Release 2 (9.0.2)
Part Number A90146-01
Home |
Solution Area |
Contents |
Index |
| Oracle9i Application Server Security Guide Release 2 (9.0.2) Part Number A90146-01 |
|
This chapter presents an overview of security requirements in a Web environment. For security professionals, the issues and solutions will be familiar. For readers whose experience is less extensive, this chapter can provide a framework for understanding the problems that must be confronted and the methods currently in use.
This chapter contains the following topics:
This section provides an overview of Internet security issues.
Security for computer systems means protection for data, processes, and transmissions against unauthorized, accidental, malicious, or otherwise inappropriate access, use, corruption, or misrepresentation. This chapter refers to all such undesired effects as "inappropriate."
In today's Internet-connected world, security concerns have multiplied beyond every simple solution because the number and complexity of such inappropriate possibilities have multiplied with every new Internet user and business connection.
While databases, applications, operating systems, and communication methods have grown ever more complicated and interwoven, so too has the number and sophistication of attackers. Some are teenagers; some are competitors; some are foreign governments; and some are criminals. Whatever the source of the inappropriate action, the ideal scene is for it to fail. The design goals of security systems and methods are that, to the greatest extent possible with the resources available, the following objectives be achieved:
These objectives represent layers of defense against inappropriate access and use. The intention is to make each layer as impenetrable and incorruptible as possible, within constraints of time, money, staff, and "user convenience." But this layered defense also requires each layer to contain defenses against inappropriate actions by users who, though validated for entry to this level, might accidentally or intentionally act inappropriately.
This chapter presents today's concepts and methods that address the vulnerabilities inherent in e-business and Internet interactions, using the terminology defined in Tables 1-1, 1-2, and 1-3. Reading these definitions will help you understand the approaches taken by security experts and will clarify the connections among the security measures discussed in this book.
|
Protection Terms |
Meaning |
|---|---|
|
Authentication |
The process or result of validating an entity's identity, typically based on what the entity is, what it knows, or what it has. For example, someone might be authenticated by proving she is a voter, or by knowing her social security number, or by having a driver's license. |
|
Authorization |
The process or result of establishing what objects and actions an entity can access or perform, such as view, add, change, delete, etc. One authenticated person might be authorized to view but not change his profile in the company records; another might be authorized to change a title but not a salary; and so forth. |
|
Accountability |
A verifiable, undeniable association between actions and the person or entity who performed those actions. |
|
Certificates |
Digital identity records, issued by trusted third parties, that identify users and machines. |
|
Electronic Signature |
Also known as digital signature. An encrypted compression of a message that can provide reliable proof that the person signing the electronic transmission really is that person, since no one else can create the unique digital signature supplied. |
|
Decryption |
Transforming plain text into a less readable or understandable form. Using a mathematical process to do so. If a specific word, phrase, or number is central to the encryption, it is called the key. Transforming the less readable form back into the original plain text. Decrypting means undoing the encrypting. If a key was used, decrypting requires knowing and using the key. |
|
Integrity |
The original form, relationships, and rules of the data. If these are changed without permission or notice, integrity is said to be lost or corrupted. |
|
Permissions |
Attributes of an entity that allow it to view data or take actions that would otherwise be restricted or prohibited. |
|
PKI, |
Public Key Infrastructure: a system of digital certificates issued by Certificate Authorities (CA) that verify and authenticate that the parties to an Internet transaction are who they say they are. Each party has a public key available to anyone, and a private key known only to itself. These are used for encryption and decryption of messages or transactions. A PKI is also called a trust hierarchy, since a CA with a certificate from a known-good CA can also issue certificates. See Certificates and Certificate Authorities. |
|
Privileges |
Permissions. See above. |
|
Non-repudiation |
Making it impossible to deny that a message or transaction you sent was sent by you. |
As noted in the Introduction, the exponential growth of business and personal connections over the Internet has put valuable and sensitive data at greater risk than ever before. Figure 1-1 illustrates the complex computing environment that your system security plan must encompass.
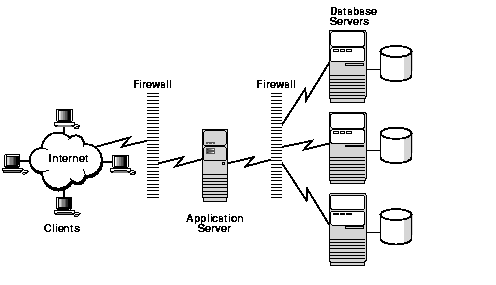
You must protect databases and the servers on which they reside; you must administer and protect the rights of internal database users; and you must guarantee the confidentiality of e-business customers and their data as they access your database.
The Internet enables businesses to use information more effectively by allowing customers, suppliers, employees, and partners to get access to the business information they need, when they need it. The greatest promise of e-business is more timely information accessible to more people, at reduced cost of information access.
These benefits are challenged by the security vulnerabilities associated with replacing trusted and accountable human processes with easy access over the Internet. "Cutting out the middleman" too often cuts out the information security that the middleman provides. Many brick-and-mortar business processes typically performed by employees, such as typing in an order received by telephone, mail, or fax, are now done directly by outsiders using an Internet connection. While employees are not invariably reliable, at least they are known, and their access to sensitive data is limited by their job function. Physical and procedural controls can be more readily enforced, and there is disciplinary or legal recourse against employees who pass sensitive information outside the company contrary to policy. The threat of punishment thus helps prevent unauthorized access.
But in the Internet-enabled world, users now include persons outside the traditional corporate boundary, such as prospects, customers, suppliers, partners, and ex-employees. The potential user community expands from a small group of known, vetted users accessing data on an intranet to thousands of users accessing data over the Internet.
All these users can have direct and immediate online access to business information. Only some of it pertains to each legitimate user; the rest needs protection even during legitimate access. And all of it needs protection from illegitimate access.
In addition, the data available for access has changed. Online data has grown more diverse, more timely, more integrated, and more valuable. It is more tempting than ever before. The reasons arise from the efficiencies offered by Internet-enabled business practices. A great variety of costs can be reduced or eliminated while reaching ever more prospects and serving ever more customers. Inventories can be reduced by streamlined operations that give suppliers direct access to consolidated order information and allow just-in-time purchasing. Online competitive bidding can help companies pay lower costs and offer consumers lower prices. Costly errors and delays from manual data handling can be reduced or eliminated by enabling other businesses and consumers to submit and receive business information directly through the Internet.
These Internet processes can often replace even electronic data interchange mechanisms, which are typically proprietary and difficult to integrate with multiple companies' internal data infrastructures.
Linking or consolidating formerly compartmentalized departmental databases allows users to obtain better information, and to get more benefit from it. The integration of formerly physically separate and incompatible databases and applications -- often called silos or islands of information -- enables faster and better use of sales, manufacturing, distribution, and financial information.
But the better you make the timeliness, accuracy, and scope of data available to legitimate users, the greater its value to intruders as well. As the rewards rise for unauthorized access, the potential also rises for damage to the image and effectiveness of the corporation whose confidentiality can be breached and whose data can be corrupted or misused.
Protecting against such misuse is made more complex by the diversity and sheer size of the user communities that can access business systems over the Internet. Business and security systems designed to cope with this level of risk and complexity need to be
These requirements demand designs based on widely-accepted standards such as Java, C, and XML. Only then can security mechanisms deployed in e-business systems have the flexibility and interoperability to work easily with multiple systems, thin clients, and multitier architectures.
Secure hosting and data exchange can enable economical, secure partitioning of data access by customer or by user, while supporting secure data sharing among communities of interest. Oracle9i Application Server makes this possible through support for a public key infrastructure and enterprise user security.
The principal security challenge of hosting is keeping data from different hosted user communities separate. Providing separate systems for each hosted community has the disadvantage of requiring separate installation, configuration, and management for each hosted user community. This solution provides little in the way of economies of scale to a hosting company.
Using Oracle9iAS provides several factors that can greatly reduce costs to hosting service providers. These factors include mechanisms that allow multiple user communities to share a single hardware and software instance, that securely separate data for different user communities, and that provide a single administrative interface to service all the hosted communities.
Similar considerations support the requirements that exchanges have for both data separation and data sharing. For example, an exchange may ensure that a supplier's bid remains unviewable by other suppliers, yet allow all bids to be evaluated by the entity requesting the bid. Furthermore, exchanges may also support "communities of interest" in which groups of organizations can share data selectively, or work together to provide such things as joint bids.
No system can be 100 percent secure and still allow user access: there is a trade-off between security and ease of access. A similar trade-off must also be expected in terms of cost and performance.
As you apply security mechanisms to protect data, the cost to break those defenses increases. No single solution can provide total security for a system. If you identify eight different ways to break the security of a system, you can begin to improve security by making a particular way more expensive to break. You can then move on to making the next way more expensive, such as incorporating 128-bit cryptography, which is extremely difficult for hackers to break. Faced with this and other obstacles, malefactors might try to bribe the CEO, rather than try to break in and decrypt the data. Here is a rule of thumb: when the cost to break security is greater than the value of the data protected, then you can quit making the system more secure.
Furthermore, trying to protect all the data with every possible defense might degrade performance. For this reason, you must decide just what data needs to be protected. You may want to apply security protection to certain classes of data, and not to others. Regional sales data, for example, may require protection, while promotional photographs may not.
This section outlines the security needs of systems within a Web environment using the following headings:
Confidentiality refers to not revealing or exposing critical or sensitive information. Data must be stored and transmitted securely, so that information such as credit card numbers cannot be stolen.
Over the Internet and in Wide Area Network (WAN) environments, both public carriers and private network owners often route portions of their network through insecure land lines, extremely vulnerable microwave and satellite links, or a number of servers. This situation leaves valuable data open to view by any interested party. However, communications known to be sensitive, such as credit card numbers, are routinely encrypted, so that even if observed, they cannot be read or used.
In Local Area Network (LAN) environments within a building or campus, insiders with access to the physical wiring can potentially view data not intended for them. Network sniffers can easily be installed to eavesdrop on network traffic. Packet sniffers can be designed to find and steal user names and passwords. Frequent password changes can lessen the risk of misuse, since the stolen data would only be usable until the next change.
Authentication ensures that users are who they claim to be. Some authentication methods require the user to be known in advance, by name and password, but other methods dispense with this requirement by using unforgeable certificates. Authentication can be applied in several ways at various points of vulnerability to guard against unauthorized access and actions.
The idea remains the same even though authentication mechanisms vary for different contexts. In database authentication, the database performs both identification and authentication of users. In external authentication, the operating system or network service performs the authentication. When database user identities are verified by SSL (Secure Sockets Layer), they are called global users, and their access to the database through global roles is authenticated by means of an enterprise directory. When users are allowed to connect through a proxy server, the verification is called multitier authentication and authorization.
Requiring passwords at several points can act as a layered defense against unauthorized access and actions in that a stolen password at one level would not unlock all lower level services. Some companies safeguarding sensitive or valuable data, such as credit card firms, require several items of identification, such as social security number, mother's maiden name, and mailing zipcode. These items are usually not used as multiple passwords but rather as a combined authentication mechanism when passwords have not yet been established. They are advantageous in being specific to the individual while remaining generally not easy to access or to guess, criteria often suggested for selecting passwords. On the other hand, passwords generally should be selectable and easy to change, advantages that these items lack.
However, there are problems inherent in requiring users to have multiple passwords. In large systems, users must remember several passwords for the different applications and services that they use. For example, a developer can have access to a development application on a workstation, a PC for sending e-mail, and several computers or intranet sites for testing, reporting bugs, and managing configurations. Security vulnerabilities arise from the typical user responses to the problem of managing multiple passwords:
All of these strategies compromise password secrecy and service availability. From the user's point of view, remembering multiple passwords is a hassle. From an administrator's viewpoint, maintaining multiple user accounts and passwords is complex, time-consuming, and expensive. Password queries from legitimate users account for a high percentage of help-desk time. And user reactions to the complexity often compromise the intended security benefits.
Authorization guards against misuse of systems, applications, or data after access has already been granted; it controls what objects and actions can be used. Authorization generally refers to the process that determines what a user can access or maintains a record thereof. The enforcement of that authorization is called access control, which can require an additional password or validate a request for resources against lists of approved users or permissible activities. For example, a directory that lists your privileges performs an authorization function, whereas database software using that information to limit which data you can see is doing access control.
As an example, the data and services provided by an Oracle database can be protected by such authorization actions. Using Oracle9i Application Server can mediate access to services provided by the back-end database. For each transaction, Oracle9i Application Server reports a user identity to the database. At that point, the database's native access controls take over, providing resource restrictions based on the identity of the requestor as established by the authentication function. The user's database privileges determine the specific data (that is, the tables, columns, and rows) that are accessible to him.
Authorization is also a defense against hackers who may try to corrupt your Web site. They also try to redirect users to a different site, fooling a client or server into believing that the site is something it is not.
To prevent corruption, you can control access to the administrative functions that govern the content of the site. To help protect against stolen Web connections, you can employ user authorization and encryption.
The intent of non-repudiation is to preserve accountability and prevent misrepresentation. Non-repudiation means that when someone actually sends a message, the sender cannot later disclaim responsibility for sending it.
To ensure against false claims, there must be a digital "signature," usable only by the true sender, that any recipient can verify. A digital signature also solves the parallel problem of someone else sending a message that falsely claims to be from a third party.
How can such a signature be created, and how is it to be protected? If hackers were to steal someone's private key (the person's digital signing capability), that person could be held responsible for any actions the hacker performed using it.
|
See Also:
"Security Considerations in an Internet Environment" where public and private keys, which are used for encryption and key distribution as well as digital signatures, are discussed. |
This section describes various types of network attack:
Distributed environments bring with them the possibility that a malicious third party can perpetrate a computer crime by tampering with data. The damage can be done to messages as they move between sites on the network or, more seriously, to the sites themselves.
In a data modification attack, an unauthorized party on the network intercepts data in transit and changes parts of that data before retransmitting it. An example of this is changing the dollar amount of a banking transaction from $100 to $10,000.
In a replay attack, an entire set of valid data is interjected again onto the network. An example would be to repeat, one thousand times or even once, an initially-valid $100 bank account transfer transaction.
This type of injury to messages is relatively rare, given the usual protections. The more dangerous attack puts in undetected changes to the site itself, either to the data in its presentation or to an underlying database. There is high potential for damage to subsequent visitors or users, and certainly to the responsible company.
Levels of authentication and authorization are your primary defenses in preventing a hacker's access and use of administrative or database functions to corrupt, falsify, or otherwise misuse site data.
Auditing mechanisms can ensure that data tampering is detected. Non-repudiation mechanisms can help to identify perpetrators.
Data in transit must not be modified or viewed, and database data must not be accessible for unauthorized copying or sharing. No unauthorized party should be able to intercept, display, or otherwise misuse confidential information while it is being transmitted over the network or available online for legitimate users.
Data and Web security also involve the accessibility of information to authorized users, as needed. While system security by itself does not ensure availability, availability may not be possible without security.
Most denial-of-service attacks prevent legitimate users from getting serviced by overwhelming a site with an extremely high volume of repetitive requests. The results can include much slower service for legitimate users or actual site shutdown due to resource overload. Security of the attacked site has little to do with such an attack.
On the other hand, many such attacks begin by exploiting security flaws in other systems, which are not targets of denial-of-service. The intent is to acquire rights and resources that can later be used to generate some of those repetitive phony requests that do build a denial-of-service attack.
In addition to protecting the site itself, appropriate security measures prevent exposing any vulnerabilities that could be exploited by a malicious intruder to mount an attack elsewhere. Individual user profiles that limit the system resources available to each user can help. Examples include limiting usable disk space, the allowable number of concurrent sessions, the permissible CPU processing time, and the amount of logical I/O available to the user.
If there is a security breach, how do you limit the damage it can cause?
Among the best ways to lessen security risk on the Internet is to provide multiple layers of security mechanisms. Each layer's independent security measures prevent a single security failure from compromising all critical information. This concept is referred to as deep data protection. Deep data protection ensures well-formed, comprehensive security from client to application server to data server, as well as throughout the layers of an application.
Oracle9i Application Server provides fault containment through access control, data encryption, and extensive auditing. Access to the database is limited by controls intended to permit only those with established identities to gain entry. Nevertheless, if an unauthorized entity does gain access, the fact that the data is encrypted makes it difficult or impossible for that illegitimate entity to view or use it. Furthermore, Oracle9i Application Server's auditing can quickly reveal this breach and provide valuable information in tracking that entity.
As an example at a different level, Oracle9i Application Server can ensure that applications do not use root privileges and that cross-site scripting is disallowed. In other words, even a person using root privilege would not be able to insert into a normal message a Java script to send the entire machine configuration to a third party.
Security mechanisms must remain effective and easy to administer even when the number of transactions and the size of the databases become huge. Yet with corporate mergers and acquisitions, or even simple unexpected Web site success, the number of users can grow from 6,000 to six million within a single month. A company's system must be able to handle these enormous numbers of simultaneous users without compromising the confidentiality and integrity of its data and transactions with each one. Dissatisfied customers or prospects may turn to competitors (or lawyers).
In such large-scale environments, the burden of managing user accounts and passwords can make a system vulnerable to error and attack. To have reliable security, you need to know who the user really is, across all tiers.
Oracle9i Application Server provides a number of security features that support development of Internet-scale applications. These features include proxy authentication, support for Internet and relevant public key infrastructure (PKI) standards, and enterprise user security features such as directory-based privilege management.
The user management problem becomes particularly complex in multitier systems. Here, as in most packaged applications, the typical security model is that of One Big Application User. The user connects to the application, and the application (or application server) logs on and provides complete access for everyone, with unlimited privileges and no auditing. This model places your data at risk -- especially on the Internet, where your Web server or application server depends on the security imposed by a firewall. Firewalls are commonly subject to continual attack from outside, and a single breach can spawn a multitude of problems.
Security mechanisms that can handle hundreds of users may not be adequate to handle enormous communities of users. Security administration must thus be scalable. The administration of hundreds of thousands of users is difficult enough on a single system. When security must be administered on multiple such systems, there must be some way to divide and conquer the complexity. Only an intelligent combination of sharing, automated self-service, and delegation can make it manageable.
Creating and maintaining separate databases for multiple application subscribers is not a cost-efficient model for an application service provider. While technically possible, the separate database model would itself quickly become unmanageable. To be successful, a single application installation should be able to host multiple companies--and be administered centrally.
If user identities and privileges can be maintained securely in a single, central repository, other systems and applications can rely on that as a secure starting point. Downstream, other systems and applications can require additional security validations appropriate to their functionality or content. But the burden is then split among collaborating entities, each with a narrower focus more closely related to its specific service.
Thus challenges of scale in administration -- particularly for security -- can be met through a combination of central management cooperating with multiple applications and databases. Applying appropriate layers of security using a directory based on industry standards can reduce system management costs and increase business efficiency.
This section presents some important system security considerations applicable to a multitier network environment.
As described in earlier sections, effective Internet security requires secure information exchange mechanisms that are scalable and that support the security of distributed systems. Public Key Infrastructure (PKI) is a technology that meets these requirements with minimal inconvenience.
Oracle9i Application Server can use elements of PKI to provide a secure, resilient environment for deploying electronic commerce. This reliable environment supports building systems to handle virtually any type of electronic interaction, from corporate intranets to e-business applications designed for deployment on the Internet.
Strong system security starts with the physical security of systems and the trustworthiness of personnel. With these in place, PKI enhances secure electronic commerce and Internet communications by supporting the following processes:
For public-key cryptography, entities that want to communicate in a secure manner must possess certain security credentials. This collection of security credentials is stored in a wallet. Security credentials consist of:
Use of a cryptographic key pair to set up a secure, encrypted channel ensures the privacy of a message and can validate the authenticity of the sender of the message. Wide distribution of the public key on a server, or in a central directory, does not jeopardize security because the private key is never shared. The public key for an entity is published by a certificate authority in a user certificate. Entities that want to send secure information can encrypt the information with the recipient entity's public key. An entity that receives a communication encrypted by this method can use its own private key to decrypt the message. (In some cases, the sender might need to reassure the recipient regarding who sent the message. Encrypting the coded message again using its own public key would do the trick. The recipient could decrypt the doubly-encoded message using his private key, and then decrypt the resulting coded message using the sender's public key. If the original message was not encoded using both public keys, the result of decrypting will be unreadable.)
Without effective authentication, authorization policies have little value. Authentication mechanisms rely on the user supplying something uniquely associated with her: something she is, something she knows, or something she has.
This section describes the following aspects of authentication services:
Passwords are one of the basic forms of authentication. A user must provide the correct password when establishing a connection to prevent unauthorized access to systems, applications, or data. Security systems that are dependent on passwords require that passwords be kept secret at all times. However, passwords are vulnerable to theft and misuse.
A number of steps can strengthen the basic password feature and provide greater control over Web site, application, or database security. For example, password management policy can be controlled by administrators and security officers through user profiles. The administrator can establish standards for password complexity, and deny reuse of passwords. Passwords can be timed out, expiring after a certain amount of time; they should not be stored, or sent over the network, in unprotected form.
Having a trusted authority available to authenticate all members of the network (clients to servers, servers to servers, users to both clients and servers) is an effective way to address the threat of nodes on a network falsifying their identities. In the PKI model, this method involves certificates and certificate authorities.
A certificate authority (CA) is a trusted third party able to certify that other entities--users, databases, administrators, clients, servers--are who they say they are. A certificate authority might be an external company that offers certificate services, or an internal organization such as a corporate MIS department. The certificate authority has its own certificate and public key, which it publishes, as well as a private key, which is securely maintained. When certifying a user, the certificate authority verifies the user's identity and grants a certificate, signing it with the CA's private key. Servers and clients use the CA's root certificate to verify signatures that the certificate authority has made. The primary services of a CA are
A certificate is like an electronic passport that proves the identity of a user or device seeking to access the network. Used with security policies and other infrastructure, the certificate ensures that the entity's information is correct and that the public key it offers as its "passport number" actually belongs to that entity. The primary contents of a certificate are
Other validating information in a certificate includes the name of the CA that issued the certificate, an expiration date, a unique serial number assigned to the certificate by the CA, the CA's signature, and an algorithm identifier that indicates the particular algorithm that was used to sign the certificate.
A certificate is created when an entity's public key is signed by a CA. Because a certificate is signed by a trusted authority and is obtained in a secure manner, it does not need to be validated for authenticity each time it is accessed. A client or a server can validate that an entity is who it claims to be by verifying that the entity's certificate was issued by a known and trusted certificate authority. A server need be consulted only to find out if the certificate has been revoked. Clients and servers can use these credentials to access secure services, such as SSL, using public key cryptography.
Although every certificate is signed by some known and trusted certificate authority, the particular CA named by a certificate might not be known to the verifying system. To enable that system to trust this certificate, the certificate also names the CA who validated its CA, and the CA before that who validated the earlier CA. This becomes a list of the trusted CAs whose prior verification processes culminated in validating the received certificate. The earliest of these is called the root certificate. Oracle9i Application Server provides several default trusted root certificates, so that users do not have to install their own.
The Secure Sockets Layer (SSL) protocol, developed by Netscape Corporation, is a widely accepted standard for network security. It provides authentication, data encryption, and data integrity, in a public-key infrastructure. SSL is widely employed over the Internet to give users established digital identities and to prevent eavesdropping, tampering with, or forging messages. SSL uses digital certificates (X.509 v3), and a public/private key pair to authenticate users and systems. SSL is supported by all currently available Web servers and Web browsers. It is also gaining acceptance for other protocols, including LDAP and IMAP.
SSL addresses the problem of protecting user data exchanged between tiers in a multitier system. By providing strong, standards-based encryption and integrity algorithms, SSL provides system developers and users with confidence that data will not be compromised on the Internet. Unlike password-based authentication, which authenticates client to server only, SSL can authenticate server to client as well as client to server. This feature is useful in a multitier system that is exposed to the Web, because users want the server authenticated before providing sensitive information, such as credit card numbers. Figure 1-2 illustrates SSL-protected communication links to the Oracle server from a remote client through the Internet and an Oracle Application Server.
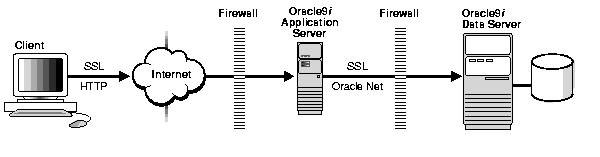
Text description of the illustration sslsecur.gif
Many organizations manage users and authorizations separately in an LDAP-compliant directory. They can also store credentials securely in the directory, enhancing their ability to manage users centrally. Doing so also supports user mobility.
With PKI, secure credentials such as digital certificates can be stored in containers called "wallets." A wallet is used to manage authentication data such as keys and the trusted certificates needed by the Secure Sockets Layer. Wallets can be stored in an LDAP-compliant directory. Security administrators use a tool such as Oracle Wallet Manager to manage security credentials on the server. Wallet owners also use this tool, to manage security credentials on clients.
Public Key Certificate Standards are a set of security standards laid out by the PKI vendor RSA. In particular, Oracle9i Application Server supports PKCS#12, the standard for secure credential storage.
Single sign-on (SSO) to Web-based applications enables users to log on only once to access multiple databases and services. The user need not remember multiple separate identities and passwords, because SSO handles all that after the initial user log-in to each registered application or resource. SSO can be used with security features such as SSL, certificates, and IP checking, as explained later in the SSO chapter of this book.
This section explains why the single sign-on feature saves time and improves security.
It starts with the fact that more and more companies are deploying diverse Web-based e-business applications for use by employees, customers, and partners. Each application typically requires a user or account ID and a password.
From the user's point of view, keeping track of so many account and password pairs is tedious and annoying. The temptation to use shortcuts, as described below, reduces security not only for the individual user but also for the entire community of users. Each breach potentially exposes some or all of the others to damage or loss of confidentiality, whether malicious or unintentional.
From the administrator's point of view, maintaining multiple accounts and passwords for each user is expensive and potentially insecure.
Single sign-on therefore benefits users while easing the burdens of coping with Internet-related volumes and of maintaining security in rapidly changing circumstances.
This section discusses the following points:
Most users cannot remember more than a few passwords. Users who maintain more than one login account often choose passwords that are easy to remember, choose identical passwords for different accounts, reuse passwords when asked to change them, or write passwords down. All these practices reduce password security.
Writing passwords down or choosing easily remembered (and thus easily guessed) passwords increases the risk of passwords being compromised. When a password is compromised, the potential damage increases if users have reused passwords when asked to change them, or have used the same password on multiple systems.
Many systems implement password management mechanisms that force users to choose complex passwords, or prevent them from reusing a password. However, these mechanisms often backfire because users figure out ways to defeat them that may reduce security even more. For example, forcing users to use random passwords almost guarantees that they will be written down.
Changes in a user's membership or functional roles in an organization should cause appropriate corresponding changes in the user's privileges when using the organization's applications. Multiple independent accounts per user make it even more likely that associated user privileges will not correspond with organizational changes. User accounts and access privileges, for example, may remain unchanged in the system long after the user has left the organization or changed roles. This circumstance leaves the system vulnerable to potential attack by disgruntled former employees.
Single sign-on's single point of entry empowers users while they are active, and also gives administrators a single point of control for changing conditions.
Managing multiple accounts and passwords per user is expensive. In many enterprise deployments, a substantial fraction of the system administrator's time is spent on account- and password-related problems. This time includes initial creation of users' accounts when they join the organization and deletion of accounts when they leave. It includes changing settings when they change roles, and resetting passwords that have been forgotten. Administrators must sometimes access multiple systems to add or remove user accounts on each, using multiple administrative interfaces that can have different requirements. All this is expensive, and prone to various types of errors. Single sign-on reduces both types of cost.
Authorization is the process of controlling access to data, resources, or services based on the identity of the user, host, or client. Proper authorization ensures that a user, program, or process receives the appropriate privileges. Once the user is identified through the process of authentication, his appropriate authorization can be determined.
In enterprise systems, it is often desirable to centralize authorization management and control of privileges in the directory. This approach has two important aspects:
Consider, for example, a user who needs access to 40 servers within an enterprise. With single station administration, the administrator can set up access for the user from one place: she need not log in to 40 separate machines. To change the user's privileges on the 40 servers, the system administrator can utilize a single source of control, performing the change at a single server.
Nevertheless, in some circumstances single sign-on is a better solution than is central authority for the organization's needs. With Oracle9i Application Server, both choices are available for appropriate use.
|
See Also:
"Delegated Administration Service (DAS)" Oracle9iAS Single Sign-On Developer's Guide |
Sensitive information that travels over an intranet or the Internet can be protected by encryption. Encryption is the transformation of information into a pattern readable only with a decryption key. This security mechanism is powerful because decryption can be practically infeasible if you do not possess the decryption key.
Consider, for example, an Internet buyer who wishes to purchase a company's product using a credit card in a secure fashion. The buyer's credit card number is encrypted with an encryption key. The encrypted credit card number is sent across the network to the database. Encryption can be used to scramble the message, rendering it unreadable to anyone but the recipient, although this encryption is not mandated since the number itself is encrypted. The server decrypts the message with a decryption key and reads the credit card number.
Encryption must address all communications with the database, including transmissions from clients and transmissions from middle tiers. It must also secure all protocols into the database. Table 1-4 lists encryption algorithms that have become industry standards for the encryption and decryption of data.
Note that the secrecy of encrypted data depends on the existence of a secret key shared between the communicating parties. Providing and maintaining such secret keys is known as key management. In a multiuser environment, distributing keys securely can be difficult, since it's hard to be certain that secrecy is maintained by the parties and that the transmission remains secure. Public-key cryptography was invented to solve this problem.
In addition to encryption, there are integrity algorithms that can ensure data has not been tampered with and that packets have not been replayed. In a replay attack, an observer inserts a copy of something you entered earlier for a different purpose, disrupting what's going on and possibly having destructive effects. These integrity algorithms can be used to detect corruption in data blocks.
A Web browser enables people to use the Internet conveniently by searching, accessing Web sites, sending and receiving transactions, e-mail, and instant messages. A secure browser is essential, so that sensitive data sent or accessed over the Internet is not corrupted or copied by an intruder. Examples of such data include customers' names, e-mail IDs, addresses, and credit card numbers.
In the overall system security picture, the Web browser may be the component over which e-business sites have least control. When running a Web storefront, for example, you may not be able to control the browser that customers use. The customer's browser nonetheless impacts the security of your system, and must be taken into consideration.
Most commercially available Web browsers support a number of security-related features. However, users must configure the browser properly, to take advantage of its security capabilities.
Full consideration of browser security issues is beyond the scope of this document.
Oracle9i Application Server (Oracle9iAS) can be used as a client to the database. In this configuration, all the fundamental database security concepts apply. When designing such a system, you can employ a number of powerful security features of the Oracle9i database. This section provides an overview of the major server security issues, and describes how they are addressed in Oracle9i Application Server:
In Oracle9i Application Server, enterprise user security is provided by the Oracle9iAS Portal component. This section introduces users and groups, and the relationship of users to database schemas, as reflected in the architecture of Oracle9iAS Portal.
In Internet computing, where millions of users may access a portal, user representation must be as lightweight as possible. It is important to avoid a situation in which each user must have a corresponding database schema and a distinct database login.
With Oracle9iAS Portal, a user account does not require its own database schema. Oracle9iAS Portal is primarily implemented in PL/SQL, so a database account is still needed for execution of the PL/SQL code. Users are by default mapped onto a single schema for executing procedures. When Oracle9iAS Portal is installed, a default set of user accounts is created: for the database administrator, for the portal administrator, and for the public.
With Oracle9iAS Single Sign-On, the administrator specifies a user name and password and the Oracle9iAS Single Sign-On privilege level to be given to the user. This privilege level is either End User or Full Administrator. The Full Administrator privilege is required for creating users and other Oracle9iAS Single Sign-On administration tasks.
Oracle9iAS Portal supports groups, which provide a convenient means of granting privileges to a collection of users in one action. In addition, certain attributes in the Oracle9iAS Portal system can be associated with a group, and if a user has a default group specified in his preferences, then those attributes can be applied to his session. Examples of this include a default home page for a group, or a default style.
Management of users, groups, and permissions is increasingly done by a directory. Oracle Enterprise Security Manager is the graphical user interface used to centrally administer enterprise users and enterprise roles in an LDAP directory, such as Oracle Internet Directory. System administrators can use this tool to perform a variety of tasks, such as creating new enterprise domains, assigning enrolled users and published databases to an enterprise domain, and authorizing enterprise roles on systems in the enterprise domain.
Oracle Enterprise Security Manager, which launches out of Oracle Enterprise Manager, scales to tens of thousands of users, and enables you to manage thousands of users and systems in various domains.
Authentication is the process of verifying the identity of a user being presented to the system, usually in a login screen. Typically, the user enters a user name for identification and password for verification.
Authorization depends on authenticating the person or entity requesting the processing of a particular HTTP request. A number of facilities in Oracle HTTP Server can be invoked to establish various forms of user authentication. These include:
Although basic authentication is a standard Web authentication mechanism, it is relatively insecure because user code and password pairs are essentially transmitted in the clear as a base 64-encoded string. Where security is very important, SSL facilities should be invoked because they protect the confidentiality of the challenge and response dialog used when Oracle HTTP Server requests user code and password information.
After the user's identity has been verified (authenticated), rules can be applied to restrict or allow further processing of URL requests. Also, user authentication can be combined with IP and hostname requirements so that processing is allowed only when either or both directives are satisfied.
When you use Oracle9i Application Server as a secure connection to an Oracle9i database, the application server must authenticate itself to the database. These authentication procedures are different from the authentication procedure used by a Web browser.
Proxy authentication is a feature of the Oracle9i database that enables the administrator to allow middle tier connections only on behalf of a particular set of users. The middle tier can authenticate itself, and then establish a lightweight session for its users without the need to authenticate each user separately.
Further, the Oracle9i database can be configured to empower a specific middle tier to assume a specific set of database roles on behalf of a specific user. In other words, the database uses both middle-tier and client user identity to determine the middle tier's privileges when acting for a user through a lightweight session.
Because Java development is very important to the Web, Java security is a vital feature of Oracle9i Application Server. JAAS is part of a larger set of Oracle9i Application Server security services that includes Web single sign-on, network encryption, and other features. JAAS provides core security services for developing Java-based applications. Oracle Corporation designs all of these products to the emerging industry standards for Java security.
JAAS is the Oracle implementation of Java Authentication and Authorization Service (JAAS), a Java package that supports user authentication and access control. While the JAAS specification is not yet integrated with the J2EE security model, JAAS does integrate JAAS with J2EE for developers of Java applications in an Oracle environment. This enables developers to add core security functionality to their Java applications, which J2EE alone cannot provide.
JAAS provides key security services in the following areas:
|
Authentication |
Identifying users |
|
Authorization |
Limiting what users can do |
|
Delegation |
Enabling code to run securely, with privileges of other users |
JAAS provides benefits to any customer developing Java applications. JAAS is also used by a number of Java components within Oracle9i Application Server to provide authentication and authorization services within those components.
|
See Also:
|
To eliminate potential weak points in the network infrastructure, you may opt to pass data from protocol to protocol without the complexity of decryption and re-encryption. To do so securely, you must have some way to transfer data securely across network protocol boundaries.
The Internet enables you to connect your corporate intranet to a broad public network. Although this capability provides enormous business advantages, it also entails risk to your data and your computer system. One way of protecting the privacy and integrity of your system is to place a firewall between the public network and your intranet.
A firewall is a single point of control on a network, used to prevent unauthorized clients from reaching the server. It acts as a filter, screening out unauthorized network users from using the intranet. It does this by enforcing access controls based on the contents of the packets of data being transmitted, and can thus protect against attacks on individual protocols or applications.
Firewalls are rule-based. They have a list of rules that define which clients can connect, and which cannot. They can compare the client's hostname or IP name with the rules, and either grant the client access, or not.
The Internet provides enormous and unparalleled opportunities for both expansion of and efficiencies in communication, commerce, and business practices. Dangers accompany almost every one of these opportunities. These include threats to our privacy, our savings, and our confidence in the reliability of our daily interactions in the personal, professional, and commercial arenas.
These threats can be reduced or eliminated by selecting mechanisms, policies, and practices that enforce both accountability and security limitations in each area of vulnerability. Secure communications can make eavesdropping useless.
Authentication can limit inappropriate system access, and authorization policies can restrict the possibilities for inappropriate data visibility or manipulation.
Each of the applications described in the later sections of this book has built-in security features that protect users and data from the vulnerabilities discussed in this chapter. These features also combine to work seamlessly with the other security software that Oracle supplies and supports.
Once you have understood and mastered the principles and techniques presented in this book, you will be prepared to take the steps necessary to providing effective security for your sites and systems.
See Also:
|
|
|
 Copyright © 2002 Oracle Corporation. All Rights Reserved. |
|