3 User Interface
This chapter describes how to work with the Oracle Communications Operations Monitor web user interface.
General
This section provides an introduction to the web interface, requirements, and frequently used interface elements of Operations Monitor.
Requirements
Operations Monitor runs in any major web browser without extra plug-ins or add-ons.
Note:
Operations Monitor does not require Flash, Java or Microsoft Silverlight.The following list contains the web browsers in which we regularly test the web interface:
-
Internet Explorer: version 8 or higher.
-
Firefox: 1.5 or higher running on any operating system (Windows, Mac, Oracle Linux).
-
Safari: any version, including Safari for the iPad.
-
Google Chrome: any version.
-
Opera: 9 or higher running on any operating system (Windows, Mac, Oracle Linux).
In order to use the web interface of Operations Monitor, you must enable Javascript. It is recommended that you enable HTTP cookies for features such as remembering login credentials and the state of tables.
Interface Arrangement
On the left side of the Operations Monitor web user interface is the navigation pane. This navigation bar allows access to many of the features of Operations Monitor.
The right side of the Operations Monitor menu bar displays your username, which contains a list with following options (see Figure 3-1):
-
My Profile for user settings.
-
Settings for administrative features.
-
License for the Oracle Communications Session Monitor license terms.
-
About the product for the Operations Monitor copyright information.
-
Help for access to the Operations Monitor online manual.
-
Setup to access the Session Monitor Platform Setup Application.
-
Logout to sign out.
Language Selection
The right side of the Operations Monitor menu bar contains the selected language code, as shown in Figure 3-2. From the locale list, select the language to display in Operations Monitor.
Panels
When you click an element in the navigation pane, a panel appears in the center of the browser window. This panel is a user interface element that displays data.
Many panels can be added to your dashboard for at-a-glance viewing. For more information, see "Dashboard".
To collapse panels and display titles only, you can click the up-arrow in the upper-right hand corner.
Another common user interface element is the tab panel. An instance of this element is depicted in Figure 3-3.
Tooltips and Help
In the title bar of each panel is a gray i-symbol. This is the information box. When you hover over the information box, a question mark symbol appears and a tooltip provides a brief description of the panel. When you click the information box, the corresponding section of the user manual appears in a new browser window or tab describing the panel and its functions.
Other user interface elements support tooltips. Hovering over an element with the mouse pointer often brings up a small box explaining the element underneath.
Windows
You may encounter modal windows overlaid on the user interface, similar to the windows of your desktop environment. These windows can be dragged by their title bar, and closed by clicking on the x-symbol or pressing the ESC key. These windows also contain Help and Close buttons at the bottom. The Help button opens the online Help in a new window, describing the current page and its functionality.
Refresh Button
Some areas of the interface contain a Refresh button that controls the update interval for the content of the page, panel, or section. It is identified by a circle of dots (flashing during refresh). Click the button once to refresh the corresponding content. It also contains a drop-down list to set the interval for the Auto Refresh as shown in Figure 3-4.
Tables
The tables used in the Operations Monitor user interface offer some features to make the data most useful to you.
To adjust tables, hover above a column header. A down-arrow appears on the right side of the column header. To access the table menu, click the down arrow. The table menu options may differ depending on the data presented in the table.
Filters
Some tables support filters. If a table column can be filtered, the column menu contains a Filter submenu as illustrated in Figure 3-5.
Below are possible options in the filters sub menu (depending on the column type):
-
String Filter
Filters the table to display rows that contain the entered value as a sub-string. The input value is not exclusive. This filter menu provides a text field for entering the string.
-
Numeric Comparison Filter
Restricts the table to rows where the comparison of the column value with the entered numeric results is 'true'. This filter menu provides three fields, one for each of the supported operators (>, <, =). The = field cannot be used simultaneously with any of the other fields.
-
Date Comparison Filter
Restricts the table to rows where the column value in the selected date range. This filter menu provides three items for choosing a date (Before, After, On). With Before and After you can select the rows where the timestamp of the column values lies before and/or after the chosen day. With On you can select the rows of only the chosen day.
-
List Filter
Restricts the table to rows where the column values contains the selected value. This filter menu provides a list of possible values, which you can choose by selecting or deselecting the corresponding check box.
You can choose to hide certain columns in each table. Every column drop-down menu contains a Columns submenu that lists all available columns for this table. Select or deselect the check box to the left of each entry to show or hide the corresponding column.
Note the paging toolbar at the bottom of tables as illustrated in Figure 3-6. The presence of this toolbar means that the table offers page-wise access to its data. The paging toolbar displays the total number of pages, and to the right, the total number of items in the table.
Quick User Inspection
Tables such as Recent calls, Registrations, and the user table in User Devices have context menu entries to quickly trace or track a user (see Figure 3-7). You can right-click on a table row to track or trace the user (in the Recent calls table, you can quickly inspect both the caller and the callee). For more information, see "Recent Calls", "Registrations" and "User Devices".
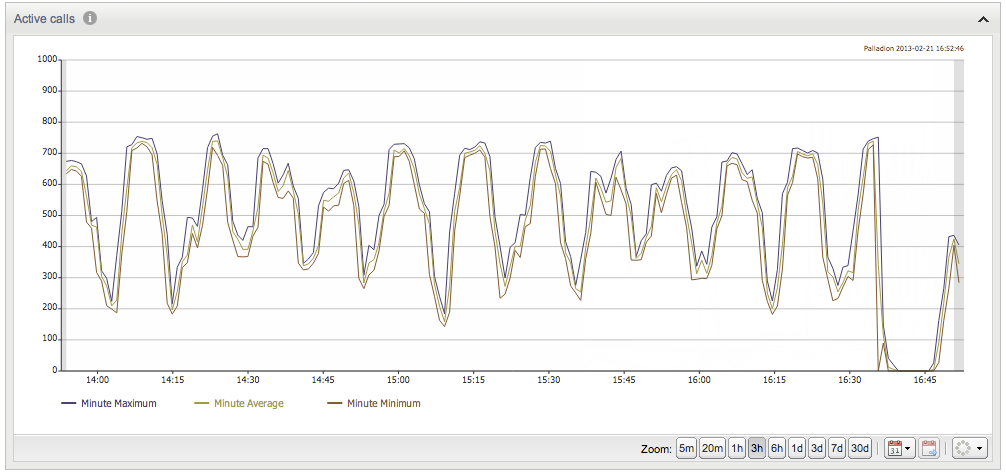
Charts
You may encounter metric charts that display values of a numeric property over a certain time span. Metric charts provide two important features:
-
Adjusting the temporal resolution.
-
Panning of the visible portion along the time line.
A basic metric chart is shown in Figure 3-8:
Adjusting the temporal resolution can be achieved using the Zoom buttons in the bottom-right corner of the chart. The buttons correspond to resolutions of five minutes to thirty days.
Operations Monitor's time-lined charts can be updated by clicking the Refresh button. This button also offers Automatic Refresh functionality from the button's drop-down list. For more information, see "Refresh Button".
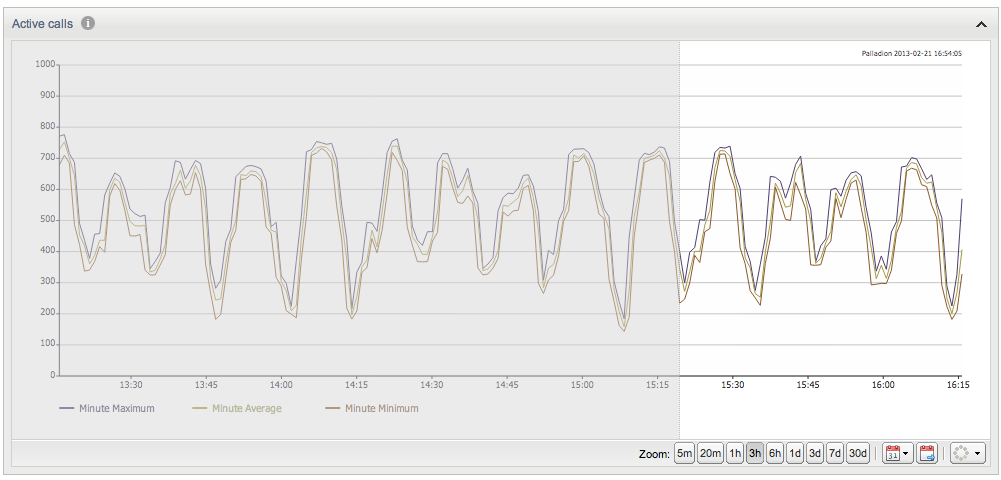
Panning
To pan the chart, click and drag the mouse pointer inside the chart itself. When you click the chart and drag it to the right, the visible area will be shifted further left (further in the past) on the time line. When you drag it to the left, the visible area is shifted further right (nearer to the present) on the time line. While dragging, a gray overlay indicates the direction of the chart, and how far on the spectrum you are dragging. Panning is shown in Figure 3-9.
Note:
Panning stops the automatic refresh of a chart. Automatic refresh is re-enabled after clicking on the Go to now button at the bottom of the chart.Working with Message Flows
A message flow is a diagram of a call event or a registration event. The message flow displays the network devices involved in the call event or registration event and the protocol messages that have been exchanged between the network devices. For more information on how to configure the hosts on which the network devices run, see "Platform Devices".
Displaying a Message Flow
To display a message flow of a call event or a registration event:
-
In a web browser, log in to Operations Monitor.
The Operations Monitor window appears.
-
In the navigation pane under Operations, do one of the following:
-
To display a message flow for a call event:
-
Click Calls.
The Calls page opens in the main display.
-
In the Recent calls table, right-click the row for which to display the call event's message flow and select Message flow.
The Message Flow for Call: caller and callee window appears.
where caller is the number that initiated the call and callee is the call number that received the call.
Note:
Message flows for a call event can also be displayed by right-clicking on the call row and selecting Message flow in the Calls going through this device tab on the Devices page.
-
-
To display a message flow for a registration event:
-
Click Registrations.
The Registrations page opens in the main display.
-
In the Registrations table, select a registration event for which to display a registration message flow.
-
From the Registrations table tool bar, click the Message flow button.
The Registration registration_number window appears.
where registration_number is the number of the registration event.
-
-
-
Press the ESC key, which closes the message flow window.
Arranging Message Flows
In order to compare the network devices and protocol messages contained in multiple call events or registration events, you can open multiple message flows to view side-by-side in the same browser window, or you can open multiple message flows to view side-by-side in multiple browser windows.
To adjust the message flow window to fit in your browser screen, view a message flow in a new browser window, resize the message flow window, or view more of the message flow, do one or more of the following:
-
To adjust the width of the sequence diagram within the message flow window. In the message flow window's toolbar, click the Zoom in or Zoom out icons accordingly.
-
To resize the message flow window. In the message flow window's title bar, toggle between the Maximize and Minimize icon, or expand or contract the message flow window's borders.
-
To view more of the message flow without resizing the message flow's window. Inside the message flow window, drag the message flow, or use the message flow window's scroll bar.
-
To view the message flow in another browser window. In the message flow window's toolbar, click the Open in a new window button.
-
To refresh the message flow window. In the message flow window's toolbar, click the Refresh button. For more information, see "Refresh Button".
Customizing the Display of Contents within Message Flows
The contents displayed in the sequence diagram, protocol messages, and network devices within the message flow are customizable.
To customize the display of contents within message flows:
-
Verify that the message flow is displayed.
-
In the message flow window's toolbar, select the View menu.
-
From the View menu, select or de-select one or more of the following check boxes:
-
Pin Devices
When enabled, the devices are always visible at the top of the scrolling area.
-
Unwind messaging
By default, each network device appears only once and a transaction arrow is drawn for each message that passes between the hosts. When several messages are exchanged between two particular network devices, it becomes difficult to distinguish the call legs. When enabled, each call leg is drawn separately, which results in a wider diagram. Hosts that appear multiple times contain a number suffix, which is the number of times the host appears.
-
Resolve IP addresses
When enabled, Operations Monitor creates a reverse DNS lookup on the IP addresses of the network devices.
-
Duplicates
For retransmissions, only one SIP message appears. Enable this option to display all duplicate messages.
-
Transport protocol
When enabled, the message flow displays the transport protocol (TCP or UDP).
-
IP addresses
When enabled, the message flow displays the IP addresses for the source and destination of the message.
-
MAC addresses
When enabled, this option displays the MAC addresses for the source and destination of the message. In a scenario where one server is realized by several machines, this can be used to determine which machine was used to process the request.
-
OPC/DPC
When enabled, this option displays the originating point code (OPC) and the destination point code (DPC) for the source and destination of the message.
-
Codecs
When enabled, the message flow displays the media codecs of the caller and the callee. If the codecs are the same for the both the caller and the callee after the INVITE transaction is completed, the codecs are grouped.
-
Absolute Time
By default, the information below a transaction arrow displays the time that has passed after the first message was seen. When enabled, the date and time are displayed for each transaction arrow.
-
Media
When enabled, protocol messages for media transport, such as RTP, are displayed in addition to the signal.
Note:
For some protocols, the raw message is not available. -
DTMF Events
When enabled, protocol messages for RTP events of the type DTMF are visible. The DTMF event will show the name and code of the tone. For tones 0-9 the name and the code are the same.
Example
DTMF Event '2' (2) DTMF Event '#' (11)
Requires the View DTMF tones permission to be visible. See "User Permissions".
-
SIP URIs
When enabled, the transaction arrows display the recipient's URI.
-
Hide SIP Methods
This submenu allows you to hide certain types of SIP messages based on their method. For example, enabling OPTIONS will remove all SIP messages from the diagram that have the method OPTIONS.
-
MEGACO
This submenu allows you to hide selected MEGACO message properties.
-
-
Press the ESC key, which closes the message flow window.
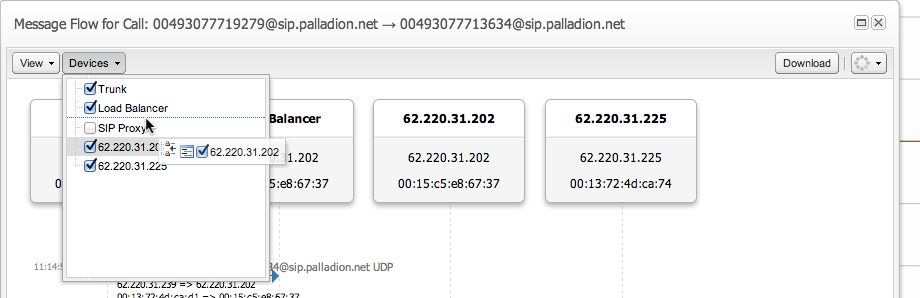
Customizing the Visibility and Position of Network Devices within Message Flows
By default, all networking devices are displayed in the message flow in the order of the call event transaction or the registration event transaction. The visibility and position of a network device is customizable in a message flow.
To customize the visibility and position of network devices within message flows:
-
Verify that the message flow is displayed.
-
In the message flow window's toolbar, select the Devices menu.
-
Do one or both of the following:
-
To hide a network device, deselect the check box of the network device you want to hide. Alternatively, select the check box of the network device you want to display.
-
To reposition a device in the sequence diagram, select the check box row of the network device you want repositioned and drag the check box row to the position you require. See Figure 3-10.
-
-
Press the ESC key, which closes the message flow window.
Viewing Individual Protocol Messages
Protocol messages of the sniffed packet can be viewed and saved. For more information on saving a protocol message, see "Saving a Message Flow as an HTML File".
Each protocol message is numbered in brackets in the order of the call event transaction or the registration event transaction between the network devices.
To view individual protocol messages:
-
Verify that the message flow is displayed.
-
In the message flow, click the message type you wish to view, which appears above the message transaction arrow.
The Message transaction_number window appears.
where transaction_number is the number associated with the order of the transaction between the network devices.
-
(Optional) Resize, or move the protocol message by dragging the title bar of the protocol message's window to the required position within the message flow.
-
When you have finished viewing the protocol message, click the Close icon in the protocol message window's title bar.
-
Press the ESC key, which closes the message flow window.
Note:
The maximum number of messages for a flow is limited. You can change the limit value in System Settings. For more information, see "System Settings".Viewing Call Event ISUP Protocol Messages
When a call event contains ISDN User Part (ISUP) binary content, you can view the ISUP binary content as human readable text.
To view call event ISUP protocol messages:
-
Verify that the message flow is displayed.
-
In the message flow, click the message type identified by [1], which appears above the message transaction arrow.
The Message transaction_number window appears.
-
Scroll down the protocol message until you see the Content-Type header. Do one of the following:
-
If the Content-Type header's value contains either, multipart/mixed and one of the multiple parts is application/ISUP, or application/ISUP, go to step 4.
For example:
Content-Type:application/ISUP;boundary=A6B35A2329D0F2312C9F4692 -
If the Content-Type header's value does not contain either, multipart/mixed and one of the multiple parts is application/ISUP, or application/ISUP, close the protocol message and click the next message.
-
-
Scroll down the protocol message until you see the decode ISUP body link.
-
Click the decode ISUP body link.
The ISUP binary content is decoded into human readable text and an ISUP message contained in Message transaction_number window appears.
-
When you have finished viewing the ISUP message, click the Close icon in the ISUP protocol message window's title bar.
-
When you have finished viewing the protocol messages, click the Close icon in the protocol message window's title bar.
-
Press the ESC key, which closes the message flow window.
Saving a Message Flow as an HTML File
You can save a message flow as an HTML file on your computer to view at another time or share with others. This is important when diagnosing issues.
To save a message flow as an HTML file:
-
Verify that the message flow is displayed.
-
In the message flow window's toolbar, click the Download button.
The Save As dialog box appears.
-
Browse to the directory in which you want to save the HTML file.
-
(Optional) In the File name text box, enter a file name for the HTML file.
By default, HTML files are named message-flow.html.
-
Click Save.
-
Press the ESC key, which closes the message flow window.
Saving a Call Event Message Flow as a PDF File
You can save a call event message flow as a PDF file.
To save a call event message flow as a PDF file:
-
In the navigation pane under Operations, click Calls.
The Calls page opens in the main display.
-
In the Recent calls table, right-click the row for which to create a call event PDF report file and select PDF report.
The Create Report window appears.
By default, all the Report Content options are selected.
-
In the Report Content section, deselect the options you do not require in your report. Do not deselect the Messages option.
-
(Optional) In the Additional Info section's Report Comment (optional) text box, enter information about the report.
-
(Optional) In the Additional Info section's, Filename (optional) text box, enter a file name for the report.
By default, PDF files are named CallReport-YMDHMS-callid.pdf
where
-
YMDHMS is the syntax for year, month, day, hour, minutes, and seconds that the file was generated.
-
callid is the call event's identifier.
-
-
Click the Create button.
The Save As dialog box appears.
-
Browse to the directory in which you want to save the call event PDF file and click Save.
-
Click the Cancel button, which closes the Create Report window.
Note:
Because the decoded binary ISUP content can be lengthy, only two levels of information are displayed in the PDF report.Dashboard
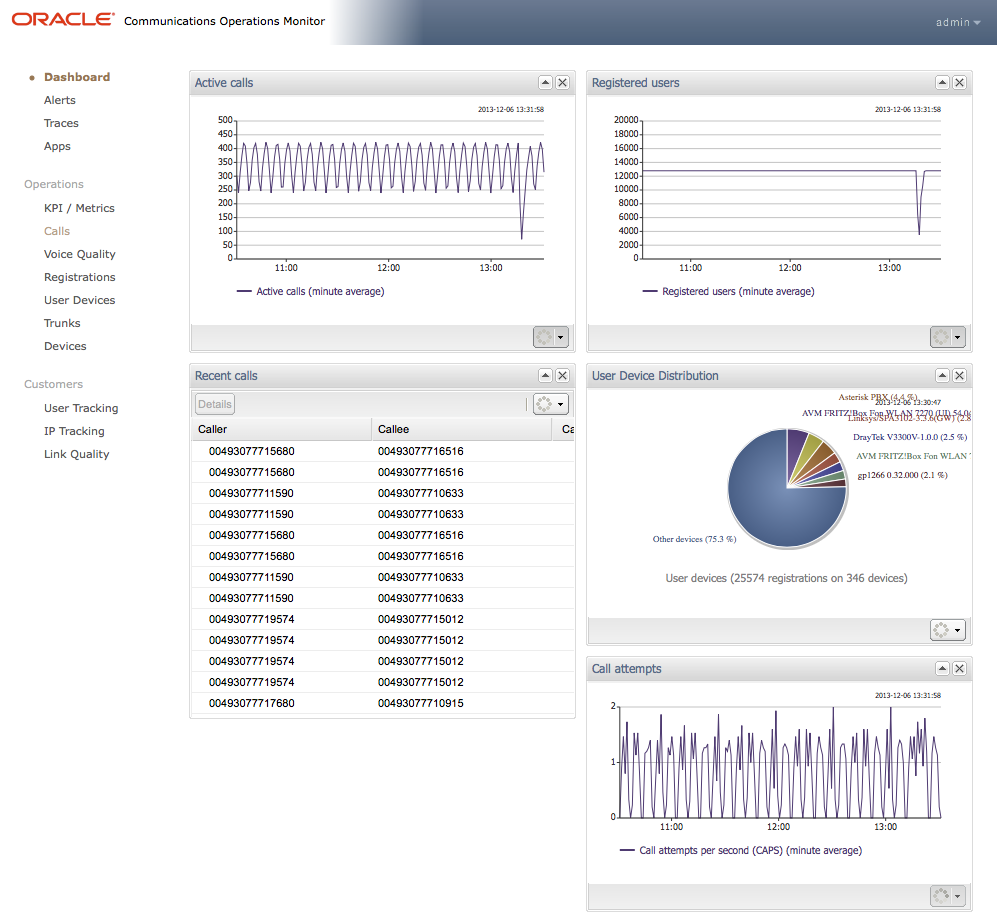
The Dashboard is Operations Monitor's flexible entry page (as illustrated in Figure 3-11). It allows you to view the information at a glance that is most important to you. Reduced panels are defined for many features of Operations Monitor, and can be displayed on the Dashboard.
Types of panels that may appear on your dashboard are:
-
Counter chart (see "KPI/Metrics")
-
Recent calls (see "Calls")
-
Registrations (see "Registrations")
-
User devices pie chart (see "User Devices")
-
Voice Quality (VQ) overview chart (see "Voice Quality")
-
Alerts (see "Alerts")
These panels come in variants. For example, you can display a Recent calls table only for call events passing through a certain platform device.
Configuring Your Personal Dashboard
Each Operations Monitor user can define their own Dashboard layout. The default Dashboard layout contains four panels:
-
Registrations Counter
-
Active Calls Counter
-
Recent Calls table
-
User Devices Chart
Panels can be added, removed, and rearranged.
Adding a Dashboard Panel
You can add Dashboard panels from the Dashboard page or from the Operations Monitor pages, which provide information that you would like to display on the Dashboard.
To add a panel directly from the Dashboard page, right-click on the Dashboard to get a context menu, and choose Add a panel.... A pop-up window appears that provides dashboard panel options.
To add a dashboard panel from another window in Operations Monitor, click the Show in Dashboard icon (shown in Figure 3-12). This button is located throughout the Operations Monitor web interface. For more information, please refer to the documentation sections referenced beside the dashboard panel types listed above.
Alerts
Operations Monitor has a notification system to warn you of important events called alerts. You can prioritize alerts and configure them to trigger certain actions. The Alerts page displays all alerts that have been raised. The following alert types are supported:
-
Generic Metrics
Statistics metrics exceed or fall below certain thresholds.
-
Device/Tag Metrics
Statistics metrics exceed or fall below certain thresholds.
-
Metric Baseline Derivation
Allows comparison between a current KPI value and a previously captured KPI value. An alert is generated based on the difference between the two values.
-
User Devices
A certain user device is detected by the system.
-
Voice Quality
The quality for a percentage of calls falls beyond a MOS threshold.
-
Device Monitoring
A device is down.
-
Limits
An internal soft limit within Operations Monitor was passed.
-
Phone Number
A certain phone number placed or received a call.
The Alerts table displays notifications. You can create or edit an alert definition in the Alert Definitions tab.
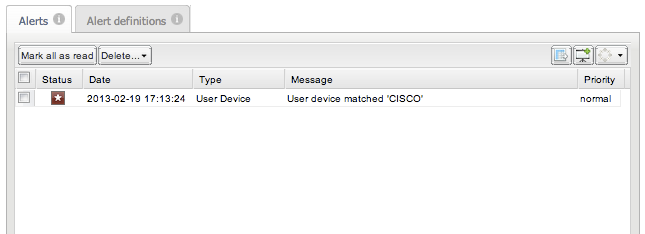
Alerts Table
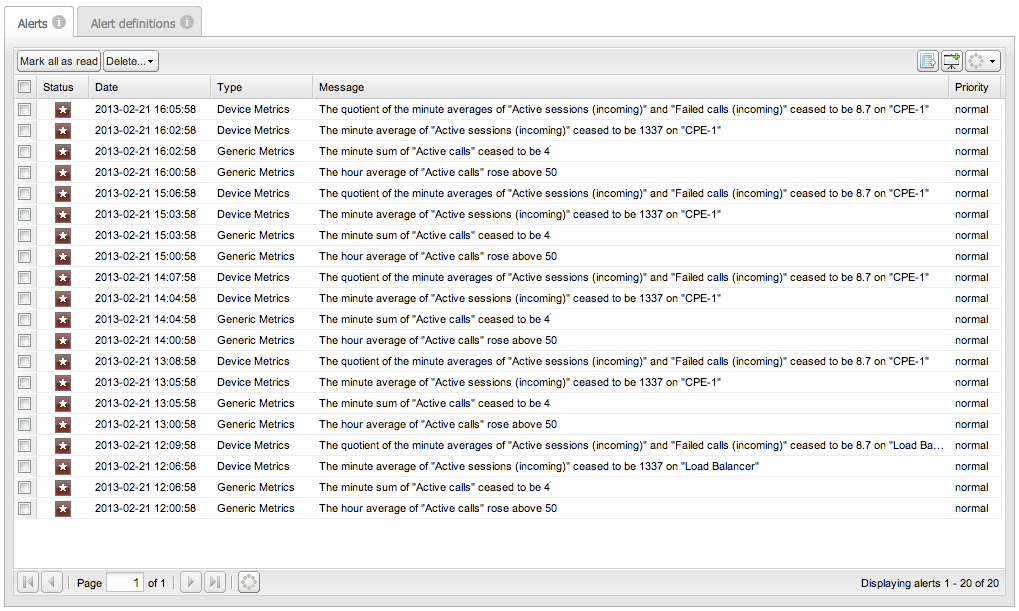
Click Alerts in the navigation pane to display the alerts panel, as shown in Figure 3-13.
Table 3-1 lists the Alerts panel table columns:
Table 3-1 Alerts Panel Columns
| Column | Description |
|---|---|
|
Status |
Unread alerts are marked with a red icon. Clicking on the icon toggles the status as read/unread. |
|
Date |
The date when the alert was raised. |
|
Type |
The type of the alert. This columns allows for easy filtering. |
|
Message |
The alert message explains why the alert was raised. |
|
Priority |
Setting priority ranks the alerts. The alert entries with high priority are highlighted by a red background. Low priority alerts are displayed in a lighter color. |
When you double-click an alert, a small window appears with an extended message and an offer to mark the alert as read.
The Mark all as read button respects table filters, and can be helpful when treating similar alerts. For example, to mark all statistic threshold alerts, enable Filters in the Type column and click Mark all as read. The Delete drop-down menu allows you to delete either:
-
Selected alerts (the check box in the first column is marked).
-
Alerts marked as read.
-
All alerts.
Upon initial installation of Operations Monitor, the only alerts raised are related to licenses. You must create Alert definitions to receive further notifications.
Note:
To avoid being inundated with alerts (for example Number of active calls exceeded 5000), Operations Monitor creates duplicate alerts only when the previous one has been deleted, marked as read, or when 1 day has passed (recurrence threshold adjustable via recurrent alerts threshold. For more information, see "Recurrent Alerts Threshold").Alert Definitions Tab
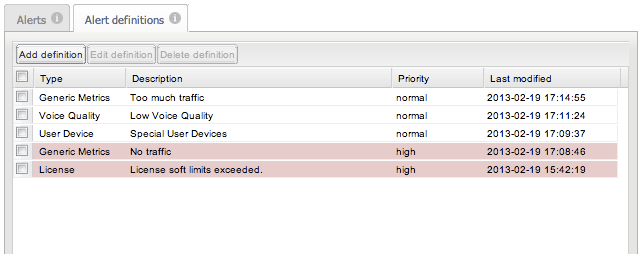
Alert definitions establish which events on the system raise a notification. On the Alerts page, click the Alert Definitions tab to see a table of all definitions that have been created.
Creating Alert Definitions
To create an alert definition:
-
Click Add definition, which starts the Alert Definition wizard.
-
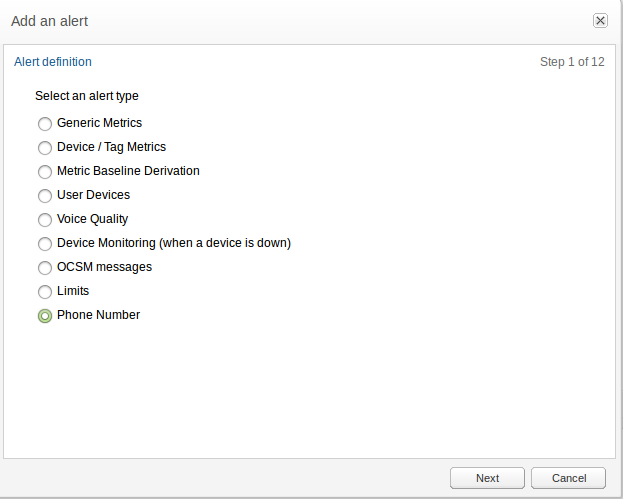
In the Add an alert page, select an alert type (see Figure 3-15). This also determines if parameters are required.
-
Optionally, parameters have to be provided that tell Operations Monitor when to raise an alert and of that type. Some alert types do not require parameters.
-
If desired, set actions to execute when the alert is raised, for example, to send an e-mail. For more information see, "Actions".
-
Assign an alert name and priority for the notifications raised according to this definition. For more information, see "Alert Name and Priority".
-
Click Finish to save the alert definition.
Operations Monitor raises an alert whenever the specified event occurs.
Actions
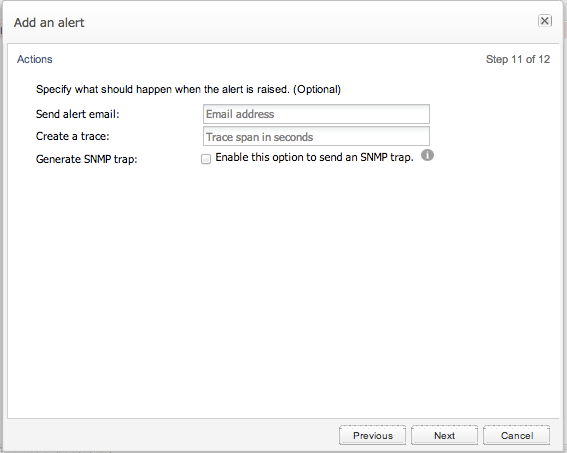
For all alerts additional actions can be configured (see Figure 3-16). All actions are optional and can be combined.
-
Send alert e-mail
Sends an e-mail about the alert to the specified address. An SMTP access needs to be configured before. Please check the PSA manual for more details about configuring SMTP.
For most alert types, a deep link to the source of the alert can be provided in the alert e-mail. To receive this link, you must first configure the External IP/hostname. For more information, see "External IP/hostname."
-
Create a trace
Creates a trace of the current SIP traffic when the alert is raised. Enter an appropriate time span (in seconds) for packet capture to tell Operations Monitor how far back in time the trace should go.
-
Generate SNMP trap
Sends an SNMP trap to a configured SNMP target. When this is enabled, Operations Monitor alerts can be tracked and analyzed by an SNMP manager in the network. For more information, see "SNMP Options".
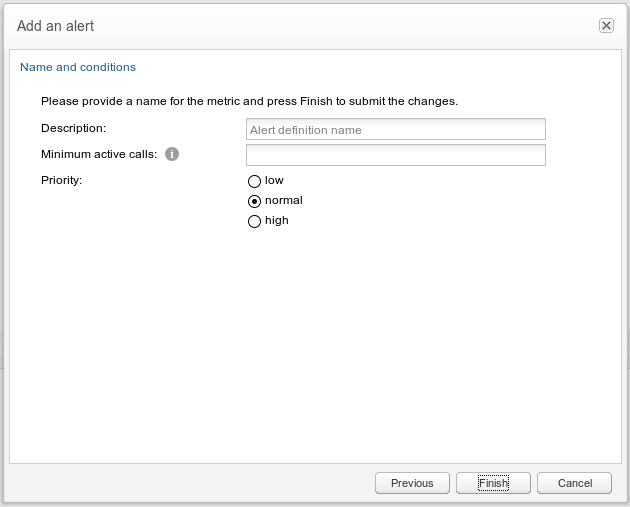
Alert Name and Priority
For all alerts a name and priority needs to be provided (see Figure 3-17). It is also possible to define a minimum number of active calls to trigger the alert.
Editing and Deleting Alert Definitions
To edit a definition, perform one of the following actions:
-
Select the entry and click Delete.
-
Double click the entry.
To delete a definition, select the entry and click Delete definition. Once an alert has been deleted, Operations Monitor no longer raises a notification for this definition.
Parameters
The following sections describe the various parameters for each alert type.
Statistics Metrics
Alerts can be defined with either one or two metrics. The metrics are compared to a threshold value using a comparison operator (for example =, <, > or not).
When you input one metric, the alert is triggered if the metric exceeds or falls below the given threshold value, depending on the comparison operator provided. This is suited for alerts such as 'The number of registered users exceeds 20,000.' In this example, an alert is sent when the number of registered users exceeds 20,000. If you would like a second alert to notify you if the value falls below 20,000, you must create a second definition.
When you provide two metrics, Operations Monitor considers the difference of the two metric values to a given threshold value, and therefore allows for more sophisticated alerting scenarios. For example, a statistics metric value deviates too much from its average value.
The example in Figure 3-18 shows the metric configuration of the alert scenario 'The number of registered users fell by 1,000 in the last week'. For using this alert definition, you must set the regular value for the metric as well as its average metric. For more information, see "KPI/Metrics".
Figure 3-18 Defining Alerts Based on Metrics
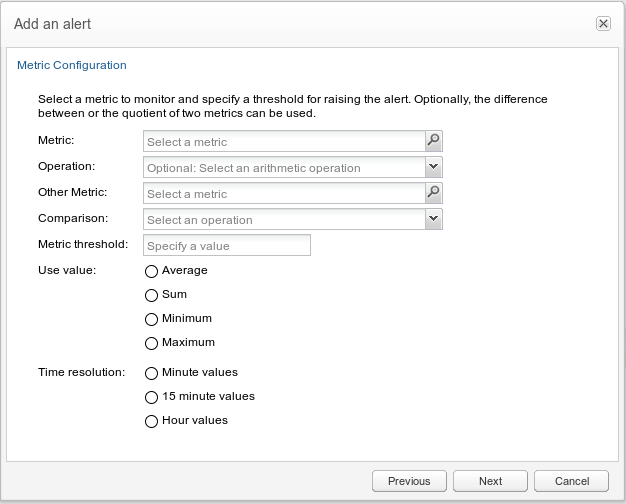
Description of ''Figure 3-18 Defining Alerts Based on Metrics''
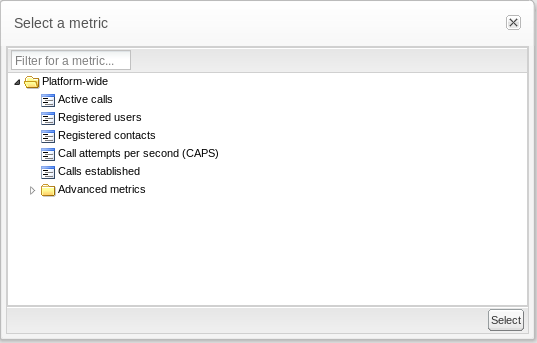
Clicking on the Choose button for a metric displays the metrics dialog box (see Figure 3-19), where you can choose a metric:
Device Metrics for All Trunks
It is possible to define an alert that triggers when the value of a metric exceeds or falls below a given threshold on any trunk. You must select the alert type Device Metrics for All Trunks. The metric in question needs to be added to all trunks first. For more information, see "Adding Metrics to All Trunks".
If the metric exceeds or falls below the threshold on multiple trunks, the alert is triggered for each trunk and will thus have multiple independent entries on the alerts table.
User Agent
Operations Monitor keeps track of all user devices that are registered on the platform and raises an alert depending on the desired option:
Highlighted Devices
If a list of disapproved devices has been configured in User Devices, and Operations Monitor notices a user device from that list, an alert is sent. This option is recommended if User Devices is frequently updated so that the list can be centrally managed there. For more information, see "User Devices".
Alert on match
This option is intended for a more ad-hoc tracking of user devices. A regular expression can be entered to raise an alert when a matching user device is found. For every expression to track you need to add another alert definition.
Figure 3-20 shows an example configuration for detecting any AVM or Linksys devices.
Figure 3-20 Defining Alerts Based on Devices
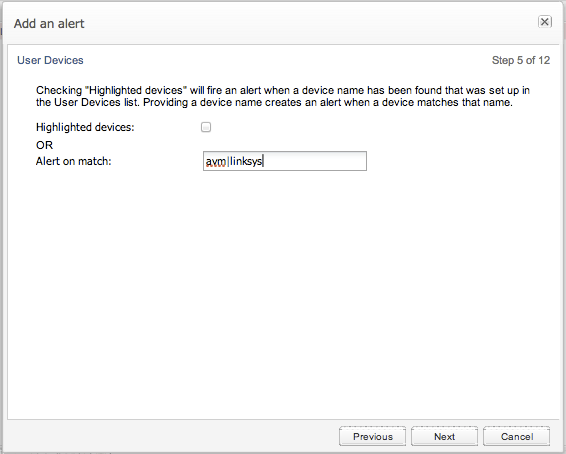
Description of ''Figure 3-20 Defining Alerts Based on Devices''
Device Monitoring
This alert type refers to Device Monitoring and does not need additional parameters. Whenever a monitored device is down, an alert is raised. Only one alert definition of this type is needed. For more information, see "Device Monitoring".
Phone Number Alerting
The Phone Number type provides the possibility to alert on a specific phone number. The alert will be triggered when a call to or from a configured number is detected. To use this alert type the user needs to have the Number Alerting permission (see Figure 3-21). Without this permission the Phone Number option will not be shown.
Phone numbers are configured in preferred number format. If the Use User Domains system setting is set to true then a phone number should be provided as a SIP user, that is, with a domain name: for example, 00403077811-call@example.com. If not, the phone number should be provided without domain (and without the @ sign). For more information, see "Use User Domains".
Note:
Only one number per alert can be defined. No wild cards are allowed.A good strategy for setting up a number alert is to place a phone call to the desired number and look in the calls grid for the callee to get the exact SIP address/phone number to use for the alert definition.
The search for predefined phone numbers happens two times per minute, with calls that are at least 10 seconds old (in the early stages of a call, not all information needed is available). This means that a call in best case is detected after 10 seconds, in worst case after 40 seconds.
Figure 3-21 Configuring the Phone Number for Alerts
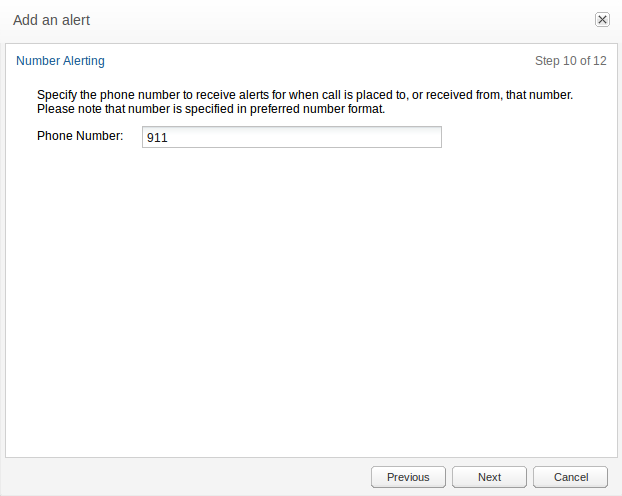
Description of ''Figure 3-21 Configuring the Phone Number for Alerts''
Traces
The Traces page allows you to capture, store and download packet traces of the SIP traffic. Downloads are done in the industry-standard PCAP format, which contains the complete messages as monitored on the network.
The PCAP file format can be interpreted by most of the available protocol analyzers, including open source tools. Any stored message contains TCP/UDP headers, an IP header, and layer 2 headers, as well as the time stamp at which Operations Monitor received it. All messages are written to the disk before any processing is performed. The filter defining, which traffic the traces, can be set in the Signaling Protocols section in the Platform Setup Application.
Packets are captured from the moment a trace is started. With Operations Monitor, you can also trace events in the recent past. For more information, see "Packet Buffer".
You can restrict traces to a single SIP user or an IP.
Note:
If you restrict the traces to a SIP user, only UDP packets will be captured.Packet Buffer
In order to create traces with packets received prior to the current time, Operations Monitor keeps an in-memory, rotating raw packet buffer with all the messages captured. The default size of this buffer is 1 GB including the message overhead. The buffer size system option allows you to change the size of this buffer.
The Traces page contains three panels: the first shows information about the raw packet buffer, the second panel can be used for creating a new trace, and the third panel shows the currently running and finished traces.
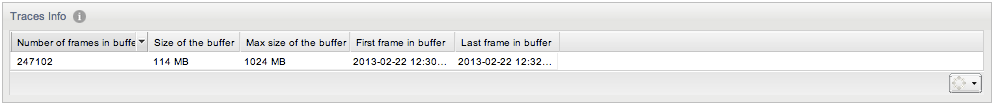
Traces Info Panel
The Traces Info panel displays details about the state of the raw packet buffer:
-
Number of frames in buffer
The total number of frames that are currently in the in-memory buffer.
-
Size of the buffer
The total size in bytes of the raw packet buffer, including the overhead needed for indexing the messages.
-
Max size of the buffer
The maximum size in bytes to which the buffer can grow. When this limit is reached, old packets are discarded.
-
First frame in buffer
The timestamp of the oldest packet still in the buffer. Traces cannot capture messages before this point in time.
-
Last frame in buffer
The timestamp of the newest packet in the buffer. This information is provided in order to approximate the capacity of the buffer in seconds.
Signaling Traffic Capture Panel
The Signaling Traffic Capture panel allows you to capture signaling traffic and save the data to a PCAP file. If you click Start Capture immediately, a trace begins with default settings. This provides a trace for activity in the last five minutes including non-call related messages such as OPTIONS and PUBLISH.
This panel allows you to configure time ranges, and filter SIP traffic by user or IP.
You can specify the Start time, End time, and the Filters used for a new trace in the Signaling Traffic Capture panel. Start and end times can either be set relative to the current time or by using absolute times. If the start time lies before the current time, the trace contains packets from the raw buffer. If the end time lies after the current time, the trace is started and write the packets received until the selected end time or until the user stops the trace.
Note:
Traces are limited to durations up to 24 hours. Set traces to a duration shorter than 24 hours. After 24 hours of capturing, no further packets are traced.A Filter restricts captured messages to a single user, a single Operations Monitor network port, an IP address, or a combination of these. The User field has a live auto-complete feature: while typing the first characters of a user name or number, Operations Monitor suggests user names and numbers containing those characters from the set of known users.
The number of traces running simultaneously is limited to 3 by default and are configurable depending on the license. If the limit is exceeded, an error message is displayed.
Examples
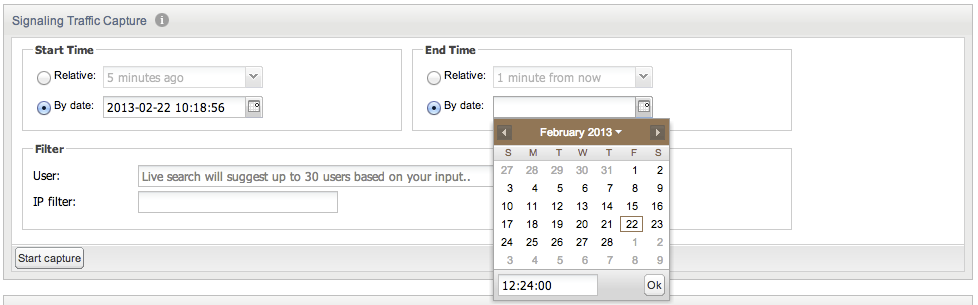
Figure 3-23 shows a new trace created for a past transaction using absolute times (from 10:18:56 to 12:24:00). No filter is selected: all messages received by Operations Monitor in the given time interval are included in the trace.
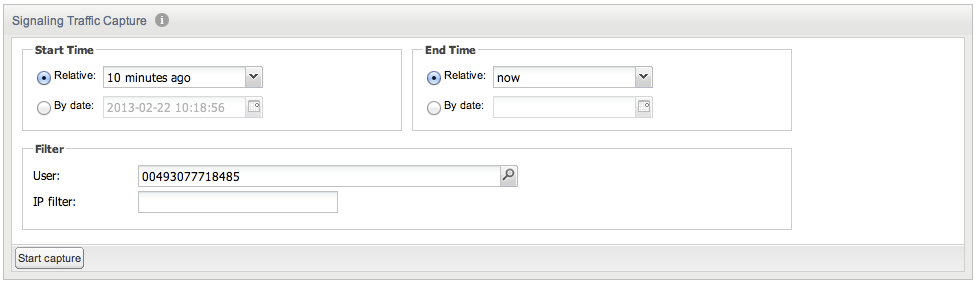
In Figure 3-24, a new trace is created for all messages from user '00493077718485' from the last 10 minutes. Here, we use a relative start and end time.
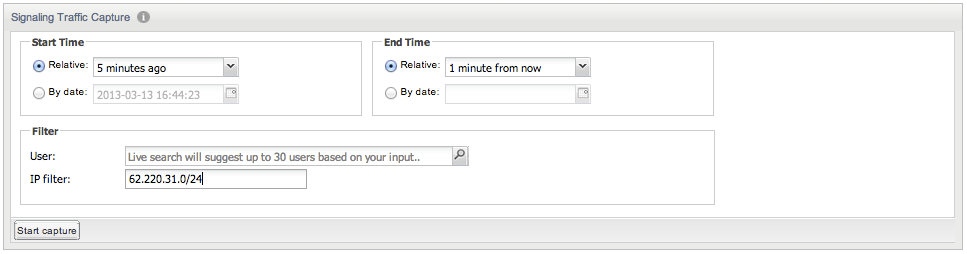
Figure 3-25 illustrates a trace created for all messages, which have either the source or destination IP address in the 62.220.32.0/24 network range. The IP filter field accepts both a host IP address in dotted format (a.b.c.d) or a sub-network address with the net mask appended(a.b.c.d/e).
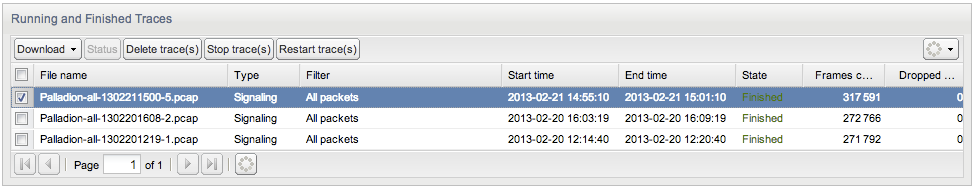
Running and Finished Traces Panel
The last panel on the page lists all traces that are stored on the disk and offered for download. Traces that are currently in progress are also listed and may be stopped before their scheduled end time. Figure 3-26 illustrates the panel.
The following information is presented for every trace:
-
File name
The name of the PCAP file on disk. This will be also used as the proposed filename when downloading the trace.
-
Filter
Short description of the filter used for the trace.
-
Start time
The date and time the packet trace began. This can lie before the time at which the user has requested the trace.
-
End time
The date and time when the trace was stopped, or the time it is scheduled to stop in the case of running traces.
-
State
The current state of the trace is one of the following:
-
Running: Trace is in progress.
-
Finished: Trace has finished normally because its end time was reached.
-
Stopped: Trace was stopped by the user before its end time was reached.
-
Error: Trace failed to complete, possibly due to an internal error or an Operations Monitor core restart.
-
-
Frames captured
The number of packets stored in the trace. For running traces, this value is the number of packets written thus far.
-
Size
The size in bytes of the capture file.
All columns of in the Running and Finished Traces can be sorted. For example, you can click the Size column to sort the traces by size.
By default, the table is refreshed every five seconds, which can be changed using the Refresher's drop-down menu at the top right corner of the table.
When you select a trace from the list, the following actions are available from the toolbar above the table:
-
Download
Downloads the selected trace. This only works when selecting one trace at a time. Traces are compressed in a .gzip format in order to speed up the download.
-
Delete trace(s)
Deletes the selected traces from Operations Monitor storage.
-
Stop trace(s)
Stops the selected traces if they are currently running.
-
Restart trace(s)
Starts a trace with the same parameters as the selected trace, but with the time shifted to present. This only works for traces with relative start and end times.
Note:
The total size of storage space, which all traces can use is limited. When the space is full, the oldest trace is automatically deleted. The default value of this limit is set to 40 GB on a standard Operations Monitor server, with the traces being stored in a compressed form.Packet Inspector
The Packet Inspector page allows you to examine and download arbitrary network traffic captured on the probes. Downloads are done in the industry-standard PCAP file format, that contains the complete messages as monitored on the network.
Most of the available protocol analyzers can interpret the PCAP file format, including open- source tools. Any stored message contains the full raw frame including IP and TCP/UDP headers, as well as the timestamp when the message was received.
The filter for Packet Inspector determines the traffic that is captured and available for searching. You set this filter in the Signaling Protocols page in Platform Setup Application on the Probe. For increased system performance, it is important that this filter restrict the traffic that is captured and is comparable to the default filter. The Probe captures the packets from the moment the it is set up. See Session Monitor Installation Guide for more information about signaling protocol filters.
If you use Packet Inspector for recording media, you need to include media packets in the filter. Media packets are initially stored on the Probe machine until the Probe sends the packets to the Mediation Engine when a user downloads the media to a PCAP file. You need to ensure that there is sufficient disk space on the Probe machine for storing media.
Packet Inspector Page
The Packet Inspector page consists of a form where you specify the search parameters and a panel listing the preview of the results of a search.
Query Panel
The Query panel displays a chart that shows the amount of traffic received every two seconds. You can use the chart for selecting a time range. Operations Monitor searches the packets captured during the selected interval of time.
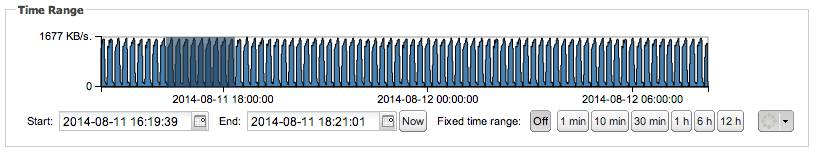
To select a time range, you can select, move, or resize a time range selection in the chart or use the controls to select a specific start and end date or a fixed time range (see Figure 3-27). If you select a start and end date, the selection on the chart changes accordingly. If you select a fixed time range, the start and end dates and the selection on the chart changes accordingly.
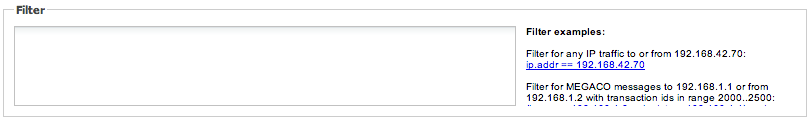
To filter the result set further, you can enter filters in the Filter text field. On the right of the Filter text field (see Figure 3-28) are some filter examples. See "Query Examples" for additional usage examples.
Search Results Preview Panel
The Search Results Preview panel shows a preview of the search results (see Figure 3-29). You can sort the preview using each column. To browse the packet data details, expand its corresponding row. To download the complete set of search results, click the Download PCAP file button on the bottom of the panel.
Figure 3-29 Search Results Preview Panel
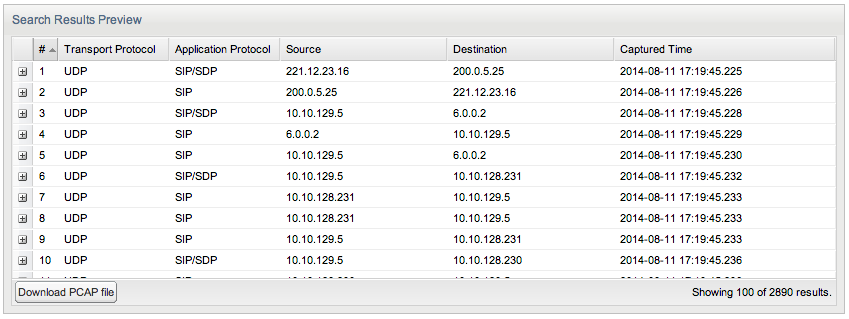
Description of ''Figure 3-29 Search Results Preview Panel''
Query Examples
Query examples are Wireshark syntax.The following are examples of queries that can be used in the Filter text field:
-
Filter for any IP traffic to or from 192.168.42.70:
ip.addr == 192.168.42.70
-
Filter for MEGACO messages to 192.168.1.1 or from 192.168.1.2 with transaction ids in range 2000..2500:
(ip.src == 192.168.1.2 or ip.dst == 192.168.1.1) and megaco.transid > "2000" and megaco.transid < "2500"
-
Filter for ISUP to the device with point-code 1111 calling number 1234567:
mtp3.dpc == 1111 and isup and e164.called_party_number.digits == "1234567"
Not all filter expressions work with fragmented packets. To get all packets, use an expression like:
sip.Call-ID == "910820420140505605616932@172.19.235.6" || ip.flags.mf==1
Using a query to filter for media packets can decrease system performance; therefore, it is not recommended.
Note:
The total size of the storage space that Packet Inspector can use is limited. The default value of this limit is 90% of the disk space for each configured probe. Furthermore, there is a limit of three concurrent queries for each product instance running.To improve the speed of Packet Inspector queries, use the following syntax to search for IP or ports:
tcpdump: [bpf filter]
You can use this syntax to search only for IP or ports and without any message content. For examples of BPF filters, see the topic on Filter Syntax in the Oracle Communications Session monitor Installation Guide.
Note:
Searches combining tcpdump/BPF and Wireshark filter language are not supported.Apps
Apps allow you to extend Operations Monitor's reporting capability. You can upload an app to customize the queries and report information provided by Operations Monitor. Operations Monitor provides a number of default apps, which can be accessed on this page. For information on how to develop new extension apps for Operations Monitor, see "Implementing Apps".
Note:
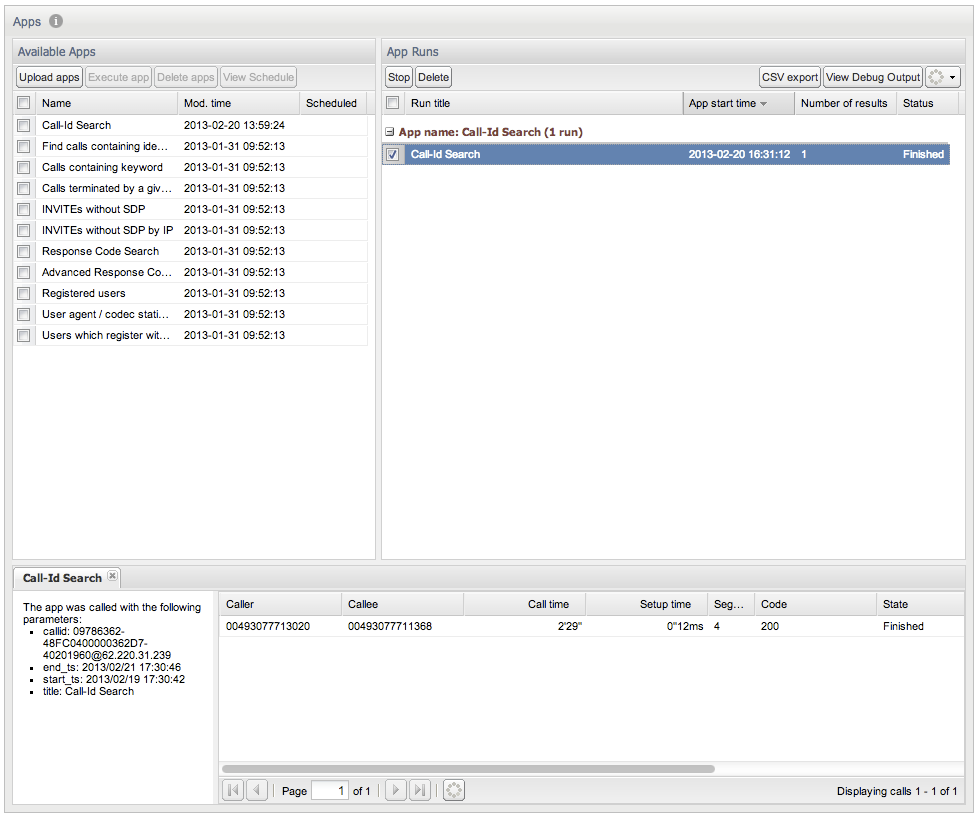
Apps searches are not guaranteed to be real-time without advanced hardware sizing.The Apps page (see Figure 3-30) is divided into three sections:
-
The upper-left area lists Available Apps.
-
The upper-right area displays outputs of previous App Runs.
-
The bottom area displays the results of the selected App Run. It is empty when you first access the page.
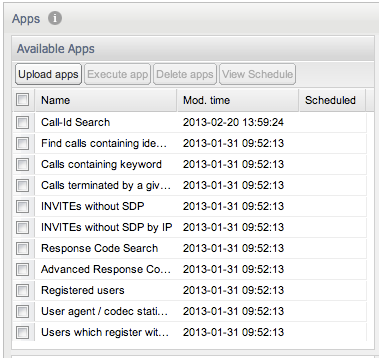
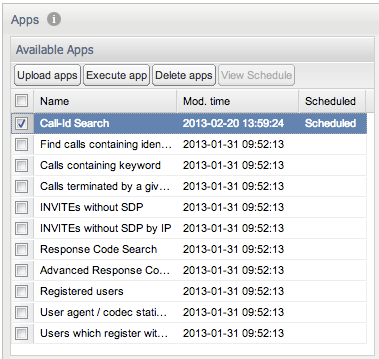
Available Apps
The Available Apps table (see Figure 3-31) contains the columns Name and Mod. time by default. The first column displays a name for each application, the second column displays each apps modification time. The Scheduled column marks apps that are scheduled to run at a certain point in time. Additionally, the Id column can be enabled, which displays a unique identifier for each app. This is useful when you want to access the application using the remote procedure call functionality described in section "Remote App Procedure Calls" of this manual.
Uploading Apps
You can upload new apps to Operations Monitor in the Available apps table. Click Upload app to open a dialog box to search for an app archive on your computer and upload it to Operations Monitor. The procedure for creating an archive is described in the section "Implementing Apps".
Caution:
When creating your own applications, or using third-party applications, test your scripts in a test environment to ensure they are safe before uploading them to your production environment. Applications approved by Oracle are safe to use in your environments. However, non-approved applications could cause security and performance issues. Oracle is not responsible for any loss, costs, or damages incurred from using your own applications, or third-party applications.Running Apps
The Available apps section also allows you to start any app that is already present on the system. Starting an app requires you to enter any parameters that the app defines.
To start an app, select it in the table and click on the Execute app button. A dialog appears that allows you to enter the app parameters. Every app has a title parameter. The sole purpose of the title parameter is to distinguish between different app runs of the same app in the App runs table. Click Execute in the parameter entry dialog to go to the App runs table. Execution also starts when a user double-clicks one of the available apps.
There are limits for simultaneous execution of scripts and for the maximum debug output that an script can generate. They are defined by the Maximum Simultaneous Script Runs and the Maximum Script Output Size system settings. For more information, see "Maximum Simultaneous Script Runs" and "Maximum Script Output Size".
Scheduling Apps
You can also schedule a repeated execution of a given app. For more information, see "Scheduling App Execution".
The table entitled Available apps allows you to delete apps from Operations Monitor. To do this, select the app you want to delete in the table and click the Delete app button. After confirmation, the selected app is deleted from the system.
The View Schedule button displays the scheduling configuration for a given app: the cron expression which determines when this app is triggered, the e-mail address to notify, and the option to attach the result as a csv file.
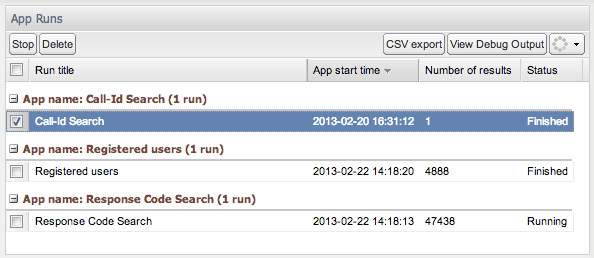
View App Runs
The App Runs table (see Figure 3-32) displays four columns by default:
-
The Run title column displays the Run title parameter that was entered when starting the app.
-
The App start time column displays the start time of the app.
-
The Number of results column displays the number of results that the app reported. This column updates as the app run proceeds.
-
The Status column displays either Starting, Running or Finished depending on whether the app run is still in progress or already finished.
Two other columns can be enabled: the Id column to display the ID of each app run, and App name to show the unaltered name of the app. The Id column is useful when you want to access the results of an app using the remote procedure call functionality. For more information, see "Remote App Procedure Calls".
-
Exporting the App Runs to CSV
The CSV export button lets you download the displayed items as a CSV file.
-
Debug App Run
The View output action opens a window in which the console output of the selected app is shown.
-
Stopping and Removing App Runs
The App Runs table allows you to stop an app run that is still active. To do this, select the app run you want to stop in the table and click the Stop button.
Note:
You can only stop an app run when it is in the Running state.
The App Runs table can also be used to remove app runs from the system. Select an app run in the table and click the Delete... button. You can only delete app runs that are in a Finished state.
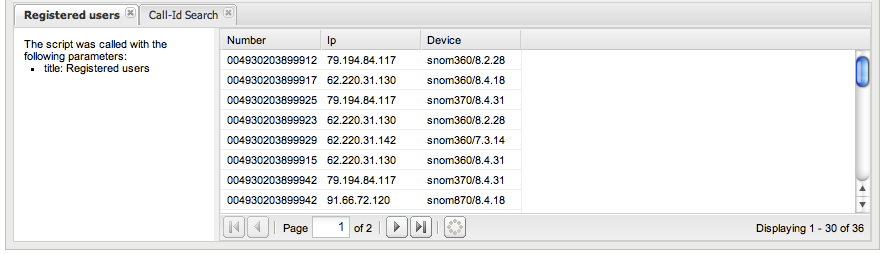
View App Results
The lower portion of the Apps page displays result pages for app runs. The Apps page is empty when you first access it. When you double click an app run in the App Runs table, a new tab containing an app results view appears in the lower area.
App results view consists of a text display, which shows the parameters provided when starting the app, and a table containing the data rows reported by the app. The information in the table depends on the type of app that generated the results. Apps that search for calls use a similar results table to the calls table described in the section "Calls". Similar to the Recent calls table, you can double click on a row to get more detailed call information. This type of results table is shown in Figure 3-33.
The results page varies for each app. Multiple app results can be displayed simultaneously, and a new tab is opened in the lower portion for each.
Scheduling App Execution
Apps can be scheduled to run periodically.
To set up an app schedule:
-
Select the app from Available Apps and click the Execute App button.
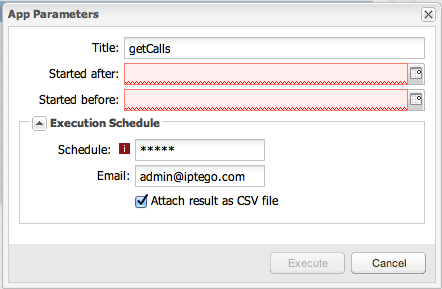
-
In the App Parameters dialog box, click on the Execution Schedule arrow to expand and show the scheduling options (see Figure 3-34):
-
The Schedule itself must be supplied as a cron expression. For more information, see "Cron Expressions".
-
Optionally, an email address can be provided for notification of app completion. The results of the execution may be attached to this email as a CSV file. Each execution of a scheduled app will also always appear in the View App Runs. For more information, see "View App Runs".
-
Multiple schedules can be defined for each app. To avoid schedules with a high frequency monopolizing resources, the system limits the number of stored app runs. This is defined by the Maximum Stored Script Runs system setting. For more information, see "Maximum Stored Script Runs".
Removing an App Schedule
Once a schedule has been set it can be deleted from the schedule list view. Select the app and click the Delete apps button in the Available Apps. Scheduled apps also have the string Scheduled visible in the Scheduled column of this table. For more information, see "Available Apps".
Cron Expressions
Operations Monitor supports cron expressions as a means of defining your app schedules. An expression consists of 5 fields separated by white space that represent a set of times. The first field represents minutes, followed by hours, the day of the month, month, and day of the week. For example:
-
To run an app every minute use this expression:
* * * * * *
-
To run an app every 30 minutes (on the 0th and 30th minute of every hour):
0,30 * * * *
-
And below, every Monday (2nd day of the week) at 1am:
0, 1, 2 * * *
Note:
App results that include data for calls (result type "calls") remain valid and accessible only as long as the calls are accessible in the system. Once the call(s) fall out of Operations Monitor's scope, the app results which reference them will no longer be available.