SSL Kernel Proxy Encrypts Web Server Communications
Any web server that runs on Oracle Solaris can be configured to use the SSL protocol at the kernel level, that is, the SSL kernel proxy. Examples of such web servers are the Apache 2.2 web server and the Oracle iPlanet Web Server. The SSL protocol provides confidentiality, message integrity, and endpoint authentication between two applications. When the SSL kernel proxy runs on the web server, communications are accelerated. The following illustration shows the basic configuration.
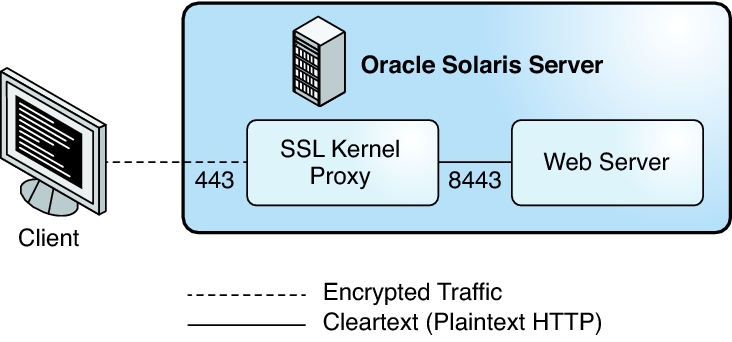
Figure 1 Kernel-Encrypted Web Server Communications
The proxy accelerates SSL performance for server applications, like web servers, so it offers better performance than applications that rely on user-level SSL libraries. The performance improvement can be over 35 percent, depending on the workload of the application.
The SSL kernel proxy is transparent. It has no assigned IP address. Therefore, web servers see real client IP addresses and TCP ports.
The SSL kernel proxy and web servers are designed to work together.
Kernel-Encrypted Web Server Communications shows a basic scenario with a web server that is using the SSL kernel proxy. The SSL kernel proxy is configured on port 443, whereas the web server is configured on port 8443, where it receives unencrypted HTTP communications.
The SSL kernel proxy can be configured to fall back to user-level ciphers when it does not support the requested encryption.
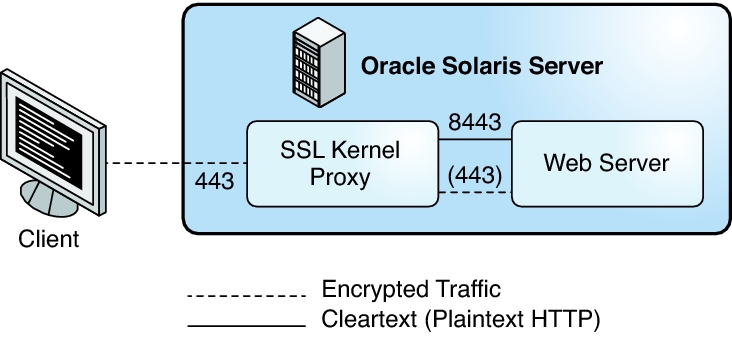
Kernel-Encrypted Web Server Communications With User-Level Fallback Option shows a more complex scenario. The web server and SSL kernel proxy are configured to fall back to the user-level web server SSL.
The SSL kernel proxy is configured on port 443. The web server is configured on two ports. Port 8443 receives unencrypted HTTP communications, while port 443 is a fallback port. The fallback port receives encrypted SSL traffic for cipher suites that are unsupported by the SSL kernel proxy.
The SSL kernel proxy implements the server side of the SSL protocol. The proxy offers several advantages.
Figure 2 Kernel-Encrypted Web Server Communications With User-Level Fallback Option
The SSL kernel proxy supports the TLS 1.0 and SSL 3.0 protocols, although the SSL 3.0 protocol is disabled by default. Most common cipher suites are supported. See the ksslcfg(1M) man page for the complete list of supported cipher suites and instructions for enabling or disabling specific cipher suites or protocols. The proxy can be configured to fall back to the user-level server for any unsupported cipher suites.