1 About the Connector
Oracle Identity Manager automates access rights management, and the security of resources to various target systems. Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with target applications. This guide discusses the connector that enables you to use PeopleSoft Campus as an authoritative (trusted) source of identity information for Oracle Identity Manager.
Note:
In this guide, PeopleSoft Campus has been referred to as the target system.
In the identity reconciliation (trusted source) configuration of the connector, persons are created or modified only on the target system and information about these persons is reconciled into Oracle Identity Manager.
This chapter contains the following sections:
1.1 Certified Components
Table 1-1 lists the components certified for use with the connector.
Table 1-1 Certified Components
| Item | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Governance or Oracle Identity Manager:
|
|
Target systems |
The target system can be any one of the following:
|
|
Connector Server |
11.1.2.1.0 |
|
Connector Server JDK |
JDK 1.6 or later, or JRockit 1.6 or later |
|
Other software |
You must ensure that the following components are installed and configured in the target system environment:
The following standard PeopleSoft messages are available:
|
1.2 Connector Architecture
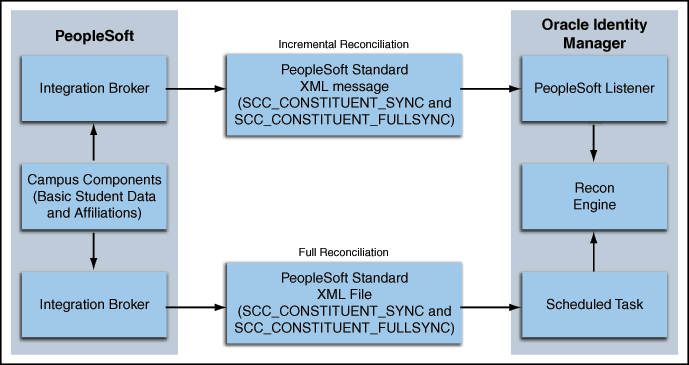
Figure 1-1 shows the architecture of the connector.
The target system is configured as a trusted source of identity data for Oracle Identity Manager. In other words, identity data that is created and updated on the target system is fetched into Oracle Identity Manager and used to create and update OIM Users.
The connector reconciles basic student (person) data and affiliations into Oracle Identity Manager. Basic student data is used in Oracle Identity Manager to create the necessary identities. Affiliations are used to define access policies. Student academic program data is not reconciled into Oracle Identity Manager.
Figure 1-2 shows how data is stored in Oracle Identity Manager.
Figure 1-2 Storing Data in Oracle Identity Manager
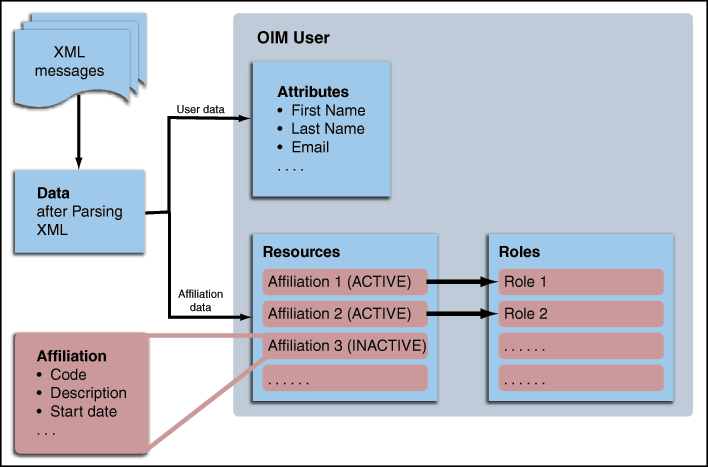
Description of "Figure 1-2 Storing Data in Oracle Identity Manager"
The data is obtained after parsing the XML messages (which can be SCC_CONSTITUENT_FULLSYNC or SCC_CONSTITUENT_SYNC messages) received from the target system. This data contains both the user data (such as First Name and Email) and the affiliation data (such as Affiliation Code and Affiliation Start Date).
The user data is stored in the OIM User form. The affiliation data goes into the Affiliation resource form.
In OIM, the affiliations are modeled as resources. The affiliation resource form has the following fields:
-
Affiliation Code
-
Affiliation Status
-
Affiliation Description
-
Affiliation Start Date
-
Affiliation End Date
-
Institution
Based on the values of the Affiliation Status and Affiliation Start Date fields, the affiliation resource is in Enabled or Disabled state. If the Affiliation Status is Active and the current date lies between Affiliation Start Date and Affiliation End Date, then the resource is in Enabled state. Otherwise, the resource is in Disabled state.
The roles are created in Oracle Identity Manager corresponding to each unique affiliation. For more information about the roles, see Seeding Roles into Oracle Identity Manager. For each enabled affiliation, the corresponding role is assigned to the user. This enables the use of access policies based on the type of affiliations that the user has.
1.3 Medium of Data Interchange
Standard PeopleSoft XML files and messages are the medium of data interchange between PeopleSoft Campus and Oracle Identity Manager. The method by which person data is sent to Oracle Identity Manager depends on the type of reconciliation that you configure. It is listed as follows:
1.3.1 Full Reconciliation
Note:
To reconcile all existing target system records into Oracle Identity Manager, you must run full reconciliation the first time you perform a reconciliation run after deploying the connector. This is to ensure that the target system and Oracle Identity Manager contain the same data.
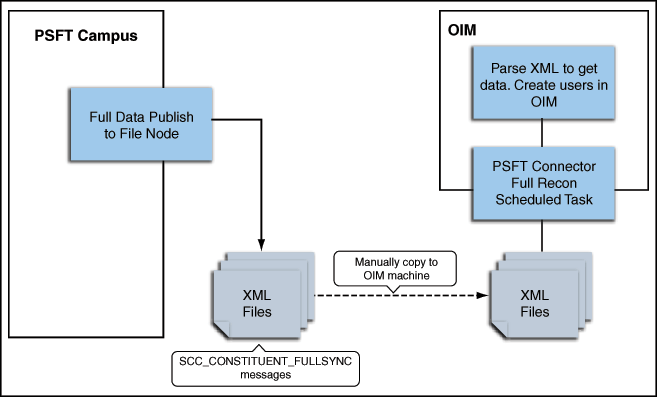
PeopleSoft uses its standard message format SCC_CONSTITUENT_FULLSYNC to send person data to external applications such as Oracle Identity Manager. Full reconciliation fetches all person records from the target system to reconcile records within Oracle Identity Manager. Full reconciliation within Oracle Identity Manager is implemented using the SCC_CONSTITUENT_FULLSYNC XML files that PeopleSoft generates. See Support for Standard PeopleSoft Messages for more information about these messages.
Figure 1-3 shows full reconciliation between PeopleSoft Campus and Oracle Identity Manager.
Full reconciliation involves the following steps:
See Performing Full Reconciliation for the procedure to perform full reconciliation.
-
The PeopleSoft Integration Broker populates the XML files for the SCC_CONSTITUENT_FULLSYNC messages with all the person data, such as biographical information and student information.
-
Copy these XML files to a directory on the Oracle Identity Manager host computer.
-
Configure the PeopleSoft Campus Trusted Full Reconciliation scheduled task. The XML files are read by this scheduled task to generate reconciliation events.
1.3.2 Incremental Reconciliation
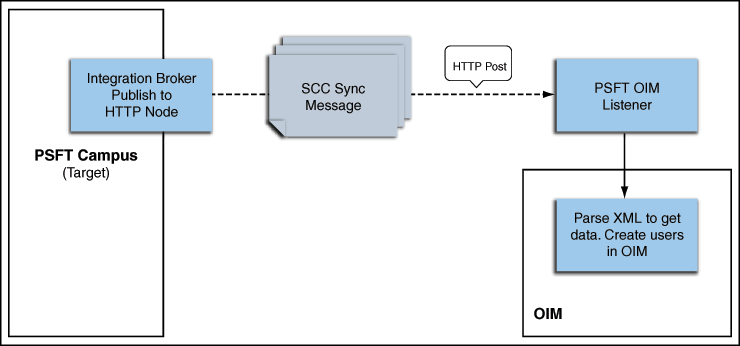
Incremental reconciliation involves real-time reconciliation of newly created or modified person data. You use incremental reconciliation to reconcile individual data changes after an initial, full reconciliation run has been performed. SCC_CONSTITUENT_SYNC is standard PeopleSoft message to initiate incremental reconciliation. See Support for Standard PeopleSoft Messages for details. These messages are used to send specific person data for each transaction on the target system that involves addition or modification of person information. Incremental reconciliation is configured using PeopleSoft application messaging.
Figure 1-4 shows incremental reconciliation between PeopleSoft Campus and Oracle Identity Manager.
Incremental reconciliation involves the following steps:
Performing Incremental Reconciliation describes the procedure to configure incremental reconciliation.
-
When person data is added or updated in the target system, a PeopleCode event is generated.
-
The PeopleCode event generates an XML message, SCC_CONSTITUENT_SYNC, containing the modified person data and sends it in real time to the PeopleSoft listener over HTTP. The PeopleSoft listener is a Web application that is deployed on an Oracle Identity Manager host computer. If SSL is configured, then the message is sent to the PeopleSoft listener over HTTPS.
-
The PeopleSoft listener parses the XML message and creates a reconciliation event in Oracle Identity Manager.
Note:
During connector deployment, the PeopleSoft listener is deployed as an EAR file.
1.4 Features of the Connector
The following are the features of the connector:
1.4.1 Dedicated Support for Trusted Source Reconciliation
The connector provides all the features required for setting up PeopleSoft Campus as a trusted (authoritative) source of identity data for Oracle Identity Manager. Oracle Identity Manager uses this message for incremental reconciliation. In other words, the connector does not support provisioning operations and target resource reconciliation with PeopleSoft Campus.
1.4.2 Seeding Roles into Oracle Identity Manager
The connector supports seeding roles into Oracle Identity Manager corresponding to each unique affiliation in PeopleSoft Campus. This is done so that when a particular affiliation (a resource in Oracle Identity Manager) is assigned to a user, then if the affiliation is active, the corresponding role is assigned to the user.You can write access policies on those roles, which are access policies effectively based on affiliations such as student, prospect, employee, alumni, and so on.There is a separate scheduled task, called PeopleSoft Campus Role Creation, for seeding the roles into Oracle Identity Manager. You must run this task before using the connector for reconciliation. See Seeding Roles into Oracle Identity Manager for more information.
Figure 1-5 shows seeding PeopleSoft Campus roles in Oracle Identity Manager.
Figure 1-5 Seeding Roles in Oracle Identity Manager
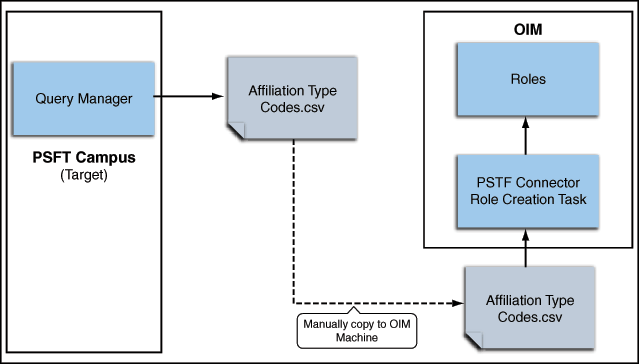
Description of "Figure 1-5 Seeding Roles in Oracle Identity Manager"
1.4.3 Full and Incremental Reconciliation
The connector supports reconciliation in two ways:
In a full reconciliation run, all records are fetched from the target system to Oracle Identity Manager in the form of XML files. In incremental reconciliation, records that are added or modified are directly sent to the listener deployed on the Oracle Identity Manager host computer. The listener parses the records and sends reconciliation events to Oracle Identity Manager.
1.4.4 Reconciliation of Effective-Dated Lifecycle Events
On the target system, you can use the effective-dated feature to assign a future date to changes that you want to make to a person account.
The connector can distinguish between hire events and other events in the lifecycle of a person record on the target system. These events may be either current-dated or future-dated (in other words, effective-dated). A current-dated event is one in which the date of the event is prior to or same as the current date. A future-dated event is one in which the date the event will take effect is set in the future. For example, if the current date is 30-Jan-09 and if the date set for an event is 15-Feb-09, then the event is future-dated. During reconciliation, the manner in which an event is processed depends on the type of the event.
PeopleSoft uses two standard messages to reconcile a record. These are the SCC_CONSTITUENT_SYNC messages. See Support for Standard PeopleSoft Messages for more information about these messages.
You run the SCC_CONSTITUENT_SYNC message to create an OIM User. The default status of an OIM User is Active. See the Employee Status Code Key in the lookup definition described in Lookup.PSFT.Message.SccConstituentFullSync.Configuration.
Note:
In the context of the Effective Date feature, records for a particular person on the target system can be categorized into the following types:
-
Current: The record with an effective date that is closest to or same as, but not greater than, the system date. There can be only one current record
-
History: Records with dates that are earlier than that of the current-dated record
-
Future: Records that have effective dates later than the system date
1.4.5 Support for Standard PeopleSoft Messages
PeopleSoft provides standard messages to send biographical data (Campus ID, Email ID, First Name, Last Name, Home Phone, User ID, and Start Date) and student-related data to external applications, such as Oracle Identity Manager. These messages also contain affiliation information (Affiliation Code, Affiliation Status, Affiliation Description, Affiliation Start Date, Affiliation End Date, and Institution). Affiliations are defined as the relationship between and an individual and an institution, such as STUDENT, PROSPECT, and so on. The connector uses the following standard PeopleSoft messages that are delivered as part of PeopleSoft Campus installation to achieve full reconciliation and incremental reconciliation:
-
SCC_CONSTITUENT_FULLSYNC
During full reconciliation, these messages are sent to Oracle Identity Manager.
-
SCC_CONSTITUENT_SYNC
This message contains the information about a particular person. This includes the information that is added or modified. During incremental reconciliation, these messages are sent to Oracle Identity Manager.
Note:
It is only if a person is added in PeopleSoft that the triggering of SCC_CONSTITUENT_SYNC creates an OIM User. But, if an OIM User has been created during full reconciliation, then the SCC_CONSTITUENT_SYNC message contains modifications to personal data.
1.4.6 Support for Resending Messages That Are Not Processed
Standard messages provided by PeopleSoft are asynchronous. In other words, if a message is not delivered successfully, then the PeopleSoft Integration Broker marks that message as not delivered. The message can then be resent manually.
If the connector is not able to process a message successfully, then it sends an error code and PeopleSoft Integration Broker marks that message as Failed. A message marked as Failed can be resent to the listener. See Resending Messages That Are Not Received by the PeopleSoft Listener for details.
See Also:
Resubmitting and Canceling Service Operations for Processing topic in the PeopleBook Enterprise PeopleTools 8.49 PeopleBook: PeopleSoft Integration Broker available on Oracle Technology Network:
http://download.oracle.com/docs/cd/E13292_01/pt849pbr0/eng/psbooks/tibr/book.htm
1.4.7 Validation and Transformation of Person Data
You can configure validation of person data that is brought into Oracle Identity Manager during reconciliation. In addition, you can configure transformation of person data that is brought into Oracle Identity Manager during reconciliation.
-
Configuring Validation of Data During Reconciliation provides information about setting up the validation feature.
-
Configuring Transformation of Data During Reconciliation provides information about setting up the transformation feature.
1.4.8 Target Authentication
Target authentication is done to validate whether Oracle Identity Manager should accept messages from the target system or not. It is done by passing the name of the IT resource in the Integration Broker node. You must ensure that the correct value of the IT resource name is specified in the node. See Configuring PeopleSoft Integration Broker for setting up the node. In addition, the flag IsActive is used to verify whether the IT Resource is active or not. The value of this flag is Yes, by default. When this value is Yes, target authentication is carried out. Target authentication fails if it is set to No.
1.4.9 Support for Specifying Persons to Be Excluded from Reconciliation Operation
You can specify a list of persons who must be excluded from all reconciliation operations. Persons whose User IDs you specify in the exclusion list are not affected by the reconciliation operation. See Lookup.PSFT.Campus.ExclusionList for more information.
1.5 Connector Objects Used During Reconciliation
Trusted source reconciliation involves reconciling data of newly created or modified accounts on the target system into Oracle Identity Manager and adding or updating OIM Users.
See Also:
Reconciliation Metadata in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for conceptual information about trusted source reconciliation.
This section discusses the following topics:
1.5.1 Reconciliation Rules
See Also:
Reconciliation Engine in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Manager for generic information about reconciliation matching and action rules
The following sections provide information about the reconciliation rules for this connector:
1.5.1.1 Overview of the Reconciliation Rule
The following are the process-matching rules:
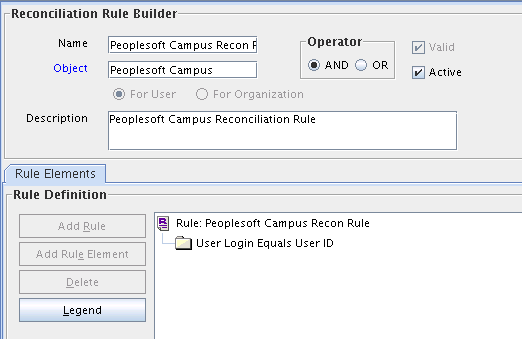
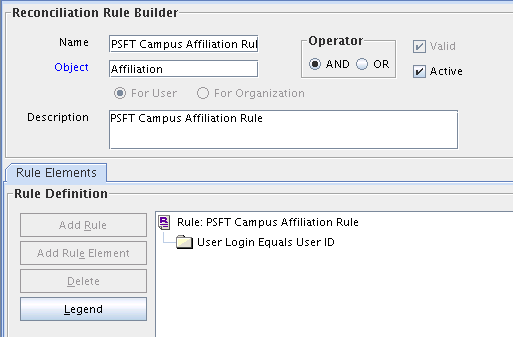
Rule Name: PeopleSoft Campus Reconciliation Rule
Rule Name: PSFT Campus Affiliation Rule
Rule Element: User Login Equals User ID
In this rule:
-
User Login represents the User ID field on the OIM User form.
-
User ID represents the Employee ID field of the employee on the target system.
For trusted source reconciliation, the User ID field of the OIM User form is matched against the Employee ID field on the target system. These are the key fields in Oracle Identity Manager and the target system, respectively.
1.5.2 Reconciliation Action Rules
Application of the matching rule on reconciliation events would result in one of multiple possible outcomes. The action rules for reconciliation define the actions to be taken for these outcomes.
Note:
For any rule condition that is not predefined for this connector, no action is performed and no error message is logged.
The following sections provide information about the reconciliation action rules for this connector:
1.5.2.1 Overview of the Reconciliation Action Rules
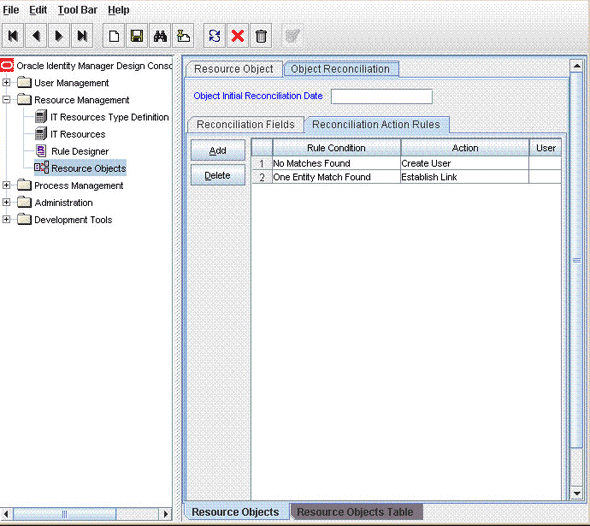
Table 1-2 lists the reconciliation action rules for this connector:
Table 1-2 Action Rules for Trusted Source Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Create User |
|
One Entity Match Found |
Establish Link |
1.5.3 Predefined Lookup Definitions
The predefined lookup definitions can be categorized as follows:
1.5.3.1 Lookup.PSFT.Campus.Configuration
The Lookup.PSFT.Campus.Configuration lookup definition is used to store configuration information that is used by the connector. See Configuring the IT Resource for more information about the entries in this lookup definition.
The Lookup.PSFT.Campus.Configuration lookup definition has the following entries:
| Code Key | Decode | Description |
|---|---|---|
|
Campus Resource Exclusion List Lookup |
Lookup.PSFT.Campus.ExclusionList |
Name of the Resource Exclusion lookup for PeopleSoft Campus See Lookup.PSFT.Campus.ExclusionList for more information about this lookup definition. |
|
Ignore Root Audit Action |
No |
Use this value if the Root PSCAMA audit action is required to be considered while parsing the XML message. Enter Enter |
|
SCC_CONSTITUENT_FULLSYNC |
Lookup.PSFT.Message.SccConstituentFullSync.Configuration |
Name of the lookup definition for SCC_CONSTITUENT_FULLSYNC message See Lookup.PSFT.Message.SccConstituentFullSync.Configuration for more information about this lookup definition. |
|
SCC_CONSTITUENT_SYNC.v1 |
Lookup.PSFT.Message.SccConstituentSync.Configuration |
Name of the lookup definition for SCC_CONSTITUENT_SYNC message See Lookup.PSFT.Message.SccConstituentSync.Configuration for more information about this lookup definition. |
|
Target Date Format |
yyyy-MM-dd |
Data format of the Date type data in the XML file and messages Do not modify this value. |
You can configure the message names, such as the SCC_CONSTITUENT_SYNC and SCC_CONSTITUENT_FULLSYNC defined in this lookup definition. Setting Up the Lookup.PSFT.Campus.Configuration Lookup Definition describes the procedure to configure these message names.
1.5.3.2 Lookup Definitions Used to Process SCC_CONSTITUENT_FULLSYNC Messages
The following lookup definitions are used to process SCC_CONSTITUENT_FULLSYNC messages:
1.5.3.2.1 Lookup.PSFT.Message.SccConstituentFullSync.Configuration
The Lookup.PSFT.Message.SccConstituentFullSync.Configuration lookup definition provides the configuration-related information for the SCC_CONSTITUENT_FULLSYNC messages.
The lookup definition has the following entries:
| Code Key | Decode | Description |
|---|---|---|
|
Affiliation Resource Object |
Affiliation |
Name of the Affiliation Resource Object |
|
Affiliations |
Affiliation Code~Affiliation Status~Affiliation Description~Affiliation Start Date~Affiliation End Date~Institution |
The code key value should be the same as the decode key value for the Affiliation Attribute Name entry (the next entry in this table).The decode key value lists all the attributes which are part of the Affiliation Resource form. The values should be separated by tilde (~) character.If a new affiliation attribute has to be added for reconciliation, the new attribute must be added to this decode key value. |
|
Affiliations Attribute Name |
Affiliations |
Name of the Affiliations Attribute Default value: |
|
Attribute Mapping Lookup |
Lookup.PSFT.Campus.SccConstituentFullSync.AttributeMapping |
Name of the lookup definition that maps Oracle Identity Manager attributes with the attributes in the SCC_CONSTITUENT_FULLSYNC message XML See Lookup.PSFT.Campus.SccConstituentFullSync.AttributeMapping for more information about this lookup definition. |
|
Custom Query |
Enter a Value |
If you want to implement limited reconciliation, then enter the query condition that you create by following the instructions given in the Limited Reconciliation. |
|
Custom Query Lookup Definition |
Lookup.PSFT.Campus.CustomQuery |
This entry holds the name of the lookup definition that maps resource object fields with OIM User form fields. This lookup definition is used during application of the custom query. See Limited Reconciliation for more information. |
|
Data Node Name |
Transaction |
Name of the node in the XML files to execute a transaction Default value: You must not change the default value. |
|
Employee Status |
Enabled |
Default status of an employee during the creation of an OIM User Note: You can change the status to Disabled, if you want the status to be Inactive when the OIM User is created. |
|
Message Handler Class |
oracle.iam.connectors.psft.common.handler.impl.PSFTCampusSyncReconMessageHandlerImpl |
Name of the Java class that accepts the XML payload, configuration information, and a handle to Oracle Identity Manager. Depending on the message type, it retrieves the appropriate configuration from Oracle Identity Manager and processes the message. To parse a specific message type, it relies on a Message Parser factory. If you want a customized implementation of the message, then you must extend the |
|
Message Parser |
oracle.iam.connectors.psft.common.parser.impl.CampusMessageParser |
Name of the parser implementation class that contains the logic for message parsing If you want a customized implementation of the message, then you must extend the |
|
Organization |
Xellerate Users |
Default organization in Oracle Identity Manager |
|
Recon Lookup Definition |
Lookup.PSFT.Campus.SccConstituentSync.Recon |
Name of the lookup definition that maps Oracle Identity Manager attributes with the Resource Object attributes See Lookup.PSFT.Campus.SccConstituentSync.Recon for more information about this lookup definition. |
|
Resource Object |
PeopleSoft Campus |
Name of the resource object |
|
Transformation Lookup Definition |
Lookup.PSFT.Campus.SccConstituentSync.Transformation |
Name of the transformation lookup definition See Configuring Transformation of Data During Reconciliation for more information about adding entries in this lookup definition. Note: The default value for transformation lookups for both SCC_CONSTITUENT_SYNC and SCC_CONSTITUENT_FULLSYNC messages is the same. You can use different lookups by changing the decode key value. |
|
User Type |
End-User |
It specifies the value with which a person is created in Oracle Identity Manager using the SCC_CONSTITUENT_FULLSYNC message. |
|
Use Transformation |
No |
Enter |
|
Use Validation |
No |
Enter |
|
Validation Lookup Definition |
Lookup.PSFT.Campus.SccConstituentSync.Validation |
Name of the validation lookup definition See Configuring Validation of Data During Reconciliation for more information about adding entries in this lookup definition. Note: The default value for validation lookups for both SCC_CONSTITUENT_SYNC and SCC_CONSTITUENT_FULLSYNC messages is the same. You can use different lookups by changing the decode key value. |
1.5.3.2.2 Lookup.PSFT.Campus.SccConstituentFullSync.AttributeMapping
The Lookup.PSFT.Campus.SccConstituentFullSync.AttributeMapping lookup definition maps OIM User attributes with the attributes defined in the SCC_CONSTITUENT_FULLSYNC message.
The Decode entries of this lookup definition are based on the message structure shown in Message Structure. All full data publish XML files contain this message structure at the beginning of the files. If the message structure changes (if the node names in the XML file are different), then the Decode entries in the lookup definition need to be updated as per the new message structure.
The following table provides the format of the values stored in this lookup definition:
| Code Key | Decode |
|---|---|
|
Affiliation Code |
SCC_AFL_CODE~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Affiliation Description |
SCC_AFL_STS_DESCR~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Affiliation End Date |
END_DT~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Affiliation Start Date |
START_DT~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Affiliation Status |
SCC_AFL_STATUS~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Campus ID |
CAMPUS_ID~PERSON_SA |
|
|
EMAIL_ADDR~SCC_PER_EMAIL_I |
|
First Name |
FIRST_NAME~SCC_PER_NAME_I2~NAME_TYPE=PRI~EFFDT |
|
Home Phone |
PHONE~SCC_PER_PHONE_I |
|
Institution |
INSTITUTION~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Last Name |
LAST_NAME~SCC_PER_NAME_I2~NAME_TYPE=PRI~EFFDT |
|
Start Date |
EFFDT~SCC_PER_NAME_I2~None~EFFDT |
|
User ID |
EMPLID~SCC_CM_PERSON_I~None~None~PRIMARY |
Code Key: Name of the OIM User field
Decode: Combination of the following elements separated by the tilde (~) character:
NODE~PARENT NODE~TYPE NODE=Value~EFFECTIVE DATED NODE~PRIMARY or RESOURCE=Resource Name
In this format:
NODE: Name of the node in the SCC_CONSTITUENT_SYNC message XML file from which the value is read. You must specify the name of the NODE in the lookup definition. It is a mandatory field.
PARENT NODE: Name of the parent node for the NODE. You must specify the name of the parent node in the lookup definition. It is a mandatory field.
TYPE NODE=Value: Type of the node associated with the Node value. Value defines the type of the Node.
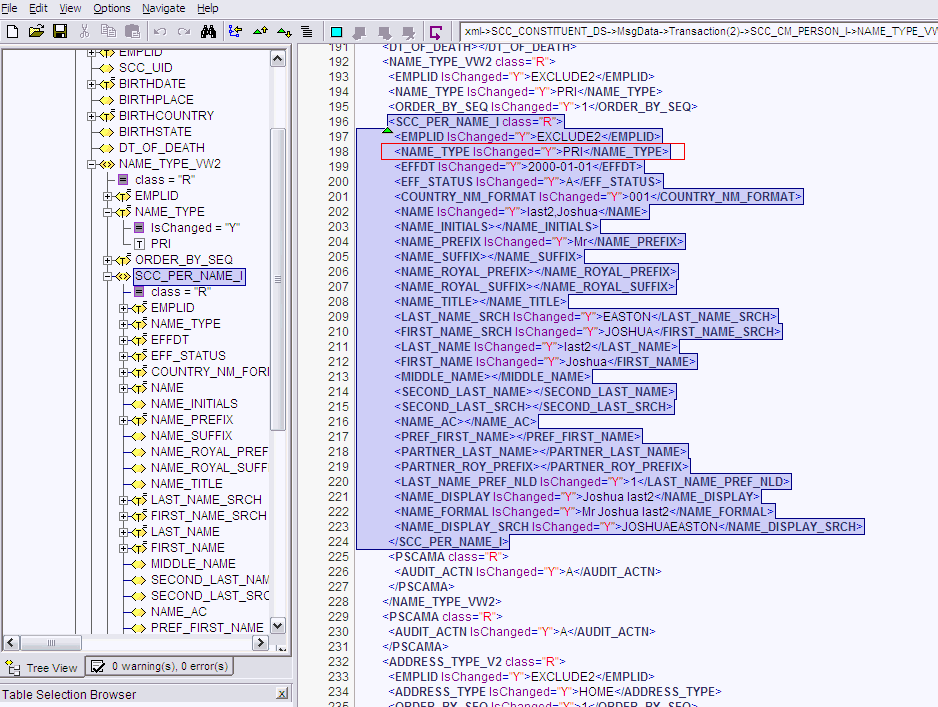
For example, in the SCC_CONSTITUENT_SYNC message, the rowset NAME_TYPE_VW lists the names assigned to a person. The names assigned could be primary, secondary, or nickname, depending on how it is configured in PeopleSoft.
If you want to use the primary name to create an OIM User, then you must locate the NAME_TYPE node with the value PRI to fetch First Name and Last Name from the XML message. Therefore, you must provide the following mapping in Decode column for First Name:
FIRST_NAME~NAMES~NAME_TYPE=PRI~EFFDT
In this format, NAME_TYPE specifies the TYPE NODE to consider, and PRI specifies that name of type PRI (primary) must be considered while fetching data from the XML messages. All other names types are then ignored.
The NAME_TYPE node with PRI value is shown in the following screenshot:
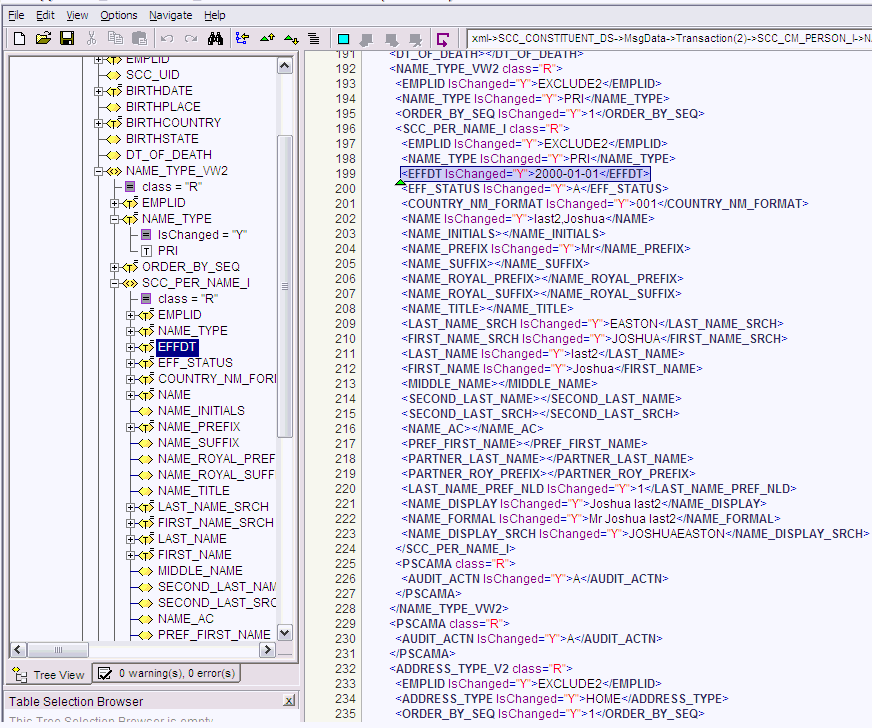
EFFECTIVE DATED NODE: Effective-dated node for the NODE, if any.
PeopleSoft supports effective-dated events. The value refers to the name of the node that provides information about the date on which the event becomes effective.
For example, names can be effective-dated in PeopleSoft. The EFFDT node in XML provides the date on which the name becomes effective for the OIM User.
The EFFDT node is shown in the following screenshot:
Primary or RESOURCE=Resource Name: Specifies if the node is a mandatory field or a resource field. For example, in case of a resource field, RESOURCE=Affiliations specifies that it is a field in the Affiliations resource object.
The following scenario illustrates how to map the entries in the lookup definition. On the target system, there is no direct equivalent for the First Name attribute of the OIM User. As a workaround, a combination of elements is used to decipher the value for each Code Key entry in the preceding table.
If you want to retrieve the value for the Code Key, First Name, then the name of the NODE will be FIRST_NAME as depicted in the XML file. See the sample XML file in Figure 1-9 for more information about each node in the SCC_CONSTITUENT_SYNC message.
Figure 1-9 Sample XML File for SCC_CONSTITUENT_SYNC Message
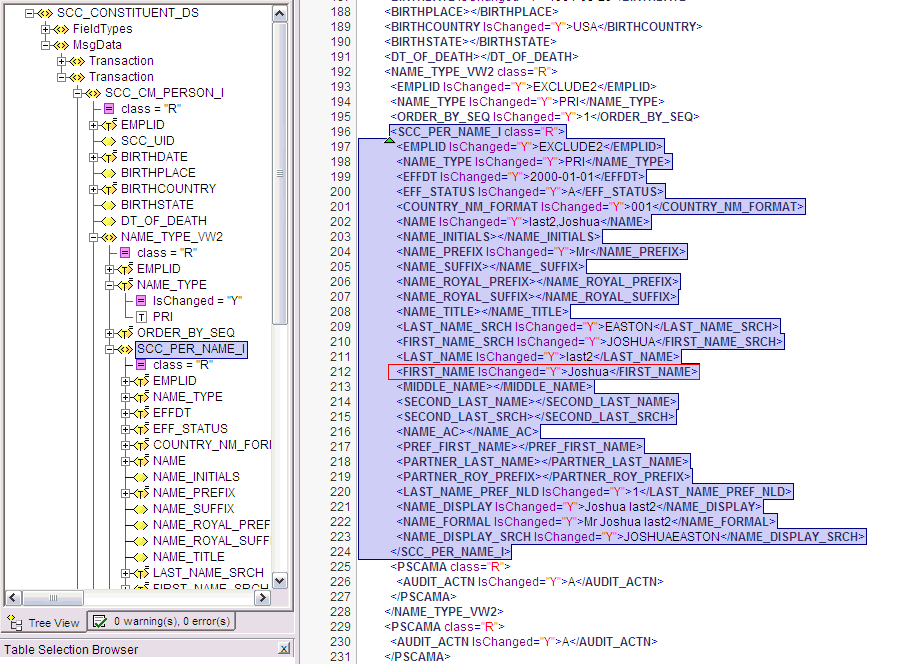
Description of "Figure 1-9 Sample XML File for SCC_CONSTITUENT_SYNC Message"
The PARENT NODE for the NODE FIRST_NAME will be SCC_PER_NAME_I. Now suppose, you have a scenario where you have multiple FIRST_NAME nodes in the XML file to support the effective-dated feature for this attribute. In this case, you must identify the TYPE NODE for the PARENT NODE that has the value PRI. In this example, the TYPE NODE is NAME_TYPE with the value PRI.
Next, you must locate the EFFECTIVE DATED NODE for FIRST_NAME in the XML file. This node provides the value when the event becomes effective-dated.
In Oracle Identity Manager, you must specify a mandatory field, such as User ID for reconciliation. This implies that to retrieve the value from XML, you must mention User ID as the primary node.
If you do not want to provide any element in the Decode column, then you must specify None. This is implemented for the User ID attribute.
Now, you can concatenate the various elements of the syntax using a tilde (~) to create the Decode entry for First Name as follows:
NODE: FIRST_NAME
PARENT NODE: SCC_PER_NAME_I
TYPE NODE=Value: NAME_TYPE=PRI
EFFECTIVE DATED NODE: EFFDT
So, the Decode column for First Name is as follows:
FIRST_NAME~SCC_PER_NAME_I~NAME_TYPE=PRI~EFFDT
1.5.3.3 Lookup Definitions Used to Process SCC_CONSTITUENT_SYNC Messages
The following lookup definitions are used to process the SCC_CONSTITUENT_SYNC messages:
1.5.3.3.1 Lookup.PSFT.Message.SccConstituentSync.Configuration
The Lookup.PSFT.Message.SccConstituentSync.Configuration lookup definition provides the configuration-related information for the SCC_CONSTITUENT_SYNC messages for reconciliation.
The Lookup.PSFT.Message.SccConstituentSync.Configuration lookup definition has the following entries:
| Code Key | Decode | Description |
|---|---|---|
|
Affiliation Resource Object |
Affiliation |
Name of the Affiliation Resource Object |
|
Affiliations |
Affiliation Code~Affiliation Status~Affiliation Description~Affiliation Start Date~Affiliation End Date~Institution |
The code key value should be the same as the decode key value for the Affiliation Attribute Name entry (the next entry in this table).The decode key value lists all the attributes which are part of the Affiliation Resource form. The values should be separated by tilde (~) character.If a new affiliation attribute has to be added for reconciliation, the new attribute must be added to this decode key value. |
|
Affiliations Attribute Name |
Affiliations |
Name of the Affiliations Attribute |
|
Attribute Mapping Lookup |
Lookup.PSFT.Campus.SccConstituentSync.AttributeMapping |
Name of the lookup definition that maps Oracle Identity Manager attributes with attributes in the SCC_CONSTITUENT_SYNC message XML See Lookup.PSFT.Campus.SccConstituentSync.AttributeMapping for more information about this lookup definition. |
|
Custom Query |
Enter a Value |
If you want to implement limited reconciliation, then enter the query condition that you create by following the instructions given in Limited Reconciliation. |
|
Custom Query Lookup Definition |
Lookup.PSFT.Campus.CustomQuery |
This entry holds the name of the lookup definition that maps resource object fields with OIM User form fields. This lookup definition is used during application of the custom query. See Limited Reconciliation for more information. |
|
Data Node Name |
Transaction |
Name of the node in the XML files to run a transaction |
|
Employee Status |
Enabled |
Default status of an employee during the creation of an OIM User Note: You can change the status to Disabled, if you want the status to be Inactive when the OIM User is created. |
|
Message Handler Class |
oracle.iam.connectors.psft.common.handler.impl.PSFTCampusSyncReconMessageHandlerImpl |
Name of the Java class that accepts the XML payload, configuration information, and a handle to Oracle Identity Manager. Depending on the message type, it retrieves the appropriate configuration from Oracle Identity Manager and processes the message. To parse a specific message type, it relies on a Message Parser factory. If you want a customized implementation of the message, then you must extend the |
|
Message Parser |
oracle.iam.connectors.psft.common.parser.impl.CampusMessageParser |
Name of the parser implementation class that contains the logic for message parsing If you want a customized implementation of the message, then you must extend the |
|
Organization |
Xellerate Users |
Default organization in Oracle Identity Manager |
|
Recon Lookup Definition |
Lookup.PSFT.Campus.SccConstituentSync.Recon |
Name of the lookup definition that maps Oracle Identity Manager attribute with Resource Object attribute See Lookup.PSFT.Campus.SccConstituentSync.Recon for more information about this lookup definition. |
|
Resource Object |
PeopleSoft Campus |
Name of the resource object |
|
Transformation Lookup Definition |
Lookup.PSFT.Campus.SccConstituentSync.Transformation |
Name of the transformation lookup definition It is empty by default. Note: The default value for transformation lookups for both SCC_CONSTITUENT_SYNC and SCC_CONSTITUENT_FULLSYNC messages is the same. You can use different lookups by changing the decode key value. |
|
User Type |
End-User |
It specifies the value with which a person is created in Oracle Identity Manager using the SCC_CONSTITUENT_SYNC message. |
|
Use Transformation |
No |
Enter |
|
Use Validation |
No |
Enter |
|
Validation Lookup Definition |
Lookup.PSFT.Campus.SccConstituentSync.Validation |
Name of the validation lookup definition It is empty by default. Note: The default value for validation lookups for both SCC_CONSTITUENT_SYNC and SCC_CONSTITUENT_FULLSYNC messages is the same. You can use different lookups by changing the decode key value. |
1.5.3.3.2 Lookup.PSFT.Campus.SccConstituentSync.AttributeMapping
The Lookup.PSFT.Campus.SccConstituentSync.AttributeMapping lookup definition maps OIM User attributes with the attributes defined in the SCC_CONSTITUENT_SYNC message XML. The following is the format of the values stored in this lookup definition:
| Code Key | Decode |
|---|---|
|
Affiliation Code |
SCC_AFL_CODE~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Affiliation Description |
SCC_AFL_STS_DESCR~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Affiliation End Date |
END_DT~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Affiliation Start Date |
START_DT~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Affiliation Status |
SCC_AFL_STATUS~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Campus ID |
CAMPUS_ID~PERSON_SA |
|
|
EMAIL_ADDR~SCC_PER_EMAIL_I |
|
First Name |
FIRST_NAME~SCC_PER_NAME_I~NAME_TYPE=PRI~EFFDT |
|
Home Phone |
PHONE~SCC_PER_PHONE_I |
|
Institution |
INSTITUTION~SCC_AFL_PERSON~None~None~RESOURCE=Affiliations |
|
Last Name |
LAST_NAME~SCC_PER_NAME_I~NAME_TYPE=PRI~EFFDT |
|
Start Date |
EFFDT~SCC_PER_NAME_I~None~EFFDT |
|
User ID |
EMPLID~SCC_CM_PERSON_I~None~None~PRIMARY |
For the description and format of the Code Key and Decode entries, see Lookup.PSFT.Campus.SccConstituentFullSync.AttributeMapping.
1.5.3.3.3 Lookup.PSFT.Campus.SccConstituentSync.Recon
This Lookup.PSFT.Campus.SccConstituentSync.Recon lookup definition maps the resource object field name with the value fetched from the Lookup.PSFT.Campus.SccConstituentSync.AttributeMapping lookup definition. The following is the format of the values stored in this lookup definition:
| Code Key | Decode |
|---|---|
|
Affiliation Code |
Affiliation Code~None~None~Resource |
|
Affiliation Description |
Affiliation Description~None~None~Resource |
|
Affiliation End Date |
Affiliation End Date~None~None~Resource |
|
Affiliations |
Affiliations |
|
Affiliation Start Date |
Affiliation Start Date~None~None~Resource |
|
Affiliation Status |
Affiliation Status~None~None~Resource |
|
Campus ID |
Campus ID |
|
Effective Start Date |
Start Date |
|
|
|
|
First Name |
First Name |
|
Home Phone |
Home Phone |
|
Institution |
Institution~None~None~Resource |
|
Last Name |
Last Name |
|
User ID |
User ID |
|
User Type |
User Type |
Code Key: Name of the resource object field in Oracle Identity Manager
Decode: Combination of the following elements separated by a tilde (~) character:
ATTRIBUTE~LOOKUP DEF~LKF~Resource
In this format:
ATTRIBUTE: Refers to the Code Key of the Lookup.PSFT.Campus.SccConstituentSync.AttributeMapping lookup definition
LOOKUP DEF: If the field is not a resource field, provide the value for ATTRIBUTE. If it is a resource field, provide None for LOOKUP DEF and LKF as they are not used in PeopleSoft Campus.
Resource: It indicates that this field is a resource field, which is an Affiliation form field.
In the following example, if the field is a user form field, such as Email, then:Code Key: Email
This is the resource object field name.Decode: Email
This is the Code Key entry in the attribute mapping lookup definition.
In the following example, if the field is an Affiliations resource form field, such as Affiliation Code, then:Code Key: Affiliation Code
Decode: Affiliation Code~None~None~Resource
The two values in the middle are None because they are not used in this connector. However, they are used in the PeopleSoft Employee Reconciliation and PeopleSoft User Management connectors.
1.5.3.4 Lookup.PSFT.Campus.CustomQuery
You can configure limited reconciliation to specify the subset of target system records that must be fetched into Oracle Identity Manager. This subset is defined on the basis of attribute values that you specify in a query condition, which is then applied during reconciliation.
The Lookup.PSFT.Campus.CustomQuery lookup definition maps resource object fields with OIM User form fields. It is used during application of the query condition that you create. See Limited Reconciliation. for more information. Setting Up the Lookup.PSFT.Campus.CustomQuery Lookup Definition provides instructions on how to add an entry in this lookup definition.
The following is the format of the values stored in this table:
Code Key: Resource object field name
Decode: Column name of the USR table
| Code Key | Decode |
|---|---|
|
Campus ID |
USR_UDF_CAMPUS_ID |
|
Effective Start Date |
Users.Start Date |
|
|
Users.Email |
|
First Name |
Users.First Name |
|
Last Name |
Users.Last Name |
|
User ID |
Users.User ID |
1.5.3.5 Lookup.PSFT.Campus.ExclusionList
The Lookup.PSFT.Campus.ExclusionList lookup definition provides a list of user IDs or person IDs that cannot be created on Oracle Identity Manager.
The following is the format of the values stored in this table:
Code Key: User ID resource object field name
Decode: List of user IDs separated by the pipe character (|)
See Setting Up the Lookup.PSFT.Campus.ExclusionList Lookup Definition for more information.
1.6 Roadmap for Deploying and Using the Connector
The following shows how information is organized in the rest of the guide:
-
Deploying the Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Using the Connector provides information about the tasks that must be performed each time you want to run reconciliation.
-
Extending the Functionality of the Connector describes procedures that you can perform to extend the functionality of the connector.
-
Testing and Troubleshooting provides information about testing the connector.
-
Determining the Root Audit Action Details provides information about root audit action.
-
Setting Up SSL on Oracle WebLogic Server describes how to configure SSL on Oracle WebLogic Server for PeopleTools.
-
Message Structure contains the message structure that is part of all full data publish XML files.