Release 3.0.9
Part Number A88732-01
Library |
Solution Area |
Contents |
Index |
| Oracle9iAS Single Sign-On
Administrator's Guide
Release 3.0.9 Part Number A88732-01 |
|
This chapter provides a high-level overview of Oracle9iAS Single Sign-On.
This chapter contains these topics:
Oracle9iAS Single Sign-On is a component of Oracle9iAS Portal that provides a framework for secure single sign-on; allowing users to log in to multiple Web-based applications, such as expense reporting, e-mail, and benefits information, using a single username and password.
Oracle9iAS Single Sign-On provides the following benefits:
This section describes the following Oracle9iAS Single Sign-On components:
The core of the Oracle9iAS Single Sign-On technology is the Login Server. For partner applications, which rely on the Login Server for authentication, the Login Server authenticates users and passes their identities to the applications. For external applications, which do not use the Login Server authentication mechanism, the Login Server provides single sign-on through a centralized password repository.
When a user first tries to access a Oracle9iAS Single Sign-On enabled application, the Login Server:
During subsequent user logins, the login cookie provides the Login Server with the user's identity and indicates that authentication has already been performed. If there is no login cookie, the Login Server presents the user with a login page.
To guard against eavesdropping, the Login Server can send the login cookie to the client browser over an encrypted SSL channel.
The login cookie expires with the session, either at the end of a time interval specified by the administrator, or when the user exits the browser. The login cookie is never written to disk.
Partner applications are integrated with the Login Server. They support a single sign-on mechanism that enables them to accept a user's username and password as validated by the Login Server. Partner applications are generally written using the Oracle9iAS Single Sign-On SDK or Login Server specification.
A partner application delegates its authentication to the Login Server. If a partner application is registered with the Login Server, users can log into it using the single sign-on mechanism.
A partner application is responsible for determining whether a user authenticated by Oracle9iAS Single Sign-On has the requisite privileges for using the partner application. It also controls user access within the application.
An example of a partner application is the Oracle9iAS Portal itself.
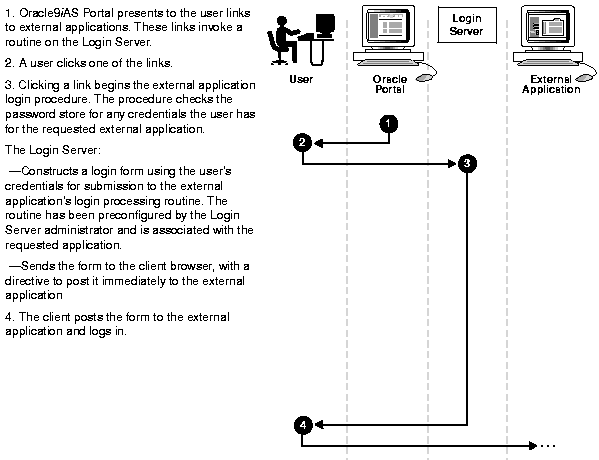
External applications retain their own authentication logic and do not delegate authentication to the Login Server. External applications therefore require application-specific usernames and passwords for providing access.
External applications typically use HTML login forms to accept the username and password. The username for the application can be different from the Oracle9iAS Single Sign-On username, in which case Login Server provides the required mapping.
Examples of external applications that use HTML login forms include Oracle Mobile and Yahoo! Mail. A unique username and password may be required to access each external application.
The Login Server provides usernames and passwords to external applications on behalf of the user. Users have the option of mapping external application authentication information to one or more usernames and passwords that are stored in the Login Server's password store. To map a password, the user selects the Remember My Login Information For This Application checkbox for the external application.
|
See Also:
"Specifying External Application Login Information" in Chapter 4, "Application Management" for information about the Remember My Login Information For This Application checkbox. |
A single Login Server account can be mapped to several external application usernames and passwords. When the user attempts to log in, the Login Server automatically checks the mappings and sends the user's authentication information to the appropriate external application.
|
See Also:
"Adding Partner and External Applications" in Chapter 4, "Application Management" for information about adding external applications. |
The Oracle9iAS Single Sign-On Software Development Kit (SDK) enables the following functionality:
Oracle9iAS Single Sign-On uses the following authentication methods:
Local user authentication uses a lookup table within the Login Server schema on the Oracle database associated with Oracle9iAS Portal. The table contains usernames, passwords, and Login Server privilege levels for the users. The incoming password is one-way hashed and compared to the entry in the table.
External repository authentication typically relies on an LDAP-compliant directory, specifically Oracle Internet Directory. In this case, the Login Server binds to Oracle Internet Directory, then looks up the user credentials stored in the directory. External repository authentication includes LDAP and other methods that can be custom developed.
Before a user can access a Oracle9iAS Single Sign-On enabled application, the Login Server must authenticate the user.
This section describes the following Oracle9iAS Single Sign-On processes:
Figure 1-1 illustrates the Login Server authentication process.
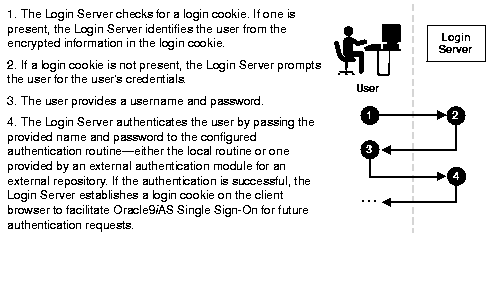
Figure 1-2 illustrates the process that occurs when a user seeks access to a partner application.
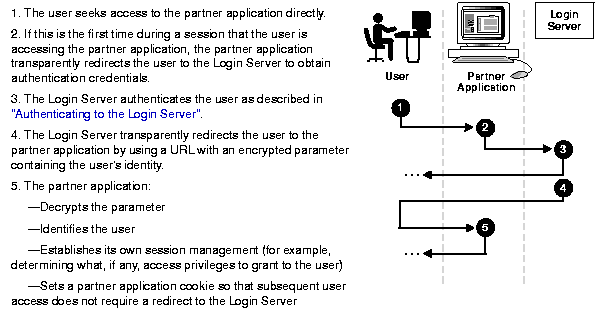
In Step 2 of this process, the partner application redirects the user to the Login Server only if the application requires it, based on the requested URL. Some URLs may be public and no redirection to the Login Server is required. When necessary, the partner application protects itself from unauthenticated access by its own session management.
If, during the same session, the user again seeks access to the same or to a different partner application, the Login Server does not prompt the user for a username and password. Instead, the Login Server obtains the information from the login cookie that is already on the client browser.
To implement an authentication check:
To implement a sign-on URL:
You can access an external application through Oracle9iAS Portal. In this scenario, Oracle9iAS Portal functions as a partner application.
This section contains these topics:
When a user seeks access to an external application through Oracle9iAS Portal, the Login Server authenticates the user to Oracle9iAS Portal by the process described in Figure 1-3.
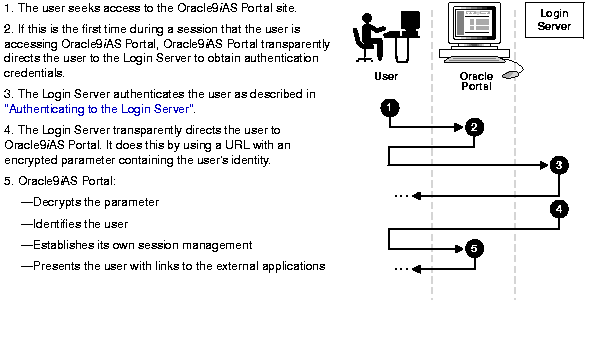
If, during the same session, the user again seeks access to Oracle9iAS Portal, the Login Server does not prompt the user for a username and password. Instead, it obtains that information from the login cookie on the client browser.
Oracle9iAS Single Sign-On uses the process described in Figure 1-4 if the user:
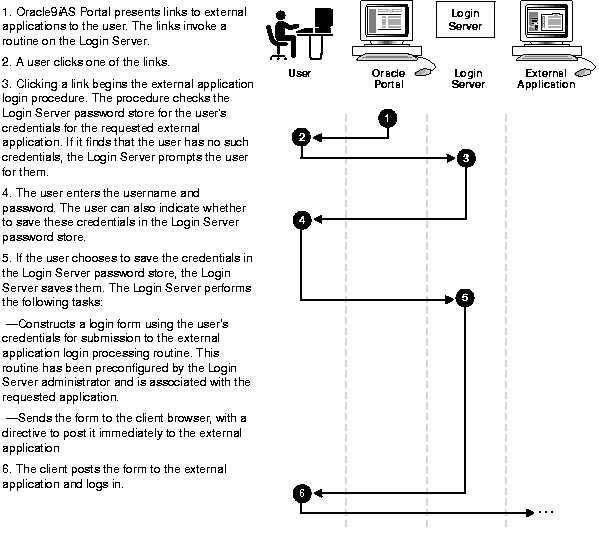
Oracle9iAS Single Sign-On uses the process described in Figure 1-5 if the user:
|
|
 Copyright © 2001 Oracle Corporation. All Rights Reserved. |
|