


|

|
|
|
|
Implementing Nonrepudiation
This topic includes the following sections:
Overview of Nonrepudiation
Nonrepudiation is the ability of a trading partner to prove or disprove having previously sent or received a particular business message to or from another trading partner. Consider the following example.
Trading Partner A has agreed to purchase 1000 ergonomic chairs from Trading Partner B. In the course of this agreement, Trading Partner A has sent a business message to Trading Partner B agreeing to buy the chairs at a set price. Later, though, Trading Partner A disputes the original price and denies having sent a message in which they agreed to pay that price.
If a reliable nonrepudiation system has been in place, Trading Partner B can disprove Trading Partner A's claim by producing a document from Trading Partner A specifying the amount Trading Partner A agreed to pay. Further, if this original document is digitally signed, timestamped, recorded, and secured by a trusted third-party source, the validity of this document has full legal recourse.
Nonrepudiation, or the ability to provide legal evidence of the involvement of a denying party, is a requirement for critical business messages. WebLogic Collaborate supports both nonrepudiation of origin and nonrepudiation of receipt:
To support nonrepudiation, the WebLogic Collaborate software incorporates the following services:
The remaining sections in this topic describe each of these services and explain how to incorporate them into your WebLogic Collaborate environment.
Digital Signature Support
The purpose of digital signature support is to provide a means to prevent anyone or anything from tampering with the contents of a business message, especially when the business message is in transit between two trading partners. WebLogic Collaborate provides digital signature support that conforms to the Public Key Cryptography Standard 7 (PKCS7) packaging for digital signatures.
A digital signature itself is a set of data appended to a business message consisting of an encrypted, one-way hash value of data packaged in a specific format (for example, PKCS7 SignedData). A digital signature:
The data required to create a digital signature is obtained from the trading partner configuration data in the repository. The information required to create a digital signature also includes the following:
Business Protocols with Which You May Use Digital Signature Support
WebLogic Collaborate provides digital signature support for messages that use the following business protocols:
Configuring Digital Signature Support
When you configure the WebLogic Collaborate Server, you have the option of specifying a digital signature service. To use a digital signature service, you must configure it as described in Configuring Digital Signatures for Nonrepudiation.
Secure Timestamp Service
If nonrepudiation is being used, secure timestamp services are required to attach a Coordinated Universal Time (UTC) timestamp to the secure audit log when business messages are also logged to the secure audit log. For example, when you receive a business message, a timestamp is entered as a nonrepudiation of receipt (NRR) message in the audit log. When you send a business message, a timestamp is entered as a nonrepudiation of origin (NRO) message in the audit log. WebLogic Collaborate includes a Service Provider Interface (SPI) so that you can incorporate a secure timestamp service from a trusted third-party provider.
If you incorporate a secure timestamp service from a trusted third-party provider, you need to create a Java class file that implements the com.bea.b2b.security.TimestampProvider interface. In the class methods (for example, getTimestamp) of your class implementing the com.bea.b2b.security.TimestampProvider interface, you call out to the third party timestamp provider. For details about creating this application, see Using the SPI for the Secure Timestamp Service.
WebLogic Collaborate prohibits more than one secure timestamp provider from being registered in WebLogic Collaborate. This restriction ensures that all timestamps created in the WebLogic Collaborate system are ordered chronologically.
Note: If you do not configure a secure timestamp service provider in your WebLogic Collaborate server, system time is used for timestamping system events and signatures.
For details about the secure timestamp SPI, see Using the SPI for the Secure Timestamp Service.
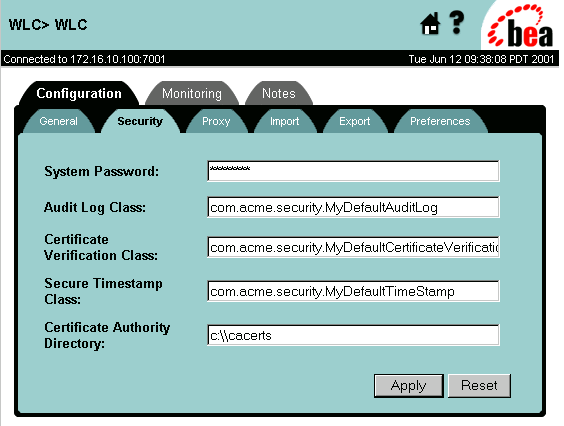
Configuring the Secure Timestamp Service
To configure the secure timestamp service, complete the following steps:
Figure 4-1 WebLogic Collaborate System Security Configuration Page
Secure Audit Log Service
A secure audit log is also required for nonrepudiation. This log typically stores each business message with its digital signature and secure timestamp. You use an audit log to reconstruct the sequence of messages and other system events that have occurred during the exchange of business messages among trading partners.
As with the timestamp service, WebLogic Collaborate provides a Service Provider Interface (SPI) for you to configure a trusted, third-party provider of the secure audit log. If you incorporate a secure audit log service from a trusted third-party provider, you need to create a class file that implements the com.bea.b2b.security.AuditLogProvider interface. In the class methods of your class implementing the com.bea.b2b.security.AuditLogProvider interface (for example, log), you call out to the third party audit log provider. For details about creating this implementation, see Using the SPI for the Secure Audit Log.
Note: If you do not configure a third-party provider for a secure audit log service, WebLogic Collaborate provides a default audit log in a file named secureaudit.log, which you can enable by setting the system property bea.secureaudit to on. This file is based on the logging subsystem in WebLogic Collaborate, and is protected by only the underlying operating system's file permissions system. This file is not digitally signed or encrypted.
Writing to the Audit Log Directly
As an alternative to writing a Java implementation of the com.bea.b2b.security.AuditLogProvider interface to call out to an application that writes to the audit log, you can write an application that writes to the audit log directly via an invocation to the com.bea.b2b.security.Audit.log(byte[] data) method, as shown in the code example provided in this section.
This example is a modification of the CreateMultiplyReply.java class, which is located in the following directory, where WLC_HOME represents the directory in which the WebLogic Collaborate software is installed:
%WLC_HOME%\config\samples\messageManipulators
$WLC_HOME/config/samples/messageManipulators
In this example, the bolded code shows the statements that have been added to show writing to the audit log.
Listing 4-1 Example of Writing to the Audit Log Directly
package wlcsamples;
import java.io.*;
import org.apache.xerces.dom.*;
import org.w3c.dom.*;
import com.bea.eci.logging.*;
import com.bea.b2b.wlpi.MessageManipulator;
import com.bea.b2b.wlpi.WorkflowInstance;
import com.bea.b2b.wlpi.WLPIException;
import com.bea.b2b.protocol.conversation.ConversationType;
import com.bea.b2b.enabler.*;
import com.bea.b2b.enabler.xocp.*;
import com.bea.b2b.protocol.messaging.*;
import com.bea.b2b.protocol.xocp.conversation.local.*;
import com.bea.b2b.protocol.xocp.messaging.*;
//Import the Audit class from security package.
import com.bea.b2b.security.Audit;
public class CreateMultiplyReply implements MessageManipulator{
public CreateMultiplyReply(){};
public XOCPMessage manipulate(WorkflowInstance instance,
XOCPMessage in)
throws WLPIException{
debug("In CreateMultiplyReply");
int integerOne =
((Long)instance.getVariable(WLCSamplesConstants.INTEGER_ONE_VAR)).intValue
();
int integerTwo =
((Long)instance.getVariable(WLCSamplesConstants.INTEGER_TWO_VAR)).intValue
();
int result = integerTwo * integerOne;
debug("integerOne = " + integerOne);
debug("integerTwo = " + integerTwo);
debug("result = " + result);
String sender =
((String)instance.getVariable(WLCSamplesConstants.SENDER_VAR));
String recip =
((String)instance.getVariable(WLCSamplesConstants.RECIPIENT_VAR));
debug("sender = " + sender);
debug("recip = " + recip);
XOCPMessage xocpmsg = null;
try{
DOMImplementationImpl domi = new DOMImplementationImpl();
// "reply" - (param1) The qualified name of the document
// type to be created.
// "reply" - The document type public identifier.
// "multiply-reply.dtd" - The document type system identifier
DocumentType dType = domi.createDocumentType("reply", "reply",
"multiply-reply.dtd");
org.w3c.dom.Document rq = new DocumentImpl(dType);
Element root = rq.createElement("multiply-reply");
rq.appendChild(root);
Element elementProduct = rq.createElement("integer-product");
Text tProduct = rq.createTextNode( new Integer(result).toString() );
elementProduct.appendChild(tProduct);
root.appendChild(elementProduct);
String note =
"Dear " + sender + ": " +
"Here is the product of " + integerOne + " and " + integerTwo + ". " +
"With Love, " + recip + ".";
debug("NOTE...\n" + note );
// we got the data here. Let us log it
new byte[] ba = note.getBytes();
Audit.log(ba);
Element elementNote = rq.createElement("note");
Text tNote = rq.createTextNode( note );
elementNote.appendChild(tNote);
root.appendChild(elementNote);
debug("Created root: \n" + root.toString() );
xocpmsg = new XOCPMessage("");
xocpmsg.addPayloadPart(new BusinessDocument(rq));
}catch(Exception e){
debug("Error at manipulate.");
e.printStackTrace();
throw new WLPIException("CreateMultiplyReply raised exception:" + e);
}
return xocpmsg;
}
/**
* A simple routine that writes to the wlc log
*/
private static String debug(String msg){
UserLog.log("****CreateMultiplyReply: "+msg);
return msg;
}
}
Configuring the Secure Audit Log
To configure the secure audit log, complete the following steps:
Figure 4-2 WebLogic Collaborate System Security Configuration Page

Using the Service Provider Interfaces (SPIs) for Nonrepudiation
This section describes the SPIs for the following nonrepudiation services:
Using the SPI for the Secure Timestamp Service
WebLogic Collaborate allows you to create a customized secure timestamp service by implementing the com.bea.security.TimeStampProvider interface. If you implement a timestamp using the SPI described in this section, you must configure this service later in the WebLogic Collaborate Administration Console so that the service is invoked properly during run time.
The com.bea.b2b.security.TimeStampProvider interface has the following methods, which a timestamp application must implement:
This method returns a string specifying the time in Coordinate Universal Time (UTC) format.
This method returns a string specifying the UTC time in milliseconds.
Your implementation of the timestamp interface must include a default public constructor with no arguments. Neither the constructor nor any methods in the class that implements the TimeStampProvider interface should throw any exceptions.
Using the SPI for the Secure Audit Log
WebLogic Collaborate allows you to create a secure audit log service by implementing the com.bea.security.AuditLogProvider interface. If you implement an audit log service using the SPI described in this section, you must configure this service later in the WebLogic Collaborate Administration Console so that the service is invoked properly during run time.
The com.bea.b2b.security.AuditLogProvider interface has the following methods, which a secure audit log application must implement:
This method initializes the audit log.
This method is invoked to log a message in the secure audit log. It has the following parameters:
Contains the component that is logging the message
Specifies the type of the nonrepudiation message
Contains the data to be logged
Contains the name of the trading partner who is logging this message
Your implementation of the secure audit interface must include a default public constructor with no arguments. Neither the constructor nor any methods in the class that implements the AuditLogProvider interface should throw any exceptions.
Audit Log Messages
All log messages correspond to the DTD log-message.dtd, which defines the contents for each message type.
All audit log messages have the following three identifiers:
The following table describes the contents of the data for each of the message types. All the log messages contain the timestamp obtained from the timestamp provider that is configured in WebLogic Collaborate.
Audit Log DTD
The following code example shows the log-message.dtd file:
<!ELEMENT LOG (non-repudiation-origin| non-repudiation-receipt | application)>
<!ATTLIST LOG time-stamp CDATA #REQUIRED >
<!ATTLIST LOG location CDATA #IMPLIED >
<!ATTLIST LOG Principal CDATA #IMPLIED >
<!ELEMENT non-repudiation-origin (#PCDATA)>
<!ELEMENT non-repudiation-receipt (#PCDATA)>
<!ELEMENT application (#PCDATA)>
|
|

|
|
|
|
Copyright © 2001 BEA Systems, Inc. All rights reserved.
|