Release 8.1.6
A76932-01
Library |
Product |
Contents |
Index |
| Oracle Advanced Security Administrator's Guide Release 8.1.6 A76932-01 |
|
This chapter introduces Oracle Advanced Security (formerly Oracle Advanced Networking Option) encryption, integrity, and authentication features. These features are available to network products using Net8, including Oracle8i, Oracle Designer, Oracle Developer, and any other Oracle or third-party products that support Net8.
Topics covered in this chapter include the following:
Oracle Advanced Security (formerly Oracle Advanced Networking Option and Secure Network Services) provides a comprehensive suite of security features to protect enterprise networks and securely extend corporate networks to the Internet. Oracle Advanced Security provides a single source of integration with network encryption and authentication solutions, single sign-on services, and security protocols. By integrating industry standards, it delivers unparalleled security to the Oracle network and beyond.
This section contains the following topics:
Oracle databases power the largest and most popular web sites. Organizations around the world are deploying distributed databases and client/server applications in record numbers, often on a global scale, based on Net8 and Oracle8i. This proliferation of distributed computing has been matched by an increase in the amount of information that organizations now place on computers. Employee records, financial records, product testing information, and other sensitive or critical data have moved from filing cabinets into file structures. The volume of critical or sensitive information on computers has increased the value of data that can be compromised.
The increased distribution of data in distributed environments brings with it serious security threats, including the following:
Distributed environments bring with them the possibility that a malicious third party can execute a computer crime by tampering with data as it moves between sites.
Over the Internet and in Wide Area Network (WAN) environments, both public carriers and private network owners often route portions of their network through insecure land lines, extremely vulnerable microwave and satellite links, or a number of servers, leaving valuable data open to view by any interested party. In Local Area Network (LAN) environments within a building or campus, the potential exists for insiders with access to the physical wiring to view data not intended for them, and network sniffers can be easily installed to eavesdrop on network traffic.
In a distributed environment, it becomes more feasible for a user to falsify an identity to gain access to sensitive and important information. How can you be sure that user Pat connecting to Server A from Client B really is user Pat?
Moreover, in distributed environments, malefactors can hijack connections. How can you be sure that Client B and Server A are what they claim to be? A transaction that should go from the Personnel system on Server A to the Payroll system on Server B could be intercepted in transit and routed instead to a terminal masquerading as Server B.
In a distributed system, users often need to remember multiple passwords for the different applications and services that they use. For example, a developer can have access to an application in development on a workstation, a production system on a mini-computer, a PC for creating documents, and several computers or intranet sites for testing, reporting bugs, and managing configurations.
Users generally respond to managing the passwords of multiple accounts in one of the following ways:
All three strategies severely compromise password secrecy and service availability. Moreover, administration of all these accounts and passwords is complex, time-consuming, and expensive.
Oracle Advanced Security protects against these threats to the security of distributed environments. It provides the following features, each of which is described in this section:
Oracle Advanced Security ensures that data is not disclosed during transmission through the following types of encryption:
RSA encryption is an encryption module that uses the RSA Data Security RC4 encryption algorithm. Using a secret, randomly-generated key unique to each session, all network traffic is fully safeguarded--including all data values, SQL statements, and stored procedure calls and results. The client, server, or both, can request or require the use of the encryption module to guarantee that data is protected. Oracle's optimized implementation provides a high degree of security for a minimal performance penalty. For the RC4 algorithm, Oracle provides encryption key lengths of 40 bits, 56 bits, and 128 bits.
Since the Oracle Advanced Security RSA RC4 40-bit and 56-bit implementations meet the U.S. government export guidelines for encryption products, Oracle provides an export version of the media and exports it to all but a few countries, allowing most companies to safeguard their entire worldwide operations with this software.
The U.S. Data Encryption Standard (DES) is required for financial and many other institutions. Oracle Advanced Security offers a standard, optimized 56-bit key DES encryption algorithm. Due to former U.S. government export restrictions, Oracle Advanced Security also offers DES40, a version of DES that combines the standard DES encryption algorithm with the international availability of a 40-bit key. While DES56 is now exportable, Oracle Advanced Security supports DES40 for backwards compatibility. Selecting the algorithm to use for network encryption is a user configuration option, allowing varying levels of security and performance for different types of data transfers.
|
More Information:
For more information, see Chapter 2, "Configuring Data Encryption and Integrity" and Appendix A, "Data Encryption and Integrity Parameters." |
To ensure that data has not been modified, deleted, or replayed during transmission, Oracle Advanced Security optionally generates a cryptographically secure message digest--through cryptographic checksums using the MD5 algorithm--and includes it with each packet sent across the network.
Moreover, the SSL feature of Oracle Advanced Security allows the use of the Secure Hash Algorithm (SHA). SHA is slightly slower than MD5, but produces a larger message digest to make it more secure against brute-force collision and inversion attacks.
Establishing user identity is of primary concern in distributed environments; otherwise, there can be little confidence in limiting privileges by user. Passwords are the most common authentication method in use, and Oracle Advanced Security integrates with stronger authentication services. Oracle Advanced Security release 8.1.6 provides authentication through Oracle authentication adapters that support various third-party authentication services.
Many Oracle Advanced Security authentication methods use centralized authentication. This can give you high confidence in the identity of users, clients, and servers in distributed environments. Having a central facility authenticate all members of the network (clients to servers, servers to servers, users to both clients and servers) is one effective way to address the threat of nodes on a network falsifying their identities.
Centralized authentication can also provide the benefit of single sign-on for users. Single sign-on allows users to access multiple accounts and applications with a single password, eliminates the need for multiple passwords, and simplifies management of user accounts and passwords for system administrators.
Figure 1-1 shows how a centralized network authentication service typically operates.
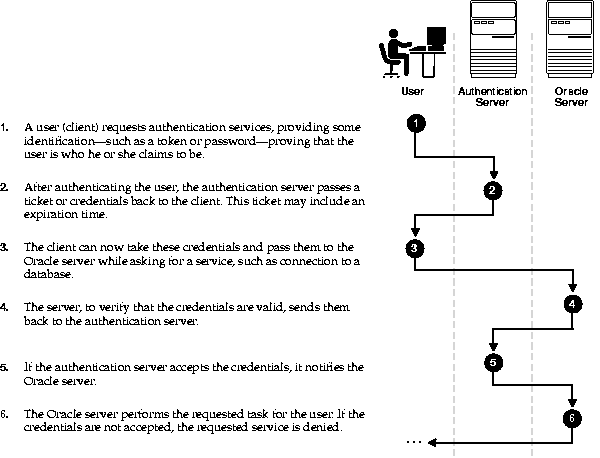
Oracle Advanced Security supports the following authentication methods:
SSL (Secure Sockets Layer) is an industry standard protocol for securing network connections. SSL provides authentication, data encryption, and data integrity, and it contributes to a public key infrastructure (PKI).
The Oracle Advanced Security SSL feature can be used to secure communications between any client and any server. Specifically, you can use SSL to authenticate the following:
SSL features can be used by themselves or in combination with other authentication methods supported by Oracle Advanced Security. For example, SSL can be used with Kerberos, using the encryption provided by SSL in combination with the Kerberos authentication method.
You can configure SSL to require server authentication only, or both client and server authentication.
Remote Authentication Dial-In User Service (RADIUS) is a client-server security protocol that is most widely known for enabling remote authentication and access. Oracle Advanced Security uses this standard in a client-server network environment to enable use of any authentication method that supports the RADIUS protocol. RADIUS can be used with a variety of authentication mechanisms, including token cards, smart cards, and biometrics.
The Oracle Advanced Security support for Kerberos and CyberSafe provides the benefits of single sign-on and centralized authentication in an Oracle environment. Kerberos is a trusted third-party authentication system that relies on shared secrets. It assumes that the third party is secure, and provides single sign-on capabilities, centralized password storage, database link authentication, and enhanced PC security. It does this through Kerberos authentication and through the CyberSafe TrustBroker, a commercial Kerberos-based authentication server.
This authentication method uses a hardware device that looks like a credit card. It has memory and a processor and is read by a smart card reader located at the client workstation.
Smart cards offer the following benefits:
Token cards can provide improved ease-of-use through several different mechanisms. Some token cards dynamically display one-time passwords that are synchronized with an authentication service. The server can verify the password provided by the token card at any given time by contacting the authentication service. Other token cards have a keypad and operate on a challenge-response basis. In this case, the server offers a challenge (a number) that the user enters into a token card. The token card provides a response, namely, another number cryptographically-derived from the challenge, which the user offers to the server.
Token cards offer the following benefits:
You can use SecurID tokens through either the SecurID adapter or through RADIUS.
Identix Biometric Authentication is used on both the clients and Oracle servers to communicate fingerprint-based authentication data between the authentication server and the clients. Other biometric authentication devices that are RADIUS compliant can integrate with Oracle Advanced Security using RADIUS to authenticate Oracle users.
Bull Integrated System Management (ISM) is an offering from Bull Worldwide Information Systems that provides system administrators with a variety of management tools. This authentication method is available on the AIX platform only. See the AIX-specific documentation for more information.
User authorization, already a standard feature of Oracle8i with roles and privileges, is significantly enhanced by using the authentication methods supported by Oracle Advanced Security. For example, on certain platforms such as Solaris, Oracle Advanced Security supports authorization with DCE.
Authorizations are also provided with the Oracle Advanced Security directory integration feature. Oracle Advanced Security can integrate with LDAP version 3-compliant directories. Your Oracle Advanced Security license entitles you to deploy Oracle Internet Directory for user management as well as authorization storage and retrieval. You must license Oracle Internet Directory separately if you intend to use it for additional purposes.
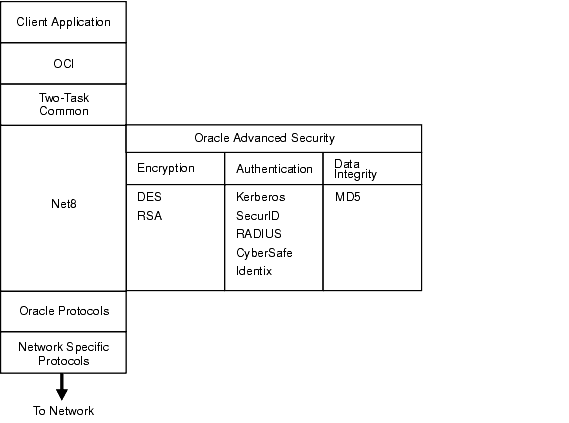
Oracle Advanced Security is an add-on product to a standard Net8 Server or Net8 Client. Figure 1-2 shows the location of Oracle Advanced Security within a typical stack in an Oracle networking environment.
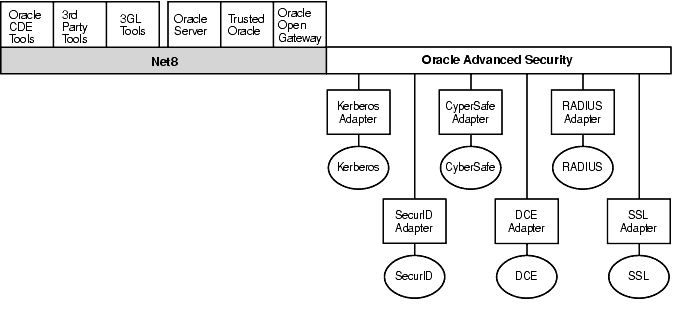
Oracle Advanced Security supports authentication through adapters that are very much like the existing Oracle protocol adapters. As shown in Figure 1-3, authentication adapters integrate below the Net8 interface and allow existing applications to take advantage of new authentication systems transparently, without any changes to the application.
Oracle Advanced Security is fully supported by Oracle Connection Manager, making secure data transfer a reality across network protocol boundaries. Clients using LAN protocols such as NetWare (SPX/IPX), for example, can securely share data with large servers using different network protocols such as LU6.2, TCP/IP, or DECnet. To eliminate potential weak points in the network infrastructure and to maximize performance, Connection Manager passes encrypted data from protocol to protocol without the cost and exposure of decryption and re-encryption.
Oracle Advanced Security is an add-on product to the standard Net8 Server or Net8 Client. It must be purchased and installed on both the client and the server.
Oracle Advanced Security release 8.1.6 requires Net8 release 8.1.6 and supports Oracle8i Enterprise Edition. Table 1-1 lists additional system requirements.
|
Important: Oracle Advanced Security is not available with Oracle8i Standard Edition, nor are any of its components. |
Install Oracle Advanced Security on each client and server where Oracle Advanced Security is required.
Table 1-1 Authentication Methods and System Requirements
This section describes the following parameters that are set when configuring Oracle for network authentication. Specifically, it describes the following tasks:
For information on configuring a particular authentication method, see the method's corresponding chapter in this guide. See also Appendix A, "Data Encryption and Integrity Parameters."
More Information:
The following parameter must be set in the sqlnet.ora file for clients and servers to be able to use an Oracle Advanced Security authentication method:
SQLNET.AUTHENTICATION_SERVICES=(oracle_authentication_method)
For example, the parameter must be set in the sqlnet.ora files on all clients and servers that use the Kerberos Authentication as follows:
SQLNET.AUTHENTICATION_SERVICES=(KERBEROS5)
Oracle Corporation recommends that you add the following parameter to the initialization file used for the database instance when you configure the Oracle authentication method:
REMOTE_OS_AUTHENT=FALSE
If REMOTE_OS_AUTHENT is set to FALSE, and the server cannot support any of the authentication methods requested by the client, the authentication service negotiation fails and the connection terminates.
If the following parameter is set in the sqlnet.ora file on either the client or server side:
SQLNET.AUTHENTICATION_SERVICES=(NONE)
the database attempts to use the provided user name and password to log the user in. However, if REMOTE_OS_AUTHENT is set to FALSE, the connection fails.
Authentication service-based user names can be long, and Oracle user names are limited to 30 characters. Oracle Corporation strongly recommends that you enter a null value for the OS_AUTHENT_PREFIX parameter in the initialization file used for the database instance as follows:
OS_AUTHENT_PREFIX=""
To create a user, launch SQL*Plus and enter the following:
SQL> CREATE USER os_authent_prefix username IDENTIFIED EXTERNALLY;
When OS_AUTHENT_PREFIX is set to a null value (" "), enter the following to create the user king:
SQL> CREATE USER king IDENTIFIED EXTERNALLY;
The advantage of creating a user in this way is that the administrator no longer needs to maintain different user names for externally-identified users.
|
More Information:
Refer to Oracle8i Administrator's Guide and Oracle8i Distributed Database Systems. |
Oracle Applications support Oracle Advanced Security encryption and data integrity. However, because Oracle Advanced Security requires Net8 to transmit data securely, Oracle Advanced Security external authentication features are not supported by some parts of Oracle Financial, Human Resource, and Manufacturing Applications when they are running on the Windows platform. The portions of these products that use Oracle Display Manager (ODM) do not take advantage of Oracle Advanced Security, since ODM does not use Net8.
|
|
 Copyright © 1999 Oracle Corporation. All Rights Reserved. |
|