Two-Factor Authentication and Smart Cards
Smart cards provide a second proof of identity when logging in to sensitive computers and web sites.
About Two-Factor Authentication
Two-factor authentication (2FA) adds an independent authentication step, which strengthens login verification. 2FA is a form of Multi-Factor Authentication (MFA) in which a user must present several separate pieces of evidence to an authentication mechanism before the user can gain access to a computer system. In 2FA, the user must supply two of the following categories of MFA evidence:
-
Something you know, for example a personal identification number (PIN) or password
-
Something you possess, for example a smart card, challenge response key fob, or token generator
-
Something inherent to your body, for example a biometric fingerprint, retina scan, or voice print
In addition to the two proofs of identity, 2FA typically requires users to confirm that they themselves are the persons trying to log in to the account. An Oracle Solaris computer server enforcing 2FA would require two separate proofs of identity, a smart card (something you possess) and a PIN (something you know).
Smart cards, also called common access cards (CAC), are plastic cards with an embedded microchip that can provide personal identification, authentication, data storage, and application processing. In addition, they can enable the encryption and cryptographic signing of email and use of public key infrastructure (PKI) authentication tools. Logging in with a smart card in Oracle Solaris provides much stronger security than network login processes that depend on traditional passwords only.
U.S. Government Smart Cards
In this guide, a CAC is a U.S. Department of Defense (DoD) smart card that is used for 2FA. CACs are issued as standard identification for cleared government employees. Government employees use their CAC to access government buildings and computer networks. The CAC contains cardholder information, including a PKI certificate. Software in a smart card reader through standard Internet protocols can compare the cardholder information with data on a government server and either grant or deny access.
-
Geneva Conventions Identification Card – For active duty/reserve armed forces and uniform service members
-
Geneva Convention Accompany Forces Card – For emergency-essential civilian personnel
-
ID and Privilege Common Access Card – For civilians residing on military installations
-
ID card for DoD/Government Agency identification – For civilian employees and contractors
Oracle Solaris recognizes the four kinds of DoD CAC cards for computer authentication:
Local, Remote, and ILOM Smart Card Logins
The following figure illustrates the entry points for smart card logins.
Figure 7 Smart Card Entry Points
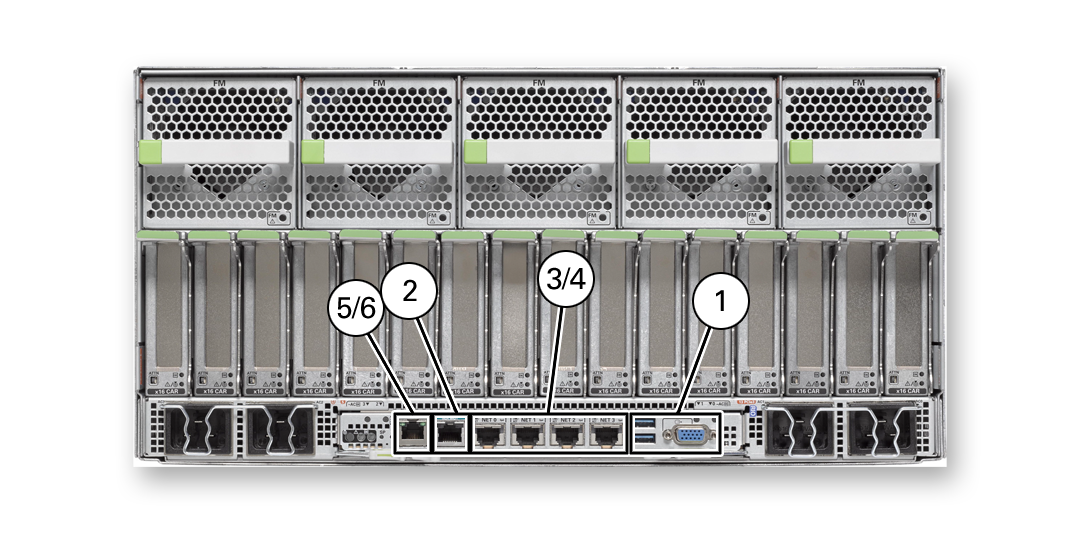
-
1 – Smart card reader directly attached to the system. Monitors and keyboards also use this entry point. See Local Login With a Smart Card.
-
2 – Smart card reader directly attached to the system through a serial port. Consoles and terminal programs also use serial ports. See Local Login With a Smart Card.
-
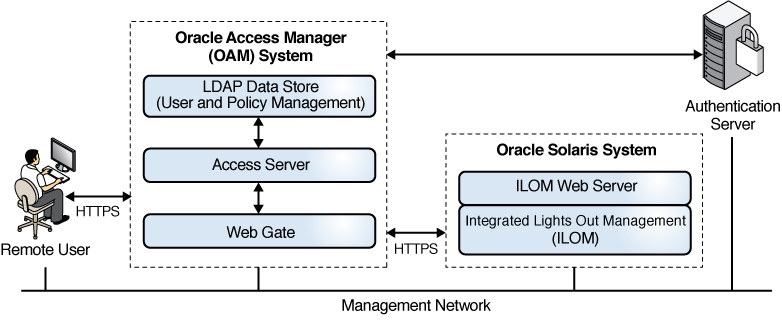
3 – Remote network access to smart card by using Secure Shell. See Remote Login Over a Network With a Smart Card.
-
4 – Remote network access to smart card by using an X11 desktop. See Remote Login Over a Network With a Smart Card.
-
5/6 – Integrated Lights Out Management (ILOM) port connects to smart card by using Secure Shell or https. See ILOM Login With a Smart Card.
Smart cards and smart card readers in Oracle Solaris provide 2FA user authentication and nonrepudiation for three types of login: local login, remote login over the network, and remote login using Oracle Integrated Lights Out Manager (ILOM). After configuring their smart card login and authenticating to the server, users can also use secure web communication and secure email by configuring their web browser and mailer. For details, see Enabling Your Web Browser and Email to Use Your Smart Card.
The following figures illustrate 2FA logins that use a smart card.
Figure 8 Local Login With a Smart Card
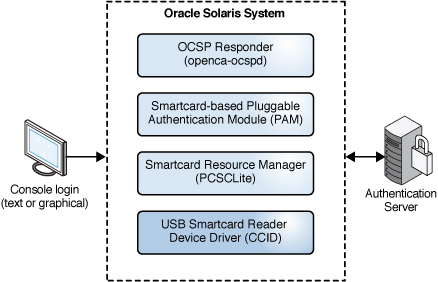
Figure 9 Remote Login Over a Network With a Smart Card
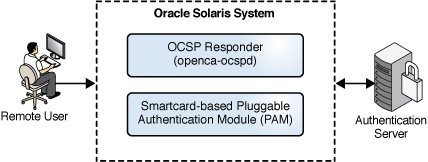
Figure 10 ILOM Login With a Smart Card
Implementation of Two-Factor Authentication in Oracle Solaris
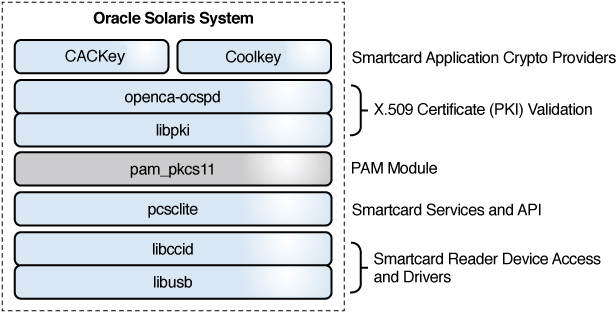
Oracle Solaris implements 2FA with smart cards by using the following software stack. Most of the software is available in the smartcard package. The CACKey crypto provider is in a separate package. None of the IPS package groups install smart card packages, so you must install them.
Figure 11 Software Implementation of Two-Factor Authentication in Oracle Solaris
-
libusb – Open source library that enables access to USB devices. See https://sourceforge.net/projects/libusb/files/libusb-1.0/
-
libccid – Open source library for generic USB CCID (Chip/Smart Card Interface Devices) driver and ICCD (Integrated Circuit Card Devices).
-
libpki – Open source library that manages certificates from generation to validation.
For documentation, see libpki Documentation.
-
pcsclite – Provides the pcscd daemon as an SMF service that responds to requests to load drivers and handles runtime programs that are linked to the libpcsclite.so client library.
The libpcsclite.so client library connects a smart card driver to authentication software, in concert with the pam_pkcs11 module.
-
For support of DoD CAC-enabled applications and web sites, a 2FA implementation requires CACKey software to link to the PKCS #11 module and web browser plugin.
-
For support of PIV card-enabled applications and web sites, a 2FA implementation requires Coolkey software to link to the PKCS #11 module and web browser plugin.
-
-
openca-ocspd – Open source Online Certificate Status Protocol (OCSP) responder
OCSP is an Internet protocol for verifying whether an X.509 digital certificate is still valid. OCSP messages are encoded in ASN.1 and are usually communicated over HTTP. An OCSP server responds to requests for certificate verification, therefore are called OCSP responders.
-
pam_pkcs11(5) – Pluggable authentication module (PAM) for the PKCS #11 token libraries that are used to authenticate users to an Oracle Solaris system.
The 2FA software stack consists of the following modules:
The following figure illustrates the module connections for smart cards.
Figure 12 Software Connections for Two-Factor Authentication in Oracle Solaris
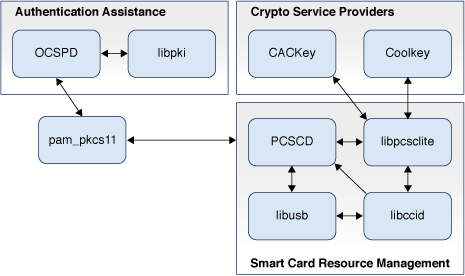
Software Cryptographic Providers for Smart Cards
-
Coolkey – Available from the smartcard package.
Coolkey dynamically detects the presence of tokens when the pcsclite daemon (pcscd) is managing one or more PKI hardware token device interfaces, such as a smart card reader or other CCID supported devices.
-
CACKey – Available from DISA for users with a security clearance and a Controlled Access Card. This software is also available from the solaris publisher.
CACKey provides a standard PKCS #11 interface for smart cards that are connected to a PC/SC compliant reader. CACKey performs a similar function to Coolkey, but supports only U.S. Government smart cards that implement the Government Smart Card Interoperability Specification (GSC-IS) v2.1 or newer. To view the specification, go to NIST Computer Security Division web site and search the page for "6887". For a list of the cards, see U.S. Government Smart Cards.
As illustrated in Software Implementation of Two-Factor Authentication in Oracle Solaris and Software Connections for Two-Factor Authentication in Oracle Solaris, Oracle Solaris supports smart card cryptography from two providers:
Hardware Readers for Smart Cards
-
HID/Omnikey, 3121
-
Identive (formerly SCM Microsystems), SCR-3310v2 and SCR-3310
-
ActivCard / ActivIdentity V3
The following smart card hardware readers can be attached to an Oracle Solaris system for a local login with a smart card to authenticate to the system:
Smart Card Architecture in Oracle Solaris
The following figure illustrates how Oracle Solaris connects to locally attached smart card readers and makes the resources on those smart cards available to cryptographic service providers and smart card-enabled applications.
Figure 13 PC/SC Layer Connecting Drivers to the Smart Card
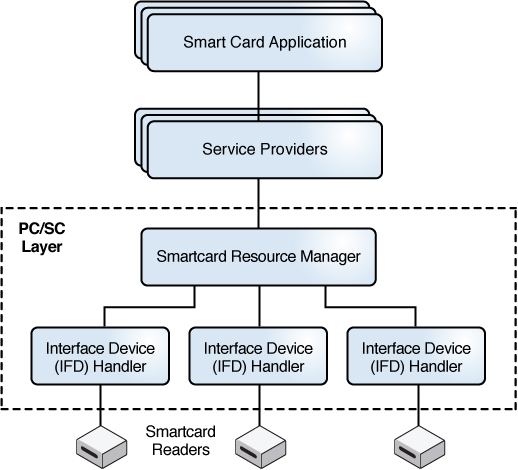
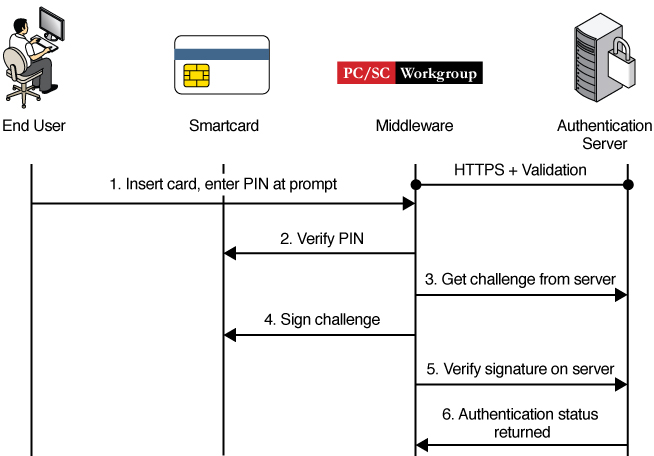
A smart card reader connects and communicates with a smart card on an Oracle Solaris system by using the PC/SC industry standard for accessing smart cards. The pam_pkcs11 module integrates with the software in the smartcard package to provide 2FA authentication. Then, the OCSP responder communicates with an existing smart card Certificate Authentication (CA) server infrastructure to authenticate and verify the user-entered smart card PIN and verify the X.509 certificate that resides on the smart card.
Note - If you do not use OCSP, you can use local files to verify certificates and users.
The following figure illustrates how Oracle Solaris handles PKI authentication of a smart card.
Figure 14 PKI Authentication by Smart Card