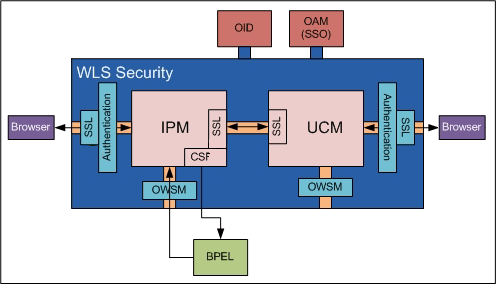
2.1 Security Model Overview
Access to documents within Oracle I/PM first requires access to the Oracle I/PM system. The Oracle I/PM system is managed within a WebLogic Server domain and the WebLogic Server credential store is leveraged to grant access to I/PM. Once access to the I/PM is granted, access to Oracle I/PM features and documents requires security rights assigned by an Oracle I/PM administrator.
The first person to log in to Oracle I/PM after initial installation is granted full rights to all features, in order to properly set up an Oracle I/PM solution to meet company needs. After the system is properly set up, security rights can be changed or revoked if necessary. Additionally, initial security rights can be reset if the credential store has been changed during set up. See "Installation Security Initialization" for more information.
2.1.1 System Access
As managed servers running within a WebLogic Server domain, user and group access to Oracle I/PM and its repository is controlled by WebLogic Server. As such, system security configuration, as well as SSL configuration if desired, is handled through the WebLogic Server console. If additional services are required, such as Oracle Internet Directory or single sign on using Oracle Access Manager, these can be linked to the WLS domain managing I/PM using WebLogic Server controls.
Access to Oracle I/PM through web services is controlled by Oracle Web Services Manager (OWSM) policies. Policies are configured through the WebLogic Server console. Some policies require a keystore be defined. For example, Oracle I/PM must use access credentials stored in Credential Store Framework (CSF) to communicate with a BPEL server or to use SSL. Keystores can be defined using Keytool from the Java Development Kit. Credentials can be added to defined keystores using WebLogic Scripting Tool (WLST).
For additional information, see the following documentation:
Table 2-1 Additional System Security Documentation
| Task | Where to Go For More Information |
|---|---|
|
Administering Oracle WebLogic Server |
Oracle Fusion Middleware Administrator's Guide |
|
Using WebLogic Scripting Tool |
Oracle Fusion Middleware WebLogic Scripting Tool Command Reference |
|
Administering Universal Content Management |
See the following Oracle Universal Content Management guides:
|
2.1.2 Installation Security Initialization
The first person to log in to Oracle I/PM after initial installation is granted full rights to all features, in order to properly set up an Oracle I/PM solution to meet company needs. WebLogic Server managing Oracle I/PM can provide multiple credential store providers to its hosted applications.
During WebLogic Server installation, one of the credential stores was defined as the default. Upon installation, Oracle I/PM, it uses the default credential store. If the credential store changes after the first Oracle I/PM user logs in, system security must be reset. For example, if the security configuration is changed to point to an Oracle Internet Directory (OID) provider or a Microsoft Active Directory provider, you must reset I/PM system security.
To reset system security, do the following:
-
Create or migrate users and groups to the new policy store using the management tools associated with the policy store.
-
Open WebLogic Scripting Tool (WLST) and run refreshIPMSecurity() MBean command. The system security is reset. For information on using WLST to run MBean commands, see "Using WLST to Change MBeans" or Oracle Fusion Middleware WebLogic Scripting Tool Command Reference.
Note:
During the refresh, users or groups for whom matching identifying information is not found are ignored. As security changes are made, invalid users or groups are removed from the I/PM database.For information on configuring WebLogic Server security providers, such as Oracle Internet Directory (OID) or Microsoft Active Directory, see Oracle Fusion Middleware Installation Guide for Oracle Enterprise Content Management Suite.
2.1.2.1 Migrating User Store from LDAP Server to Oracle Internet Directory
For information on migrating an existing LDAP Server user store to Oracle Internet Directory, see “Migrating Oracle I/PM Users and Groups from the Embedded LDAP Server to Oracle Internet Directory” in Oracle Fusion Middleware Installation Guide for Oracle Enterprise Content Management Suite.
2.1.3 Integration with Single Sign-On
Oracle Access Manager (OAM), part of Oracle's enterprise class suite of products for identity management and security, provides a wide range of identity administration and security functions, including several single sign-on options for Fusion Middleware and custom Fusions Middleware applications. OAM is the recommended single sign-on solution for Oracle Fusion Middleware 11g installations.
For smaller scale Oracle Fusion Middleware 11g installations, where you do not have an enterprise-class single sign-on infrastructure like Oracle Access Manager, you only need to provide a single sign-on capability within your specific Fusion Middleware application, you can configure a SAML-based SSO solution. If you need to provide single sign-on with other enterprise applications, this solution is not recommended.
If your enterprise uses Microsoft desktop logins that authenticate with a Microsoft domain controller with user accounts in Active Directory, then configuring SSO with Microsoft Clients may also be an option to consider.
The setup required for each of these SSO solutions is described in the following documents/sections:
Table 2-2 Single Sign-on Documentation
| For Information On... | See The Following Guide... |
|---|---|
|
Configuring OAM and OSSO |
|
|
Using Windows Native Authentication for Single Sign-on |
Oracle WebLogic Server Admin Console Help: Configure Authentication and Identify Assertion Providers |
|
Using WebLogic SAML for Single Sign-on |
High-Level Process for Configuring SAML-based Single Sign-On
-
Generate and register certificates.
-
Create the SAML Credential mapping provider instance.
-
Configure a relaying party.
-
Configure source site federation services.
-
Configuring the SAML Identity Assertion provider.
-
Configure destination site federation services.
-
Deploy the <application> server for SAML SSO.
-
Check your configuration.
2.1.4 Definition Management Security Rights and Definition Security Rights
Once a user or group has been authenticated and access to Oracle I/PM has been granted, security rights to Oracle I/PM definitions take over.
Oracle I/PM definitions include the following:
-
Applications
-
Inputs
-
Searches
-
Connections
Note:
Document security is defined within an application and includes security rights to annotations associated with a document. See "Working with Document Security" and "Working with Annotation Security".If a user has been authenticated for access to Oracle I/PM but has not yet been given security rights to any Oracle I/PM definitions or definition management, they are presented with the Home page, but no navigation links are displayed in the Navigator Pane.
To properly administer an I/PM solution, a distinction must be made between definition management rights and definition rights:
-
Definition management security rights grant a user the ability to create or administer definitions (applications, inputs, searches, and connections).
-
Definition rights grant a user the ability to view, modify, delete, or manage access to specific definitions, such as an application named Invoice or search named Purchase Order.
Oracle I/PM definition management security rights and definition rights are managed within the Oracle I/PM user interface.
2.1.4.1 Definition Management Rights
Definition management security is done using the Manage Security pages, accessed from the Manage Security panel of the Navigator Pane. Definition management rights have two levels of security:
| Security Right | Definition |
|---|---|
| Administrator | Grants users or groups full rights to definition management and includes the ability to assign other users or groups Administrator or Create rights. |
| Create | Grants the ability to create definitions. Users who create a definition are assigned all definition rights for that definition by default. |
In order to ensure that only authorized people have access to sensitive documents across an enterprise, there is an additional restriction for users and groups with Administrator rights to search definitions and input definitions. They cannot modify or delete any search definitions or input definitions that are dependent on applications to which they do not have View security rights. Similarly, users with Administrator rights to applications cannot modify or delete any application definitions that are dependent on connections to which they do not have View security rights. This is designed to prevent them from changing definitions in order to gain access to documents that are restricted to them.
For example, as designed, a user in the Human Resources group with Administrator rights to search definitions could view all search definitions, including those for Accounts Payable, but because they do not have View rights to the Accounts Payable application, they would not be able to modify or delete an Accounts Payable search definition.
2.1.4.2 Definition Rights
Definition security is defined when the definition is created and managed using the appropriate panel of the Navigator Pane. Definition rights have four levels of security:
| Security Right | Definition |
|---|---|
| View | Enabled by default. Grants the user or group the right to view this definition. |
| Modify | Grants the user or group the right to modify all aspects of this definition except for granting security rights. |
| Delete | Grants the user or group the right to delete this definition. |
| Grant Access | Grants a user or group the right to grant security rights to others for this definition. If this is the only security level granted, the user can modify only the security information for this definition. |
2.1.5 Users and Groups
Definition management rights and definition rights are defined for either individual users or for user groups managed through separate security providers to WebLogic Server, such as Oracle Internet Directory (OID) or other. Once authenticated and available to I/PM, users or groups are granted various levels of access to definitions and definition management using the Oracle I/PM user interface. For example, when an application definition is created, a user or group is granted View rights to the application when they are added using the Application Security Page. Additional rights are then specified as required.
Groups are an efficient way to assign security rights to many individuals in an organization with identical access needs. For example, a Managers group could contain managers across an enterprise who need View rights to documents checked in using an application called Resumes, and an HR_Managers group can be given Write, Delete, and Grant Access rights to the same application in order to upload and delete resumes to and from I/PM or grant access to new managers.
Note:
Group membership is loaded at the time a user logs in to Oracle I/PM and remains active throughout the session until the user logs out. If a user is removed from a group while the user is logged in, that user retains the full rights of the group until the user logs out or the session is closed. The new user rights will take effect at the next log in.Document security is assigned when an application is defined and only allows security rights to be assigned at the group level.