4 Updating an OS
Enterprise Manager Ops Center enables you to update, or patch, the following operating systems:
-
Oracle Solaris 8, 9, and 10 (SPARC)
-
Oracle Solaris 10 (x86)
-
Oracle Linux
-
Red Hat Linux Advanced Server 3, 4, and 5
-
SUSE Linux Enterprise 8, 9, and 10
-
Microsoft Windows
About Updating an OS
You can use Enterprise Manager Ops Center to update operating systems, such as Solaris, Linux and Windows, to the latest released patches. It reduces the complexity of patching a large number of systems, standardizes the patch installation process, minimizes downtime, and automates patching without user interaction. You can manage different patching conditions that exist for installing a patch. The software helps you to keep track of the patching conditions and helps you do your work efficiently and effectively.
How to Start Patching in Enterprise Manager Ops Center?
You must first discover and manage the OS. Managing an OS enables the patching operations through Enterprise Manager Ops Center. Discovering and managing an OS gathers information about the OS and installs the agent controller software on the OS. When you install the agent controller on the OS, the following actions occur:
-
It takes at least 5 minutes for the agent to be registered. You cannot update the OS until the agent is registered.
-
A notification is sent when the update function is enabled for the OS.
-
The agent controller runs an inventory check on the OS and creates a catalog for the OS. The catalog lists the patches and packages, and the versions that are currently installed on the OS.
The update function enabled for a user depends on the roles that are granted for that user. See Update Roles and Authorizations for the roles granted to a user. Contact your administrator to get the appropriate role.
What Does Enterprise Manager Ops Center Provide to Help Patching?
Enterprise Manager Ops Center provides the following:
-
Update Profiles
-
Update Policies
-
Catalogs
-
Reports
You create update jobs with OS update profiles and policies to patch an OS. OS Update profiles and policies define which patches must be installed, and how the update job proceeds after determining the patch dependencies and user interaction. There are system-defined update profiles and you can also create your own customized profiles and policies.
The snapshots of the OS are taken after executing any job on the OS. The snapshots are stored as catalogs with a time and date stamp. You can also create a catalog and store the catalogs. You can compare the catalogs between operating systems and create profiles from the saved catalogs that can be later used for creating systems. At any point of time, you can roll back to a saved state of the system.
Enterprise Manager Ops Center provides reports for different operating systems. Reports give an insight into the OS compliance status to the recommended patches and packages. Generate reports to know the state of your OS patch levels.
How Does the Enterprise Controller Provide the Latest Updates?
The Enterprise Controller obtains information about latest updates from the Knowledge Base. It requires an Internet connection to connect to the Knowledge Base to download the patches from OS vendor sites. In the absence of an Internet connection to the Enterprise Controller, you can get the latest updates using different ways. See Using Knowledge Base and Connection Modes for more information about knowledge base and connected mode.
How to Run an Update Job in Enterprise Manager Ops Center
When you manage an OS, the update functions are enabled for the OS. The New Update OS Job option is enabled in the Actions pane for the OS. This option invokes a wizard where you define the job parameters. You can also run an update job in Enterprise Manager Ops Center from:
-
Update profiles and policies
-
System catalogs
-
Reports
You can use the appropriate options to run an update job from these sections. These sections launch an update job with patches that must be installed or removed accordingly.
What are the Options Available When Running an Update Job?
You have the following options available when running an update job:
-
Select update profiles and policies.
-
Select different targets for each task in the job.
-
Select job simulation mode. Simulating a patching job helps to estimate the time required to run the job, to know the patch dependencies and the expected job result. In the simulation mode, you can select to download the required patches.
-
Roles specification for an user to carry out only specific tasks on an asset.
-
Failure policy to determine the action when a task fails.
Using Knowledge Base and Connection Modes
This section provides information about Knowledge Base and the connection modes of the Enterprise Controller. It describes the procedure to switch the Enterprise Controller mode, and how to get the latest updates of an OS in the disconnected mode.
Knowledge Base
The Knowledge Base (KB) is the repository for metadata about Solaris and Linux OS components. The metadata includes patch dependencies, standard patch compatibilities, withdrawn patches, downloads, and deployment rules. The KB stores a mapping of the OS download URLs and uses those URLs to download the components from the appropriate vendor download site.
The following operating systems are supported:
-
Solaris 10, 9, and 8 OS
-
Oracle Linux
-
Red Hat Enterprise Linux (RHEL)
-
SUSE Linux Enterprise Server (SLES)
KB Update Intervals
The following are the maximum intervals between updates:
-
New Solaris patches – 1 day (including security patches, Oracle Solaris Cluster patches, and standard patches)
-
Solaris updates – 3 weeks
-
Solaris EIS Baseline – 7 days
-
Solaris Freeware Package – 3 days
-
Linux Software Update (RPM) – 1 day
-
Linux Service Pack – 3 weeks
-
Linux Distribution New Version – 30 days
Connection Modes
The Enterprise Controller requires an Internet connection to connect to the KB and to download the patches from the OS vendor sites. In the connected mode, the Enterprise Controller has an Internet connection to connect to the KB. The KB contains the metadata information about the latest patches and packages released. By default, Enterprise Manager Ops Center is configured in connected mode, where the Enterprise Controller has an Internet connection to the KB. When an update job is started, the agent sends a request to the KB through the Enterprise Controller. When running in connected mode, the KB is updated on a regular basis.
You can configure your environment and Enterprise Manager Ops Center to run in disconnected mode by changing the connection mode of the Enterprise Controller. In disconnected mode, the Enterprise Controller does not have Internet access to connect to the KB.
In disconnected mode, you must manually upload all the required content to the Enterprise Controller. If the software and other files are not uploaded, an error message similar to Not installable by current KB is displayed when you run jobs. You can create a local KB on your Enterprise Controller when you are operating your Enterprise Controller in disconnected mode.
Uploading patches and packages to the Enterprise Controller in disconnected mode is similar to uploading local content, and is identified as local content. To upload all of the current and appropriate software and patches, use Bulk Upload Packages and Patches option. Several other upload options are available to upload all the patches, packages, and RPM content, including uploading from an EIS DVD or Solaris CD/CD.
For more information about uploading local contents, see Oracle Enterprise Manager Ops Center Advanced User's Guide.
To create a local KB, you can run a harvester script provided by Enterprise Manager Ops Center on a system outside the data center that has Internet access. The harvester script downloads the patches and packages. You can then save the downloaded information to a portable media device, such as a CD or DVD, bring it into to your data center, and manually upload to the Enterprise Controller.
You can operate the Linux-based Enterprise Controller in disconnected mode. However, you cannot use the harvester script to obtain the KB bundle. The harvester script is mainly for the Solaris OS.
Semi-disconnected Mode
If your data center allows Internet access or infrequent access, you can run your Enterprise Controller in disconnected mode until you need patches or packages. You can then change the Enterprise Controller's connection mode to Connected, download the required patches and packages, and then change the Enterprise Controller back to Disconnected mode.
Note:
You can import only signed patches from My Oracle Support or EIS DVD and the patches must be of the format jar, jar.gz or in the patch directory.Switching the Enterprise Controller Mode
During the initial Enterprise Controller configuration, you have an option to set up Enterprise Manager Ops Center in disconnected mode. If you select this mode, you have the option to change the mode to connected after the Enterprise Controller is operational (the assets are discovered, agents are provisioned, systems are updated, and so forth.)
When in connected mode, authentications, such as Online Account or My Oracle Support (MOS) credentials, are necessary to download updates and other content from Oracle and third-party sites.
Note:
The first time you change to connected mode, you must add your Online Account in the UI to access the Knowledge Base Service and any HTTP proxy to access the Internet.-
Select Administration from the Navigation pane.
-
Select Setup Disconnected Mode from the Actions pane.
-
Select Switch to Connected Mode. A confirmation window is displayed. Click Confirm to switch to connected mode.
To Switch to Disconnected Mode
You must first load a KB bundle or you will be unable to switch modes.
-
Select Administration from the Navigation pane.
-
Select Setup Disconnected Mode from the Actions pane.
-
Specify a KB bundle and click Load KB Bundle.
-
Select Switch to Disconnected Mode. A confirmation window is displayed. Click Confirm to switch to disconnected mode.
Obtaining a KB Bundle With the Harvester Script
When the Enterprise Controller runs in disconnected mode, the harvester script that downloads the metadata and patches does not operate. You must use another system that connects to the Internet to get the Knowledge Base (KB) bundle and provide it to the Enterprise Controller.
To get a KB bundle, use the following general procedure:
-
Identify a system that can connect to the Internet.
-
Load the prerequisite software onto the system.
-
Transfer the harvester bundle to the system.
-
Use the harvester script to download the KB bundle.
-
Copy the bundle onto removable media such as a CD, DVD or memory stick.
-
Bring the media to the system that runs the Enterprise Controller and copy the KB bundle to a directory on the local file system of the Enterprise Controller.
Note:
Disconnected mode is supported on a Linux Enterprise Controller. However, the harvester script to get a KB bundle is not supported on Linux.Harvester Script Utility
The harvester script is available at https://updates.oracle.com/OCDoctor/harvester_bundle-latest.zip. This script must be run on a system that is connected to the Internet. This script helps to download the latest KB bundle.
Loading Prerequisite Software
The harvester script requires that the system has wget version 1.10.0 or later installed. Perform the following steps to install the appropriate version of wget software:
-
To check the version of wget, run the wget command with the
-Voption, for example:# /usr/sfw/bin/wget -V GNU Wget 1.10.2 Copyright (C) 2005 Free Software Foundation, Inc. This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. # -
If an older version of the wget is installed, download the version 1.10.0 or later and install it on the system connected to the Internet.
The latest version of wget is available at:
# pkgadd -d wget-1.11.4-sol10-sparc-local The following packages are available: 1 SMCwget wget (sparc) 1.11.4 Select package(s) you wish to process (or 'all' to process all packages). (default: all) [?,??,q]: Processing package instance <SMCwget> from </jf/wget-1.11.4-sol10-sparc-local> wget(sparc) 1.11.4 Free Software Foundation Using </usr/local> as the package base directory. (output omitted) Installation of <SMCwget> was successful. #wget version 1.11.4 depends on additional software:
-
openssl-0.9.8j
-
libiconv
-
libintl
-
/usr/local/lib/libgcc_s.so.1and/usr/local/lib/libstdc++.so.6- Installinglibgcc-3.4.6orgcc-3.4.6installs these files. Download each of these objects from sunfreeware.com and install them on the Internet-facing system.
-
-
With the additional software installed, verify that the wget command runs. The wget command installs into the
/usr/local/bindirectory, for example:# /usr/local/bin/wget -V GNU Wget 1.11.4 Copyright (C) 2008 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later <http://www.gnu.org/licenses/gpl.html>. This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law.
Transferring the harvester Bundle to the System
The harvester bundle contains the script harvester.sh and signing utilities for signature checking and generation of the downloaded software. To download the script:
-
On the internet-facing system, download the harvester script from
https://updates.oracle.com/OCDoctor/harvester_bundle-latest.zip. -
Unpack the bundle
harvester_bundle.tar.gz.
Using the harvester Script to Obtain the KB Bundle
-
On the system, create a temporary directory, for example,
/var/tmp/OpsCtr, to hold the password file that you create in this procedure.# mkdir -p /var/tmp/OpsCtr
-
Create an empty file named
/var/tmp/OpsCtr/mypasswd, and set its permission mode to 400.# touch /var/tmp/OpsCtr/mypasswd # chmod 400 /var/tmp/OpsCtr/mypasswd
-
Edit the
/var/tmp/OpsCtr/mypasswdfile so that it contains the password of your Online Account. The followingechocommand appends the password to the/var/tmp/OpsCtr/mypasswdfile. (Replace password with the correct password.) For example:# echo password > /var/tmp/OpsCtr/mypasswd -
Change the permission of the harvester script to 744. For example:
# chmod 744 harvester # ls -l total 36 -rwxr--r-- 1 root root 17546 Jan 27 04:56 harvester #
-
Run the harvester script, with at least the
-uand-poptions:-
-uOnline Account user name – Specify the Online Account user name that you have registered with the Oracle Inventory online environment. -
-ppassword-file – Specify the full path name of the file that contains the Online Account password. -
-xproxy url – Specify the https URL to the proxy server. -
-Uproxy user – Specify the proxy user name. -
-Pproxypassfile – Specify the full path name of the file that contains only the proxy password. -
-tdir – Specify the temporary directory for storing the downloaded contents. Ensure that this directory is empty before running the script. -
-c– Use this option to clean up the temporary directory if the downloaded contents exist. By default, all the downloaded contents are stored and not cleared. -
-dlist – Specify the distributions for which you want to download all the Solaris patches. Specify a quoted, space separated list of the names of Solaris OS distributions for which you want to download patches. If the distribution is not specified, the patches for all Solaris distributions are downloaded. Without the-doption, the harvester script downloads only the metadata. Available distributions are:-
SOLARIS_10_0_SPARC
-
SOLARIS_10_0_X86
-
SOLARIS_9_0_SPARC
-
SOLARIS_8_0_SPARC
The disk space requirement on the Internet-facing system and the Enterprise Controller to run the harvester script with
-doption is approximately 150 GB for a distribution.Note:
Do not use the-doption while running the harvester script. It might take couple of days for the harvester script to finish running with the-doption. You can upload the patches in bulk from the EIS DVD. -
-
-Rrevisions – Specify the number of revisions of a patch to download. By default, the revision number is 100. -
-sdistro – This option displays the baselines for a given distribution. You can enter only one distribution at a time. Valid distributions are:-
SOLARIS_10_0_SPARC
-
SOLARIS_10_0_X86
-
SOLARIS_9_0_SPARC
-
SOLARIS_8_0_SPARC
-
-
-bID – Specify the Solaris baseline ID to download.Note:
When you use the-boption, you must use the-doption. You can use the option only for one distribution. -
-khost – Specify the hostname of a different Knowledge Base which hosts the metadata information.
-
Examples of Running the harvester Script
Example 4-1 Running Harvester Script with Online Account
Running the harvester script only with the Online Account user name and password.
# ./harvester -u username@oracle.com -p /var/tmp/OpsCtr/mypasswd
Directory /export/home/public not found. This directory will be created.
Setting up local directory structure at: /export/home/public
Initialization: Downloading channels.xml
Tue Jan 27 05:08:01 MST 2009 Clearing cookies to initialize new session.
Distributions:
Identifying and Downloading the Notifications and Seeker scripts
Creating tarball...
Tarball successfully created at /discon/standalone-0127.tar.gz
Start time: Tue Jan 27 05:08:00 MST 2009
Completion time: Tue Jan 27 05:08:01 MST 2009
Tarball includes 0 distribution(s):
Tarball includes only distribution metadata (no patches.)
Please copy this file to a Ops Center server and
use the BUI to configure Update Disconnected Mode.
When you are finished you can delete the content in /export/home/public
#
The harvester script without the -d option generates a .tar.gz file that contains the KB metadata only (no patch content). In this example, the harvester script created the /discon/standalone-0127.tar.gz KB bundle.
Example 4-2 Running Harvester Script to Download Solaris 10 SPARC patches
Running the harvester script to download Solaris 10 patches up to four revisions for a SPARC distribution
./harvester.sh -u username@oracle.com -p /var/tmp/OpsCtr/mypasswd -d "SOLARIS_10_0_SPARC SOLARIS_10_0_X86" -R 4
Example 4-3 Running Harvester Script to Display Baselines for Solaris 10 SPARC
Running the harvester script to display the available Solaris baselines for a Solaris 10 SPARC distribution.
./harvester.sh -u username@oracle.com -p /var/tmp/OpsCtr/mypasswd -s SOLARIS_10_0_SPARC
Example 4-4 Running Harvester Script to Download Security Baselines for Solaris 10 SPARC
Running the harvester script to download the security baseline DEC-2009 for a Solaris 10 SPARC distribution.
./harvester.sh -u username@oracle.com -p /var/tmp/OpsCtr/mypasswd -d "SOLARIS_10_0_SPARC" -b 40011729
Example 4-5 Running Harvester Script Using a Proxy Server
Running the harvester script using a proxy server instead of directly connecting to the Oracle Knowledge Base Service.
./harvester.sh -u username@oracle.com -p /var/tmp/OpsCtr/mypasswd -x http://www.oracle.com -U proxyuser -P /var/tmp/proxypassword
Example 4-6 Running Harvester Script Using Different Knowledge Base Server
Running the harvester script using a different Knowledge Base server. You can point it to another server instead of the default server getupdates.oracle.com.
./harvester.sh -u username@oracle.com -p /var/tmp/OpsCtr/mypasswd -k servername.com
Enhancements in the Harvester Script
The following enhancements were made to the harvester script:
-
The new harvester script performs incremental downloads. The user can choose not to delete the previously downloaded data. This action makes subsequent runs of the harvester script faster.
-
The new option
-Ris provided to define the number of revisions of a patch to be downloaded. This reduces the number of patches to be downloaded. -
The new option
-bis provided to download the full baselines. The download includes the dependencies for the patches in the baselines also. -
The patch download progress counter was added; it displays the number of patches to be downloaded. This counter is updated after every 10 patches are downloaded.
Transferring the KB Bundle to the Enterprise Controller
-
Copy the KB bundle onto removable media that you can use to install the KB bundle on the Enterprise Controller.
-
Copy the KB bundle into a directory on a local file system of the Enterprise Controller.
-
Load the KB bundle into Ops Center on the Enterprise Controller. See Loading and Refreshing a KB Bundle for more information about loading and refreshing a KB bundle.
Loading and Refreshing a KB Bundle
To load or refresh a KB bundle, a new KB bundle must be generated by the harvester script and then loaded. To refresh with a newer KB bundle, run the harvester script again and load the KB bundle. For more information about obtaining a KB bundle, see Obtaining a KB Bundle With the Harvester Script.
To Load and Refresh a KB Bundle
Perform the following steps to load and refresh a KB bundle:
-
Select Administration from the Navigation pane.
-
Select Setup Connection Mode from the Actions pane. The Configuring Disconnected Mode window is displayed.
-
Browse for and select a KB bundle, then click Load KB Bundle.
-
Switch to disconnected mode.
Note:
Unpacking and untarring can take some time depending on the size of the bundle. The absolute path to the generated KB bundle must be specified when you load the bundle. For example, a bundle could be located at/tmp/standalone-0127.tar.gz.Update Profiles
Update profiles specify which update components are to be installed and which are not allowed, and actions to perform on a system. You use profiles to maintain the configuration of the system that you want to manage.
Enterprise Manager Ops Center provides system-defined policies that are not editable and cannot be deleted. You can also create customized profiles by selecting the required OS update components and the required action that must be applied.
Use profiles to accomplish the following:
-
Manage multiple systems in a consistent manner
-
Automate repetitive administration jobs
-
Record the requirements of your enterprise
-
Automatically configure servers and workstations
-
Manage dependencies and ensure consistency
The profile settings Required, Not Allowed, and Upgrade affect a managed host only during the actual deployment of that profile. At any time you can run a job that contradicts the settings of a previously used profile, therefore you should thoroughly understand your system settings and requirements.
Predefined profiles are provided to perform common system-wide checks and to automate the operating system updates. These profiles cannot be edited or deleted.
The following predefined profiles are available:
-
Check Bugs Fix – Checks every bug fix patch known to the Enterprise Controller of the selected distribution to see whether the patch applies to the installed components.
-
Check Security – Checks every security update known to the Enterprise Controller of the selected distribution to see whether the update applies to the installed components.
-
Check System – Installs or upgrades missing dependent components according to the rules that are set in the satellite local services of the selected distribution.
-
Check Withdrawn Patches – Checks all installed patches to find out whether any patches have been withdrawn. If any patches are withdrawn, the profile either upgrades to a newer patch or downgrades to a supported version.
-
Local Software Review – Checks local components against the Enterprise Controller of the selected distribution. This profile helps to locate uncertified versions of software packages. If you confirm the actions of this profile, the currently installed version is replaced with a certified version.
-
Perform Reboot – Restarts the selected system.
-
Perform Reboot + Reconfigure – Restarts the selected system and performs specific post-installation configurations.
-
Upgrade All Components – Checks all the installed components of the selected distribution to see if any of those components can be upgraded.
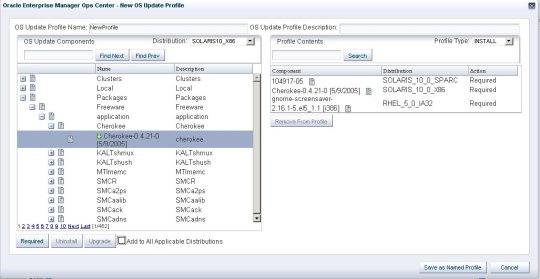
Creating an OS Update Profile
You must have the Admin role to create update profiles in Ops Center. An OS update job requires one profile and one policy. Profiles cannot be nested or combined, except as noted below. When the job is submitted a component called the Dependency Resolver (DR) attempts to find a series of actions that can be performed on the target which satisfy the requirements of the Profile and any conditions imposed by the Policy.
It is important to note that a Profile is not limited to a set of actions for a single operating system; it can contain actions for one or more different operating systems, but each action is OS-specific. When the profile is applied on the target system, actions which do not apply to the target OS are disregarded without informing the user. Thus a job containing a profile which has no actions applicable to the target OS will take no action and will report a successful run.
The options associated with Update Profiles will be disabled if no distributions are activated. This can happen if you have selected not to configure the Software Update Service from the initial configuration wizard of the Enterprise Controller. Similarly, profiles can only be created for active distributions. To resolve these issues select an existing asset of the required OS type and manage it.
Note:
The process of managing an asset and activating its distribution takes few minutes to complete.-
Select Plan Management from the Navigation pane.
-
Select Update Profiles from the Profiles and Policies tree.
-
Select New Profile from the Actions pane.
The New OS Update Profile window is displayed.
-
Enter a profile name and brief description of the profile.
-
(Optional) Select a Profile Type. Valid types include Upgrade, Install and Script. The default type is Unknown. The profile type is simply a tag to assist when creating deployment plans.
-
Install indicates that new components to be installed
-
Upgrade indicates that existing components are upgraded
-
Script indicates that action scripts are executed.
Note:
It is possible to create profiles that do all the actions of the profile type, or to tag a profile with a type inconsistent with its actions. The tag is used for filtering the required profiles in deployment plans. See Oracle Enterprise Manager Ops Center Advanced User's Guide for more information about complex plans.
-
-
For each OS that the profile applies to, select the Distribution from the drop-down list. (For example, SOLARIS10_X86)
-
Locate and select a Component from the Component tree. You can locate the component by clicking the Expand (+) icon, or by entering any part of the component name in the search. If a component cannot be found, check whether the selected Distribution is correct.
-
If required, select the check box to specify that the component should be added to all applicable distributions.
Note:
This only applies to distributions that are active at the time the profile is created. As new distributions are activated you must edit the profile to explicitly add any components for those distributions. -
Specify whether the action is Required, Upgrade, or Uninstall.
Note:
Some actions might not apply. For example, a component cannot be Required if the system does not have the information about how to obtain the component. -
(Optional) You can repeat the preceding actions to select multiple components for the same or different operating systems.
-
When you are finished, click Save as Named Profile. If a profile of that name exists you will be asked to confirm that it is to be replaced.
Note:
You cannot replace system-defined profiles.
As components are added to the profile, Profile Contents shows the Component Name, Distribution, and type of action. To remove a component from the list, select the component from Profile Contents list and click Remove from Profile.
The UI will not allow you to select contradicting combination of actions. For example, you cannot mark the same package as both Required and Uninstalled, or request multiple versions of the same component. However, this does not guarantee that the set of actions in the Profile has a valid solution. The UI does not check for dependencies or conflicts, this is handled by the Dependency Resolver on the target when the job is processed.
As stated earlier, profiles cannot be nested or combined. You can import the actions from another profile by selecting the profile and clicking Required. This causes the actions from the profile to be copied into the current profile. Any future edits to the profile will not affect the current profile.
For example, you can import the actions of Profile A and create another profile B. If you edit Profile A, it will not be modified in Profile B.
Editing an OS Update Profile
Check for roles and permission to edit an update profile. You must have edit permission to modify the profiles. You cannot alter the system-defined profiles.
When you change the name of the profile, a new profile is created. The existing profile is not modified for other changes and retained.
-
Select Plan Management from the Navigation pane.
-
Select Update Profiles from the Profiles and Policies tree. The system-defined and use-defined profiles are listed in the center pane.
-
Select a profile from the user-defined profiles list.
-
Click the Edit Profile icon.
-
The Edit OS Update Profile window is displayed.
-
Edit the profile details as required. You can add or remove Components and change profile settings, such as the name, description, or type.
-
Click Save as Named Profile to save the changes made to the profile. If you changed the profile name the system will save the profile under the new name and the old version will be unaffected. If you did not change the profile name, or changed it to match an existing profile, the system will warn you before you overwrite the existing version.
Exporting an OS Update Profile
If you have the Admin role, you can export user-defined profiles one profile at a time. System-defined profiles cannot be exported. The exported profile is in an XML-style format which can be read and copied easily. You can edit the profile with any standard text editor.
To Export an OS Update Profile
-
Select Plan Management section from the Navigation pane.
-
Select Update Profiles from the Profiles and Policies tree. The system-defined and user-defined profiles are listed in the center pane.
-
Select a user-defined profile.
-
Click the Export Profile icon in the center pane. Depending on your browser, you will get a pop-up window from which you can either open the file or save the file to a disk.
-
Click either Open or Save to disk, then click OK.
Importing an OS Update Profile
Once a profile has been exported, you can import it into a different environment. In this release, the profile might not contain any components for distributions which are not activated; attempting to do so will result in an error. (A solution is to manually edit the profile to remove any such entries). Additionally, any profile entries referring to 'NCOs', such as local content, are silently removed during the import process.
To Import an OS Update Profile
-
Select Plan Management section from the Navigation pane.
-
Select Update Profiles from the Profiles and Policies tree.
-
Click on the Import Profile icon in the center pane. An Import OS Update Profile window is displayed.
-
Enter the file name or click Browse to locate the file to be imported.
-
Click Import Profile. If the import is successful, the Edit Profile window is displayed. See Editing an OS Update Profile for more information.
-
Review the profile and make changes, as appropriate.
-
Save the profile to the database.
Note:
If you o not save the profile, it is discarded.
Deleting an OS Update Profile
You can delete profiles that you have created. You cannot delete a system-defined profile or profiles created by other users.
-
Select Plan Management from the Navigation pane.
-
Select Update Profiles from the Profiles and Policies tree. The system-defined and user-defined profiles are listed in the center pane.
-
Select the user-defined profile that you want to delete from the list.
-
Click the Delete Profile icon.
-
Click Yes to confirm the delete action.
Note:
This marks the profile as deleted in the database; it can no longer be accessed through the UI and will not appear in the lists. Completely removing the profile, or recovering a deleted profile, is a task for a database administrator and is beyond the scope of these instructions.Update Policies
Update policies define how an OS update job must be performed. Policies helps to automate the update jobs without user interaction. You can use the policy to specify the update tasks about which you want to be notified.
A policy is a list of actions that are explicitly approved or denied. They can be created by the user in advance of submitting a job; alternatively the question and answer exchange when a job is executed can be saved as a policy for future re-use.
As with profiles, policies can contain actions relating to more than one operating system. There are a number of system policies which can be used to automate the update jobs.
Enterprise Manager Ops Center provides 3 system-defined policies. You can also create policies by setting the action for a selected OS update component.
Policy settings are hierarchical; if there is not a policy setting for a component then the policy for that component's parent applies. For example, it is possible to create a policy that allows the system to install a given component but prohibits installation of certain specific versions of that component.
Note:
The policy only applies to actions that are implicitly generated by the dependency resolver. If a conflict occurs between a profile and policy, the profile overrides the policy.The update policy is not applicable to Windows OS.
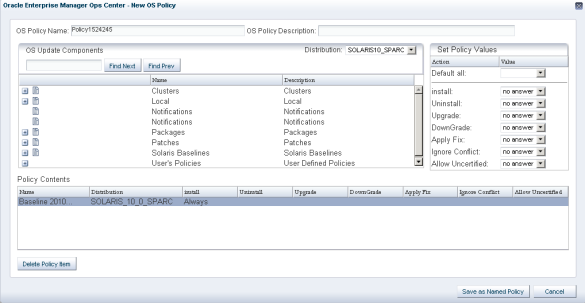
Creating an OS Update Policy
Policies focus on the component level. Depending on the selected distribution, OS Update Components categories may include:
-
Oracle Solaris Baselines
-
Packages or Software
-
Patches
-
Clusters
-
Notifications
There is also a category of User's Policies, which allows existing policy definitions to be merged into the current policy.
You can select a single component within a category, such as the latest Oracle Solaris baseline, or an entire category. You can set the following policy actions for the selected component:
-
Install
-
Uninstall
-
Upgrade
-
Downgrade
-
Apply Fix
-
Ignore Conflict
-
Allow Uncertified
If the selected component is a category or a package group, the setting applies to all the packages in the category or package group. Once you select the component and OS distribution, you can define the policy actions. The Policy Component and Action Settings are described below.
-
Install or Uninstall
-
Ask Me – Pause the job for confirmation before installing or uninstalling the selected component.
-
Yes – Install or uninstall the selected component automatically, as required by solution.
-
No – Find a solution that does not install or uninstall the selected component.
-
-
Upgrade from or Downgrade from
-
Ask Me – Pause the job for confirmation before changing the version of the selected component.
-
Yes – Upgrade or downgrade the selected component automatically, as required by solution.
-
No – Find a solution that does not upgrade or downgrade the selected component.
-
-
Apply Fix
-
Ask Me – Pause the job for confirmation before fixing dependency, security, or bug issues on selected component.
-
Yes – Automatically apply the fix.
-
No – Find a solution that does not apply a fix on the selected component.
-
-
Ignore File Conflict A file conflict will occur if the selected component provides a file that cannot be installed on a system with a file provided by another component that is already installed. If both components are certified, the rules of the knowledge base handle deployment without conflicts. If one or both are local components that are not in the knowledge base, the conflict will cause the job to fail.
Note:
Do not set the Ignore File Conflict setting to Yes unless you know the conflict.-
Ask Me – Pause the job for confirmation, so you see the conflict and decide at run-time whether to ignore it and continue the job, or to fail the job.
-
Yes – The conflict is understood and known to be unimportant. Continue the job without pause.
-
No – Find a solution that does not allow for any file conflicts.
-
-
Allow Uncertified Allow the agent to install an uncertified Object, one that is not officially recognized by the software update service.
-
Ask Me – Pause the job for confirmation before installing the object.
-
Yes – Install the object automatically, as required by the solution.
-
No – Look for a solution that does not depend on the uncertified object.
-
If a policy has the Ask Me action, the job pauses for confirmation before continuing. The user will receive a notification that there is a job waiting for an answer. Click Jobs to view the job status. If a job is paused, the Waiting User Input icon appears in the status column. Click the icon to answer the questions.
This procedure enables you to create an OS policy that you can use in update jobs. All user roles can create an OS Policy. Other users see the policies as read-only and can use or copy your policies, but they cannot edit or delete them.
-
Select Plan Management section from the Navigation pane.
-
Select Update Policies from the Profiles and Policies tree. A list of existing policies is displayed in the Summary tab.
-
Click New Policy in the Actions pane or click New Policy icon in the Summary tab.
The New OS Policy window is displayed.
-
A default policy name is provided. Edit the policy name and add a brief OS Policy Description.
-
Select the distribution from which you want to select a component.
-
Select a category or component. Expand a category to display the available components.
-
Click on the component for which you want to specify policy values
-
Set the policy values for each action. Once an action has been set for a component that component will appear in the Policy Contents area.
-
Repeat for additional components.
-
Click Save as Named Policy. The policy appears in the OS Update Policies Summary page.
Note:
It is important to know that policy value changes apply to the component currently selected in the component tree. To make additional changes to a component, it is necessary to find that component in the tree again. Selecting the entry under Policy Contents has no effect.Editing an OS Update Policy
You can edit the user-defined policies that you have created. You have read-only option for policies created by other users.
-
Select Plan Management section from the Navigation pane.
-
Select Update Policies from the Profiles and Policies tree. A list of policies is displayed in the center pane.
-
Select a policy from the user-defined policies list.
-
Click the Edit Policy icon in the center pane. The Edit OS Policy window is displayed. You can change the name, description, and policy settings.
-
Click Save as Named Policy to save the changes. If you changed the policy name the system will save the policy under the new name and the old version will be unaffected. If you did not change the policy name, or changed it to match an existing policy, the system will warn you before you overwrite the existing version.
Exporting an OS Update Policy
You can export only the user-defined policies, not the system-defined policies. You can export policies one at a time. The exported policy is in an XML-style format which can be read and copied easily. It can also be edited with any standard text editor.
-
Select Plan Management section from the Navigation pane.
-
Select Update Policies from the Profiles and Policies tree.
-
Select a policy from the user-defined policies table in the center pane.
-
Click the Export Policy icon in the center pane. Depending on your browser, you will get a pop-up window from which you can either open the file or save the file to a disk.
-
Click either Open or Save to disk, then click OK.
Importing an OS Update Policy
A policy that has been exported can be imported into a different environment. Unlike Profiles, the policy might contain components for distributions which are not activated; however the UI will be unable to display these correctly. They will appear as "System Policy Item" and the Distribution will appear as "Unknown". You can delete them, but you cannot edit them. Additionally, any policy entries referring to NCO, such as local content, are silently removed during the import process.
-
Select Plan Management section from the Navigation pane.
-
Select Update Policies from Profiles and Policies tree.
-
Click on the Import Policy icon in the center pane. An Import OS Update Policy window is displayed.
-
Enter the file name or click Browse to locate the file to be imported.
-
Click Import Policy.
If the import is successful, the Edit Policy window is displayed. You can review the policy, making changes as appropriate, before saving it to the database.
Note:
If you do not save the policy, it will be discarded.Deleting an OS Update Policy
You can delete the policies that you have created. You cannot delete the policies created by other users.
Note:
This marks the policy as deleted in the database. It can no longer be accessed through the UI and will not appear in the lists. Completely removing the policy, or recovering a deleted policy, is a task for a database administrator and is beyond the scope of these instructions.-
Select Plan Management section from the Navigation pane.
-
Select Update Policies from the Profiles and Policies tree. A list of policies is displayed in the center pane.
-
Select a policy from the user-defined policies list.
-
Click the Delete Policy icon.
-
Click Yes to confirm the delete action.
System Catalogs
A system catalog is a list of OS software components that are installed on a particular managed system. An initial catalog is created after the system is discovered and managed.
After an operating system is available and selected, catalogs can be viewed and modified, and historical catalogs (snapshots of the system) can be created.
Modifying a catalog is an alternate way to run an OS update job to install, uninstall, or upgrade a component. Modifying a catalog does not require an update profile to run the update job. It is a quick way of changing the component configuration of a system.
System catalogs of two managed systems can be compared. You can view the summary of the comparison and also have the option to make the target system the same as the source system.
Catalogs provide the capability to directly manipulate the installed software components on a single operating system or a group of operating systems. Alternatively, a catalog can be saved as a profile, and then an OS update job can be run using this profile.
Creating a Historical Catalog
You can create a historical catalog (snapshots) for an OS. A snapshot of a system is created, then stored with the time stamp and job details after every job is executed on a system. All the snapshots are listed in the catalog list.
When you create a historical catalog, the current state of the selected system is identified and stored as the previous catalog of the system. The saved previous catalog is the most recent system catalog.
Note:
You can create a historical catalog only for the current state of the system.The catalog list always provides the listing of the most recent catalog. The catalog list is populated when the system is updated or a historical catalog is created. The current catalog is identified with a time stamp when you create a historical catalog.
To Create a Historical Catalog
-
Select Assets from the Navigation pane.
-
Select an OS group or a specific OS from the Assets section.
-
Select View/Modify Catalog.
-
If you selected an OS Group, the available systems appear in the center pane. After you select a system, the View/Modify Catalog icon is available above the list of systems.
-
If you select a specific system from the Assets section, the View/Modify Catalog option appears in the Actions pane. The View/Modify Catalog window is displayed.
-
-
In the View/Modify Catalog window, click Create Historical Catalog. The Save Inventory as Snapshot window is displayed.
-
(Optional) You can edit the name of the snapshot to be saved.
-
Click Save Snapshot to save the current state of the system. The saved snapshot will be listed in the Catalog list of View/Modify Catalog window.
You can use the created historical catalog to create a profile and apply to configure the systems.
Viewing and Modifying a Catalog
A catalog is available for each system that you discover and manage in Enterprise Manager Ops Center. A catalog is automatically created when you manage a system.
If you are using dual boot environments for Solaris Live Upgrade, the catalog displays the inventory of the active boot environment of the operating system. To view the catalog of an alternate boot environment (ABE), you must first activate the ABE from the UI, and then wait for the job to finish. The current catalog is updated and contains the ABE catalog information and OS software components. This will also automatically update the catalog of any zones.
-
Select Assets from the Navigation pane.
-
Select an OS from Assets section.
-
Select View/Modify Catalog from the Actions pane. The View/Modify Catalog window is displayed. The current catalog is displayed by default.
-
If a previous catalog is available, select a catalog from the Catalog list. The installed components are displayed.
-
Select Assets from the Navigation pane.
-
Select an OS from the Assets section.
-
Select View/Modify Catalog from the Actions pane. The View/Modify Catalog window is displayed.
-
Select a catalog from the Catalog list. The components that are installed on the system are displayed.
-
Select the component for which you want to modify the action. The available actions are No Action, Required, Uninstall and Upgrade. The actions that are available for the selected component are enabled accordingly.
-
Select the action for the component that you want to modify.
-
Click Launch Modification Job. A New Job wizard is displayed.
-
Complete the job Information as required.
-
Either click Run Now to run the job immediately or click Next to schedule the job later.
Comparing System Catalogs
You can compare two managed systems or two system catalogs for differences in the installed update components. You can also compare the current system catalog and saved snapshots of the same managed system to examine the differences in the components that were installed and uninstalled after executing a job.
Use the Compare Catalogs option to change the software components of a particular operating system to that of the source system.
If you have an alternate boot environment (ABE), you cannot create and compare catalogs until you activate the ABE. By default, only the catalogs of the active boot environment are compared.
To view differences between the target and one of its ABEs, perform the following steps:
-
Create a snapshot of the current BE.
-
Activate the ABE.
-
Wait for the Activate job to finish and for the catalog of the ABE to be reported. Check the notification alerts. When the activation is complete, an OS Update Inventory is Available message appears.
-
Select the snapshot created in Step 1 as the source.
-
Select the new BE (previous ABE) to compare as the target.
To Compare System Catalogs and Copy a Catalog
-
Select an OS from the Assets section in the Navigation pane.
-
Click Compare System Catalogs from the Actions pane. The Compare Catalogs window is displayed. The source system is displayed first.
-
Select a catalog for the source system.
-
Click Select target(s) from inventory. The Select Target window is displayed.
-
Select the target systems.
-
Select one of the following options:
-
Differences Between Systems – Displays the difference between the source and the target systems update components. The difference is displayed in the Compare Catalog window.}
-
Tasks to Make Target Like Source – Creates the list of components that must be installed on the target system. Select Include for the components that you want to install on the target system.
-
-
Click Create job to copy the source to the target(s). The New Update OS Job wizard is displayed.
-
Complete the job information in the wizard.
-
Either click Run Now to run the job immediately or click Next to schedule the job to run later.
Creating an Update Profile From a System Catalog
You can save the catalog of a system as a profile. Using this profile, you can create the systems with the required configuration in your data center.
To Create an Update Profile from a System Catalog
-
Select Assets in the Navigation pane.
-
Select an OS from the Assets section.
-
Choose View/Modify Catalog from the Actions pane. The View/Modify Catalog window is displayed.
-
Select a system catalog to save as a profile. The installed components for the selected catalog are displayed.
-
(Optional) Select the option Profile should include the removal actions to save the exact state of the system. This option ensures that the components that are not installed are selected with Uninstall as the Action in the profile. The removal actions option is selected. The default is no removal actions included in the profile.
-
To save the catalog as a profile, click Convert Catalog to Profile. The Profile window is displayed. You can edit the profile name and description. If necessary, you can add or delete any component, or modify a component action in the profile settings.
-
Click Save as Named Profile to save the profile.
Methods of Updating an OS
When an OS is first discovered and managed, a system catalog of the OS is created. The catalog shows the system update components that are installed on the system. You can create reports to identify the system compliance with the recommended updates. You must update the system with the required and recommended updates for security and other application requirements.
This section describes how to update an OS using different options that are available in Enterprise Manager Ops Center. The following figure describes the different methods available for updating your OSs:
-
Use predefined or custom profiles to update a system or group of systems. This method is mainly used for a Linux OS.
-
Use a system catalog to create a simple update job without creating a profile. This method is used to apply a single patch quickly.
-
Use the compliance reports output to update your OS. This method is used to make your systems compliant with newly released updates.
-
Use compare catalogs to roll a system back to its previous state.
Figure 4-3 Different Methods of Updating an OS
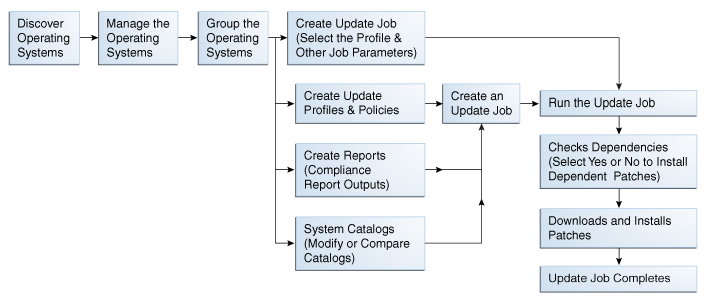
Description of "Figure 4-3 Different Methods of Updating an OS"
In addition to the methods described previously, you can use Live Upgrade and alternate boot environments to update your Solaris OS with a minimum of downtime.
See Updating a Windows OS for updating your Windows OS using Enterprise Manager Ops Center.
Creating an OS Update Job
Creating a new update job enables you to use custom or predefined profiles. This method is typically used for complex update scenarios.
The New Update OS Job option enables you to create customized update jobs. When creating a job, you must define the following job parameters:
-
Name of the update job.
-
Profile – Defines what updates are to be installed, uninstalled, or upgraded on an OS. Select a profile from the list of profiles. Predefined profiles are available, or you can create customized profiles. See UPDATE PROFILES for more information.
-
Policy – Defines how a job is performed and sets the automation level of the job. Select a policy from the list of available policies. You can also create your own policies. See UPDATE POLICIES for more information.
-
Target Settings – Defines whether the target must be different or similar for each task in the job.
-
Run Type – Defines the type of update job:
-
Simulation – Determines the actions and results of a job, and estimates how much time is required to complete the job. A job simulation also indicates whether your policy and profile responses will enable the job to succeed. You can run a simulation with or without downloading patches.
-
Actual Run – Deploys the update job.
-
-
Task Execution Order – Specifies whether the tasks must be run in parallel or sequentially.
-
Task Failure Policy – Specifies what action to take if a task fails.
-
Targets – Select the target operating systems for this job.
Note:
To use an alternate boot environment (ABE) and run ABE pre-action scripts for Solaris OS, see the procedures in Oracle Solaris Live Upgrade.-
Select an OS from the Assets section in the Navigation pane.
-
Click New Update OS Job in the Actions pane. The New Update OS Job wizard is displayed.
-
In the Job Information, specify the job parameters.
-
Enter a name for the update job.
-
Select the Target Setting:
-
Use the same Targets for all tasks in the job
-
Use different Targets for each task in the job
-
-
Select a Run type:
-
Simulation – Enables you to run a job simulation without downloading patches.
-
Download – Click the Download check box to download the patches as part of the job simulation.
-
-
Actual Run – Enables you to download the patches and run the update job.
-
-
Select the Task Execution Order:
-
Sequential
-
Parallel
-
-
Select the Task Failure Policy:
-
Complete as much of job as possible
-
Stop at failure and notify
-
-
To use an alternate boot environment (ABE) and run ABE pre-action scripts, see the procedures in Oracle Solaris Live Upgrade.
-
Click the Add icon to add more tasks to the update job. You can define the profile, policy, and target for each task. If the target setting is a different target for each task in the job, then the new task includes the Select Targets button. Click Select Targets to select the target for the task.
-
To change the profile or policy, click the appropriate table cell for the target to display a drop-down list. Select the profiles and policies from the lists.
Note:
If there is a conflict between a profile and policy, the profile overrides the policy. -
To change the selected target system, select the row and click Edit Targets. The Select Targets window is displayed. Select the targets on which you want to run the update job. You can select multiple targets.
-
Determine how you want to run the job:
-
To schedule the job to run later, click Next.
-
To run the job immediately, click Run Now.
-
-
Select a schedule option.
-
Now – Starts the update job immediately.
-
Start Date – Enables you to define a start date.
-
On a Recurring Schedule – Enables you to create a recurring schedule.
-
-
Click Next to display the Job Summary.
-
Click Finish to run the update job according to the defined configuration and schedule.
Updating an OS by Modifying a System Catalog
A system catalog is a list of OS software components that are installed on a managed system. Catalogs provide the capability to directly manipulate the installed software components on a single operating system or a group of operating systems.
See System Catalogs for more information about managing catalogs.
Updating an OS by modifying a system catalog provides the following advantages:
-
Enables you to create a quick ad hoc job
-
Provides an easy method of applying a single patch, baseline, or package
-
Enables you to update an OS without creating a profile for a one-time job
To Update an OS by Modifying a System Catalog
-
Select Asset from the Navigation pane.
-
Select an OS from the Asset tree.
-
Select View/Modify Catalog from the Actions pane. The View/Modify Catalog window is displayed.
-
Select a catalog from the Catalog list. The components that are installed on the system are displayed.
-
Select the component for which you want to modify the action. The available actions are No Action, Required, Uninstall, and Upgrade. The actions that are available for the selected component are enabled accordingly.
-
Select the action for the component that you want to modify.
-
Click Launch Modification Job. A New Update OS Job wizard is displayed.
-
Complete the job Information as required.
-
Either click Run Now to run the job immediately or click Next to schedule the job to run later.
Updating From an OS Profile
In Enterprise Manager Ops Center, you can create an update job from Update Profiles in the Plan Management section. In the Update Profile section, the New OS Update Job option is available to run an update job.
To Create a Job From a Profile
-
Select Plan Management section in the Navigation pane.
-
Select Update Profiles in the Profiles tree.
-
Select a profile from the predefined profile or user-defined profile list.
-
Click New Update OS Job in the Actions pane. The New Update OS Job wizard is displayed.
-
Enter a name and description for the update job in the Job Information step.
-
Select the run type for the job. It can be either Simulation or Actual Run.
-
Make your selections from the following:
-
Task Execution Order
-
Target Setting
-
Task Failure Policy
-
Boot Environment Type
-
Run ABE Pre-action Script
-
-
Select the profile and policy from the drop-down list under the Profile and Policy columns in the Tasks table.
-
Click the link below the Targets column in the Task table to select the target for the task. The Select Targets window is displayed. Select the target on which you want to run the update job and click Add to Target List. You can select multiple targets.
-
Click Select in the Select Targets window.
-
Click Run Now to run the job immediately or click Next to schedule the job to run later.
Updating From an OS Report Result
In Enterprise Manager Ops Center, you can generate the following compliance reports for an OS from which you can create an OS update job:
-
Baseline Analysis Report
-
Host Compliance Report
-
Incident Compliance Report
-
CVE Compliance Report
-
Profile Report
-
Package Compliance Report
-
Recommended Software Configuration Report
See Firmware and OS Update Reports for information about generating these reports. You can generate these reports for non-compliant components. The report result is displayed with the option to install the patches, packages, updates, and incidents.
The report results are stored in the database associated with the Enterprise Controller. The history of the reports is maintained for analysis purposes.
From the report result, you can initiate a job to install the non-compliant component updates. The New Update OS Job wizard starts, enabling you to enter job information and to schedule the job. The required data for profiles, policies, and targets are automatically pre-populated in the job wizard.
After you submit the job to run the report, the result is displayed under the Report Results.
To Use Report Result to Update an OS
-
Click Reports from the Navigation pane. The saved report templates and the report results are displayed in the content pane under All Reports.
-
In the Report Results section, select the required report and click the View Interactive icon. The interactive result viewer opens the Report Details window. The Report Details lists the targets for which the report was generated.
-
Select a target from the list. The applicable OS updates are listed. The report lists the patch number, required action for the patch and the link to the patch information in the applicable vendor Web site.
-
Select the updates that you want to install and click Make Targets Compliant. The New Update OS job wizard is displayed with defined profiles and targets.
-
Complete the wizard and run the update job.
Updating Zones
Enterprise Manager Ops Center enables you to update the global and non-global zones of your Solaris OS. You can update both the greenfield and brownfield zones. You can also patch zones that are running on a supported configuration. The installation of the patches on the zones depend on the package parameters and the attribute set for the patch commands. This section describes the parameters for installation of the packages and patches. The concepts involved in updating global and non-global zones, and the procedures to update the zones are described in this section.
Installing Packages and Patches on Zones
A patch is a collection of files and directories that replace existing files and directories that are preventing proper execution of the software.
You can install packages and patches on a zone. The patchadd and pkgadd commands operate in the background to install a patch and package respectively. However, the installation of packages on zones also depends on the parameters SUNW_PKG_ALLZONES, SUNW_PKG_HOLLOW, and SUNW_PKG_THISZONE. These parameters control whether a package can be installed on global zones or non-global zones. The actions for the parameters are as follows:
-
SUNW_PKG_ALLZONES – If the value is true, the package is installed on all zones, both global and non-global.
-
SUNW_PKG_HOLLOW – If the value is true, the package information is propagated to the non-global zones, but the package is not installed.
-
SUNW_PKG_THISZONE – If the value is true, the package is installed only in that zone.
Configuring patchadd and pkgadd Commands
In Enterprise Manager Ops Center, the patchadd, pkgadd, patchrm, and pkgrm commands are implemented without the -G switch by default. To install updates or packages only on the current zone, enable the -G switch by editing the .uce.rc file.
Note:
There is auce.rc file and a .uce.rc file. The uce.rc file is the default file and should not be edited. Please ensure that you are editing the .uce.rc file.Editing the .uce.rc File
-
Open the
.uce.rcfile in the/SUNWuce/agent/bindirectory in the managed system. -
Add the following lines to the
.uce.rcfile:( all ) (invisible.__is_patchadd_g_specified, false) ( all ) (invisible.__is_patchremove_g_specified, false) ( all ) ( invisible.__is_pkgadd_g_specified, false)
-
Set the
-Gparameter to true for the action that you want to perform. -
Save and close the file.
-
For this change to take effect, restart the services using the following commands:
svcadm disable -s update-agent svcadm enable -s update-agent
Updating a Global Zone
In Enterprise Manager Ops Center, when a package or patch is installed, the patchadd and pkgadd commands are implemented in the background as shown in the following example:
patchadd <patchid> pkgadd <pkgname>
You can change the way that these commands are implemented by enabling the -G switch. You can enable the -G switch to cause the patch or package to be installed to the target zone only if the package parameter SUNW_PKG_THISZONE is set to true. See Installing Packages and Patches on Zones for information about configuring the patchadd and pkgadd commands on the managed systems.
See the following scenarios when you are updating a global zone. The result for each scenario determines whether the update job will be successful, depending on the package information.
Table 4-1 Updating a Global Zone Scenarios
| SUNW_PKG_ALLZONES | SUNW_PKG_THISZONE | SUNW_PKG_HOLLOW | Impact | Impact with -G Configuration |
|---|---|---|---|---|
|
False |
False |
False |
The package will be installed on the global zone, and all the non-global zones |
The package is installed only on the global zone. |
|
True |
False |
False |
The package is installed on the global zone and all the non-global zones. |
The |
|
True |
False |
True |
The package is installed on the global zone and the package information is made available on all the non-global zones. |
The |
|
False |
True |
False |
The package is installed only on the global zone. |
The package is installed only on the global zone. |
Patches are sets of updates to packages. When you install a patch, the patch is installed on the global zone and the non-global zones, depending on the package parameters as shown in the previous table.
Note:
Use caution while enabling the-G option on a host with sparse zones. Packages that are inherited from the global zone that are not SUNW_ALL_ZONES cannot be patched within a sparse zone.Updating Non-Global Zones
As a zone administrator, you can install packages and patches on non-global zones. The patchadd and pkgadd command must be used without any options. Do not configure the -G switch to the commands while updating the non-global zones.
See the following scenarios when you are updating a non-global zone. The results of each scenario determine whether the update job will be successful, depending on the package information.
Note:
The-G switch does not have any effect on installing packages or patches in a non-global zone.Table 4-2 Updating Non-Global Zones Scenarios
| SUNW_PKG_ALLZONES | SUNW_PKG_THISZONE | SUNW_PKG_HOLLOW | Impact |
|---|---|---|---|
|
False |
False |
False |
The package is installed only on the target non-global zone. |
|
True |
False |
False |
The package installation fails. |
|
True |
False |
True |
The package installation fails. |
|
False |
True |
False |
The package is installed only on the target non-global zone. |
Note:
When the patch is installed only on the non-global zone, ensure that autoboot property is set to true for the zone. Otherwise, single user mode patches will fail to apply as the zone does not come up after the reboot.Patches are sets of packages that must be installed. If any one of the packages has the SUNW_PKG_ALLZONES parameter set to true, then the patch installation fails. For a successful patch installation, ensure that none of the packages have SUNW_PKG_ALLZONES parameter set to true.
Note:
Packages that deliver to read-only inherit directories will not install to sparse root zones. These packages must be installed from the global zone with the-G switch disabled. If a package has the parameter SUNW_PKG_THISZONE=true, it will not appear as installed from the sparse zone and the software might not function correctly. In this case, a whole root zone must be used. Packages with SUNW_PKG_THISZONE=true must not deliver to read-only inherit directories.OS Update Capability
The list of services that are provided by Enterprise Manager Ops Center for the operating systems such as Solaris, Linux, and Windows.
| Service | Solaris | Linux | Windows | Zones | Branded Zones |
|---|---|---|---|---|---|
|
Patch analysis |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Job simulation |
Yes |
Yes |
No |
Yes |
Yes |
|
Job scheduling |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Rollback and recovery |
Yes |
Yes |
No |
NA |
NA |
|
Custom packages |
Yes |
Yes |
No |
Yes |
Yes |
|
Active dependency rules |
Yes |
Yes |
No |
Yes |
Yes |
OS Update Reports
Several predefined OS Update reports are available. The reports enable you to check for new patches and security advisories. You can get a general report, or test a system or installed package for available fixes.
When you create a report, you select the criteria that are relevant to you, such as a list of hosts that have a specific patch or a list of hosts that do not have a specific patch.
The following reports are available for the hosts such as Oracle Solaris and Linux:
-
CVE report
-
Host compliance report
-
Incidence compliance report
-
Package compliance report
-
Service pack compliance report
-
Distribution update report
-
Recommended software configuration report
-
Profile report
-
Change history report
The following reports are exclusive to Oracle Solaris OS:
-
Baseline analysis report
-
Solaris update compliance report
The following reports can be generated for Windows OS:
-
Host compliance report
-
Incidence compliance report
Update Roles and Authorizations
To use the Update feature, you must have the proper permissions, or user role, for the asset.
An Enterprise Manager Ops Center administrator can grant a user the following roles for a group or asset:
-
Admin – To perform administration actions such as grouping
-
Update – To update a system or group of systems
-
Update Sim – To run simulated update jobs
-
Provision – To provision new operating systems
-
Manage – To use management actions, such as rebooting
An Admin can assign a user role for a specific asset, such as the Enterprise Controller, or an asset group. When a user is assigned a group role, the user also has the same permissions to all subgroups.
To update multiple operating systems with a single job, you must use a homogeneous OS group as the target. See Oracle Enterprise Manager Ops Center User's Guide for information about how to create a group and add operating systems to the group. Homogeneous groups contain the same release of an OS.
To update a Linux OS, you must provide your Red Hat or SUSE login credentials. Enterprise Manager Ops Center uses the credentials to log in to the third-party site and download the patches or packages.
To provide or update your My Oracle Support or third-party vendor credentials, see Oracle Enterprise Manager Ops Center Reference Guide for information about editing authentications.
The following tasks are available for an admin:
-
Reports
-
Save, run, and view BAR from Database Report
-
Save and view BAR from Agent Report
-
Run BAR from Agent Report
-
Save, Run and View Compliance Report
-
-
Job Submission
-
Launch Job Wizard from Asset, Group and Profile
-
View Catalog and Catalog Compare
-
Launch Job Wizard from Catalog and Catalog Compare
-
Submit Simulation Job
-
Submit Deploy Job
-
Answer questions
-
Rerun job
-
Launch Copy Job wizard
-
-
Profile and Policy Management
-
Create Profile and Policy
-
Save Profile and Policy from job
-
Edit Profile and Policy
-
Delete Profile and Policy
-
View Profile and Policy
-
View Profile and Policy from job
-
-
Administration
-
Edit Authentications
-
Setup Connection Mode
-
OS Update Library Actions
-
For a non-admin, the following tasks are available:
-
Reports
-
Save, run, and view BAR from Database Report
-
Save and view BAR from Agent Report
-
Run BAR from Agent Report – If you have the Update or Update Sim role for the OS targets
-
Save, Run and View Compliance Report
-
-
Job Submission
-
Launch Job Wizard from Asset, Group and Profile
-
View Catalog and Catalog Compare
-
Launch Job Wizard from Catalog and Catalog Compare
-
Submit Simulation Job – if you have the Update or Update Sim role for the OS targets
-
Submit Deploy Job – if you have the Update role for the OS targets
-
Answer questions – if you have the Update or Update Sim role for the job targets
-
Rerun job – if you have the Update or Update Sim role for the job targets
-
Launch Copy Job wizard
-
-
Profile and Policy Management
-
Edit Profile and Policy – if you have the admin role for profile and policy
-
Delete Profile and Policy – if you have the admin role for profile and policy
-
View Profile and Policy
-
View Profile and Policy from job
-
Note:
You must have root permissions to view system profiles and policies. You cannot view a system defined profile or policy from a job.Updating Clusters
You can provision clusters with an OS and the Oracle Solaris Cluster software. You must create the provisioning profile by importing the cluster profile and editing it to include the post-action script.
See Oracle Enterprise Manager Ops Center Advanced User's Guide for more information about importing a cluster profile.
To provision an OS on an Oracle Solaris Cluster, use the procedure described in Creating an OS Update Job with the cluster provisioning profile and select the cluster as the target of the update job.