The Login Process
Before you can log in to the Trusted Solaris environment, your system administrator and security administrator must set up a user account for you. The account gives you permission to use some of the computer facilities and contains identifying information, such as the username assigned to you and your user ID (UID). The username in conjunction with your password lets you log into the system. The user ID identifies all of your transactions as well as the files and directories that you own.
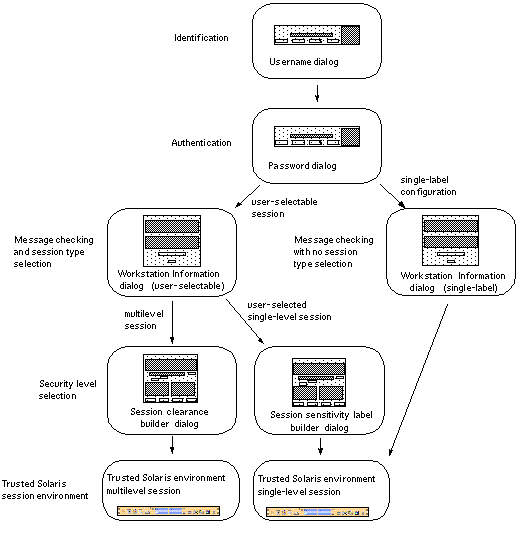
An overview of the login process is shown in Figure 2-1. The process is described in more detail in the material following the overview figure. The steps in the process include:
-
Identification - Typing your username in the Username dialog box.
-
Authentication - Typing your password in the Password dialog box.
Successful completion of identification and authentication confirms your right to use the system.
-
Message checking and session type selection - The Workstation Information dialog box displays the message of the day, provides account access information (so that you can check for any possible security breaches), and asks you to specify the type of session: single-level or multi-level.
Note -Your account may be configured such that you always operate at the same label (a single-label configuration). If this is the case, you will not be able to select the type of session in the Workstation Information dialog box or set a security level.
-
Security level selection - Setting the highest security level at which you intend to operate while in your session.
Figure 2-1 Trusted Solaris Environment Login Process
- © 2010, Oracle Corporation and/or its affiliates
