cycle of an item, the review history of an item, the classification history of an item or the metadata history of an item |
Record.Read |
X |
X |
X |
|
Edit the review information for an item |
Record.EditReview |
X |
X |
|
|
Review the classification of an item |
Record.Edit |
X |
X |
|
|
Delete the metadata history of an item |
Record.DeleteHistoryFile |
X |
X |
|
|
Delete an item |
Record.Delete |
X |
||
|
Freeze/unfreeze a folder |
Record.Freeze/Record.Unfreeze |
X |
||
|
Cancel or expire an item |
Record.Edit |
X |
X |
|
|
Rescind or make an item obsolete |
Record.Edit |
X |
X |
|
|
Undo an item's obsolescence status |
Record.Edit |
X |
X |
|
|
Move an item to another category or folder. |
Record.Edit |
X |
X |
|
|
Edit record metadata before cutoff. Note: Non-record metadata can be edited after cutoff as well as before. |
Record.UndoCutoff |
X |
||
|
Upgrade or downgrade an item's classification status |
Record.Upgrade/Record.Downgrade |
X |
X |
|
|
Review an item |
Admin.PerformPendingReviews |
X |
X |
|
|
Remove supplemental markings |
Record.Edit |
X |
X |
|
|
Undo the cutoff status of an item |
Record.UndoCutoff |
X |
||
|
Undo the record status of an item |
Record.UndoRecord |
X |
13.1.4.13 Disposition Rules
The following table describes the default rights assigned to the default roles for tasks involving disposition rules.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
View disposition information |
Category.Read |
X |
X |
X |
|
Enable/disable user-friendly captions |
Admin.RecordManager |
X |
||
|
Create a rule |
Category.Create |
X |
||
|
Edit a rule |
Category.Edit |
X |
||
|
Delete a rule |
Category.Delete |
X |
||
|
Define a custom disposition rule |
Admin.CustomDispositionActions |
|||
|
Disabling a disposition rule |
Admin.CustomDispositionActions |
13.1.4.14 Archiving
The following table describes the default rights assigned to the default roles for tasks involving archiving.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Import an archive |
Admin.RetentionSchedulesArchive and other rights for specific items in the import |
X |
||
|
Export an archive |
Admin.RetentionSchedulesArchive and other rights for specific items in the export |
X |
13.1.4.15 Screening
The following table describes the default rights assigned to the default roles for tasks involving screening.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Enable/disable user-friendly captions |
Admin.RecordManager |
X |
||
|
Screen a category, folder, or content |
Any user can screen for items to which they have permission. |
13.1.4.16 Audit Trails
The following table describes the default rights assigned to the default roles for tasks involving audit trails.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Configure the audit trail |
Admin.Audit |
X |
||
|
Choose metadata fields to audit |
Admin.SelectMeta |
X |
||
|
Generate and view an audit trail |
Admin.Audit |
X |
||
|
Search an audit trail or an archived audit trail |
Admin.Audit |
X |
||
|
Set default metadata for audit trail check-in |
Admin.Audit |
X |
||
|
Check in and archive audit trail |
Admin.Audit, Admin.RecordManager |
X |
13.1.4.17 Links
The following table describes the default rights assigned to the default roles for tasks involving the configuration of links. Rights involved in using links are noted in Content.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Add a custom link type |
Admin.ConfigureLinkTypes |
X |
||
|
Edit a custom link type |
Admin.ConfigureLinkTypes |
X |
||
|
Delete a custom link type |
Admin.ConfigureLinkTypes |
X |
13.1.4.18 Reports
The following table describes the default rights assigned to the default roles for tasks involving the configuration of reports.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Create a user, role, group, or user-group report |
Admin.Reports |
X |
13.1.4.19 Customization
The Rma.Admin.Customization right is required to create custom dispositions, custom reports, or custom barcode actions. This right is not assigned by default to any role.
A detailed knowledge of services and their uses is required in order to customize your system.
13.1.4.20 General Configuration
The following table describes the default rights assigned to the default roles for tasks involving general product configuration.
| Task | Required RM Right | User | Officer | Admin |
|---|---|---|---|---|
|
Set the fiscal calendar |
Admin.RecordManager |
X |
||
|
Perform disposition actions (process events) |
Admin.RecordManager |
X |
||
|
Specify default review recipients |
Admin.RecordManager |
X |
13.1.5 Rights and Roles for PCM Tasks
This section describes the rights and roles for tasks encountered while using Physical Content Management.
The default roles provided with PCM are pcmrequestor (Requestor) and pcmadmin (PCM Admin).
13.1.5.1 Physical Item Management
The following table describes the default rights assigned to the default roles for tasks involving physical items.
Note that the ability to freeze or screen physical items are not enabled by default for any role. The menu options to perform these tasks are not visible until those rights are assigned to a role.
| Task | Required RM Right | Requestor | Admin |
|---|---|---|---|
|
View information about physical items |
PCM.Physical.Read and PCM.Storage.Read |
X |
X |
|
Create (check in) a physical item |
PCM.Physical.Create and PCM.Storage.Read |
X |
X |
|
Edit a physical item |
PCM.Physical.Edit and PCM.Storage.Read |
X |
X |
|
Move a physical item |
PCM.Physical.Edit, PCM.Physical.Move and PCM.Storage.Read |
X |
|
|
Delete a physical item |
PCM.Physical.Delete and PCM.Storage.Read |
X |
|
|
Search physical items |
PCM.Physical.Read and PCM.Storage.Read |
X |
X |
|
Print labels for physical items |
PCM.Admin.PrintLabel |
X |
|
|
Freeze or unfreeze physical items |
Record.Freeze/Record.Unfreeze |
||
|
To manually override freeze errors |
Admin.PerformActions |
||
|
To screen for physical items |
Admin.Screening |
13.1.5.2 Storage Space
The following table describes the default rights assigned to the default roles for tasks involving storage locations.
Note that the ability to import a storage hierarchy is not enabled by default for any role. The menu option to perform this task is not visible until that right is assigned to a role.
| Task | Required RM Right | Requestor | Admin |
|---|---|---|---|
|
View information about locations |
PCM.Storage.Read |
X |
X |
|
Create a location |
PCM.Storage.Create |
X |
|
|
Edit a location |
PCM.Storage.Edit |
X |
|
|
Delete a location |
PCM.Storage.Delete |
X |
|
|
Reserve a location |
PCM.Storage.Reserve |
X |
X |
|
Block a location |
PCM.Storage.Block |
X |
|
|
Print labels for a location |
PCM.AdminPrintLabel |
X |
|
|
Import batch-created storage hierarchy |
Admin.RetentionScheduleArchive |
13.1.5.3 Location, Media, and Object Types
The following table describes the default rights assigned to the default roles for tasks involving the creation of location, media, and object types.
| Task | Required RM Right | Requestor | Admin |
|---|---|---|---|
|
Set up location types |
PCM.Admin.Manager and PCM.Admin.LocationTypes |
X |
|
|
Set up object types |
PCM.Admin.Manager |
X |
|
|
Set up media types |
PCM.Admin.Manager |
X |
|
|
Set up custom metadata fields |
PCM.Admin.Manager |
X |
13.1.5.4 Reservations
The following table describes the default rights assigned to the default roles for tasks involving reservations.
| Task | Required RM Right | Requestor | Admin |
|---|---|---|---|
|
View reservation information |
PCM.Reservation.Read |
X |
X |
|
Create a reservation request |
PCM.Reservation.Create |
X |
X |
|
Edit a reservation request |
PCM.Reservation.Edit |
X |
|
|
Delete a reservation request |
PCM.Reservation.Delete |
X |
|
|
Process a reservation request |
PCM.Reservation.Process |
X |
|
|
Run a reservation request report |
PCM.Admin.Manager |
X |
|
|
Configure default metadata for reservations |
PCM.Admin.Manager |
X |
13.1.5.5 Chargebacks
The following table describes the default rights assigned to the default roles for tasks involving chargebacks.
| Task | Required RM Right | Requestor | Admin |
|---|---|---|---|
|
Set up chargeback types, payment types, and customers |
PCM.Admin.Manager and CBC.ChargeBacks.Admin |
X |
|
|
View information about chargebacks (transactions, invoices, and so on) |
PCM.Admin.Manager, CBC.ChargeBacks.Admin and CBC.ChargeBacks.Read |
X |
|
|
Create chargeback items (transactions, invoices, and so on) |
PCM.Admin.Manager, CBC.ChargeBacks.Admin and CBC.ChargeBacks.Read |
X |
|
|
Edit chargeback items (transactions, invoices, and so on) |
PCM.Admin.Manager, CBC.ChargeBacks.Admin and CBC.ChargeBacks.Edit |
X |
|
|
Delete chargeback items (transactions, invoices, and so on) |
PCM.Admin.Manager, CBC.ChargeBacks.Admin and CBC.ChargeBacks.Delete |
X |
|
|
Screen for charges |
PCM.Admin.Manager and CBC.ChargeBacks.Admin |
X |
|
|
Browse invoices |
PCM.Admin.Manager and CBC.ChargeBacks.Admin |
X |
|
|
Print invoices |
PCM.Admin.Manager and CBC.ChargeBacks.PrintInvoice |
X |
|
|
Adjust invoices |
PCM.Admin.Manager and CBC.ChargeBacks.Adjust |
X |
13.1.5.6 Barcodes
The following table describes the default rights assigned to the default roles for tasks involving barcodes and barcode labels.
| Task | Required RM Right | Requestor | Admin |
|---|---|---|---|
|
Process barcode files |
PCM.Barcode.Process |
X |
|
|
Print labels for users, storage locations, and physical locations |
PCM.Admin.PrintLabel |
X |
13.1.6 External Source Tasks and Defaults for Predefined Roles
For more information about adapters, see Managing the Oracle WebCenter Content Records Adapter.
The following rights are required to perform the following tasks:
-
To read external items, the ECM.External.Read right is required. This right is assigned by default to the ERM Requestor and ERM Administrator roles.
-
To create an external item, the ECM.External.Create right is required. This right is assigned by default to the ERM Requestor and ERM Administrator roles.
-
To edit an external item, the ECM.External.Edit right is required. This right is assigned by default to the ERM Administrator role.
-
To delete an external item, the ECM.External.Delete right is required. This right is assigned by default to the ERM Administrator role.
-
To perform administrative functions involving the external source, the ECM.External.Admin right is required. This right is assigned by default to the ERM Administrator role.
13.1.7 Permissions Matrix
The table below shows a matrix of content and retention schedule components, and the corresponding permissions for each predefined role. Supplemental markings have the most restrictive access capabilities.
| Objects and Retention Schedule Components | Subject to Additional Security of Type | Records User (rma) | Records Officer (recordsofficer) | Records Administrator (rmaadmin) |
|---|---|---|---|---|
|
Content Items |
Rights; supplemental markings; custom security field; ACLs |
RW |
RW |
RWDA |
|
Folders |
Rights; supplemental markings; ACLs |
R |
RWD |
RWD |
|
Categories |
Rights; supplemental markings; ACLs |
R |
R |
RWD |
|
Series |
Rights; ACLs |
R |
R |
RWD |
|
Triggers |
Rights; ACLs |
RW RWD permission required to delete triggers. |
RWDA Only custom triggers can be deleted. |
|
|
Periods |
Rights |
R |
RWD Only custom periods can be deleted. |
|
|
Supplemental markings |
Rights |
RWD |
||
|
Classification guides |
Rights |
RWD |
13.2 Setting Security Preferences
Security preferences are set on the Configure Retention Settings page. The security preferences set on that page are in addition to those provided with Oracle WebCenter Content. The available security depends on what type of installation was chosen (for example, Minimal or a DoD setting).
Note:
After your production environment is underway, it is recommended that you do not change the security settings for ACLs or the default security.
To configure security setting:
13.3 Assigning Rights to User Roles
The system is shipped with several predefined roles. Each of these roles has several default rights, which define what users with that role are allowed to do.
Some of the rights are interconnected. Enabling or disabling certain options automatically enables or disables other options. For example, if you disable the Record.Create option on the Record tab, some of the other options on that tab are disabled as well. Conversely, if you enable the Category.Create option on the Category tab and the Category.Read option is not yet enabled, it is enabled automatically.
The following sections describe the tabs where rights appear:
13.3.1 Series Tab
The following rights appear on the Series tab of the Edit Rights page:
-
Read: Allows the user to view information about a series. It is assigned by default to the Records User, Records Officer, and Records Administrator roles.
The following rights are assigned by default to the Records Administrator role.
-
Create: Allows the user to create a series.
-
Delete: Allows the user to delete a series.
-
Move: Allows the user to move a series.
-
Edit: Allows the user to edit a series.
-
Hide/Unhide: Allows the user hide and unhide a series.
13.3.2 Category Tab
The following rights appear on the Category tab of the Edit Rights page.
-
Read: Allows the user to view information about a retention category. It is assigned by default to the Records User, Records Officer, and Records Administrator roles.
The following rights are assigned by default to the Records Administrator role:
-
Create: Allows the user to create a retention category.
-
Delete: Allows a user to delete a retention category.
-
Move: Allows a user to move a retention category.
-
Edit: Allows a user to edit a retention category.
-
Edit Review: Allows a user to edit a retention category that is subject to review.
13.3.3 Folder Tab
For more information about folders, see Managing Folders.
The following rights appear on the Folder tab of the Edit Rights page:
-
Read: Allows the user to view information about a folder. It is assigned by default to the Records User, Records Officer, and Records Administrator roles.
-
EditIfAuthor: Allows a user to edit a folder, but only if the user is the author of that folder. It is not assigned by default to any role.
The following rights are assigned by default to the Records Officer and Records Administrator roles:
-
Create: Allows a user to create a folder.
-
Open/Close: Allows a user to open or close a folder.
-
Edit Review: Allows a user to edit a folder that is subject to review.
-
Move: Allows a user to move a folder.
The following rights are assigned by default to the Records Administrator role:
-
Edit: Allows a user to edit a folder, even if the user is not the author of that folder.
-
UndoCutoff: Allows a user to undo the cutoff of a folder.
-
Delete: Allows a user to delete a folder.
-
Freeze/Unfreeze: Allows a user to freeze and unfreeze a folder.
13.3.4 Record Tab
The following rights appear on the Record tab of the Edit Rights page. These rights are assigned by default to the Records User, Records Officer, and Records Administrator roles:
-
Read: Allows the user to view information about an item.
-
CreateLink: Allows the user to link content items.
-
Create: Allows a user to create content or check it in to the retention schedule.
-
Unlink: Allows a user to unlink content.
The following rights are assigned by default to the Records Officer, Records User, and Records Administrator roles:
-
Edit: Allows the user to edit content, including moving, canceling, expiring, rescinding, making obsolete, and reviewing.
-
EditReview: Allows a user to edit content that is subject to review.
-
DeleteHistoryFile: Allows a user to delete the metadata history file of content. This option is only available if the Classified Security option is enabled.
-
Upgrade/Downgrade: Allows a user to upgrade and downgrade the security classification of content. This option is only available if the Classified Security option has been enabled on the Configure Retention Settings page.
The following rights are assigned by default to the Records Administrator role:
-
UndoCutoff: Allows a user to undo the cutoff of an item.
-
Delete: Allows a user to delete content within the retention schedule.
-
Freeze/Unfreeze: Allows a user to freeze and unfreeze content.
-
UndoRecord: Allows a user to undo the status of content.
13.3.5 Admin Tab
The following rights appear on the Admin tab of the Edit Rights page.
-
PerformPendingReviews: Allows a user to perform pending reviews. This right is assigned by default to the Records Officer, Records User, and Records Administrator roles. See Assigning Rights to User Roles.
-
PrivilegedEnvironment: Allows a user to set the de-classification time frame. For details, see Assigning Rights to User Roles. This right is assigned by default to the Records Officer and Records Administrator roles. This option is only available if the Classified Security option has been enabled on the Configure Retention Settings page.
-
ClassificationGuide: Allows a user to work with classification guides. This right is assigned by default to the Records Officer and Records Administrator roles.
-
Triggers: Allows the user to work with global triggers, custom direct triggers, and indirect triggers. For details, see Assigning Rights to User Roles. To delete a trigger, Delete permission (D) for the trigger's security group is also required. This right is assigned by default to the Records Officer and Records Administrator roles.
-
ShareFavorites: Allows users to share the contents of their Favorites list with other users. This right is assigned by default to the Records Officer and Records Administrator roles.
The following rights are assigned by default to the Records Administrator role:
-
RecordManager: Allows a user to configure several settings and also set up and administer periods, supplemental markings, security classifications, custom security fields, custom category and folder metadata fields, classification guides and freezes.
-
Screening: Allows a user to screen retention categories, folders, and content.
-
PerformActions: Allows a user to process content assignments.
-
SelectMeta: Allows a user to specify metadata fields to be audited.
-
Reports: Allows a user to generate user and group reports.
-
RetentionScheduleArchive: Allows a user to import and export a retention schedule archive.
-
SelectAuthor: Allows a user to select a different filer (author) for a category than him/herself.
-
Audit: Allows a user to work with audit trials.
-
ConfigureLinkTypes: Allows a user to manage custom content links.
-
AllowDispositionUpgrade/Downgrade: Allows a user to perform upgrade and downgrade classification actions.
The following rights are not assigned by default to any role.
-
NoPostFilterSearch: Allows users to unfilter search results. The results include content the user has no access to based on security classifications, supplemental markings, custom security fields, and ACLs. If the user has no access to a content item in the search results, clicking on it results in an access denied error. By enabling this option, search queries are executed much faster because no complex post-filtering must be performed.
Users with this right can still only access content items they have been explicitly granted access privileges to based on security groups and accounts. They will see other results in the search results list, but cannot access them. They may also see some metadata information about the content item (for example, their title), which may interfere with an organization's security model.
-
NoSecurity: Allows users to become immune to security classifications, supplemental markings, custom security fields, and ACLs. Their access to content is unrestricted by these security features. In addition, this option turns off search post-filtering, so search results include content the user has not been explicitly granted access to. For example, a user would have access to content marked as Top Secret even if that security classification has not been assigned to the user. This right can be used to give system administrators the privilege to access every content item in the system.
Access to content items continues to be restricted by security groups and accounts.
-
Customization: Allows users to define custom disposition actions or to delete any disposition action. Also allows users to define custom reports.
-
SecurityClassifications: new installs only. If enabled (with the Admin.RecordManager option), the user is allowed to set up security classification levels. This option is only available if the Classified Security option is enabled.
-
GetAllFilePlan: Allows a user to get all series, categories, and folders when the GET_FILE_PLAN_ALL service is called. Without this right, inaccessible objects are excluded. The service is typically used by adapters.
Note:
When a user has Admin permission to a security group but does not have the Admin.SelectAuthor right, the user is still able to select an author at checkin. The Admin.SelectAuthor right is used only to add that functionality to a user who does not have Admin permission to a group.
13.3.6 CBC Tab
Chargebacks are used with Physical Content Management, which is only available when that software is enabled.
The following rights are assigned by default to the PCM Administrator role:
-
ChargeBacks.Read: Allows the user to view information about chargeback-related items (transactions, invoices, and so on).
-
ChargeBacks.Create: Allows a user to create chargeback-related items.
-
ChargeBacks.Edit: Allows a user to edit chargeback-related items.
-
ChargeBacks.Delete: Allows users to delete chargeback-related items.
-
ChargeBacks.PrintInvoices: Allows users to print invoices.
-
ChargeBacks.MarkPaid: Allows users to mark invoices as paid.
-
ChargeBacks.Adjust: Allows users to manually adjust invoices.
-
ChargeBacks.Admin: Allows users to perform administrative tasks such as define new payment types, define customers, and so on.
13.3.7 PCM Tab
The following rights are assigned by default to the PCM Requestor and PCM Administrator roles:
-
Physical.Read: Allows the user to view information about physical items.
-
Physical.Create: Allows a user to create physical items.
-
Physical.Edit: Allows a user to edit physical items.
-
Storage.Read: Allows users to view information about a storage location.
-
Storage.Reserve: Allows users to reserve a storage location.
-
Reservation.Read: Allows users to view information about reservations.
-
Reservation.Create: Allows users to create reservations.
-
Reservation.Edit: Allows users to alter reservations.
The following rights are assigned by default to the PCM Administrator role only:
-
Physical.Move: Allows users to move a physical item (change the location)
-
Physical.Delete: Allows users to delete physical items.
-
Storage.Create: Allows users to create new storage.
-
Storage.Edit: Allows users to edit an existing storage location.
-
Storage.Delete: Allows users to delete a storage location.
-
Storage.Block: Allows users to block or unblock a storage location.
-
Reservation.Delete: Allows users to delete reservations.
-
Reservation.Process: Allows users to process reservations by modifying the status of request items.
-
Barcode.Process: Allows users to process barcode files.
-
Admin.Manager: Allows a user to access all PCM administrative functions.
-
Admin.Location.Types: Allows users to configure location types, providing the user also has the Admin.Manager right.
-
Admin.PrintLabel: Allows users to generate labels for users, locations, and physical items.
13.3.8 ECM Tab
The following rights are assigned by default to the ERM Requestor and ERM Administrator roles:
-
External.Read: Allows the user to view information about external items.
-
External.Create: allows a user to create external items.
-
External.Edit: allows a user to edit external items.
The following rights are assigned by default to the ERM Administrator role only:
-
External.Delete: allows users to delete external items.
-
External.Admin: allows users to perform administrative tasks.
13.4 Specifying PCM Barcode Values for Users
Barcodes are used with Physical Content Management, which is only available when that software is enabled.
By default, the barcode value for a user consists of a user's login name in all upper-case letters, for example JSMITH or MJONES. If you do not want to use the login name of a user as the barcode value, use the User Admin utility to specify a different value for the user.
This is especially useful for login names containing characters other than the basic letters (a-z, A-Z) or numbers (0-9) (for example, accented letters such as kmüller). By default, the barcode values generated for such users include hexadecimal representations of the accented letters (for example, KMC39CLLER). To avoid this behavior set specific barcode values for these users (for example, KMULLER), which are then used rather than the (converted) user login names.
You can run the Update Users with no Barcode batch service to automatically set the barcode values for all users who currently do not have a barcode value. This is useful for users who are already in the system before Physical Content Management was enabled. The barcode values are set in accordance with the rules above.
To manually set a specific barcode value for a user:
13.5 Classified Security
The classification of content is the process of identifying and safeguarding content requiring protection against unauthorized disclosure, for example, because it contains information sensitive to the national security of the United States or sensitive to the stability of a company.
Classifications, supplemental markings, and classification guides provide further security and are used to organize documents that are considered classified, for either government or corporate purposes.
The following sections discuss classified security:
13.5.1 Security Classifications
Security classification can be an additional way to restrict access to content by using supplemental markings and custom security fields.
Several classification features are available to handle and process classified content in accordance with the Chapter 4 requirements of the DoD 5015.2 specification. Several built-in classifications (Top Secret, Secret, and Confidential) are available, but custom classifications can also be created.
Content is either classified, unclassified, or declassified. Classified content has an initial classification and a current classification. Unclassified content is not and has never been classified. Declassified content was formerly classified.
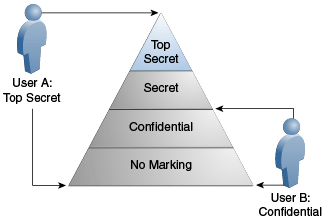
The standard security categories (classification scheme), from highest to lowest, are Top Secret, Secret, Confidential, and No markings (that is, unclassified).
Like supplemental markings, classified security can be enabled or disabled at any time. After enabling, custom security classifications can be created. If any additional security classifications are created, indicate the classification place within the marking hierarchy.
To enable security, select Classified Security on the Configure Retention Settings page. Click Submit.
Caution:
Disabling classified security puts sensitive classified information at risk of being accessed by unauthorized people. After your classified security is in force, it is recommended that you do not disable it.
Custom classifications can also be defined. For details, see Creating Custom Security Classification.
The following descriptions are applicable for those companies that are using the Oracle WebCenter Content: Records product for DoD compliance.
When using security classification for corporate use only (that is, if you are not concerned with DoD compliance), these terms can be defined as necessary for the organization's infrastructure. For example, Top Secret may apply to content that is critical to the operation of your company and should never be deleted, while Confidential may apply to content that must be kept limited to a specific group of individuals, such as Human Resource representatives or members of your accounting team.
13.5.1.1 Top Secret
If complying with DoD Section 1508, the Top Secret classification (according to Executive Order 12958) is "applied to information, the unauthorized disclosure of which could be expected to cause exceptionally grave damage to the national security that the original classification authority is able to identify or describe."
If complying with DoD Section 1508, only the President of the United States has the authority to classify content as Top Secret, pursuant to the Executive Order 12958. For further details, access the following link:
13.5.1.2 Secret
According to EO 12958, the Secret classification level is "applied to information, the unauthorized disclosure of which could be expected to cause serious damage to the national security that the original classification authority is able to identify or describe."
13.5.1.3 Confidential
According to EO 12958, the Secret classification level is "applied to information, the unauthorized disclosure of which could be expected to cause damage to the national security that the original classification authority is able to identify or describe."
13.5.1.4 Classification Levels
The standard security categories (classification scheme), from highest to lowest, are as follows:
-
Top Secret
-
Secret
-
Confidential
-
No markings (unclassified)
13.5.1.5 Classified Records Security Hierarchy
Every retention user has access to unclassified content, provided all other security criteria are met (such as supplemental markings, right, roles, and so on).
A user who has access to Top Secret classification has access to all lower classifications as well, as shown for User A in Figure 13-3. User B has access to Confidential content and unclassified content.
13.5.2 Managing Security Classifications
When using classified security, you must first set the classifications to be used. Then set the time frame for classifying and declassifying, then lastly assign classification ability to different users. The following tasks are discussed in regard to managing classifications:
13.5.2.1 Enabling or Disabling Classified Security
You can enable and disable classified security at any time. Enabling classified security enforces the security classifications assigned to users who attempt to access classified data. It is not recommended that classified security be disabled after it has been in use.
After enabling classified security, create any custom security classifications required by the organization. If additional security classifications are created, make sure to indicate the classification's place within the marking hierarchy. For further information, see Setting the Order of Security Classifications.
Note:
The Admin.RecordManager right is required to perform this action. This right is assigned by default to the Records Administrator role.
-
Choose Records then Configure then Settings.
-
Expand the Security section on the Configure Retention Settings page. Select Classified Security.
-
Click Submit.
A message appears stating the configuration was updated successfully.
Caution:
Disabling classified security puts sensitive classified items at risk of being accessed by unauthorized people. After your classified security is in force, it is recommended that you do not disable it.
To disable classified security:
13.5.2.2 Creating Custom Security Classification
Use this procedure to create a new security classification. After creating a custom classification, indicate its order in the hierarchy. If not done, the security classification is ignored. For further information, see Setting the Order of Security Classifications.
Security classifications can be created only if the classified security feature has been enabled.
When editing an existing security classification, the description can be modified but not its name.
Note:
The Admin.RecordManager and Admin.SecurityClassifications rights are required to perform these actions. These rights are assigned by default to the Records Administrator role.
13.5.2.3 Editing a security classification
To edit an existing security classification:
-
Choose Records then Configure.
-
Choose Security then Security Classification.
-
On the Configure Security Classification page, click the Edit icon (a pencil) next to the classification to edit.
-
On the Create or Edit Security Classification page, make any changes to the description and click Submit Update.
A message appears stating the security classification was updated successfully.
-
Click OK.
13.5.2.4 Setting the Order of Security Classifications
Prerequisites
-
Create any custom security classifications that are required. Assign yourself the highest classification level so you can view and reorder all levels.
Note:
The Admin.RecordManager and Admin.SecurityClassifications rights are required to perform this action. These rights are assigned by default to the Records Administrator role. You must also have the specific security classification level assigned to you to view or work with it.
Use this procedure to indicate the order of the security classifications within the security classification hierarchy. If only the built-in security classifications are used in their default order, this procedure is not needed.
13.5.2.5 Deleting a Security Classification
A classification cannot be deleted until any references to the classification in content are removed. Security classification assignments must also be manually removed from users. If you attempt to delete a security classification still in use, a message is displayed stating the classification is in use by users (it is assigned to users and must be removed) or by content.
Search for security classifications from the Search page. Use the search results to see which items have the classification in use. Screening can also be used to quickly isolate content.
Note:
The Admin.RecordManager and Admin.SecurityClassifications rights are required to perform this action. These rights are assigned by default to the Records Administrator role. You must also be assigned the highest security level to view all of the available classifications for deleting.
13.5.2.6 Setting the Declassification Time Frame
Classified items are automatically declassified after 25 years unless they were exempted from declassification. When an item is declassified, the Declassify On Date field is compared to the Publication Date, and if the retention period for classification status exceeds ten years, an alert is presented to the user.
Note:
The Admin.PrivilegedEnvironment right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.
13.5.2.7 Viewing Security Classification References
Use this procedure to view references to a security classification (those disposition rules that use the security classification in their definitions).
Note:
The Admin.RecordManager and Admin.SecurityClassifications rights are required to perform this action. These rights are assigned by default to the Records Administrator role. You must also be assigned the highest security level to view all of the available classifications for viewing.
13.5.2.8 Assigning a Classification to a User
You can assign security classifications only if the classified security feature has been enabled.
Note:
Administrator privileges in Oracle WebCenter Content are required to assign user access to classifications. Your own assigned classification level must also be at least the level being assigned to users. For example, if you are assigned the classification level Secret, you cannot assign the classification level Top Secret to users.
- Choose Admin Applets from the Administration menu.
- Click the User Admin icon from the Administration Applets list.
- On the Users tab of the User Admin utility, select the user in the Users list, and click Edit.
- On the Edit User page, make sure the Info tab is active.
- In the Security Classification field, select the maximum security level the user should have access to from the option list available on the menu.
- Click OK. Repeat the process for each user.
Note the following considerations:
-
If a user is not assigned any security classification, the user cannot pick an initial classification while checking in a content item. Because specifying the initial classification is mandatory, the user cannot check the item into the repository.
-
It is recommended that the highest security classification be assigned to the Records Administrator and overall administrator. This allows them to perform all classification-related tasks (for example, on behalf of someone who must downgrade or declassify an item but does not have the required classification privileges).
13.5.2.9 Changing a User's Classification
The assigned security classification of users determines what items they can access.
Note:
Administrator privileges in Oracle WebCenter Content are required to perform this action. Your own assigned classification level must also be at least the level being accessed.
- Choose Admin Applets from the Administration menu.
- Click the User Admin icon from the Admin Applets list.
- On the Users tab, select the user in the Users list, and click Edit.
- On the Edit User page, make sure the Info tab is active.
- In the Security Classification field, select the new maximum security level the user should have access to. Click the options list arrow, and click the classification needed.
- Click OK.
13.5.2.10 Removing a User's Classification
You may want to remove access from a user who is no longer authorized for a classification or to delete a classification no longer in use. Remove any references to a classification before deletion it.
Note:
Administrator privileges in Oracle WebCenter Content are required to perform this action. Your own assigned classification level must also be at least the level being accessed.
- Choose Admin Applets from the Administration menu.
- Click the User Admin icon in the Admin Applets list.
- On the Users tab, select the user in the Users list, and click Edit.
- On the Edit User page, make sure the Info tab is active.
- In the Security Classification field, delete the current security level (using the keyboard or by selecting the blank line from list).
- Click OK.
13.5.3 Classification Guides
Classification guides (and their associated topics) enable convenient implementation of multiple classification schemes. They are used to define default values for classification-related metadata fields on the content check-in page such as:
-
Initial Classification: (xInitialClassification)
-
Reason(s) for classification: (xClassificationReason)
-
Declassify exemption category: (xDeclassifyExemptionCategory)
-
Declassify on event: (xDeclassifyOnEventDescription)
-
Declassify on date: (xDeclassifyOnDate)
Using classification guides makes checking in classified content easier and more consistent, with similar content having the same classification metadata. Classification guides can be further refined by adding topics within a guide.
Note:
Classification guides can be set up only if the ClassifiedEnhancements component is enabled.
13.5.4 Managing Classification Guides
The following tasks are performed when managing classification guides:
13.5.4.1 Creating or Editing a Classification Guide
Note:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.
To create a classification guide:
-
Choose Records then Configure.
-
Choose Security then Classification Guide.
-
On the Configure Classification Guide page, click Add.
-
On the Create or Edit Classification Guide page, provide a guide ID and a guide name (description), and click Create.
An information page opens showing the identifier and name of the newly created classification guide. The page also includes an Actions menu, where current classification guides can be edited or deleted or add topics added to it.
-
Click OK to return to the Configure Classification Guide page.
To edit a classification guide:
13.5.4.2 Deleting a Classification Guide
Note:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.
13.5.4.3 Viewing Classification Guide Information
Note:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.
13.5.4.4 Creating Classification Topic
Note:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.
To create a classification topic:
- Choose Records then Configure.
- Choose Security then Classification Guide.
- On the Configure Classification Guide page, select the classification guide to create the topic for and click Info.
- On the Configure Classification Guide page, choose Edit then Configure Topics from the page menu.
- On the Administer Classification Topic page, click Add.
- On the Create or Edit Classification Topic page, provide a name and description for the classification topic, and click Create when done.
- On the Configure Topic Settings page, provide default values for each of the metadata fields, and click Submit Update when done.
13.5.4.5 Editing a Classification Topic
To edit a classification topic:
-
Choose Records then Configure.
-
Choose Security then Classification Guide.
-
On the Configure Classification Guide page, select the classification guide to edit and click Info.
-
From the Actions menu on the Classification Guide Information page, choose Configure Topics.
-
On the Administer Classification Topic page, select the classification topic to edit from the Topic Name list and click Info.
-
Choose Edit from the Actions menu on the Classification Topic Information page.
-
Edit the description for the classification topic, and click Submit Update when done.
-
Click OK at the confirmation page to return to the Administer Classification Topic page.
13.5.4.6 Editing Classification Topic Settings
Note:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.
- Choose Records then Configure.
- Choose Security then Classification Guide.
- On the Configure Classification Guide page, select the classification guide to edit and click Info.
- Choose Configure Topics from the Actions menu on the Information page.
- On the Administer Classification Topic page, from the Topic Name list, select the classification topic whose settings to edit, and click Info.
- Choose Edit then Edit Topic Settings from the page menu of the Classification Topic Information page.
- Modify the default metadata field values as required, and click Submit Update when done.
13.5.4.7 Deleting a Classification Topic
Note:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.
13.5.4.8 Viewing Classification Topic Information
Note:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.
- Choose Records then Configure.
- Choose Security then Classification Guide.
- Select the classification guide whose topic information is to be viewed on the Configure Classification Guide page and click Info.
- From the page menu on the Classification Guide Information page choose Edit then choose Configure Topics.
- From the Topic Name list on the Administer Classification Topic page, select the classification topic to view, and click Info.
- Click OK to return to the Administer Classification Topic page.
13.5.5 Supplemental Markings
Supplemental markings can be assigned to content and record folders to clarify document handling in addition to standard document classification. For example, you can add supplemental markings such as Restricted Data or Originator Controlled. Or you can use supplemental markings in collaboration projects. Only people with specific markings will be able to access a group of content. Supplemental markings can be set at both the record folder and the content level.
When supplemental markings are assigned to users, even if a user has access to a specific record folder, the supplemental marking further restricts access to record folders and content. In circumstances where a record folder or item has multiple supplemental markings, it can be required that a user match all assigned supplemental markings to access the item. When Match All is disabled, if a user matches just one of the multiple supplemental markings, the user can access the object.
To disable use of supplemental markings as a security feature, deselect the Supplemental Markings check box on the Configure Retention Settings page and do not assign the markings to users.
Two special supplemental markings, Restricted and Formerly Restricted, can be used to disable the following classification-related metadata fields on the content check-in and metadata update pages:
-
Declassify on event
-
Declassify on date
-
Downgrade instructions
-
Downgrade on event
-
Downgrade on date
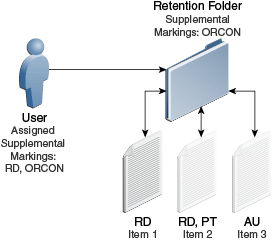
Figure 13-4 User Must Match All Supplemental Markings
Description of "Figure 13-4 User Must Match All Supplemental Markings"
For example, in Figure 13-4, the user is assigned the supplemental markings RD and ORCON. The folder is marked with ORCON, therefore the user can access the folder.
The content within the folders are assigned one or more of the markings, RD, PT, and AU. If the security configuration for supplemental markings is set to force the user to match all supplemental markings, then the user can access the folder marked ORCON and its child Item 1 marked with the supplemental marking RD. Because the user has not been assigned the supplemental marking PT or AU, the user cannot access Item 2, which has the multiple markings RD and PT, nor can the user access Item 3 with the marking AU.
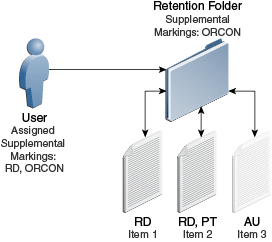
Figure 13-5 User Must Match At Least One Supplemental Marking
Description of "Figure 13-5 User Must Match At Least One Supplemental Marking"
If the supplemental marking security configuration is not forcing a user to match all markings, then the user can now access Item 2, because the user matches at least one marking RD on the Item 2. Because the user has not been assigned the supplemental marking AU, the user still cannot access Item 3, which has the supplemental marking AU. The user would have to be assigned the supplemental marking AU in the User Admin application to access the item.
Supplemental markings are not inherited by record folders or content. Markings are checked at every folder and item level. Supplemental markings do not have any permissions hierarchy. All markings have equal permissions, either access granted or access denied to users. In contrast, the classified security does have a hierarchy to its classification levels. For further information, see Classified Records Security Hierarchy.
Two special supplemental markings, Restricted and Formerly Restricted, can be used to disable the following classification-related metadata fields on the content check-in and metadata update pages:
-
Declassify on event
-
Declassify on date
-
Downgrade instructions
-
Downgrade on event
-
Downgrade on date
To work with supplemental markings, you must have one of the following rights:
-
Admin.Triggers: This right enables you to view information about supplemental markings.
-
Admin.RecordManager: In addition to viewing information about supplemental markings, this right also enables you to create (add), edit, and delete supplemental markings.
Optionally, the following right may be useful for working with supplemental markings:
-
Record.Edit: This right is required to use metadata disabling based on supplemental markings.
Note:
Oracle WebCenter Content administrative permissions are required to perform this action.
13.5.6 Managing Supplemental Markings
The following procedures are followed when managing supplemental markings:
13.5.6.1 Enabling or Disabling Supplemental Markings
You can enable and disable supplemental markings at any time. Enabling supplemental markings enforces the markings assigned to any users attempting to access marked items and record folders.
Disabling supplemental markings means the security provided by the markings is not in force; however, the supplemental markings can still be used generically as document handling instructions.
Note:
The Admin.RecordManager right is required to perform these actions. This right is assigned by default to the Records Administrator role.
To enable supplemental markings:
13.5.6.2 Disabling Supplemental Markings
To disable supplemental markings:
-
Choose Records then Configure then Settings.
-
In the Security section on the Configure Retention Settings page, deselect Supplemental Markings and User must match all supplemental markings.
-
Click Submit.
A confirmation message appears. Supplemental markings are now disabled and the Supplemental Marking selection field is hidden from view.
13.5.6.3 Creating Supplemental Marking
You can create supplemental markings only if they are enabled. After creating a supplemental marking, it is available to apply to content, record folders, and users.
When editing an existing supplemental marking, its description can be modified but not its name.
Note:
The Admin.RecordManager right is required to perform these actions. This right is assigned by default to the Records Administrator role.
To create a supplement marking:
13.5.6.4 Editing a Supplemental Marking
To edit an existing supplemental marking:
-
Choose Records then Configure.
-
Choose Security then Supplemental Markings.
-
On the Configure Supplemental Markings page, you can edit the marking in one of two ways:
-
Choose Edit Marking from the item's Actions menu.
-
Choose the name of the marking to edit. The Supplemental Marking Information page opens. Choose Edit from the page menu.
-
-
On the Create or Edit Supplemental Marking page, make the changes and click Submit Update.
The Supplemental Marking Information page opens with a message indicating the creation was successful. Use this page to edit or delete the marking, or view references to the marking.
-
Click OK when done.
13.5.6.5 Viewing Supplemental Marking Information and References
Note:
Either the Admin.Triggers or Admin.RecordManager right is required to perform these actions. The Admin.Triggers right is assigned by default to the Records Officer and Records Administrator roles, and the Admin.RecordManager right to the Records Administrator role.
- Choose Records then Configure.
- Choose Security then Supplemental Markings.
- On the Configure Supplemental Markings page, click the name of the marking with information to view.
- The Supplemental Marking Information page opens. Use the page to edit or delete the marking, or view references to the marking by choosing the appropriate option on the page menu.
- Click OK when done.
13.5.6.6 Deleting a Supplemental Marking
You can delete supplemental markings regardless of whether markings are enabled. A supplemental marking cannot be deleted until all references to the marking in content or record folders is removed. The marking must also be manually removed from any assignments to users.
If a user attempts to delete a supplemental marking currently in use, a message is displayed stating the marking is in use by users (the marking is assigned to users and must be removed), by record folders, or by a content item. The marking must then be removed from the user, folder, or item before proceeding.
To remove the marking from any option lists, the schema must be republished after deleting the marking.
Note:
The Admin.RecordManager right is required to perform this action. This right is assigned by default to the Records Administrator role.
13.5.6.7 Assigning User Supplemental Markings
Note:
Administrator privileges in Oracle WebCenter Content are required to perform this action.
Before assigning markings to users, make sure you have enabled supplemental markings, created the markings, assigned supplemental markings to record folders and retained content, and assigned roles to the users. For the most strict supplemental marking security, you can also force a user to pass all supplemental markings to access an item or record folder.
You may want to remove access from a user who is no longer authorized for a supplemental marking, or to delete a supplemental marking no longer in use. You must remove any references to a supplemental marking before you can delete it.
To disable use of supplemental markings as a security feature, do not assign the markings to users.
To assign a supplemental marking to a user:
13.5.6.8 Removing Supplemental User Markings
To remove a supplemental marking from a user:
-
Choose Admin Applets from the Administration menu.
-
Click the User Admin icon in the list of Admin Applets.
-
On the Users tab, select the user in the Users list, and click Edit.
The Info tab on the Edit User page opens.
-
In the Supplemental Markings field, delete a marking by editing the text in the Supplemental Markings field.
Caution:
Be careful when editing text in this field. Each supplemental marking must have a comma and a space between markings, or an access denied error occurs when trying to access content with multiple markings and Match All Markings is enabled.
-
Click OK. Repeat for each user who has a marking to be removed.
-
Restart Content Server. For more information about restarting, see Administering Oracle WebCenter Content.
13.5.6.9 Using Restricted and Formerly Restricted Supplemental Markings
Restricted Data and Formerly Restricted Data are supplemental markings shipped with the product. Those markings can be used alone or in combination with other markings to disable classified metadata fields on the content check-in and metadata update forms:
- Enable supplemental markings.
- Click Restricted Data or Formerly Restricted Data as the supplemental marking.
- Restart Content Server.
13.6 Custom Security
Custom security is optional and are another layer of security in addition to supplemental markings.
Two types of custom security are available:
-
Simple custom security fields, where custom field are configured to be matched by a user rather than a designated supplemental marking. This is called custom supplemental markings in the DoD 5015 standard,
-
Advanced custom security, where security is applied to fields that use option lists. Security can be applied to individual items in the option list.
Unlike supplemental markings, custom security is enforced at the item level. Supplemental markings are enforced at both the record folder and the item level.
To work with custom security, you need to have one of the following rights:
-
Admin.Triggers: This right enables you to view information.
-
Admin.RecordManager: In addition to viewing information, this right also enables you to create (add), edit, and delete custom security.
A simple custom security field pairs a custom content field with a custom user field. For example, you can create a custom security field such as Project Name. Users must be assigned the appropriate project name or names to access or view an item assigned with custom security. If the Match All setting is enabled, a user must be assigned to all the same projects as an item is assigned to for the user to access an item with multiple project assignments. If a user does not match all project names, the user cannot access an item.
You can opt to select the match all feature for custom security fields just as you can with supplemental markings. Content is then checked in with one or more custom security field options, such as a particular project name, assigned to the content.
For instance, User1 is assigned project name Pangea only. The user named User2 is assigned both project name Pangea and Tectonic. If content is checked in with multiple field options assigned (for example, Pangea and Tectonic), then only a user with all project names assigned (User2) can access that content. If the Match All setting is disabled, then a user only must match one field option to access an item.
Advanced custom security also limits access to content items. Advanced security can also restrict access based on aliases as well as individual users. This type of security assigns security at the item level for option lists. When using this type of security, the only metadata that can be used is that which has an option list associated with it. Access can then be restricted to individual items in the option list by limiting which accounts, which users, or which aliases of users can access specific options.
This section covers the following topics:
13.6.1 Managing Custom Security
The following tasks are often performed when managing custom security:
13.6.1.1 Enabling or Disabling Custom Security Usage
Use this procedure to enable the custom security feature. It can be enabled or disabled at any time.
Note:
The Admin.RecordManager right is required to enable custom security. This right is assigned by default to the Records Administrator role.
To disable the feature, deselect Custom Security.
13.6.1.2 Creating a Simple Custom Security Field
Use this procedure to create a new simple custom security field.
Note:
Make sure you have defined the custom field for the items in the Configuration Manager utility, and the custom field for the users in the User Admin utility before performing this task.
You can create custom security fields only if the custom security field feature has been enabled.
Note:
The Admin.RecordManager right is required to perform this action. This right is assigned by default to the predefined Records Administrator role.
To create a custom security field:
13.6.1.3 Editing a Custom Security Field
To edit an existing custom security field:
-
Choose Records then Configure.
-
Choose Security then Custom Security.
-
Choose Edit Field from a field's Actions menu on the Configure Custom Security page.
-
Make the necessary edits:
-
Select the name of the metadata field from the Content Field list.
-
Select the name of the user metadata field in the User Field list.
-
Select (if needed) Match all.
-
-
Click Submit Update.
A message states the update was successful.
-
Click OK.
13.6.1.4 Adding Advanced Security
Use this procedure to add advanced security to an existing field. The field used must be one that has an option list associated with it. The option list must be created before this feature can be used.
You can add custom security only if the custom security feature is enabled.
Note:
The Admin.RecordManager right is required to perform this action. This right is assigned by default to the predefined Records Administrator role.
To add advanced security to an existing custom security field:
- Choose Records then Configure.
- Choose Security then Custom Security.
- If needed, click the Advanced Custom Security tab on the Configure Custom Security page to open that page. Click Add.
- In the Select Security dialog, select a field from the list. Note that only fields with option lists are available for selection.
- Click OK.
- On the Advanced Custom Security Option page, choose the Actions menu for the option item that needs security. Click Edit Security.
- In the Select Security dialog, select users or aliases who will have access to content items with that individual option list value.
- If needed, select a security group from the list.
- The Advanced Custom Security Option page opens, showing the selections just made.
13.6.1.5 Editing Advanced Security
To alter custom security for a field (including removing the security):
-
Choose Records then Configure.
-
Choose Security then Custom Security.
-
In the Advanced Custom Security area of the Configure Custom Security page, choose Edit Security from the Actions menu of the option item. To remove security for the option item, choose Remove Security from the Actions menu of the option item.
When editing, a dialog opens so you can select a field for use. Only fields with option lists are available for selection.
-
Click OK.
-
On the Advanced Custom Security Option page, choose Edit Security from the Actions menu for the option item that needs security.
-
In the Select Security dialog, select users or aliases who will have access to content items with that individual option list value.
-
If needed, select a security group from the list.
-
The Advanced Custom Security Option page opens, showing the selections just made. The security is now in place.
13.6.1.6 Viewing Simple Custom Security Field Information
Note:
Either the Admin.Triggers or Admin.RecordManager right is required to perform this action. The Admin.Triggers right is assigned by default to the Records Officer and Records Administrator roles, and the Admin.RecordManager right to the Records Administrator role.
13.6.1.7 Deleting a Simple Custom Security Field (Simple)
You can delete a custom security field without having to remove references to it by users and content, unlike supplemental markings and security classifications.
Note:
The Admin.RecordManager right is required to delete a custom security field. This right is assigned by default to the Records Administrator role.
- Choose Records then Configure.
- Choose Security then Custom Security.
- On the Configure Custom Security page, choose Delete from the item's Actions menu. To delete multiple fields, select the check box next to the field name and choose Delete in the Table menu. A field can also be deleted when viewing the field's Information page.
- A message appears, stating the deletion was successful.
- Click OK.
13.6.2 Simple Custom Security Field Example
This example gives step-by-step instructions for setting up a custom security field called Project Name. It includes the following processes:
- Create the Custom Security Field in Configuration Manager.
- Create the Custom Security Field in User Admin. Oracle WebCenter Content assigns the
uprefix. Assign the field options to the user. - Rebuild the search index, and restart Content Server.
- Create the Custom Security Field using the exact field names defined in the Oracle WebCenter Content utilities.
After the custom security field is set up, test the field by checking in and accessing items assigned field options. See Verify the Custom Security Field.
13.6.2.1 Create the Custom Security Field in Configuration Manager
This portion of the example creates the custom security field as a document field within the Configuration Manager utility. The field will be available for use on the check-in form.
-
Choose Admin Applets from the Administration menu.
-
Click the Configuration Manager icon in the Admin Applets list.
-
Click the Information Fields tab in the Configuration Manager utility.
-
Click Add.
-
On the Add Custom Info Field page, type
ProjectName, and click OK. On the Add Custom Info Field page, specify the field attributes:-
For Field Caption, enter a space between any compound words (in the above example, Project and Name) so the field label displays properly.
-
In the Field Type list, select Long Text.
-
Select Enable Options List. Click the enabled Configure button.
The Configure Option List page opens.
-
In the Options List Type, select the Edit and Multiselect List option.
-
Click Edit next to Use Option List.
The Option List page opens.
-
In the options list, type
Pangea. Press Enter for a carriage return, then typeTectonic. -
Click OK three times.
-
-
Click Update Database Design.
13.6.2.2 Create the Custom Security Field in User Admin
This portion of the example creates the custom security field as an information field called Project Name within the User Admin utility.
-
Choose Admin Applets from the Administration menu.
-
Click the User Admin icon in the Admin Applets list.
-
On the User Admin utility, open the Information Fields tab.
-
Click Add.
-
On the Add Custom Info Field page, type
ProjectNameand click OK. Specify the field attributes on the Add Metadata Field page:-
For Field Caption, enter a space between any compound words (as in the example, Project and Name) so the field label displays properly.
-
In the Field Type list, select Long Text.
-
Select Enable Options List. This enables the Options List Settings tab.
-
In the Options List Type, click the Edit and Multiselect List option.
-
Choose Edit.
-
In the options list, type
Pangea. Press Enter for a carriage return, and then typeTectonic. -
Click OK twice.
-
-
Click Update Database Design.
-
Click the Users tab. Create a user named
User1then select that name and click Edit. The Edit User page for the user opens.-
In the Project Name list, click the down arrow, and select the project name Pangea from the list. Repeat for Tectonic. You now have a comma-separated list of project names assigned to User1.
-
Click OK.
-
-
Restart Content Server.
13.6.2.3 Create the Custom Security Field
This portion of the example creates the custom security field. Make sure the Custom Security Field option is enabled in the Configure Retention Settings page, and you have defined the document and user fields in the appropriate administration utilities.
- Click Configure then Custom Security Fields from the Configure Retention Settings page.
- On the Configure Custom Security page, click Add.
- In the Custom Security Field on the Create or Edit Simple Custom Security Field page, type
Project Name. - From the Content Field list, select ProjectName.
- From the User Field list, select ProjectName.
- Select Match all to force a user to match all content field entries. This is the strictest setting. If a user is not assigned all project names assigned to an item, the user cannot access that item.
- Click Create.
13.6.2.4 Verify the Custom Security Field
This portion of the example demonstrates how the custom security field restricts access.
-
Log in as User1 and check in an item with both Pangea and Tectonic selected as project names in the check-in form. Search for the item you just checked in as User1. The search should be successful.
-
Now log in as a new user without any custom field assignments. Attempt to access the item user1 just checked in. The attempt to view the item should not be successful because the new user does not have any assigned field options.
-
Log in as an administrator and assign the new user the field option Pangea. Disable the Match all option for the custom security field. Log in as the new user and attempt to access the item with Pangea and Tectonic assigned as the project name. The access should now be successful because only one field list option has to match, and the user is assigned the appropriate field list option.