Release 8.1.6
A76932-01
Library |
Product |
Contents |
Index |
| Oracle Advanced Security Administrator's Guide Release 8.1.6 A76932-01 |
|
This chapter covers the following topics:
This section discusses and compares the various encryption algorithms used in both domestic and export editions of Oracle Advanced Security.
The following topics are included in this section:
Due to export controls placed on encryption technology, Oracle Advanced Security is available in a domestic edition and an export edition.
Table 2-1 provides a summary of domestic and export algorithms.
Table 2-1 Differences Between Domestic and Export Editions
In certain circumstances, a special license can be obtained to export the domestic version. Special licenses can allow banks, wholly owned subsidiaries of U.S. corporations, and e-commerce venders to obtain the domestic edition. Export and import regulations vary from country to country and change from time to time, so it is important to check on current restrictions in your area.
Oracle Advanced Security for international use provides the DES (Data Encryption Standard) algorithm for customers with specialized encryption needs. DES has been a U.S. government standard for many years and is sometimes mandated in the financial services industry. In most specialized banking systems today, DES is the algorithm used to protect large international monetary transactions. Oracle Advanced Security allows this high-security system to be used to protect any kind of application, without any custom programming.
In a secure cryptosystem, the plaintext (a message that has not been encrypted) cannot be derived from the ciphertext (the encrypted message) except by using the secret decryption key. In a symmetric cryptosystem, a single key serves as both the encryption and the decryption key. DES is a secret-key, symmetric cryptosystem: both the sender and the receiver must know the same secret key, which is used both to encrypt and decrypt the message. DES is the most well-known and widely-used cryptosystem in the world.
The DES40 algorithm, available in every release of Oracle Advanced Security, Oracle Advanced Networking Option, and Secure Network Services, is a variant of DES in which the secret key is preprocessed to provide 40 effective key bits. It was designed for use by customers outside the U.S. and Canada who wanted to use a DES-based encryption algorithm while there were stronger encryption export laws. Now, in Oracle Advanced Security release 8.1.6, both DES40 and DES are available internationally. DES40 is still supported to ensure backward-compatibility for international customers.
The RC4 algorithm, developed by RSA Data Security Inc., has quickly become the de-facto international standard for high-speed data encryption. Despite ongoing attempts by cryptographic researchers to crack the RC4 algorithm, the only feasible method of breaking its encryption known today remains brute-force, systematic guessing. RC4 is a stream cipher that operates at several times the speed of DES, making it possible to encrypt even large bulk data transfers with minimal performance consequences.
RC4 is a variable key-length stream cipher. Oracle Advanced Security release 8.1.6 for domestic use offers an implementation of RC4 with a 128 bit key. This provides strong encryption with no sacrifice in performance when compared to other key lengths of the same algorithm.
Oracle has obtained a special license to export the RC4 data encryption algorithm with a 40-bit or 56-bit key to virtually all destinations where other Oracle products are available. This allows international corporations to safeguard their entire operations with fast, strong cryptography.
The Oracle Advanced Security Secure Sockets Layer (SSL) feature allows the use of triple-DES (3DES). This form of encryption involves encrypting input data three times, which can occur in a number of ways. A potential drawback of triple-DES, depending on the speed of the communications channel, is that it requires more computing power than regular DES.
Encryption of network data provides data privacy, so no unauthorized party is able to view the plaintext data as it passes over the network. Oracle Advanced Security also provides protection against two other forms of attack: data modification attack and replay attack.
In a data modification attack, an unauthorized party on the network intercepts data in transit and changes parts of that data before retransmitting it. An example of this is changing the dollar amount of a banking transaction from $100 to $10,000.
In a replay attack, an entire set of valid data is repeatedly interjected onto the network. An example would be to repeat a valid bank $100 account transfer transaction several times.
Oracle Advanced Security uses a keyed, sequenced implementation of the MD5 message digest algorithm to protect against both of these forms of active attack. MD5 creates a checksum that changes if the data is altered in any way. This protection is activated independently from the encryption features provided, so you can enable data integrity with or without enabling encryption.
The Oracle Advanced Security SSL feature allows the use of either Message Digest 5 (MD5) or Secure Hash Algorithm (SHA-1) for data integrity.
The secrecy of encrypted data depends on the existence of a secret key shared between the communicating parties. Providing and maintaining such secret keys is known as key management. In a multi-user environment, secure key distribution may be difficult; public-key cryptography was invented to solve this problem. Oracle Advanced Security uses the public-key based Diffie-Hellman key negotiation algorithm to perform secure key distribution for both encryption and data integrity.
When encryption is used to protect the security of encrypted data, keys should be changed frequently to minimize the effects of a compromised key. For this reason, the Oracle Advanced Security key management facility changes the session key with every session.
Oracle Advanced Security includes the Diffie-Hellman key negotiation algorithm to choose keys both for encryption and for data integrity.
A key is a secret shared by both sides of the connection and by no one else. Without the key, it is extremely difficult to decrypt an encrypted message or to tamper undetectably with a crypto-checksummed message.
The purpose of Authentication Key Fold-in encryption enhancement is to defeat a possible "person-in-the-middle attack" on the Diffie-Hellman key negotiation. It strengthens the session key significantly by combining a shared secret that is known only to the client and the server with the original session key negotiated by Diffie-Hellman.
The client and the server begin communicating using the session key generated by Diffie-Hellman. When the client authenticates itself to the server, they establish a shared secret that is only known to both sides. Oracle Advanced Security then combines the shared secret and Diffie-Hellman session key to generate a stronger session key that would defeat the person-in-the-middle who has no way of knowing the shared secret.
The following configuration instructions assume that the Net8 network software has already been installed and is running. The network administrator sets up the encryption and checksumming configuration parameters. The profile (sqlnet.ora) on clients and servers using data encryption and integrity must contain some or all of the parameters listed in this section.
|
Note: The following instructions demonstrate how to configure Oracle Advanced Security native encryption and integrity. See Chapter 10, "Configuring Secure Socket Layer Authentication," to configure the SSL feature for encryption, integrity, and authentication. |
This section contains the following topics:
In any network connection, it is possible that both the client and server can support more than one encryption algorithm and more than one cryptographic integrity algorithm. When each connection is made, the server selects which algorithm to use, if any, based on the algorithms specified in the sqlnet.ora files.
When the server is searching for a match between the algorithms it has made available and the algorithms the client has made available, it picks the first algorithm in its own list that also appears in the client's list. If one side of the connection does not specify a list of algorithms, all the algorithms that are installed on that side are acceptable. The connection fails with error message ORA-12650 if an algorithm that is not installed is specified on either side.
Encryption and integrity parameters are defined by modifying a sqlnet.ora file on the clients and the servers on the network.
To negotiate whether to turn on encryption or integrity, you can specify four possible values for the Oracle Advanced Security encryption and integrity configuration parameters. The four values are listed below in the order of increasing security. The value REJECTED provides the minimum amount of security between client and server communications, and the value REQUIRED provides the maximum amount of network security.
The default value for each of the parameters is ACCEPTED.
Select this value to not enable the security service even if required by the other side.
In this scenario, this side of the connection specifies that the security service is not allowed. If the other side is set to REQUIRED, the connection terminates with error message ORA-12650. If the other side is set to REQUESTED, ACCEPTED, or REJECTED, the connection continues without error and without the security service enabled.
Select this value to enable the security service if required or requested by the other side.
In this scenario, this side of the connection does not require the security service, but it is allowed if the other side is set to REQUIRED or REQUESTED. If the other side is set to REQUIRED or REQUESTED, and an algorithm match is found, the connection continues without error and with the security service enabled. If the other side is set to REQUIRED and no algorithm match is found, the connection terminates with error message ORA-12650.
If the other side is set to REQUESTED and no algorithm match is found, or if the other side is set to ACCEPTED or REJECTED, the connection continues without error and without the security service enabled.
Select this value to enable the security service if the other side allows it.
In this scenario, this side of the connection specifies that the security service is wanted but not required. The security service is enabled if the other side specifies ACCEPTED, REQUESTED, or REQUIRED. There must be a matching algorithm available on the other side, otherwise the service is not enabled. If the other side specifies REQUIRED and there is no matching algorithm, the connection fails.
Select this value to enable the security service or disallow the connection.
In this scenario, this side of the connection specifies that the security service must be enabled. The connection fails if the other side specifies REJECTED or if there is no compatible algorithm on the other side.
Table 2-2 shows whether the security service is enabled based on a combination of client and server configuration parameters. If either the server or client has specified REQUIRED, a lack of a common algorithm causes the connection to fail. Otherwise, if the service is enabled, lack of a common service algorithm results in the service being disabled.
Table 2-2 Encryption and Data Integrity Negotiation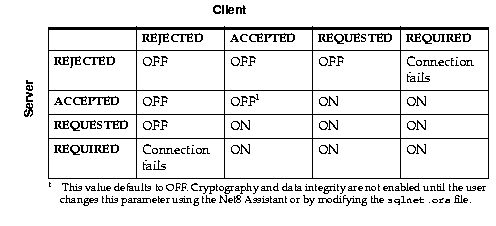
You can enter or change encryption and integrity parameter settings using Net8 Assistant.
This section describes the following tasks:
For a description of each parameter and a sample configuration file using encryption and integrity, see Appendix A, "Data Encryption and Integrity Parameters".
For more detailed configuration information, see Net8 Assistant online help.
More Information:
To configure encryption on the client and on the server:
The Oracle Advanced Security tabbed pages appear.
The encryption seed for the client should not be the same as that for the server.
Move it to the Selected Methods list by clicking the right arrow button [>]. Repeat for each additional method you want to use.
The sqlnet.ora file updates with the following entries:
SQLNET.ENCRYPTION_SERVER = [accepted | rejected | requested | required] SQLNET.ENCRYPTION_TYPES_SERVER = (valid_encryption_algorithm [,valid_ encryption_algorithm]) SQLNET.CRYPTO_SEED = "10-70 random characters"
The sqlnet.ora file should contain the following entries for the client:
SQLNET.ENCRYPTION_CLIENT = [accepted | rejected | requested | required] SQLNET.ENCRYPTION_TYPES_CLIENT = (valid_encryption_algorithm [,valid_ encryption_algorithm]) SQLNET.CRYPTO_SEED = "10-70 random characters"
To configure data integrity on the client and on the server:
The Oracle Advanced Security tabbed pages appear.
The sqlnet.ora file updates with the following entries:
SQLNET.CRYPTO_CHECKSUM_SERVER = [accepted | rejected | requested | required] SQLNET.CRYPTO_CHECKSUM_TYPES_SERVER = (crypto_checksum_algorithm)
The sqlnet.ora file should contain the following entries for the client:
SQLNET.CRYPTO_CHECKSUM_CLIENT = [accepted | rejected | requested | required] SQLNET.CRYPTO_CHECKSUM_TYPES_CLIENT = (crypto_checksum_algorithm)
|
|
 Copyright © 1999 Oracle Corporation. All Rights Reserved. |
|