6 Managing Oracle Key Vault Virtual Wallets and Security Objects
Oracle Key Vault provides the mechanism of a virtual wallet to upload and store your security objects that you can then share with trusted peers at access levels appropriate to their organizational function.
6.1 About Virtual Wallets
A virtual wallet is a container for security objects like public and private encryption keys, including TDE, Oracle wallets, Java keystores, certificates, and credential files.
6.1.1 How Virtual Wallets Work
Oracle Key Vault provides the mechanism of a virtual wallet to group security objects for sharing with multiple users, who need them to access encrypted data.
Any user can create a virtual wallet. After you create a virtual wallet, you can add keys and other security objects to the wallet. You can then grant other users, endpoints, user and endpoint groups access to the virtual wallet at various levels of access. A virtual wallet can be modified at any time. You can modify wallet contents, the users that must have access, and the access level of users according to the needs of the moment.
Other than the Key Administrator, access to the virtual wallet must be granted explicitly to all users. Read, modify, and manage wallet permissions are required to add and remove objects from the wallet, and to grant or modify wallet access to other users and groups.
Parent topic: About Virtual Wallets
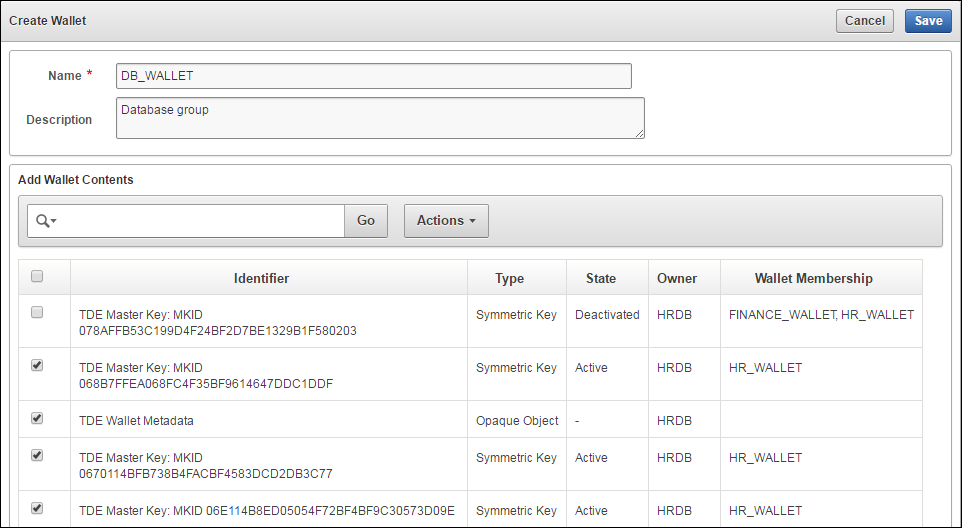
6.1.2 Create a Virtual Wallet
You can create a virtual wallet, and add security objects to it at the same time. However, you can also create an empty virtual wallet, and add security objects to it later. You can modify access-mappings on a virtual wallet at any time.
To create a virtual wallet and add security objects to it:
Parent topic: About Virtual Wallets
6.1.3 Add Security Objects to a Virtual Wallet
You can add new security objects to a virtual wallet at any time as needed.
Parent topic: About Virtual Wallets
6.1.4 Remove Security Objects from a Virtual Wallet
You can remove security objects from virtual wallets at any time as needed.
To remove security objects from wallets:
Parent topic: About Virtual Wallets
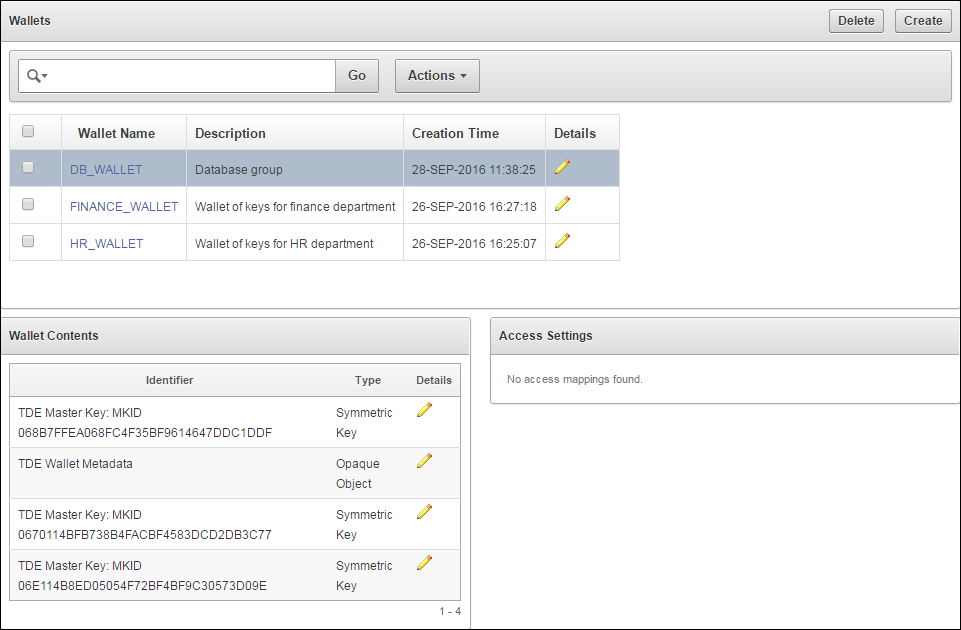
6.1.5 Delete a Virtual Wallet
Deleting a virtual wallet removes the wallet as a container, but does not delete the security objects that were contained in it. These security objects will continue to remain in Key Vault. Endpoints that have downloaded this virtual wallet will continue to retain their local copy.
To delete a virtual wallet:
Parent topic: About Virtual Wallets
6.2 Manage Access to Virtual Wallets from Keys & Wallets Menu
Access control is about deciding which users and endpoints need to share virtual wallets and security objects, and what operations they can perform on those virtual wallets.
6.2.1 How Access to Virtual Wallets from Keys & Wallets Menu Works
You must have access to a virtual wallet or be a key administrator to manage access control for users, endpoints, and their respective groups.
Oracle Key Vault provides two ways to manage access control on virtual wallets for users, endpoints, and their respective groups:
-
From the Keys & Wallets menu, where you select the wallet, and then grant an endpoint, endpoint group, user, or user group access to the wallet.
-
From the Users or Endpoints menu, where you select the user, user group, endpoint or endpoint group, and then grant one of these entities access to the wallet.
This section focusses on managing access to a virtual wallet for users and user groups from the Keys & Wallets menu.
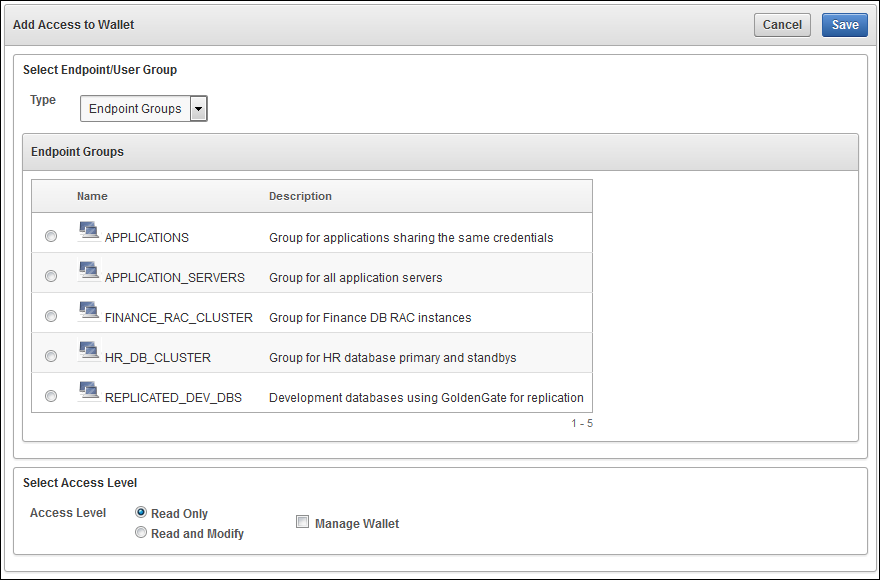
6.2.2 Grant Access to Endpoint Groups, Endpoints, User Groups, and Users
You can choose a virtual wallet and grant endpoint groups, endpoints, user groups, or users Read Only, Read and Modify, and Manage Wallet access levels on the wallet. Once they have access to the wallet, they will have access to all the security objects in the wallet.
To grant access to a virtual wallet:
6.3 Manage Access to Virtual Wallets from User’s Menu
Oracle Key Vault provides two ways to manage access control on virtual wallets for users, endpoints, and their respective groups.
6.3.1 How Access to Virtual Wallets from User's Menu Works
The two menus that you can use are as follows:
-
From the Keys & Wallets menu, where you select the wallet, and then grant an endpoint, endpoint group, user, or user group access to the wallet.
-
From the Users or Endpoints menu, where you select the user, user group, endpoint or endpoint group, and then grant one of these entities access to the wallet.
This section focuses on managing access to a virtual wallet for users and user groups from the Users menu.
See Also:
Parent topic: Manage Access to Virtual Wallets from User’s Menu
6.3.2 Grant a User Access to a Virtual Wallet
To grant a user access to a virtual wallet:
See Also:
Parent topic: Manage Access to Virtual Wallets from User’s Menu
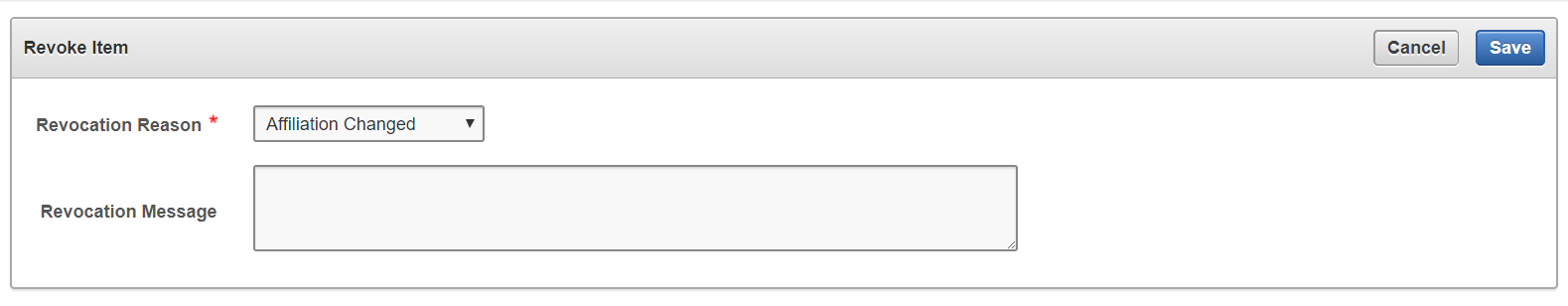
6.3.3 Revoke User Access from a Virtual Wallet
Parent topic: Manage Access to Virtual Wallets from User’s Menu
6.3.4 Grant a User Group Access to a Virtual Wallet
When you grant a user group access to a virtual wallet all members of the group will have access to the security objects within the wallet.
To grant a user group access to a virtual wallet:
Parent topic: Manage Access to Virtual Wallets from User’s Menu
6.3.5 Revoke User Group Access from a Virtual Wallet
You can remove user group access to a virtual wallet as follows:
Parent topic: Manage Access to Virtual Wallets from User’s Menu
6.4 Manage State of a Security Object
You can set the start date for a security object to become active, or deactivate it. You can also change the state of some virtual wallet security objects as needed.
6.4.1 Activate a Key or Security Object
Currently, only keys uploaded via a third-party KMIP client can be in a Pre-Active state and have the Activation date set. For all other keys the Activation Date is system generated and cannot be set.
Most keys are in Active state when they are created. However you can set the Process Start Date for a key to be used for securing data, later than its creation date as follows:
- Log in to the Oracle Key Vault management console as a user who has the Read and Modify access on this key.
- Select the Keys & Wallets tab.
- Select the All Items menu and then click the edit pencil icon corresponding to the item, whose start date you want to set.
- On the Item Details page for the item, set the Process Start Date to the desired date.
- Click Save.
Parent topic: Manage State of a Security Object
6.4.2 Deactivate a Key or Security Object
- Log in to the Oracle Key Vault management console as a user who has the Read and Modify access on this key.
- Select the Keys & Wallets tab.
- Select the All Items menu and then click the edit pencil icon corresponding to the item to be deactivated.
- On the Item Details page for the item, set the Date of Deactivation to the date by which you want the key to be deactivated.
- Click Save.
Parent topic: Manage State of a Security Object
6.4.3 Revoke a Key or Security Object
When you revoke a key, its state transitions to Deactivated or Compromised, and the key should no longer be used to encrypt new data.
However, deactivated keys may be downloaded and used to decrypt old data.
Parent topic: Manage State of a Security Object
6.4.4 Destroy a Key or Security Object
When a key is no longer used or compromised in some way you might want to destroy it.
Note:
Meta data for destroyed keys and security objects are kept in Key Vault even after they have been destroyed.To destroy a key:
- Log in to the Oracle Key Vault management console as a user who has the Read and Modify access on this key.
- Select the Keys & Wallets tab.
- Select the All Items menu and then click the edit pencil icon corresponding to the item, whose start date you want to set.
- On the Item Details page for the item, click Destroy.
- Click Save.
Parent topic: Manage State of a Security Object
6.5 Manage Details of Security Objects
After you create a virtual wallet and add security objects to it, you can search the virtual wallet for the security objects contained in it. You can add new security objects to the virtual wallet, or delete security objects from them. You can modify the contents of a virtual wallet at any time according to your specific needs.
Security objects are managed by Key Vault administrative users with a clear separation of duties. You must be an administrative user with the Key Administrator role to manage wallet privilege on the virtual wallet containing the security objects. A user with the Audit Manager role can view security objects, but cannot modify them, whereas security objects are not even viewable to a user with the System Administrator role.
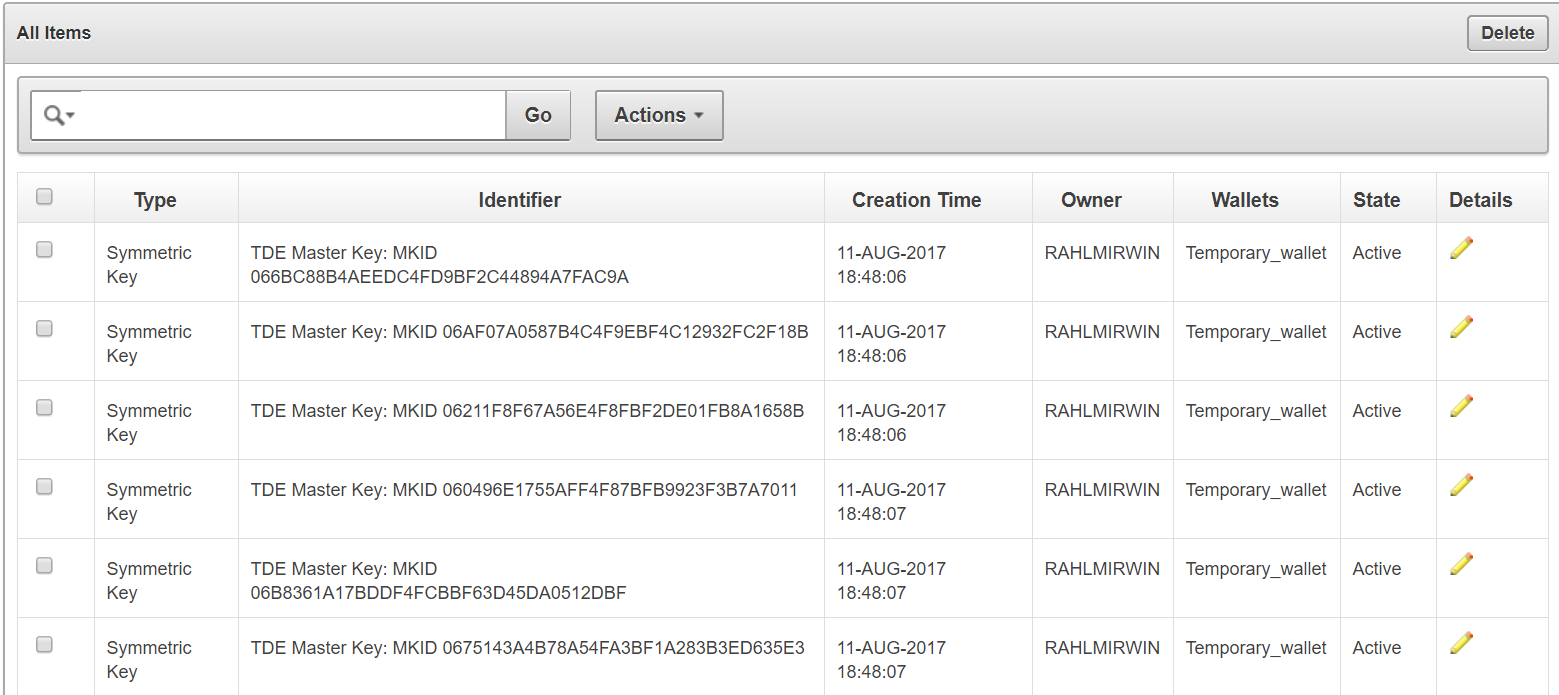
6.5.1 Search for Security Object Items
The term item refers to a single security object managed by Oracle Key Vault, such as an encryption key, keystore, certificate, password, or opaque object.
To search for items:
See Also:
Parent topic: Manage Details of Security Objects
6.5.2 View Details of a Security Object
An administrative user with the Key Administrator role can view, add, and modify the details of a security object from its corresponding Item Details page. Item details are attributes of a specific security object and depend on the type of security object.
To view the attributes of a security object from the Item Details page:
-
Log in to the Oracle Key Vault management console as a user with the Key Administrator role or as a user with access to the virtual wallet.
-
Click the tab Keys & Wallets.
The Wallets page appears.
-
Click All Items in the left sidebar.
The All Items page appears displaying all the security objects in Key Vault.
-
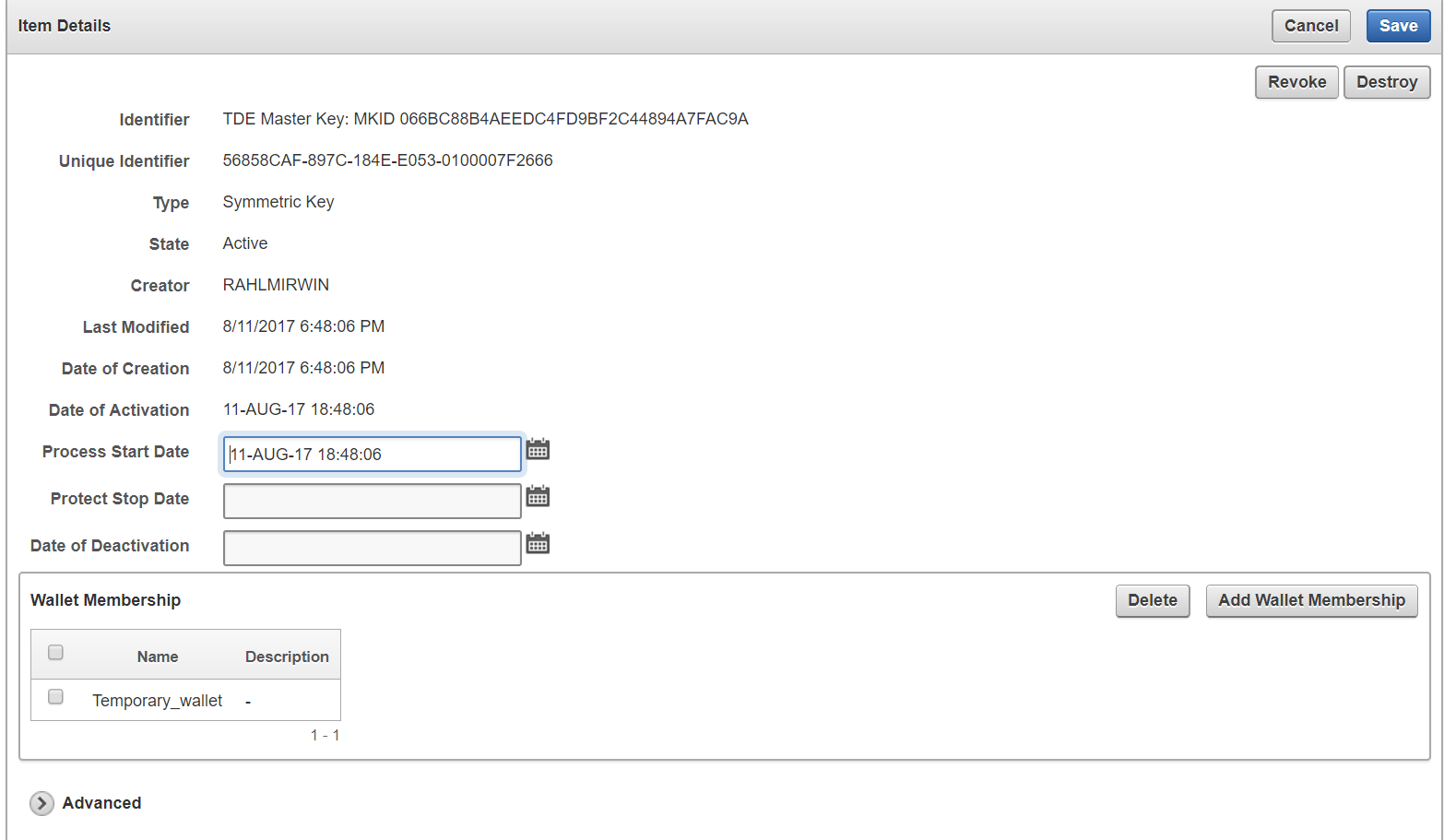
Click the pencil icon in the Details column corresponding to the security object. The Item Details page appears displaying the attributes of the security object.
You can set the dates when the security object should be deactivated or not used on the Item Details page. The attributes shown in Item Details depends on the type of security object. The attributes for a Symmetric Key are different from those of Private Key or Opaque Object.
You can revoke or destroy a security object, and add or remove it to and from a wallet from the Item Details page.
The Wallet Membership pane in the Item Details page allows you to add or delete the security object to or from a wallet.
The Item Details page contains the following attributes:
-
Identifier: A summary description to help identify the item to the user. For example, if the item is a TDE master key, the Identifier shows the prefix TDE Master Key followed by the identifier used by the database to identify the key.
-
Unique Identifier: This is a globally unique ID that identifies an item.
-
Type: Indicates the object type of the item. Valid values are Symmetric Key, Private Key, Template, Opaque Object, Certificate, and Secret Data.
-
State: Indicates the state of items. Values are as follows:
-
Pre-active: The object exists but is not yet usable for any cryptographic purpose.
-
Active: The object is available for use. Endpoints should examine the Cryptographic Usage Mask attribute to determine which uses are appropriate for this object.
-
Deactivated: The object is no longer active and should not be used to apply cryptographic protection (for example, encryption or signing). It may still be appropriate to use for decrypting or verifying previously protected data.
-
Compromised: The object is believed to be compromised and should not be used.
-
Destroyed: The object is no longer usable for any purpose.
-
Destroyed Compromised: The object was compromised and subsequently destroyed. It is no longer usable for any purpose.
-
-
Creator: The endpoint that created the security object.
-
Last Modified: The date last modified.
-
Date of Creation: The date created.
-
Date of Activation: The date of activation.
-
Process Start Date: The date when the key may start to be used to encrypt data. It can be equal or later than the Activation Date but cannot precede it.
-
Protect Stop Date: When this date is passed, the key should not be used to encrypt any more data. It cannot be later than the Deactivation Date.
-
Date of Deactivation: The date of deactivation.
-
-
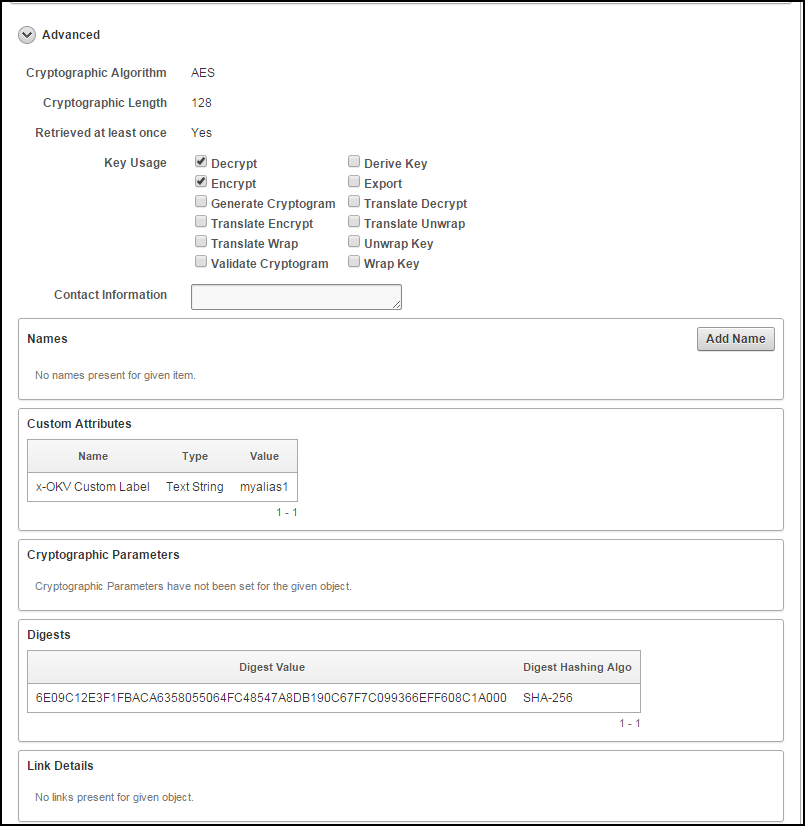
Click Advanced to view the cryptographic attributes of the security object.
Attribute information and queries may vary depending on the item type. These are some attributes:
-
Cryptographic Algorithms: The encryption algorithm used by the item
-
Key Usage: Operations that the key can be used for
-
Names: Labels attached by a user or endpoint to identify the key
-
Custom attributes: Additional attributes defined by the endpoint and not interpreted by Oracle Key Vault
-
Cryptographic Parameters: Optional parameters for the encryption algorithm used by the item, such as block cipher mode and padding method
-
Digests: Digest values of the security object
-
Link Details: Links to related objects
-
See Also:
Key Management Interoperability Protocol Specification Version 1.1
Parent topic: Manage Details of Security Objects
6.5.3 Add or Modify Details of a Security Object
To modify the attributes of a security object you must be a user with the Key Administrator role, or you must have Read and Modify access on the security object.
You can get Read and Modify access on a security object in two ways:
-
You own the security object.
-
You have access to a wallet that contains the security object.
To modify details of a security object:
Parent topic: Manage Details of Security Objects