1 Introducing Oracle Audit Vault and Database Firewall
Downloading the Latest Version of This Manual
You can download the latest version of this manual from the following website:
http://www.oracle.com/pls/topic/lookup?ctx=avdf121
You can find documentation for other Oracle products at the following website:
System Features
About Oracle Audit Vault and Database Firewall
Oracle Audit Vault and Database Firewall (AVDF) secures databases and supported operating systems in two ways:
-
For databases, it provides a database firewall that can monitor and/or block SQL statements based on a firewall policy designed by an auditor, and provides a set of firewall reports.
-
For databases and supported operating systems, it collects audit data, and makes it available in audit reports. For Oracle databases, Oracle AVDF lets an auditor set audit policies and provision them from the Audit Vault Server console.
Supported Secured Targets
A secured target is any database or other target type (such as an operating system) that you are monitoring and securing with Oracle AVDF. The secured target types supported out-of-the-box are:
-
Oracle Database
-
IBM DB2 for LUW
-
Microsoft SQL Server
-
MySQL
-
SQL Anywhere
-
Sybase
-
Solaris Operating System
-
Oracle ACSF
-
Windows Operating System
-
Windows Active Directory
-
Linux Operating System
See Oracle Audit Vault and Database Firewall Administrator's Guide for the specific
Oracle AVDF features supported for each secured target type and version.
Other types of secured targets can be monitored by deploying custom plug-ins, available from Oracle or third parties. Oracle also provides the Oracle Audit Vault and Database Firewall Developer's Guide to create your own custom plug-ins.
Additional Platform Information
See Oracle Audit Vault and Database Firewall Installation Guide for detailed platform support for the current release.
In addition, you can find platform information for prior releases in Article 1536380.1 at the following website:
Auditing Features
Oracle AVDF auditing features allow an auditor to configure and manage the following:
-
Firewall policies
-
Audit policies for Oracle Database
-
Reports and report schedules
-
Fetching entitlement audit data for Oracle Database
-
Stored procedure auditing
-
Alerts and email notifications
-
Access rights to secured targets and groups (super auditors only)
Administrative Features
Oracle AVDF administrative features allow an administrator to configure and manage the following:
-
Secured Targets, their host computers, and their audit trail collection
-
Audit Vault Agent deployment
-
Database Firewalls in the database network
-
Audit data lifecycle, archiving, and purging
-
High Availability
-
Third party integrations
-
Access rights to secured targets and groups (super administrators only)
See Oracle Audit Vault and Database Firewall Administrator's Guide for detailed information on administrative functions.
Integrations With Third-Party Products
You can integrate Oracle AVDF with the following third-party products:
-
BIG-IP Application Security Manager (ASM): This product from F5 Networks, Inc. is an advanced Web Application Firewall (WAF) that provides comprehensive edge-of-network protection against a wide range of Web-based attacks. It analyzes each HTTP and HTTPS request, and blocks potential attacks before they reach the Web application server.
-
ArcSight Security Information Event Management (SIEM): This product is a centralized system for logging, analyzing, and managing syslog messages from different sources.
See the Oracle Audit Vault and Database Firewall Administrator's Guide for information on configuring these integrations.
Component Architecture
How Oracle AVDF Components Work Together
Oracle AVDF includes the Audit Vault Server, the Database Firewall, and the Audit Vault Agent. Figure 1-1 provides a high-level overview of how these components work together.
Figure 1-1 Audit Vault and Database Firewall Architecture
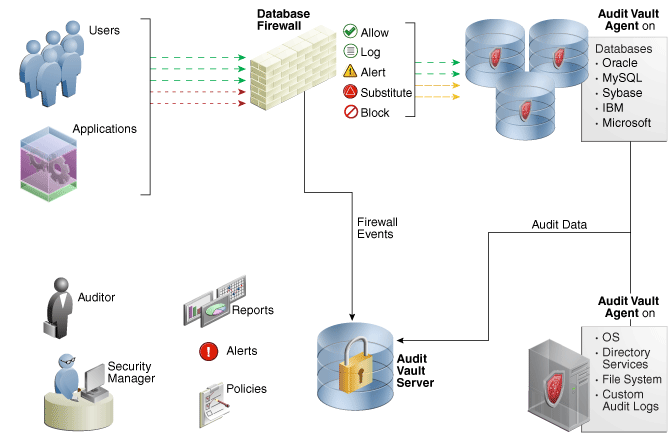
Description of ''Figure 1-1 Audit Vault and Database Firewall Architecture''
The process flow for the Oracle AVDF components is as follows:
-
For each secured target, the Audit Vault Agent has been deployed, and/or the Database Firewall has been placed in the network and configured to protect that target.
If the agent has been deployed, Oracle AVDF is configured to collect the appropriate audit trail from the secured target. If the Database Firewall is protecting the target, a firewall policy has been applied for that target.
You can configure multiple secured targets from different database product families, as well as non-database products, using the same Audit Vault Server.
-
The Audit Vault Agent retrieves the audit data from secured targets and sends this data to the Audit Vault Server.
The Database Firewall monitors SQL traffic to database secured targets and sends that data to the Audit Vault Server. The firewall can be configured to monitor and raise alerts only, or to block SQL traffic and optionally substitute statements according to a policy.
-
The Audit Vault Server collects and stores data from the Audit Vault Agent and Database Firewall in its internal data warehouse.
The data warehouse organizes this data into a set of internal dimension tables. The Audit Vault Server stores other information as well, for both the auditor and the administrator.
-
Once the audit data is in the data warehouse dimension tables, an auditor can generate and customize reports, as well as configure email notifications.
Any settings that you create, such as security settings, are contained in this server.
The Audit Vault Server
The Audit Vault Server contains the tools necessary to configure Oracle AVDF to collect audit data from, and apply firewall policies to, your secured targets. The Audit Vault Server also contains an Oracle database, and makes it available to reporting tools through a data warehouse.
The Audit Vault Server provides the following services:
-
Audit data collection and lifecycle management
-
Audit Vault Agent management
-
Database Firewall management
-
Audit and firewall policy management
-
Reporting
-
Alerting and notification management
-
User entitlement auditing
-
Stored Procedure Auditing
-
Archive and backup
-
High availability mode
-
Published data warehouse that can be used with reporting tools such as Oracle Business Intelligence Publisher to create customized reports
-
User access management
-
Third party integrations
The Database Firewall
The Database Firewall is a dedicated server that runs the Database Firewall software. Each Database Firewall collects SQL data from secured target databases, and then sends the data to the Audit Vault Server to be analyzed in reports.
An Oracle AVDF auditor can create firewall policies that define rules for how the Database Firewall handles SQL traffic to the database secured target. The firewall policy specifies the types of alerts to be raised in response to specific types of SQL statements, and when to block or substitute harmless SQL statements for potentially harmful statements. To do this, the Database Firewall can operate in one of two modes:
-
DPE Mode: Database Policy Enforcement. When in this mode, the Database Firewall applies rules in a firewall policy to monitor SQL traffic to your secured target database and block traffic, and/or substitute benign SQL statements for potentially destructive ones.
-
DAM Mode: Database Activity Monitoring. When in this mode, the Database Firewall applies rules in a firewall policy to monitor and raise alerts about potentially harmful SQL traffic to your secured target database, but it does not block or substitute SQL statements.
In order to control how the Database Firewall protects a database secured target, the administrator configures enforcement points for each secured target. The enforcement point specifies whether the firewall operates in DPE or DAM mode, which firewall policy to apply to the secured target, and other settings.
The Audit Vault Agent
The Agent retrieves the audit trail data from a secured target database and sends it to the Audit Vault Server. The Agent sends both valid and invalid audit records, gets configuration information, and sends error records using Oracle Call Interface (OCI) and JDBC password-based authentication. If the Agent is stopped, then the secured target database will still create an audit trail (assuming auditing is enabled). The next time you restart the Agent, then Oracle AVDF retrieves the audit data that had been accumulating since the Agent was stopped.
The Audit Vault Agent also contains host monitoring software that monitors SQL traffic to a database over the network and sends this information to a Database Firewall. For detailed information on host monitoring, see Oracle Audit Vault and Database Firewall Administrator's Guide.
The Oracle AVDF administrator configures one Audit Vault Agent for each host and one or more audit trails for each individual secured target database. See the Oracle Audit Vault and Database Firewall Administrator's Guide for information on all administration functions.
The Auditor's Role
As an auditor, you use the Audit Vault Server console to configure the following for databases or non-databases you are monitoring with Oracle AVDF:
-
Secured Targets - For each target you are monitoring, the Oracle AVDF administrator must configure a secured target in the Audit Vault Server. As an auditor, you can then specify audit and/or firewall policies for the secured target, as well as other requirements. See "Understanding Secured Targets".
-
Firewall Policies - For any supported database, you can use the Database Firewall and design a firewall policy based on analyzed SQL statements from your secured targets. See "Creating Database Firewall Policies" for details.
-
Audit Policies - For Oracle databases, you can use Oracle AVDF to design audit policies and provision them to the database. See "Creating Audit Policies for Oracle Databases" for details.
-
Alerts and Notifications - You can create simple or complex alerts based on conditions you specify for the secured targets you are monitoring. You can also specify alert notifications using email templates. See "Creating Alerts" for details.
-
Audit Trails - For any secured target type, you can monitor the status of audit trails and see audit reports. See "Viewing a List of Audit Trails".
-
Reports - You can schedule and generate a variety of audit and firewall reports in Oracle AVDF, create report notifications, as well as add your own customized reports. See "Generating Reports" for details.
There are two auditor roles in Oracle AVDF, with different access levels:
-
Super Auditor - This role has access to all secured targets and can grant access to specific secured targets and groups to an auditor. A super auditor can also assign the super auditor role to others.
-
Auditor - This role can only see data for secured targets to which they have been granted access by a super auditor.
Understanding Secured Targets
A secured target is any supported database or non-database that you monitor with Oracle AVDF. Secured targets can be monitored by the Audit Vault Agent, the Database Firewall, or both.
The Oracle AVDF administrator creates and configures secured targets, providing host addresses, usernames, passwords, and other necessary information.
If a secured target is monitored by a Database Firewall, the Oracle AVDF administrator configures the Database Firewall, and also configures an enforcement point for each secured target.
Once secured targets are configured, an auditor can do the following for each one:
-
Collect audit data
-
Enable stored procedure auditing (SPA)
-
If the target is a database secured by a Database Firewall:
-
Design and apply a firewall policy
-
View the status of configured enforcement points
-
-
If the secured target is an Oracle database:
-
Define and provision the audit policies
-
Retrieve user entitlement information
-
-
Set a data retention policy
-
Generate a variety of reports
-
Monitor audit trail status
Super auditors can create secured target groups for access control purposes. Super auditors grant auditors access to individual secured targets or to target groups.
For details on secured targets, see "Managing Secured Targets".
Understanding Firewall Policies
Oracle AVDF lets you protect database secured targets with a database firewall. The firewall monitors SQL traffic to the database, logs activity, sends alerts, and can also block specific types of SQL statements and replace them with substitute statements that you configure.
A firewall policy determines how the database firewall handles SQL traffic to the secured target database. Oracle AVDF includes a firewall policy editor that lets you design a firewall policy. You can design the policy by analyzing your current SQL statement traffic, and then configuring settings in the firewall policy based on these statements.
Once you design the policy in the Audit Vault Server policy editor, you can upload it to a secured target in the auditor console. You can assign a different policy to different secured targets.
For details, see "Creating Database Firewall Policies".
Planning the Protection Level for Your Databases
Depending on operational needs, Database Firewall can operate in one of the following modes:
-
Database Activity Monitoring (DAM): The system detects and logs unusual activity, and produces warnings, but does not block potential threats. This is useful during the early stages of deployment while you are developing and refining a policy. It is also known as monitoring mode.
-
Database Policy Enforcement (DPE): The system performs all the actions of database activity monitoring and blocks potential attacks. It is also known as blocking mode.
These modes operate independently. For example, one Database Firewall can simultaneously monitor one secured target while blocking another.
Consider what you want the Database Firewall to achieve for you. Do you want:
-
Access logging?
-
Warnings of potential attacks?
-
Blocking of potential attacks?
In general, implementing only audit logging requires the least up-front development time to create a satisfactory policy. SQL statement blocking requires the most development time, but provides the greatest protection.
One strategy for deployment is to start with audit logging only, and then deploy a policy file that can protect the database against potential attacks at a later date. This helps you to become familiar with the deployment.
If you want to block SQL statements eventually, then using Database Activity Monitoring (DAM) can build confidence before you deploy the system fully.
When DAM mode is set, policies can include block action levels, but statements with specified action levels pass straight through. Syslog events and reports show the statements as blocked, while in reality, the statements passed through normally. This enables you to evaluate the system in a live environment before you switch on statement blocking. During this evaluation phase, you can change the policy to modify the system responses.
Understanding Audit Policies and Audit Data Collection
About Audit Policies and Audit Data Collection
The Oracle AVDF administrator configures Oracle Database and other types of secured targets (both databases and non-databases). As an auditor, you can then retrieve audit data from these secured targets and generate various reports.
If the secured target is an Oracle Database, Oracle AVDF also lets you configure and provision audit policies for that database. You can then retrieve the current audit settings from an Oracle Database and modify them, as well as add new audit policies, for the following:
-
SQL statements
-
Database objects
-
Fine-grained auditing
-
Capture rules for redo log activity
Once you have configured the audit policies for an Oracle Database, you can then provision them to the database. You will then be able to see, in the Audit Vault Server console, if those policies are changed by a database administrator at the database.
For details, see "Creating Audit Policies for Oracle Databases".
Requirements for Collecting Audit Data from Secured Targets
Requirements for Oracle Database
-
Ensuring That Auditing Is Enabled in the Secured Target Database
-
Using Recommended Audit Settings in the Secured Target Database
Ensuring That Auditing Is Enabled in the Secured Target Database
Before Oracle AVDF can collect audit data from the secured target databases, auditing must be enabled in those databases. A database administrator can check the type of auditing your database uses by logging in to SQL*Plus and running the appropriate command.
For example, to check if standard auditing is enabled:
SQL> SHOW PARAMETER AUDIT_TRAIL NAME TYPE VALUE ---------------------- ----------- ----------- audit_trail string DB
This output shows that standard auditing is enabled and audit records are being written to the database audit trail.
For fine-grained auditing, you can query the AUDIT_TRAIL column of the DBA_AUDIT_POLICIES data dictionary view to find the audit trail types that are set for the fine-grained audit policies on the database.
Using Recommended Audit Settings in the Secured Target Database
After your database administrator checks that auditing is enabled, Oracle recommends that the following areas of the database have auditing enabled:
-
Database schema or structure changes. Use the following
AUDITSQL statement settings:-
AUDIT ALTER ANY PROCEDURE BY ACCESS; -
AUDIT ALTER ANY TABLE BY ACCESS; -
AUDIT ALTER DATABASE BY ACCESS; -
AUDIT ALTER SYSTEM BY ACCESS; -
AUDIT CREATE ANY JOB BY ACCESS; -
AUDIT CREATE ANY LIBRARY BY ACCESS; -
AUDIT CREATE ANY PROCEDURE BY ACCESS; -
AUDIT CREATE ANY TABLE BY ACCESS; -
AUDIT CREATE EXTERNAL JOB BY ACCESS; -
AUDIT DROP ANY PROCEDURE BY ACCESS; -
AUDIT DROP ANY TABLE BY ACCESS;
-
-
Database access and privileges. Use the following
AUDITSQL statements:-
AUDIT ALTER PROFILE BY ACCESS; -
AUDIT ALTER USER BY ACCESS; -
AUDIT AUDIT SYSTEM BY ACCESS; -
AUDIT CREATE PUBLIC DATABASE LINK BY ACCESS; -
AUDIT CREATE SESSION BY ACCESS; -
AUDIT CREATE USER BY ACCESS; -
AUDIT DROP PROFILE BY ACCESS; -
AUDIT DROP USER BY ACCESS; -
AUDIT EXEMPT ACCESS POLICY BY ACCESS; -
AUDIT GRANT ANY OBJECT PRIVILEGE BY ACCESS; -
AUDIT GRANT ANY PRIVILEGE BY ACCESS; -
AUDIT GRANT ANY ROLE BY ACCESS; -
AUDIT ROLE BY ACCESS;
-
Requirements for SQL Server, Sybase ASE, and IBM DB2 Databases
Ensure that auditing is enabled in these databases. You also should ensure that they are correctly configured to send audit data to the Audit Vault Server. A database administrator can check these requirements for you. For more information, check the documentation for these databases and Oracle Audit Vault and Database Firewall Administrator's Guide.
Configuring Alerts and Notifications
Oracle AVDF lets you define rule-based alerts on audit records and specify notification actions for those alerts. Whenever an audit event meets the rule or condition defined in the alert definition, an alert is raised and a notification is sent as specified. You can define alerts by type of secured target, the number of times an event occurs, and by using available fields in audit records to define a Boolean condition that must be met. You can also configure email templates to be used for alert notifications.
You can monitor and respond to alerts from the Audit Vault Server console and from alert reports.
For details, see "Creating Alerts".
Generating Reports
As an Oracle AVDF auditor, you can generate various audit reports for the secured targets to which you have access. You can schedule, print, and/or email the reports to others, in PDF or XLS format. Reports include information on audit data, entitlements, and stored procedures. You can also generate compliance reports to meet regulations associated with credit card, financial, data protection, and health care-related data.
Oracle AVDF also lets you browse and customize report data interactively, and upload your own custom reports created with third party tools.
For details, see:
Creating Users and Managing Access
A super auditor creates auditor accounts, and manages auditor access to secured targets and secured target groups. For information on these functions, see "Managing Access and Other Settings".
Logging in to Audit Vault Server Console
Logging in to the Audit Vault Server Console
To log in to the Audit Vault Server console:
-
From a browser, enter the following URL:
https://host/consolewhere
hostis the server where you installed Audit Vault Server.For example:
https://192.0.2.1/console
-
In the Login page, enter your user name and password, and then click Login.
The Home page appears.
Understanding the Tabs in the Audit Vault Server Console UI
When you log into Audit Vault Server console as an auditor or super auditor, you see the auditor's dashboard on the Home page, and the functions available for the auditor roles.
From the Home tab, you can:
-
Select a date range for viewing event data.
-
View five types of graphical summaries (pie charts and bar graphs) of alert activity and event activity over the specified time period. These graphical summaries include:
-
Recently Raised Alerts
This area displays alerts raised within the period you selected. You can view specific alert levels by clicking See all Warning Alerts or See All Critical Alerts.
-
Attestation Actions
See report attestation actions you need to take within your selected time range.
-
Top Five Audit Sources by Number of Alerts
Click a bar in this bar graph to find more detailed critical and warning alert information that shows a severity level for a particular source.
-
Failed Logins
See failed logins within your selected time range.
-
Other tabs let you access the following functions:
-
Secured Targets - lets you set firewall, audit, and data retention policies for each secured target, manage entitlement snapshots, set up secured target groups, see audit trails and enforcement points
-
Reports - lets you generate default reports, schedule reports, customize reports online, and upload your custom reports
-
Policy - lets you manage audit and firewall policies, and configure alerts
-
Settings - lets you change your password, create and manage email distribution lists, configure email notification templates for alerts and reports, view audit trail and enforcement point status, manage user accounts and access, and view job status.
The following Quick Links are available from all tabs:
-
Enforcement Points - lets you check enforcement point details and status
-
Audit Trails - lets you check audit trail details and status
Working with Lists of Objects in the UI
Throughout the Audit Vault Server UI, you will see lists of objects such as reports, users, secured targets, firewall policies, etc. You can filter and customize any of these lists of objects in the same way as you can for Oracle AVDF reports. This section provides a summary of how you can filter and custom the display of lists of objects. For more detailed information, see the "Filtering and Controlling the Display of Data in a Report".
To filter and control the display of lists of objects in the Audit Vault Server UI:
-
To find an item in the list, enter its name in the search box, and then click Go.
-
To customize the list, from the Actions menu, select any of the following:
-
Rows Per Page: Select the number of rows to display per page.
-
Select Columns: Select which columns to display.
-
Filter: Filter the list by column or by row using regular expressions with the available operators. When done, click Apply.
-
Format: Format the list by selecting from the following options:
-
Sort
-
Control Break
-
Highlight
-
Chart
-
Group By
Fill in the criteria for each option as needed and click Apply.
-
-
Save Report: Save the current view of the list. Enter a name and description and click Apply.
-
Download: Download the list. Select the download format (CSV or HTML) and click Apply.
-