10g (9.0.4)
Part Number B12118-01
Home |
Solution Area |
Contents |
Index |
| Oracle® Internet Directory Administrator's Guide 10g (9.0.4) Part Number B12118-01 |
|
Integration with the Microsoft Windows Environment, 2 of 13
This section discusses the various aspects of the Windows integration environment as well as the Oracle components and tools involved. It contains these topics:
Table 43-1 describes each Oracle component used in integrating Oracle Internet Directory with Microsoft Active Directory.
| Component | Description |
|---|---|
|
Oracle Internet Directory |
The repository in which Oracle components and third-party applications store and access user identities and credentials. It uses the Oracle directory server to authenticate users against the stored credentials. When credentials are stored in a third-party directory and not in Oracle Internet Directory, users can still be authenticated. In this case, Oracle Internet Directory uses an external authentication plug-in that goes to the third-party directory server for authentication. |
|
Oracle Directory Integration and Provisioning Platform |
This platform enables:
It is installed as part of the Oracle Application Server infrastructure, but you can install it separately. This platform includes connectors for synchronizing between Oracle Internet Directory and other LDAP directories. One of its connectors, the Active Directory connector, is designed for two-way synchronization between Oracle Internet Directory and Microsoft Active Directory. The Active Directory connector enables you to:
You cannot synchronize user data between Oracle Internet Directory and Microsoft Windows NT by using the Oracle Directory Integration and Provisioning platform. You can, however, achieve this synchronization indirectly by synchronizing first between Oracle Internet Directory and Microsoft Active Directory, and then between Microsoft Active Directory and Microsoft Windows NT. |
|
Directory Integration and Provisioning Assistant |
This tool enables you to migrate data between Oracle Internet Directory and a third-party directory. More specifically, it enables you to:
You cannot directly load user data from Oracle Internet Directory into Microsoft Windows NT by using the Directory Integration and Provisioning Assistant. You can, however, achieve this indirectly by first loading the data into Microsoft Active Directory, and then using Microsoft tools to load the data from Microsoft Active Directory into Microsoft Windows NT. |
|
Oracle Application Server Single Sign-On |
Oracle Application Server Single Sign-On enables users to access Oracle Web-based components by logging in only once. Oracle components delegate the login function to the OracleAS Single Sign-On server. When a user first logs into an Oracle component, the component redirects the login to the OracleAS Single Sign-On server. The OracleAS Single Sign-On server authenticates the user by verifying the credentials entered by the user against those stored in Oracle Internet Directory. After it has authenticated the user, and throughout the rest of the session, the OracleAS Single Sign-On server grants the user access to all the components the user seeks and is authorized to use. Oracle Application Server Single Sign-On enables native authentication, also called autologin, in a Microsoft Windows environment. Once logged into the Windows desktop, the user automatically has access to Oracle components. OracleAS Single Sign-On automatically logs the user into the Oracle environment using user's Kerberos credentials. |
|
Active Directory External Authentication Plug-in |
This plug-in, which is part of the Oracle directory server, enables Microsoft Windows users to log into the Oracle environment by using their Microsoft Windows credentials. When such a user tries to log in, the OracleAS Single Sign-On server tries to verify the credentials the user enters against those stored in Oracle Internet Directory. If the user credentials are not there, then the Oracle directory server invokes the Active Directory external authentication plug-in. This plug-in verifies the user credentials in Microsoft Windows. If the verification is successful, then the Oracle directory server notifies the OracleAS Single Sign-On accordingly. In addition to enabling external authentication against Microsoft Windows, this plug-in also automatically provisions Microsoft Windows users into the Oracle Identity Management system. |
|
Oracle Internet Directory Self-Service Console |
Oracle Internet Directory Self-Service Console is a Web-based tool for managing users, groups, and their credentials in Oracle Internet Directory. Built from service units of Oracle Delegated Administration Services, this tool enables users to manage user passwords and password policies. See Also: Chapter 31, "Oracle Internet Directory Self-Service Console" for details on how to use this tool to manage realms and user and group search bases |
|
Oracle Directory Manager |
Oracle Directory Manager is a Java-based tool for administering Oracle Internet Directory. It enables directory administrators to manage all directory data including user information and configuration information used by the Oracle directory integration and provisioning server. |
Microsoft Active Directory provides various ways of tracking changes to its directory contents. Two of these approaches are:
In each approach, the directory from which changes are derived is polled at scheduled intervals by the Active Directory connector.
Each approach has advantages and disadvantages. Table 43-2 compares and contrasts the two approaches.
During installation, default synchronization profiles, mapping rules, and access controls are preconfigured. You can customize them to meet the needs of your deployment.
Most of the information for enabling synchronization is preconfigured in Oracle Internet Directory during installation and stored in a directory entry called Synchronization Profile. This information is used by the Oracle directory integration and provisioning server during synchronization and by the Directory Integration and Provisioning Assistant during bootstrapping.
You can change this information at runtime to meet your requirements. The next time the directory integration and provisioning server uses the profile for synchronization, it automatically refreshes its cache with the changed information. This saves you from restarting this server every time you change configuration information.
During installation, three default Active Directory synchronization profiles are created in Oracle Internet Directory. You can use them for running the Active Directory connector if they are adequate for your needs. Otherwise, use them as templates, customizing them to meet the needs of your deployment. They are:
ActiveImport--The profile for importing changes from Microsoft Active Directory to Oracle Internet Directory by using the DirSync approach
ActiveChgImp--The profile for importing changes from Microsoft Active Directory to Oracle Internet Directory by using the USNChanged approach
ActiveExport--The profile for exporting changes from Oracle Internet Directory to Microsoft Active Directory.
Mapping rules, an important part of the synchronization profile, determine what directory information is to be synchronized from one directory to another and how it is to be synchronized. You can change mapping rules at runtime to meet your requirements.
Each default Active Directory synchronization profile includes default mapping rules. These rules contain a minimal set of default user and group attributes configured for synchronization out of the box. These default attributes are described in Table 43-3, which lists them using their respective names in Microsoft Active Directory and Oracle Internet Directory.
In addition to the default attributes in Table 43-3, the ou (organizational unit) attribute is also preconfigured for synchronization. It is represented by ou both in Microsoft Active Directory and Oracle Internet Directory.
To enable users to access only data they are authorized to use, proper access controls are required in Oracle Internet Directory. More specifically, access controls are required to:
Two default access control policies are preconfigured during installation. They ensure that only authorized users can create entries in Oracle Internet Directory. The first policy disallows creation of any objects except users under the users subtree, which is the default container for all users to be synchronized. The second policy disallows creation of any objects except groups under the groups subtree, which is the default container for all groups to be synchronized.
|
See Also:
"Directory Information Tree Setup for Integration with Microsoft Active Directory" for more details on the user and group subtrees. |
After installation of Oracle Internet Directory, you need to configure only minimal additional information in the synchronization profile to enable synchronization between the two directories. In a simple deployment, you can easily configure this information by using the script adprofilecfg.sh. Other tools for configuring the information are:
"Configuring the Active Directory Connector" for a detailed description of the information you need to configure to enable the synchronization
See Also:
Configuration information required in multiple-domain Microsoft Active Directory environments for synchronizing Microsoft Directory to Oracle Internet Directory depends on whether the Global Catalog is configured. If it is available, then the Active Directory connector can synchronize from the Global Catalog. In this case, you must configure only one synchronization profile. If the Global Catalog is not available, then the Active Directory connector must go to each Microsoft Active Directory server to synchronize from Microsoft Active Directory. In this case, you must configure as many export profiles as there are number of Microsoft Active Directory domains.
Configuration information required in multiple-domain Microsoft Active Directory environments for synchronizing from Oracle Internet Directory to Microsoft Active Directory does not depend on the Global Catalog. The Active Directory connector always goes to each Active Directory to synchronize from Oracle Internet Directory to Microsoft Active Directory. You must configure as many export profiles as there are Microsoft Active Directory domains.
|
See Also:
"Configuring the Active Directory Connector" and "Customizing the Active Directory Connector" for instructions on configuring synchronization in environments with multiple Microsoft Active Directory domains |
Information in an LDAP directory is organized in a Directory Information Tree (DIT). In this tree, each node is called a directory entry that is identified by a unique value, called a distinguished name (DN).
A part of a tree that serves as a container for other entries is called a subtree. A node of a tree that contains no other entries is called a leaf.
Users and groups are represented as entries and can be either leaf or non-leaf nodes.
To facilitate proper organization of information and to enforce proper access controls in the directory, a top-level DIT structure is configured in the directory during installation. For example, the domain of Oracle Internet Directory is us.MyCompany.com, and a pre-configured default realm value is chosen during installation, then, after installation, the Oracle Internet Directory Configuration Assistant configures a default DIT. This default DIT, shown in Figure 43-1, contains two special entries: users and groups. These two entries are the roots of the two subtrees containing users and groups.
The most important decisions to be made before synchronization are:
You can synchronize either the entire DIT or part of it.
The Active Directory connector enables you to choose from two possible configurations:
Figure 43-1 shows an example of one-to-one mapping between the DITs in two directories.
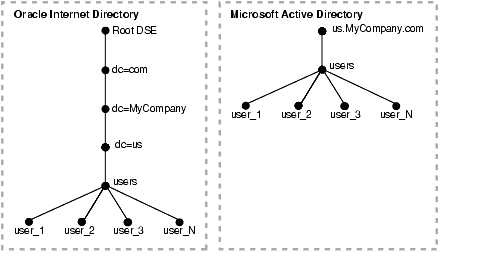
In the deployment illustrated in Figure 43-1:
us.MyCompany.com.
users.us.MyCompany.com.
users.us.MyCompany.com.
In such a deployment, only the users subtree must be synchronized from Microsoft Active Directory to Oracle Internet Directory using one-to-one domain mappings.
To configure the DIT:
Domain Rule Cn=users, dc=us, cd=MyCompany, dc=comusers.us.MyCompany.com: users.us.MyCompany.com
This mapping rule indicates that only the users container must be synchronized by using one-to-one domain mappings.
The DNs of the user entries in both Microsoft Active Directory and Oracle Internet Directory are identical.
If you choose to synchronize multiple subtrees, then you must configure multiple domain rules.
usersearchbase, and groupsearchbase values in Oracle Internet Directory. These values indicate to the various Oracle components where to look for users and groups in Oracle Internet Directory. During installation, be sure to set them correctly. Otherwise, even if the synchronization seems to function properly, components still may not be able to access users and groups in Oracle Internet Directory.
The default realm is set up during installation However, if the default realm value is incorrectly specified during installation, then do the following:
The usersearchbase and groupsearchbase values refer to the roots of the subtrees in Oracle Internet Directory under which Oracle components look for users and groups. These values are set to default values during installation. However, in deployments requiring integration with Microsoft Active Directory, these values must be reset to the appropriate values, depending on the DIT structure in Active Directory.
For example, in the above example, the value of usersearchbase should be set to at least cn=users,dc=us,dc=MyCompany,dc=com or one of its parents. Similarly, the groupsearchbase can be set to cn=groups,dc=us, dc=MyCompany,dc=com, assuming that there is a subtree named groups in the DIT.
The usersearchbase and groupsearchbase values are set as part of Windows integration setup discussed in "Configuring the Active Directory Connector".
Microsoft Active Directory deployment with multiple domains can have one single DIT or a forest of trees. In this typical scenario, Microsoft Active Directory has multiple domain controllers. A deployment with multiple domain controllers can have one single DIT or a forest of trees. The mapping between the DIT on Oracle Internet Directory and the DIT on Microsoft Active Directory for the single tree and the forest configurations are shown in Figure 43-2 and Figure 43-3 respectively.
Figure 43-2 shows an example of how multiple domains in Microsoft Active Directory are mapped to a DIT in Oracle Internet Directory.
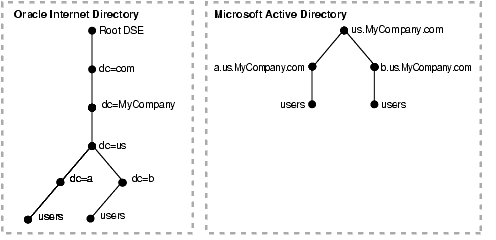
In Figure 43-2, the Microsoft Active Directory environment has a parent and two child domains. Each domain has a domain controller associated with it. The Microsoft Active Directory supporting the node us.mycompany.com is the Global Catalog Server.
The first child domain--namely, a.us.MyCompany.com--maps to dc=a,dc=us,dc=MyCompany,dc=com in Oracle Internet Directory. The second child domain--namely, b.us.MyCompany.com, maps to dc=b,dc=us,dc=MyCompany,dc=com in Oracle Internet Directory. The common domain component in Microsoft Active Directory environment--namely, us.MyCompany.com--maps to the default identity management realm in Oracle Internet Directory--namely, dc=us,MyCompany,dc=com.
Figure 43-3 shows how a forest in Microsoft Active Directory is reflected in Oracle Internet Directory.
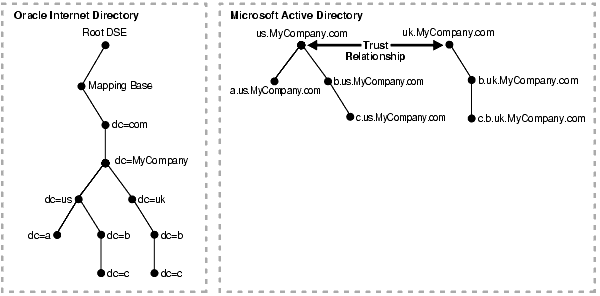
In Figure 43-3, Microsoft Active Directory is the enterprise directory. In this directory, two domain trees constitute a forest, and this forest maps to an identically structured subtree in Oracle Internet Directory.
Table 43-4 lists and describes the tools you use to set up and manage integration with Microsoft Active Directory.
| Tool | Description |
|---|---|
|
|
A shell script that provides an easy way of setting configuration information related to the Windows environment, such as the Microsoft Active Directory host and port information. This tool is useful only in simple scenarios and can be used only to configure information in default profiles. Note that this tool sets the information in all the three default profiles. When you run this tool, it creates the three default profiles, described earlier, from master default profiles and then modifies them with the information it takes as input from the user. Various setup tasks in the next section refer to this tool. This tool resides in $ |
|
Directory Integration and Provisioning Assistant |
A command-line tool primarily for initial migration of data. It also enables you to manage synchronization profiles. You can use it to create new default profiles and set various attributes in those profiles. Various setup tasks in next section are refer to this tool. See Also: "The Directory Integration and Provisioning Assistant" for more details about using the Assistant |
|
Oracle Internet Directory Self-Service Console |
A Web-based GUI tool for use by administrators and end users. In a Windows integration setup, is primarily used to configure information to manage realms and the user group search bases. It is also used to create and manage users and groups. See Also: Chapter 31, "Oracle Internet Directory Self-Service Console" for instructions about using this tool to manage realms and user and group search bases. |
|
Oracle Directory Manager |
A standalone Java- based GUI tool for managing all data in Oracle Internet Directory. You can use it to:
See Also: "Using Oracle Directory Manager" for more details |
|
Command-line tools |
Such tools as ldapmodify and ldapsearch for managing synchronization profiles and troubleshooting. Various set up tasks in next section refer to these tools tool. Once you know the various setup requirements for Windows integration, these tools are very handy for quick customization. See Also: "Entry and Attribute Management Command-Line Tools Syntax" |
|
|
 Copyright © 1999, 2003 Oracle Corporation. All Rights Reserved. |
|