Packet Filter Firewall and Packet Processing
This section illustrates how packets arrive on a firewall host and are processed by the firewall, which sits between network devices and the IP module. OpenBSD Packet Firewall illustrates how the firewall module can inspect all packets which travel between network devices and the host's IP stack. Packet Flow in the OpenBSD Packet Firewall illustrates how packets are processed inside the firewall module.
Packet Filter Firewall Module in Oracle Solaris
The following illustration shows how a firewall host forwards a packet from a remote source to a remote destination. Forwarding is shown at the bottom of the graphic.
Figure 3 OpenBSD Packet Firewall
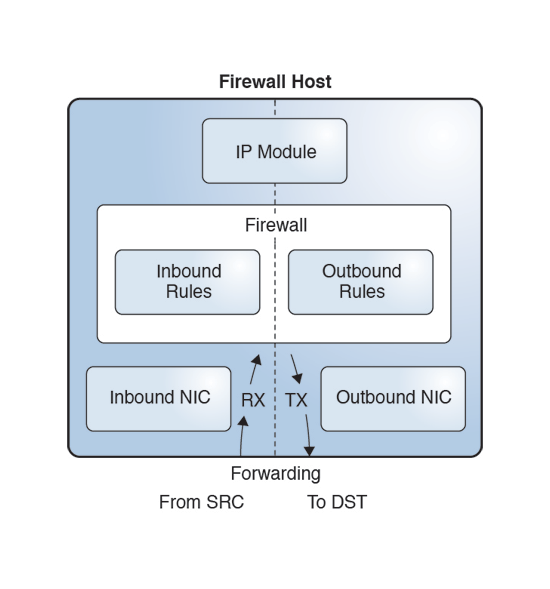
The left side is the receiving side (RX), the inbound path. The right side is the transmitting side (TX). The packet enters the host from the inbound NIC. As the inbound packet moves toward the IP module, the firewall intercepts it and applies inbound rules. If the inbound policy accepts the packet, the firewall sends the inbound packet to the IP module.
The IP module uses the destination address in the IP header to find a route. If the IP module finds a matching route, it transmits the packet (TX). As the packet travels towards the outbound NIC, the firewall intercepts it again. This time the firewall applies outbound rules to the packet. If the outbound policy accepts the packet, the firewall sends it to the outbound NIC, which transmits the packet to the remote destination.
Packet Processing in PF
Packet Flow in the OpenBSD Packet Firewall illustrates the packet inspection process by the PF firewall module. The dashed boxes indicate administrative options. PF rules can include options to reassemble IP packet fragments, process NAT rules, log actions, and create a state.
Figure 4 Packet Flow in the OpenBSD Packet Firewall
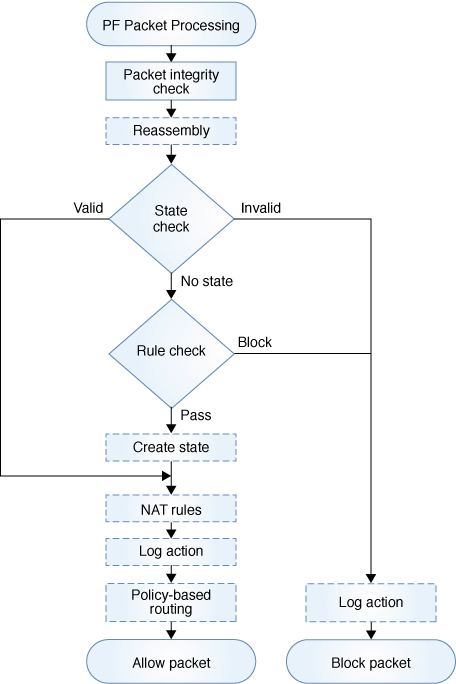
As soon as a packet enters the firewall, the firewall runs a basic packet integrity check. It also reassembles fragments into complete packets if the administrator has specified the set reassemble yes directive. These integrity checks discard packets with invalid flags settings. Then the firewall tries to match the packet to the existing state.
-
State is found but is invalid for the packet. For example, the sequence numbers of TCP packets might not be in the expected range.
-
State is found and is valid so the packet is accepted.
-
No state is found, in which case the firewall will try to find a matching rule (Rule check).
Three outcomes are possible:
In the last case, where no state is found, the firewall looks up a list of rules to find a matching rule. If no matching rule is found, the firewall accepts the packet with no further action.
If the rule is found, then it comes with a policy action, either block or pass. By default, the pass rule in PF creates state for a matching packet. To prevent state creation, use the no state option in a particular rule.
If the packet matches the block rule, then it is discarded. Both block and pass actions accept an optional log action to log the packet.
-
NAT actions change the source address, the destination address, or both addresses.
-
Routing actions, called policy-based routing (PBR), select the outbound NIC for forwarding the packet to its destination. PBR can override two parameters that the IP module uses to route packets, the outgoing interface and the next hop address. Otherwise, the IP module makes all routing decisions.
PBR is more flexible than routing in the IP module. The IP module's routing table uses only the destination address to decide which network interface to use to forward a packet. The firewall can use virtually any field in a packet header when determining which network interface should forward a packet.
The pass rule might add optional NAT actions and routing actions for the packet.
As shown in OpenBSD Packet Firewall, when an accepted packet leaves the firewall, an inbound packet travels to the IP module and an outbound packet travels to the appropriate NIC (TX).