Chapter 2 Trusted Extensions Administration Tools
This chapter describes the tools that are available in Solaris Trusted Extensions, the location of the tools, and the databases on which the tools operate.
Administration Tools for Trusted Extensions
Administration on a system that is configured with Trusted Extensions uses many of the same tools that are available in the Solaris OS. Trusted Extensions offers security-enhanced tools as well. Administration tools are available only to roles in a role workspace.
Within a role workspace, you can access commands, actions, applications, and scripts that are trusted. The following table summarizes these administrative tools.
Table 2–1 Trusted Extensions Administrative Tools|
Tool |
Description |
For More Information |
|---|---|---|
|
Provides a menu-based wizard for creating, installing, initializing, and booting zones. This script replaces the Trusted CDE actions that manage zones. The script also provides menu items for networking options, name services options, and for clienting the global zone to an existing LDAP server. txzonemgr uses the zenity command. |
See Creating Labeled Zones in Oracle Solaris Trusted Extensions Configuration Guide See also the zenity(1) man page. |
|
|
In Trusted CDE, actions in the Trusted_Extensions folder in the Application Manager folder |
Used to edit local files that the Solaris Management Console does not manage, such as /etc/system. Some actions run scripts, such as the Install Zone action. |
See Trusted CDE Actions and How to Start CDE Administrative Actions in Trusted Extensions. |
|
Used to administer the label ranges of devices, and to allocate or deallocate devices. |
See Device Allocation Manager and Handling Devices in Trusted Extensions (Task Map). |
|
|
Solaris Management Console |
Used to configure users, roles, rights, hosts, zones, and networks. This tool can update local files or LDAP databases. This tool can also launch the dtappsession legacy application. |
For basic functionality, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration. For information that is specific to Trusted Extensions, see Solaris Management Console Tools. |
|
Solaris Management Console commands, such as smuser and smtnzonecfg |
Is the command-line interface for the Solaris Management Console. |
For a list, see Table 2–4. |
|
Label Builder |
Is also a user tool. Appears when a program requires you to choose a label. |
For an example, see How to Modify a User's Label Range in the Solaris Management Console. |
|
Trusted Extensions commands |
Used to perform tasks that are not covered by Solaris Management Console tools or CDE actions. |
For the list of administrative commands, see Table 2–5. |
txzonemgr Script
Starting in the Solaris 10 5/08 release, the txzonemgr script is used to configure labeled zones. This zenity(1) script displays a dialog box with the title Labeled Zone Manager. This GUI presents a dynamically-determined menu that displays only valid choices for the current configuration status of a labeled zone. For instance, if a zone is already labeled, the Label menu item is not displayed.
Trusted CDE Actions
The following tables list the CDE actions that roles in Trusted Extensions can run. These trusted CDE actions are available from the Trusted_Extensions folder. The Trusted_Extensions folder is available from the Application Manager folder on the CDE desktop.
Table 2–2 Administrative Actions in Trusted CDE, Their Purpose, and Associated Rights Profiles|
Action Name |
Purpose of Action |
Default Rights Profile |
|---|---|---|
|
Creates devices by adding entries to device databases. See add_allocatable(1M). |
Device Security |
|
|
Edits the specified file. See How to Edit Administrative Files in Trusted Extensions. |
Object Access Management |
|
|
Edits the audit_class file. See audit_class(4). |
Audit Control |
|
|
Edits the audit_control file. See audit_control(4). |
Audit Control |
|
|
Edits the audit_event file. See audit_event(4). |
Audit Control |
|
|
Edits the audit_startup.sh script. See audit_startup(1M). |
Audit Control |
|
|
Runs the chk_encodings command on specified encodings file. See chk_encodings(1M). |
Object Label Management |
|
|
Runs the tnchkdb command on tnrhdb, tnrhtp, and tnzonecfg databases. See tnchkdb(1M). |
Network Management |
|
|
Edits /usr/dt/config/sel_config file. See sel_config(4). |
Object Label Management |
|
|
Makes the global zone an LDAP client of an existing LDAP directory service. |
Information Security |
|
|
Edits the specified label_encodings file and runs the chk_encodings command. See chk_encodings(1M). |
Object Label Management |
|
|
Edits the nsswitch.conf file. See nsswitch.conf(4). |
Network Management |
|
|
Edits the resolv.conf file. See resolv.conf(4). |
Network Management |
|
|
Edits the /etc/motd file. At login, the contents of this file display in the Last Login dialog box. |
Network Management |
|
|
Network Management |
||
|
Edits the dfstab file. Does not run the share command. See dfstab(4). |
File System Management |
The following actions are used by the initial setup team during zone creation. Some of these actions can be used for maintenance and troubleshooting.
Table 2–3 Installation Actions in Trusted CDE, Their Purpose, and Associated Rights Profiles
Device Allocation Manager
A device is either a physical peripheral that is connected to a computer or a software-simulated device called a pseudo-device. Because devices provide a means for the import and export of data to and from a system, devices must be controlled to properly protect the data. Trusted Extensions uses device allocation and device label ranges to control data flowing through devices.
Examples of devices that have label ranges are frame buffers, tape drives, diskette and CD-ROM drives, printers, and USB devices.
Users allocate devices through the Device Allocation Manager. The Device Allocation Manager mounts the device, runs a clean script to prepare the device, and performs the allocation. When finished, the user deallocates the device through the Device Allocation Manager, which runs another clean script, and unmounts and deallocates the device.
Figure 2–1 Device Allocation Manager Icon in Trusted CDE
You can manage devices by using the Device Administration tool from the Device Allocation Manager. Regular users cannot access the Device Administration tool.
Note –
In Solaris Trusted Extensions (JDS), this GUI is named Device Manager, and the Device Administration button is named Administration.
Figure 2–2 Device Allocation Manager GUI

For more information about device protection in Trusted Extensions, see Chapter 17, Managing Devices for Trusted Extensions (Tasks).
Solaris Management Console Tools
The Solaris Management Console provides access to toolboxes of GUI-based administration tools. These tools enable you to edit items in various configuration databases. In Trusted Extensions, the Solaris Management Console is the administrative interface for users, roles, and the trusted network databases.
Trusted Extensions extends the Solaris Management Console:
-
Trusted Extensions modifies the Solaris Management Console Users tool set. For an introduction to the tool set, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Trusted Extensions adds the Security Templates tool and the Trusted Network Zones tool to the Computers and Networks tool set.
Solaris Management Console tools are collected into toolboxes according to scope and security policy. To administer Trusted Extensions, Trusted Extensions provides toolboxes whose Policy=TSOL. You can access tools according to scope, that is, according to naming service. The available scopes are local host and LDAP.
The Solaris Management Console is shown in the following figure. A Scope=Files Trusted Extensions toolbox is loaded, and the Users tool set is open.
Figure 2–3 Typical Trusted Extensions Toolbox in the Solaris Management Console
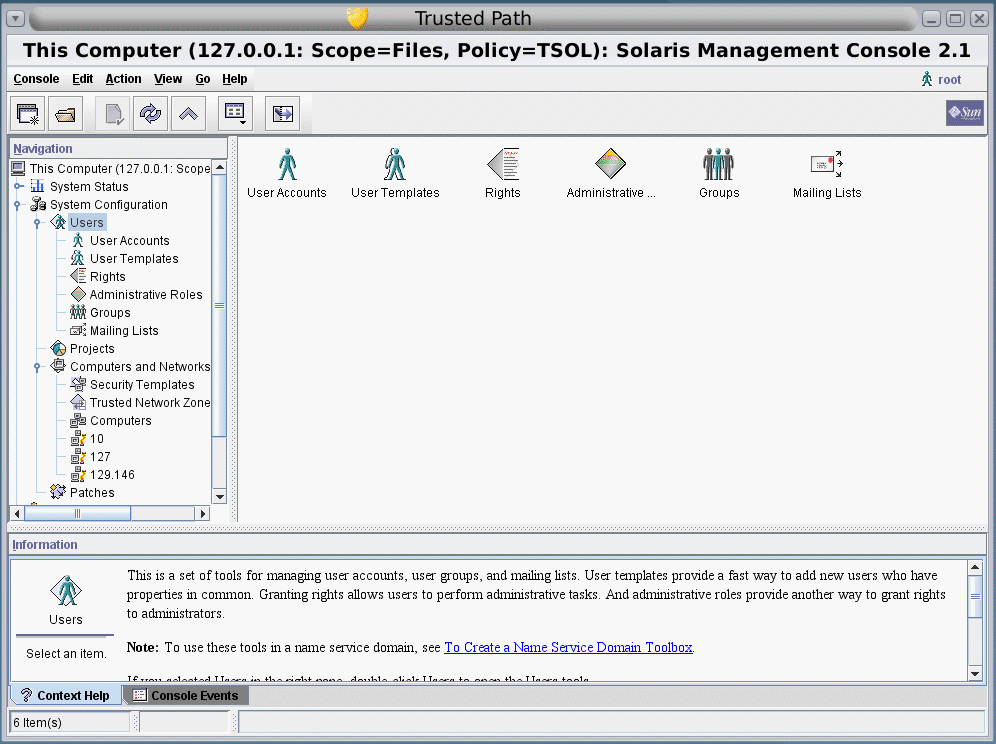
Trusted Extensions Tools in the Solaris Management Console
Trusted Extensions adds configurable security attributes to three tools:
-
User Accounts tool – Is the administrative interface to change a user's label, change a user's view of labels, and to control account usage.
-
Administrative Roles tool – Is the administrative interface to change a role's label range and screen-locking behavior when idle.
-
Rights tool – Includes CDE actions that can be assigned to rights profiles. Security attributes can be assigned to these actions.
Trusted Extensions adds two tools to the Computers and Networks tool set:
-
Security Templates tool – Is the administrative interface for managing the label aspects of hosts and networks. This tool modifies the tnrhtp and tnrhdb databases, enforces syntactic accuracy, and updates the kernel with the changes.
-
Trusted Network Zones tool – Is the administrative interface for managing the label aspects of zones. This tool modifies the tnzonecfg database, enforces syntactic accuracy, and updates the kernel with the changes.
Figure 2–4 shows the Files toolbox with the Users tool set highlighted. The Trusted Extensions tools appear below the Computers and Networks tool set.
Figure 2–4 Computers and Networks Tool Set in the Solaris Management Console

Security Templates Tool
A security template describes a set of security attributes that can be assigned to a group of hosts. The Security Templates tool enables you to conveniently assign a specific combination of security attributes to a group of hosts. These attributes control how data is packaged, transmitted, and interpreted. Hosts that are assigned to a template have identical security settings.
The hosts are defined in the Computers tool. The security attributes of the hosts are assigned in the Security Templates tool. The Modify Template dialog box contains two tabs:
-
General tab – Describes the template. Includes its name, host type, default label, domain of interpretation (DOI), accreditation range, and set of discrete sensitivity labels.
-
Hosts Assigned to Template tab – Lists all the hosts on the network that you have assigned to this template.
Trusted networking and security templates are explained in more detail in Chapter 12, Trusted Networking (Overview).
Trusted Network Zones Tool
The Trusted Network Zones tool identifies the zones on your system. Initially, the global zone is listed. When you add zones and their labels, the zone names display in the pane. Zone creation usually occurs during system configuration. Label assignment, multilevel port configuration, and label policy is configured in this tool. For details, see Chapter 10, Managing Zones in Trusted Extensions (Tasks).
Client-Server Communication With the Solaris Management Console
Typically, a Solaris Management Console client administers systems remotely. On a network that uses LDAP as a naming service, a Solaris Management Console client connects to the Solaris Management Console server that runs on the LDAP server. The following figure shows this configuration.
Figure 2–5 Solaris Management Console Client Using an LDAP Server to Administer the Network

Figure 2–6 shows a network that is not configured with an LDAP server. The administrator configured each remote system with a Solaris Management Console server.
Figure 2–6 Solaris Management Console Client Administering Individual Remote Systems on a Network

Solaris Management Console Documentation
The main source of documentation for the Solaris Management Console is its online help. Context-sensitive help is tied to the currently selected feature and is displayed in the information pane. Expanded help topics are available from the Help menu or by clicking links in the context-sensitive help. Further information is provided in Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration. Also see Using the Solaris Management Tools With RBAC (Task Map) in System Administration Guide: Basic Administration.
Label Builder in Trusted Extensions
The label builder GUI enforces your choice of a valid label or clearance when a program requires you to assign a label. For example, a label builder appears during login (see Chapter 2, Logging In to Trusted Extensions (Tasks), in Oracle Solaris Trusted Extensions User’s Guide). The label builder also appears when you change the label of a workspace, or when you assign a label to a user, zone, or network interface in the Solaris Management Console. The following label builder appears when you assign a label range to a new device.

In the label builder, component names in the Classification column correspond to the CLASSIFICATIONS section in the label_encodings file. The component names in the Sensitivity column correspond to the WORDS section in the label_encodings file.
Command Line Tools in Trusted Extensions
Commands that are unique to Trusted Extensions are contained in the Solaris Trusted Extensions Reference Manual. The Solaris commands that Trusted Extensions modifies are contained in the Solaris Reference Manual. The man command finds all the commands.
The following table lists commands that are unique to Trusted Extensions. The commands are listed in man page format.
Table 2–4 User and Administrative Trusted Extensions Commands|
Man Page |
Trusted Extensions Modification |
For More Information |
|---|---|---|
|
Enables a device to be allocated by adding the device to device allocation databases. By default, removable devices are allocatable. | ||
|
Translates a label into hexadecimal format. | ||
|
Checks the integrity of the label_encodings file. |
How to Debug a label_encodings File in Oracle Solaris Trusted Extensions Label Administration |
|
|
Opens a remote Trusted CDE session by using the Application Manager. |
Chapter 8, Remote Administration in Trusted Extensions (Tasks) |
|
|
Displays the label of the selected files or directories. | ||
|
Displays the full pathname of a specific zone. |
Acquiring a Sensitivity Label in Oracle Solaris Trusted Extensions Developer’s Guide |
|
|
Translates a hexadecimal label into its readable equivalent. | ||
|
Displays the label of the current process. |
See the man page. |
|
|
Prevents allocation of a device by removing its entry from device allocation databases. | ||
|
Relabels the selected item. Requires the solaris.label.file.downgrade or solaris.label.file.upgrade authorization. These authorizations are in the Object Label Management rights profile. |
For the equivalent GUI procedure, see How to Move Files Between Labels in Trusted CDE in Oracle Solaris Trusted Extensions User’s Guide. |
|
|
Manages entries in the tnrhdb database locally or in a naming service database. |
For equivalent procedures that use the Solaris Management Console, see Configuring Trusted Network Databases (Task Map). |
|
|
Manages entries in the tnrhtp database locally or in a naming service database. |
See the man page. |
|
|
Manages entries in the local tnzonecfg database. |
For an equivalent procedure that uses the Solaris Management Console, see How to Create a Multilevel Port for a Zone. |
|
|
Checks the integrity of the tnrhdb and tnrhtp databases. | ||
|
Caches network information in the kernel. |
How to Synchronize the Kernel Cache With Trusted Network Databases |
|
|
Executes the trusted network daemon. |
How to Synchronize the Kernel Cache With Trusted Network Databases |
|
|
Displays kernel-level network information and statistics. |
How to Compare Trusted Network Database Information With the Kernel Cache. |
|
|
How to Configure Startup Files for Users in Trusted Extensions |
The following table lists Solaris commands that are modified or extended by Trusted Extensions. The commands are listed in man page format.
Table 2–5 User and Administrative Commands That Trusted Extensions Modifies|
Man Page |
Purpose of Command |
For More Information |
|---|---|---|
|
Adds options to clean the allocated device, and to allocate a device to a specific zone. In Trusted Extensions, regular users do not use this command. |
How to Allocate a Device in Trusted Extensions in Oracle Solaris Trusted Extensions User’s Guide |
|
|
Adds options to clean the device, and to deallocate a device from a specific zone. In Trusted Extensions, regular users do not use this command. |
How to Allocate a Device in Trusted Extensions in Oracle Solaris Trusted Extensions User’s Guide |
|
|
Adds the -a option to display device attributes, such as authorizations and labels. Adds the -d option to display the default attributes of an allocated device type. Adds the -z option to display available devices that can be allocated to a labeled zone. |
See the man page. |
|
|
Adds the -T option to archive and extract files and directories that are labeled. |
How to Back Up Files in Trusted Extensions and How to Restore Files in Trusted Extensions |
|
|
Adds the windata_down and windata_up audit policy options. |
How to Configure Audit Policy in System Administration Guide: Security Services |
|
|
Adds the -l option to select audit records by label. |
How to Select Audit Events From the Audit Trail in System Administration Guide: Security Services |
|
|
Modifies the names and contents of auto_home maps to account for zone names and zone visibility from higher labels. | ||
|
Adds the all-zones option to make an interface available to every zone on the system. | ||
|
Adds the -R option to display extended security attributes for sockets and routing table entries. | ||
|
Adds the -secattr option to display the security attributes of the route: cipso, doi, max_sl, and min_sl. |
Remote Administration in Trusted Extensions
You can remotely administer a system that is configured with Trusted Extensions by using the ssh command, the dtappsession program, or the Solaris Management Console. If site security policy permits, you can configure a Trusted Extensions host to enable login from a non-Trusted Extensions host, although this configuration is less secure. For more information, see Chapter 8, Remote Administration in Trusted Extensions (Tasks).
- © 2010, Oracle Corporation and/or its affiliates
