|
Oracle® Application Server Portal Configuration Guide
10g Release 2 (10.1.2) Part No. B14037-01 |
|
 Previous |
 Next |
|
Oracle® Application Server Portal Configuration Guide
10g Release 2 (10.1.2) Part No. B14037-01 |
|
 Previous |
 Next |
This chapter discusses the configuration that must be performed to achieve some of the more advanced configurations. To perform these configurations, you must be familiar with the available administrative tools, described in Section 4.1, "Getting Started with OracleAS Portal Administration".
This chapter contains the following sections:
Configuring Multiple Middle-Tiers with a Load Balancing Router
Configuring OracleAS Portal to Use a Dedicated OracleAS Web Cache Instance
For information about procedures involved in changing ports in Oracle Application Server, refer to the Oracle Application Server Administrator's Guide .
|
Note: To view a list of all the ports currently in use by the components of a particular Oracle Application Server instance, refer to the steps outlined in Section 7.5, "Viewing Oracle Application Server Port Information". |
OracleAS Portal uses a number of different components (such as the Parallel Page Engine, Oracle HTTP Server, and OracleAS Web Cache) each of which may act as a client or server in an HTTP communication. As a result, each component in OracleAS Portal's middle-tier must be configured individually to use the HTTPS protocol.
Configuring SSL is described in Chapter 6, "Securing OracleAS Portal". The following sections describe the various configuration options you have available for SSL with OracleAS Portal:
This section describes how you can set up OracleAS Portal in a multiple middle-tier environment, front-ended by a load balancing router (LBR) to access the same Oracle Application Server Metadata Repository.
|
Note: This solution is best for internal deployments because it is not configured to use SSL. For the Oracle recommended way of configuring secure enterprise deployments, refer to Oracle Application Server Enterprise Deployment Guide. |
The purpose of a load balancing router (LBR) is to provide a single published address to the client tier, and front-end a farm of servers that actually service the requests, based on the distribution of the requests done by the LBR. The LBR itself is a very fast network device that can distribute Web requests to a large number of physical servers.
Let us assume that we want to configure the multiple middle-tier configuration, shown in Figure 5-1. In the example, we show OracleAS Web Cache on the same machine as the Portal and Wireless middle-tier, although they can theoretically be on different machines.
Figure 5-1 Multiple Middle-Tier Configuration with a Load Balancing Router
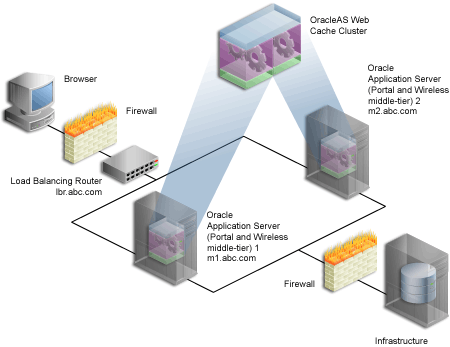
Table 5-1 Additional Information
| Machine | Details |
|---|---|
| Load Balancing Router (LBR) | Machine Name: lbr.abc.com
IP Address: Listening Port: Invalidation Port: |
| Oracle Application Server (Portal and Wireless middle-tier) 1 (M1) | Machine Name: m1.abc.com
IP Address: Oracle HTTP Server Listening Port: OracleAS Web Cache Listening Port: OracleAS Web Cache Invalidation Port: OracleAS Web Cache Administration Port: |
| Oracle Application Server (Portal and Wireless middle-tier) 2 (M2) | Machine Name: m2.abc.com
IP Address: Oracle HTTP Server Listening Port: OracleAS Web Cache Listening Port: OracleAS Web Cache Invalidation Port: OracleAS Web Cache Administration Port: |
|
Notes:
|
Additional LBR configuration is required to successfully handle:
Loopback Communication
OracleAS Portal's Parallel Page Engine (PPE) communicates with mod_plsql, running under Oracle HTTP Server, to retrieve page metadata (PMD) information. This communication is referred to as Loopback Connections, or Server to Server Load Balanced Connections. In a default configuration, the loopback connections are local, because OracleAS Web Cache and OracleAS Portal reside on the same machine.
If an LBR is front-ending Oracle Application Server, it will need additional configuration if OracleAS Web Cache is located on the same subnet. To understand this better, let's take a look at the different parts of the loopback connections without this additional configuration.
The PPE sends a loopback request for the PMD to mod_plsql when OracleAS Portal generates a page. This loopback request goes directly to the LBR.
The request is forwarded by the LBR to OracleAS Web Cache.
OracleAS Web Cache forwards the request to mod_plsql, running under Oracle HTTP Server.
mod_plsql processes the request and sends back the response to the loopback request to OracleAS Web Cache.
OracleAS Web Cache forwards the response to the LBR.
The LBR receives the response that is supposed to be routed back to the PPE.
The LBR detects that the source address, to which the response needs to be sent, is on the same subnet and it sends it back to OracleAS Web Cache, using the LBR's known socket connection, instead of using the PPE's socket connection.
OracleAS Web Cache is not listening for the request at all, and the incoming reply is dropped since there is no valid session.
OracleAS Portal pages time out with the error 'Timeout occurred while retrieving page metadata.'
As you can see, under normal circumstances, the LBR's behavior would be correct, because the LBR is essentially programmed to forward all requests to OracleAS Web Cache. However, in the case of loopback request, coming from the internal network, this results in an undesired outcome.
To avoid this, you must set up a Network Address Translation (NAT) bounce back rule on the LBR. This essentially configures the LBR as a proxy for requests coming to it from inside the firewall. This setup will make sure that the internal requests are forwarded correctly, and when the response reaches the LBR, it will be translated correctly and sent to the correct source address on the network (The PPE in this case).
The required steps for setting this up will be discussed later. NAT bounce back is set up differently on individual LBRs. Consult your LBR's configuration guide for information on how to set this up.
OracleAS Web Cache Invalidation
OracleAS Portal leverages OracleAS Web Cache to cache a lot of its content. When cached content in OracleAS Web Cache changes, OracleAS Portal sends invalidation messages from the database to OracleAS Web Cache. OracleAS Portal can only send invalidation messages to one Web Cache node in an OracleAS Web Cache cluster. Portal relies on that OracleAS Web Cache member to invalidate content in the other members of the cluster. When Oracle Application Server is front-ended by an LBR, the LBR must be configured to accept invalidation requests from the database and balance the load among the cluster members. Depending on how your routing is set up you may also need to set up NAT and open the appropriate outbound ports on your data tier. The required steps for setting this up will be discussed later.
|
Note: You will notice in Figure 5-1 that the infrastructure is behind the LBR. The infrastructure can be one host, or distributed over multiple hosts. To configure the infrastructure properly, refer to the advanced configuration information in the Oracle Application Server Single Sign-On Administrator's Guide. |
To configure OracleAS Portal in a multiple middle-tier environment, front-ended by an LBR, you must perform the following steps:
Step 1: Install a Single Portal and Wireless Middle-Tier (M1)
Step 2: Configure OracleAS Portal on M1 to Be Accessed Through the LBR
Step 5: Configure the New Middle-Tier (M2) to Run Your Existing Portal
Install a single Portal and Wireless application server middle-tier, and verify the installation. To do this perform the following steps:
Follow the steps described in Chapter 3, "Installing OracleAS Portal", to install a Portal and Wireless Oracle Application Server 10g middle-tier on the first machine (M1). It is assumed that you use the services of an existing Oracle Application Server Infrastructure.
|
See Also: Oracle Application Server Installation Guide. |
Verify that you have installed the middle-tier successfully by ensuring that you can access the OracleAS Portal home page at:
http://m1.abc.com:7777/pls/portal
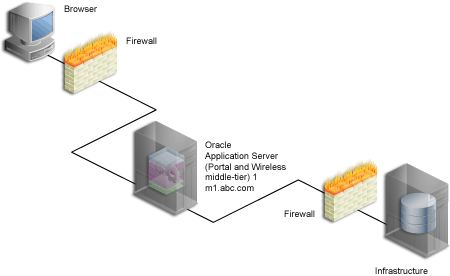
Your configuration now looks like Figure 5-2, with the details described in Table 5-1.
Figure 5-2 Installation of OracleAS Portal Middle-Tier
Access your iasconfig.xml file, located in MID_TIER_ORACLE_HOME/portal/conf, and verify that it looks something like Example 5-1:
Example 5-1 iasconfig.xml After the First Middle-Tier Installation
<IASConfig XSDVersion="1.0"> <IASInstance Name="iAS-1.m1.abc.com" Host="m1.abc.com">
<WebCacheComponent ListenPort="7777" AdminPort="4002"
InvalidationPort="4001" InvalidationUsername="invalidator"
InvalidationPassword="@Bd4D+TnaUYFTJebppIEqRc3/kleybcc70A==" SSLEnabled="false"/>
<EMComponent ConsoleHTTPPort="1814" SSLEnabled="false"/> </IASInstance>
<IASInstance Name="iAS.infra.abc.com" Host="infra.abc.com"> <OIDComponent AdminPassword="@BVs2KPJEWC5a0l4n8lbTxUY="
PortSSLEnabled="true" LDAPPort="3060" AdminDN="cn=orcladmin"/> </IASInstance> <PortalInstance DADLocation="/pls/portal" SchemaUsername="portal" SchemaPassword="@Beyh8p2bOWELQCsA5zRtuYc=" ConnectString="cn=iasdb,cn=oraclecontext">
<WebCacheDependency ContainerType="IASInstance" Name="iAS-1.m1.abc.com"/> <OIDDependency ContainerType="IASInstance" Name="iAS.infra.abc.com"/>
<EMDependency ContainerType="IASInstance" Name="iAS-1.m1.abc.com"/> </PortalInstance> </IASConfig>
You now proceed with the next step where you configure OracleAS Portal to be accessed through an LBR.
To configure OracleAS Portal so it can be accessed through the load balancing router, perform the following steps:
Configure the LBR (lbr.abc.com) to accept requests on port 80 and forward those to the OracleAS Web Cache port (7777) running on machine m1.abc.com. To do this, you need to:
Set up a group, or pool on the LBR, to which individual servers can be added.
Add the desired servers' IP addresses, and port numbers to the group.
Create a virtual server that listens on port 80, and balances load between the members of the group.
Make sure the LBR translates the port that it is listening on to forward requests to the port that OracleAS Web Cache is listening on.
|
Note: Consult the LBR documentation to set up the groups, and a virtual server. |
Configure the OracleAS Portal middle-tier on M1 to allow underlying components to construct URLs based on the LBR hostname (lbr.abc.com) and LBR port number (80), so that self-referential URLs rendered on OracleAS Portal pages are valid for the browser. To do this, perform the following steps:
Define a virtual host, using the Create Virtual Host wizard, as explained in Section 5.4.1.1, "Create the Virtual Host for www.xyz.com", with the following exceptions:
Define a second virtual host, using the Create Virtual Host wizard, as explained in Section 5.4.1.1, "Create the Virtual Host for www.xyz.com", with the following exceptions:
Define a site that matches the virtual host entry, created in the previous step (lbr.abc.com), using OracleAS Web Cache Manager on M1, as follows:
Access the OracleAS Web Cache Manager on M1, as described in Oracle Application Server Web Cache Administrator's Guide .
From Properties, click Sites.
Click Create under Named Sites Definitions.
On the Create Named Site page, specify lbr.abc.com for the Host and 80 for Port. Keep the default values for all other fields.
Click OK. You will now see lbr.abc.com in the Named Sites Definitions table.
Use OracleAS Web Cache Manager on M1, to map the site lbr.abc.com to middle-tier m1.abc.com.
In the navigation frame, select Site-to-Server Mapping under Origin Servers, Sites, and Load Balancing.
In the Site-to-Server Mapping page, select the first mapping in the table and click Insert Above.
In the Edit/Add Site-to-Server Mapping page, select the Select from Site definitions option and then select a site definition created in the previous step (lbr.abc.com).
In the Select Application Web Servers section, select the application server M1 (m1.abc.com) specified in the Origin Servers page.
Click Submit.
Click Apply Changes on the top of the page.
In the Cache Operations page, click Restart to restart Web Cache on M1.
To verify that the site has been mapped correctly, navigate to the Site-to-Server Mapping page, and ensure that M1 is mapped to the site lbr.abc.com.
Configure machine m1.abc.com so that it can resolve the LBR hostname to have the correct IP address. You can either rely on DNS resolution, or make entries in the /etc/hosts file as follows:
L1.L1.L1.L1 lbr.abc.com
Where L1.L1.L1.L1 is the IP address for the LBR. There is no need to restart the system after making these changes.
|
WARNING: Ensure that the 127.0.0.1 m1.abc.com |
Configure the LBR to perform Network Address Translation (NAT) bounce back for loopback requests coming from the PPE running on m1.abc.com. This ensures that when the PPE makes a loopback request to OracleAS Web Cache, there are no errors.
|
Notes:
|
Configure the LBR (lbr.abc.com) to accept invalidation requests from the OracleAS Metadata Repository on a separate port (4001 in this example), so that it is forwarded to the OracleAS Web Cache running on machine m1.abc.com on port 4001.
|
Note: The LBR does not have to listen on the OracleAS Web Cache invalidation port. On LBRs that do not have Port Mapping ability the port number must match the OracleAS Web Cache invalidation port. |
Set up a group, or pool on the LBR, to which individual servers can be added.
Add the desired servers' IP addresses, and port numbers to the group.
Create a virtual server that listens on port 4001, and balances load between the members of the group.
In the case where the LBR's port, that is listening for the invalidation requests, and the OracleAS Web Cache's invalidation port are different, you must ensure that the LBR translates the port that it is listening on to forward requests to the port that OracleAS Web Cache is listening on.
|
Notes:
|
|
WARNING: For security reasons, the invalidation port on the LBR (port |
You must manually edit the iasconfig.xml file, typically located in MID_TIER_ORACLE_HOME/portal/conf. Before editing the file, it is recommended that you make a backup copy of it. The file must be updated to have the correct farmname, hostname, and port information used to access OracleAS Portal, and to perform the OracleAS Web Cache invalidation, as shown in Example 5-2 (all changes are shown in bold):
Example 5-2 iasconfig.xml File Edited to Include Farm Element
<IASConfig XSDVersion="1.0"> <IASFarm Name="Farm-1.lbr.abc.com" Host="lbr.abc.com"> <WebCacheComponent ListenPort="80" AdminPort="4002"
InvalidationPort="4001" InvalidationUsername="invalidator"
InvalidationPassword="welcome1" SSLEnabled="false"/> </IASFarm>
<IASInstance Name="iAS.infra.abc.com" Host="infra.abc.com"> <OIDComponent AdminPassword="@BVs2KPJEWC5a0l4n8lbTxUY="
PortSSLEnabled="true" LDAPPort="3060" AdminDN="cn=orcladmin"/> </IASInstance>
<IASInstance Name="iAS-1.m1.abc.com" Host="m1.abc.com">
<EMComponent ConsoleHTTPPort="1814" SSLEnabled="false"/> </IASInstance>
<PortalInstance DADLocation="/pls/portal" SchemaUsername="portal"
SchemaPassword="@Beyh8p2bOWELQCsA5zRtuYc="
ConnectString="cn=iasdb,cn=oraclecontext">
<WebCacheDependency ContainerType="IASFarm" Name="Farm-1.lbr.abc.com"/>
<OIDDependency ContainerType="IASInstance" Name="iAS.infra.abc.com"/>
<EMDependency ContainerType="IASInstance" Name="iAS-1.m1.abc.com"/>
</PortalInstance>
</IASConfig>
|
Note: If OracleAS Web Cache oniAS-1.m1.abc.com (shown in Example 5-1) is not referenced by any other OracleAS Portal instance, you can remove the entry from iasconfig.xml, as seen in Example 5-2.
|
Encrypt any plain text passwords in the iasconfig.xml configuration file. To do this, navigate to MID_TIER_ORACLE_HOME/portal/conf, and run the following command:
ptlconfig -encrypt
|
Note: To useptlconfig, the ORACLE_HOME environment variable must be set.
|
Register the URL changes with OracleAS Portal. Make sure that the new URLs used for accessing OracleAS Portal use the LBR hostname and port, and that the OracleAS Web Cache invalidation URLs (OracleAS Web Cache hostname and invalidation ports) are that of the LBR. To do this, navigate to MID_TIER_ORACLE_HOME/portal/conf, and run the following command:
ptlconfig -dad <portal_dadname> -wc -site
For example,
ptlconfig -dad portal -wc -site
Run ssoreg to register the secured request with OracleAS Single Sign-On by configuring it as a partner application. ssoreg is located on the middle-tier in MID_TIER_ORACLE_HOME/sso/bin.
The following example illustrates the usage of ssoreg on UNIX:
MID_TIER_ORACLE_HOME/sso/bin/ssoreg.sh -site_name lbr.abc.com -mod_osso_url http://lbr.abc.com -config_mod_osso TRUE -oracle_home_path MID_TIER_ORACLE_HOME -config_file MID_TIER_ORACLE_HOME/Apache/Apache/conf/osso/osso.conf -admin_info cn=orcladmin -virtualhost
On Windows, you must run ssoreg.bat instead. Refer to the information on registering mod_osso in the Oracle Application Server Single Sign-On Administrator's Guide.
To enable monitoring of the load balancing router's front-end host and port settings for OracleAS Portal, you must edit targets.xml (located in MID_TIER_ORACLE_HOME/sysman/emd/) on M1, as follows:
Open targets.xml on M1, using a text editor.
Search for OracleAS Portal targets, that is, TYPE="oracle_portal".
Edit the PortalListeningHostPort property, to point to the LBR. For example:
<Property NAME="PortalListeningHostPort" VALUE=http://lbr.abc.com:80/>
Save the changes to targets.xml.
Reload the targets in the Application Server Control Console:
On Solaris/Linux, enter:
MID_TIER_ORACLE_HOME/bin/emctl reload
On Windows:
MID_TIER_ORACLE_HOME\bin\emctl reload
Optionally, re-register the Wireless gateway URL with the load-balancer's address. See Section 5.10, "Configuring OracleAS Wireless" for more information.
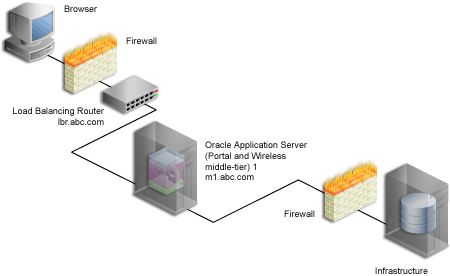
After these steps, your configuration looks like Figure 5-3 with the details described in Table 5-1.
Figure 5-3 OracleAS Portal Being Accessed Through the LBR
Confirm that OracleAS Portal is up and running by performing the following tests in the specified order. If a test fails, address the issues, before proceeding with the next test. To diagnose the OracleAS Web Cache, Oracle HTTP Server, and LBR configuration and logs, refer to the Oracle Application Server Administrator's Guide.
Test access to OracleAS Web Cache and Oracle HTTP Server through the LBR, by accessing a static file that is cached in OracleAS Web Cache, and make sure it works. For example, you can access the following URL:
http://lbr.abc.com/index.html
Test the connection to Oracle Application Server Metadata Repository through the LBR, by accessing the following URL:
http://lbr.abc.com/pls/portal/htp.p?cbuf=test
The response should be "test". If this succeeds, it means that the Oracle Application Server middle-tier can connect to the OracleAS Metadata Repository. If this fails, scan the Oracle HTTP Server error_log file for details about the request failure, and take appropriate actions.
Test access to OracleAS Portal, by completing the following steps:
Access the OracleAS Portal home page at http://lbr.abc.com/pls/portal. If this does not work, scan the application.log file for the OC4J_Portal instance, and look for errors. The most common reason for this error is because the PPE cannot make loopback connections. For this to work:
Ensure that Network Address Translation (NAT) is enabled in the LBR.
Ensure that the middle-tier on m1.abc.com can resolve the address of lbr.abc.com. To do this, run the following command from m1.abc.com:
ping lbr.abc.com
Click the portal login link. If this does not work, it could be due to one of the following reasons:
The Infrastructure middle-tier is down or is not working. Check the Oracle HTTP Server error_log file in the INFRA_ORACLE_HOME for more details.
The partner application URL registration for OracleAS Portal is incorrect, or OracleAS Single Sign-On is down.
Click some links in the portal.
Confirm that content is getting cached in OracleAS Web Cache. To do this, access the OracleAS Web Cache Manager on M1, as described in Oracle Application Server Web Cache Administrator's Guide.
|
Note: The Web Cache Administration and the Portal Service Monitoring links in the Services portlet will not work in the multiple middle-tier configuration. |
Under Monitoring, click Popular Requests. Select Cached from the Filter Objects drop-down list, and click Update. If you accessed OracleAS Portal, you will see portal content (For example, URLs that contain /pls/portal). If you don't see any portal content, open another browser and log in to OracleAS Portal. Return to the Popular Requests page, and click Update, to refresh the page content. This should provide enough content for verification.
Perform some simple page edits in OracleAS Portal, like adding a portlet to a page and make sure that the new content shows up. If the new content does not display properly, or if you see errors, OracleAS Web Cache invalidation is misconfigured.
Follow these steps to install a new Portal and Wireless middle-tier on M2 (m2.abc.com):
Set the IASCONFIG_LOC environment variable to point to the same location that IASCONFIG_LOC is pointing to on machine m1.abc.com. The iasconfig.xml file allows Portal configuration to be performed from any of the hosts involved in a Web site topology. The environment variable should ideally point to a location that is accessible over a shared file system, so that installations done on different machines can reference and update the same file.
The environment variable should be set in the second middle-tier before starting the installation. To override the default location of the configuration file, you must set the environment variable IASCONFIG_LOC to a directory in which the file is stored, for example:
set IASCONFIG_LOC=/usr/local/ias904
|
Note: By default,iasconfig.xml resides in MID_TIER_ORACLE_HOME/portal/conf. If the Portal Dependency Settings file is accessible over a network file system, you can share the file across multiple hosts, avoiding the need to manually replicate it every time the file is modified. If the installation is running on an operating system that supports symbolic links, it is recommended that you use this mechanism to reference a shared file. If, however, the Portal Dependency Settings file is not accessible over the network, you must ensure that the file is kept up-to-date with changes to your site topology. Refer to Section A.2.4, "Updating the Portal Dependency Settings File" for more information.
|
Run Oracle's Universal Installer to install a Portal and Wireless Oracle Application Server 10g middle-tier on the second machine (M2).
|
Note: It is recommended that you use the same physical path for installing the second middle-tier. This helps when you make configuration changes on one machine and want to transfer the changes to another machine. If the physical path is different on other machines, you must ensure that the path elements are corrected after copying the files. |
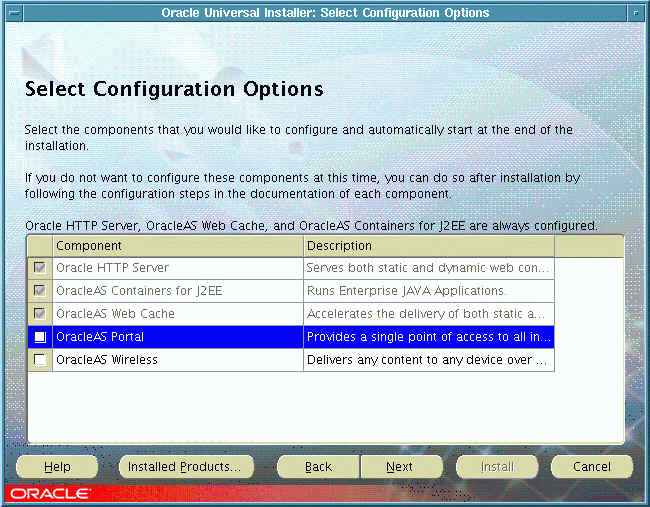
Clear the selection for OracleAS Portal in the Select Configuration Options screen during the installation of Oracle Application Server middle-tier, as shown in Figure 5-4.
Figure 5-4 Select Configuration Options Screen
|
WARNING: Selecting OracleAS Portal in the Select Configuration Options screen overwrites your previous configuration entries in OracleAS Portal. For more information, see Section 3.3, "Configuring OracleAS Portal During and After Installation". |
Enable OracleAS Portal, accessing the Application Server Control Console. Refer to Section 7.2.2, "Using Application Server Control Console to Configure OracleAS Portal", for further instructions.
|
Note: This will deploy the OracleAS Portal middle-tier components, but will not overwrite information in the OracleAS Metadata Repository. |
This new installation should not have affected your previous configuration. Confirm that OracleAS Portal is up and running on M1, and can be accessed through the LBR. See Section 5.3.3, "Step 3: Confirm That OracleAS Portal is Up and Running" for more information on how to check this.
Follow these steps, in the order specified, to configure M2 to run your existing portal:
Configure the new OracleAS Portal middle-tier to allow underlying components to construct URLs based on the LBR hostname (lbr.abc.com) and LBR port number (80). To do this, perform the following steps, using the Application Server Control Console on M2:
Define a virtual host, using the Create Virtual Host wizard, as explained in Section 5.4.1.1, "Create the Virtual Host for www.xyz.com", with the following exceptions:
Define a second virtual host, using the Create Virtual Host wizard, as explained in Section 5.4.1.1, "Create the Virtual Host for www.xyz.com", with the following exceptions:
Copy the configuration settings for OracleAS Portal from the middle-tier M1, to the middle-tier M2. It is a good idea to make backup copies of the files first. To do this, perform the following steps:
Copy MID_TIER_ORACLE_HOME/Apache/modplsql/conf/dads.conf from M1 to M2.
Copy MID_TIER_ORACLE_HOME/Apache/modplsql/conf/cache.conf from M1 to M2.
Copy MID_TIER_ORACLE_HOME/j2ee/OC4J_Portal/applications/portal/portal/WEB-INF/web.xml from M1 to M2.
If M1 and M2 are installed using different physical paths, you need to make sure that the path elements are corrected after copying the files.
If you have not defined IASCONFIG_LOC in Section 5.3.4, "Step 4: Install a New Portal and Wireless Middle-Tier (M2)", you must update the iasconfig.xml file on M2 to have the same settings as iasconfig.xml on M1, by following the steps described in Section A.2.4, "Updating the Portal Dependency Settings File".
Re-register mod_osso on M2. To do this, perform the following steps:
Copy the MID_TIER_ORACLE_HOME/Apache/Apache/conf/osso.conf from M1 to M2. osso.conf is a binary file.
Synchronize the DCM repository by issuing the following command:
MID_TIER_ORACLE_HOME/Apache/Apache/bin/ssotransfer MID_TIER_ORACLE_HOME/Apache/Apache/conf/osso/osso.conf
|
Note: This does not create any new partner applications; it enables the partner applicationlbr.abc.com for M1 and M2.
|
Synchronize the manual configuration changes done on M2 by running the following command from the directory MID-TIER_ORACLE_HOME/dcm/bin/:
dcmctl updateConfig
Restart Oracle HTTP Server on M2, by running the following command from the directory MID_TIER_ORACLE_HOME/opmn/bin:
opmnctl restartproc type=ohs
Configure the machine m2.abc.com to resolve the LBR hostname to have the correct IP address. You can either rely on DNS resolution for this, or make entries in the /etc/hosts file as follows:
L1.L1.L1.L1 lbr.abc.com
|
WARNING: Ensure that the 127.0.0.1 m2.abc.com |
Access the OracleAS Web Cache Manager on M1, as described in Oracle Application Server Web Cache Administrator's Guide.
Use OracleAS Web Cache Manager on M1, to add the OracleAS Web Cache on M2 to the OracleAS Web Cache cluster on M1. To do this, perform the following steps:
Click Clustering under Properties.
On the Clustering page, under the Cluster Members table, click Add.
On the Add Cache to Cluster page, specify the following information for M2 to be included in this Web Cache cluster:
| Property | Value |
|---|---|
| Host Name | m2.abc.com
|
| Admin Port | 4002
|
| Protocol for Admin Port | HTTP
|
| Cache Name | m2.abc.com-WebCache
|
| Capacity | 30
|
|
Note: For the value of the Cache Name property, you can specify any name. |
Click Submit.
To verify that the OracleAS Web Cache on M2 has been added to the cluster, locate m2.abc.com in the Cluster Member table.
For information on configuring a cache cluster, refer to the Oracle Application Server Web Cache Administrator's Guide.
Use OracleAS Web Cache Manager on M1, to add M2 as an additional origin server to the OracleAS Web Cache cluster, created in the previous step. To do this, perform the following steps:
Click Origin Server, under Origin Servers, Sites, and Load Balancing.
In the Origin Server page, click Add under the Application Web Servers table.
In the Add Application Web Server page, provide the following information:
| Property | Value |
|---|---|
| Hostname | m2.abc.com
|
| Port | 7778
|
| Routing | ENABLED
|
| Capacity | 100
|
| Failover Threshold | 5
|
| Ping URL | /
|
| Ping Interval | 10
|
| Protocol | HTTP
|
|
Note: For the Port value, use the M2's Oracle HTTP Server listening port. |
Click Submit
To verify that the origin server has been added properly, locate m2.abc.com in the Origin Server table.
Refer to the section "Map Sites to Origin Servers" in the Oracle Application Server Web Cache Administrator's Guide for more information.
Use OracleAS Web Cache Manager on M1, to map the site lbr.abc.com to the two origin servers m1.abc.com, and m2.abc.com, by performing the following steps:
In the navigation frame, select Site-to-Server Mapping under Origin Servers, Sites, and Load Balancing.
On the Site-to-Server Mapping page, Select the mapping for the LBR site in the table and click Edit Selected.
In the Select Application Web Servers section, select an application Web server specified in the Origins Servers page for M2 (m2.abc.com).
Click Submit.
To verify that the site has been mapped correctly, ensure that both M1 and M2 are mapped to the site lbr.abc.com in the Site to Server Mappings table.
Refer to the section "Map Sites to Origin Servers" in the Oracle Application Server Web Cache Administrator's Guide for more information.
To save your configuration changes, click Apply Changes on the top of the page. Perform the following steps in the Cache Operations page:
Click Propagate to propagate changes to M2.
Click Restart to restart Web Caches on M1 and M2.
Configure the LBR (lbr.abc.com) to forward requests on the invalidation port to OracleAS Web Cache running on the second middle-tier m2.abc.com on port 4001, similar to the configuration previously done for the first middle-tier m1.abc.com.
|
Note: The LBR does not have to listen on the OracleAS Web Cache invalidation port. On LBRs that do not have Port Mapping ability, the port number must match the OracleAS Web Cache invalidation port. |
Configure the LBR (lbr.abc.com) to forward requests on port 80 to OracleAS Web Cache running on machine m2.abc.com on port 7777, similar to the configuration previously done for the first middle-tier m1.abc.com.
|
Note: Consult the LBR documentation to complete this step. |
Configure the LBR to perform Network Address Translation (NAT) bounce back for loopback requests coming from Oracle HTTP Server on m2.abc.com. Refer to Step 6 in Section 5.3.2, "Step 2: Configure OracleAS Portal on M1 to Be Accessed Through the LBR " section for more information.
After these steps, your configuration looks like Figure 5-1.
|
Note: For adding more middle-tiers, follow the procedures outlined in Section 5.3.4, "Step 4: Install a New Portal and Wireless Middle-Tier (M2)" and Section 5.3.5, "Step 5: Configure the New Middle-Tier (M2) to Run Your Existing Portal", for each middle-tier. |
To enable monitoring of the load balancing router's front-end host and port settings for OracleAS Portal, you must edit targets.xml (located in MID_TIER_ORACLE_HOME/sysman/emd/) on M2, as follows:
Open targets.xml on M2, using a text editor.
Search for OracleAS Portal targets, that is, TYPE="oracle_portal".
Edit the PortalListeningHostPort property, to point to the LBR. For example:
<Property NAME="PortalListeningHostPort" VALUE=http://lbr.abc.com:80/>
Save the changes to targets.xml.
Reload the targets in the Application Server Control Console:
On Solaris/Linux, enter:
MID_TIER_ORACLE_HOME/bin/emctl reload
On Windows:
MID_TIER_ORACLE_HOME\bin\emctl reload
To ensure that the Portal Tools (OmniPortlet and OracleAS Web Clipping) providers and Locally Built, as well as Custom built Web providers work properly, in the middle-tier environment, some additional configuration is required. If OmniPortlet or any other Web providers already have customization in the file system, PDK-Java provides a Preference Store Migration/Upgrade Utility that can be used to migrate the existing customizations to the database and upgrade customizations from earlier releases. More information on the PDK Preference Store Migration Utility can be found in the PDK-Java Release Notes, available on Portal Center at http://portalcenter.oracle.com.
Configuring Portal Tools Providers in the Multiple Middle-Tier Environment
Perform the following steps for Portal Tools (OmniPortlet and OracleAS Web Clipping) providers to function properly in the multiple middle-tier environment:
Configure OmniPortlet to use a shared Preference Store. By default, the OmniPortlet provider uses the file-based Preference Store. However, in a multiple middle-tier environment, you must use a shared Preference Store, like the database Preference Store (DBPreferenceStore). To configure Portal Tools providers to use DBPreferenceStore, perform the following steps:
Navigate to the directory ORACLE_HOME/j2ee/OC4J_Portal/applications/jpdk/jpdk/doc/dbPreferenceStore. For example:
cd ORACLE_HOME/j2ee/OC4J_Portal/applications/jpdk/jpdk/doc/dbPreferenceStore
On the database where the PORTAL schema is installed, log on to SQL*Plus as the user that owns the DBPreferenceStore table. Ensure that this user has the necessary privileges to create tables and indexes. For example:
sqlplus scott/tiger
Run the jpdk_preference_store2.sql script as follows in SQL*Plus:
@jpdk_preference_store2
Add the following entry to the file data-sources.xml, located in the directory ORACLE_HOME/j2ee/OC4J_Portal/config:
<data-source class="com.evermind.sql.DriverManagerDataSource" name="omniPortletprefStore" location="jdbc/UnPooledConnection" xa-location="jdbc/xa/XAConnection" ejb-location="jdbc/PooledConnection" connection-driver="oracle.jdbc.driver.OracleDriver" username="scott" password="tiger" url="jdbc:oracle:thin:@infra.host.com:1521:orcl" inactivity-timeout="30" />
Edit the file provider.xml located in the directory ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/omniPortlet/WEB-INF/providers/omniPortlet. Edit the preferenceStore tag as shown in bold:
<provider class="oracle.webdb.reformlet.ReformletProvider"> <vaultId>0</vaultId> <session>true</session> <preferenceStore class="oracle.portal.provider.v2.preference.DBPreferenceStore"> <name>omniPortletprefStore</name> <connection>jdbc/PooledConnection</connection> </preferenceStore>
Restart OC4J_Portal.
More information on configuring the database Preference Store can be found in:
The PDK article titled "Installing the DBPreferenceStore Sample (V2)", located at http://portalstudio.oracle.com/pls/ops/docs/FOLDER/COMMUNITY/PDK/jpdk/v2/doc/dbPreferenceStore/installing.db.preference.store.v2.html, on Portal Center at http://portalcenter.oracle.com.
The section on Preference Information in the Oracle Application Server Portal Developer's Guide.
Typically, you perform the HTTP Proxy configuration for OmniPortlet and WebClipping before you configure the LBR. To do it after the LBR is configured, perform the following steps:
The Portal Tools configuration information is stored in the provider.xml file on the middle-tier server. You need to update the configuration directly on one middle-tier (for example, M1) and then propagate it across all middle-tiers front-ended by the LBR. Before you do this, you must disconnect M1 from the LBR. Consult your LBR's configuration guide for information on how to do this.
Turn off the Single Sign-On protection on the Portal Tools provider configuration pages on M1. You can do this by setting the param-value to false in ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/providerBuilder/WEB-INF/web.xml file, as follows:
<init-param>
<param-name>oracle.webdb.providerui.securedAccessParam</param-name>
<param-value>false</param-value>
</init-param>
Restart OC4J_Portal.
You can change the settings on the Portal Tools Edit Provider pages (OmniPortlet, and OracleAS Web Clipping), accessible from the Portal Tools providers' test pages. The test pages are located at the following URLs:
OmniPortlet provider test page on M1: http://m1.abc.com:7777/portalTools/omniPortlet/providers/omniPortlet
Web Clipping provider test page on M1: http://m1.abc.com:7777/portalTools/webClipping/providers/webClipping
Refer to Section I.1, "Configuring the Web Clipping Repository", and Section I.2, "Configuring HTTP or HTTPS Proxy Settings" for more information.
Restore the Single Sign-On protection on the Portal Tools provider configuration pages by setting the param-value to true in ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/providerBuilder/WEB-INF/web.xml file, as follows:
<init-param>
<param-name>oracle.webdb.providerui.securedAccessParam</param-name>
<param-value>true</param-value>
</init-param>
Restart OC4J_Portal.
Propagate the changes made to the provider.xml file to middle-tier M2:
Copy the ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/omniPortlet/WEB-INF/providers/omniPortlet/provider.xml from M1 to M2.
Copy the ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/webClipping/WEB-INF/providers/webClipping/provider.xml from M1 to M2.
Reconnect M1 to the LBR.
Restart middle-tier M2.
Copy the ORACLE_HOME/j2ee/OC4J_Portal/config/data-sources.xml from M1 to M2.
Click Edit Registration for the OmniPortlet Provider on the Providers tab of the Navigator, under Locally Built Providers. Then click the Connection tab, and change the first part of the provider registration URL from http://m1.abc.com:7777/ to http://lbr.abc.com/.
Click Edit Registration for the Web Clipping Provider on the Providers tab of the Navigator, under Locally Built Providers. Then click the Connection tab and change the first part of the provider registration URL from http://m1.abc.com:7777/ to http://lbr.abc.com/.
Verify that OmniPortlet and the Web Clipping Provider work properly through the LBR, by going to the test pages at the following URLs.
OmniPortlet Provider: http://lbr.abc.com/portalTools/omniPortlet/providers/omniPortlet
Web Clipping Provider: http://lbr.abc.com/portalTools/webClipping/providers/webClipping
|
Note: If you want to use the OracleAS Web Clipping provider, or the Web Page Data Source for OmniPortlet, you must also enable session binding in OracleAS Web Cache, as described in Step 7: Enable Session Binding on OracleAS Web Cache. |
Creating and Editing Locally Built Web Providers in the Multiple Middle-Tier Environment
Locally built providers are providers that are defined within an instance of OracleAS Portal. You typically create or edit these providers before configuring for LBR. If you are doing it after the LBR is configured, perform the following steps:
The Web provider information is kept in the provider.xml file on the middle-tier server. You need to update the configuration directly on one middle-tier (for example, M1) and then propagate it across all middle-tiers front-ended by the LBR. Before you do this, you must disconnect M1 from the LBR. Consult your LBR's configuration guide for information on how to do this.
Turn off the Single Sign-On protection on the Web provider creation and editing pages on M1. You can do this by setting the param-value to false in ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/providerBuilder/WEB-INF/web.xml file, as follows:
<init-param>
<param-name>oracle.webdb.providerui.securedAccessParam</param-name>
<param-value>false</param-value>
</init-param>
Restart OC4J_Portal.
Create or edit a Web provider, and its portlets. A provider.xml file is created for each new provider.
Restore the Single Sign-On protection on the Web provider creation and editing pages by setting the param-value to true in ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/providerBuilder/WEB-INF/web.xml file, as follows:
<init-param>
<param-name>oracle.webdb.providerui.securedAccessParam</param-name>
<param-value>true</param-value>
</init-param>
Restart OC4J_Portal.
Propagate the changes made to the files in M1 to middle-tier M2:
Copy the ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/providerBuilder/WEB-INF/providers/<providerName> directory from M1 to M2.
Copy the ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/providerBuilder/WEB-INF/deployment/<providerName>.properties file from M1 to M2.
Copy the ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/providerBuilder/WEB-INF/deployment_providerui/provideruiacls.xml file from M1 to M2.
Copy the entry for <providerMap> in ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/providerBuilder/WEB-INF/deployment_providerui/providerstore.xml from M1 to M2 and change the <warDir> element with the appropriate value for the ORACLE_HOME for M2 (shown in bold):
<providerMap name="MyProvider" baseLanguage="en">
<displayName language="en" translation="myprovider"></displayName>
<timeout>20</timeout>
<timeoutMessage language="en" translation="Timed Out"></timeoutMessage>
<loginFrequency>Never</loginFrequency>
<httpURL>http://lbr.abc.com:80/portalTools/builder/providers/MYPROVIDER</httpURL>
<cookieDomain>abc.com</cookieDomain>
<serviceId>MYPROVIDER</serviceId>
<requireSessionData>false</requireSessionData>
<httpAppType>Portal</httpAppType>
<warDir>ORACLE_HOME/j2ee/OC4J_Portal/applications/portalTools/providerBuilder/WEB-INF</warDir>
<warFile>providerBuilder</warFile>
</providerMap>
Click Edit Registration for the provider on the Providers tab of the Navigator, under Locally Built Providers. Then click the Connection tab and change the first part of the provider registration URL from http://m1.abc.com:7777/ to http://lbr.abc.com/.
Verify that the Web provider works properly through the LBR, by going to the test page at the URL http://lbr.abc.com:80/portalTools/builder/providers/<providerName>.
Reconnect M1 to the LBR.
Restart the middle-tier M2.
Configuring Custom Built Providers in a Multiple Middle-Tier Environment
A custom built provider is any Web provider that is not seeded by the OracleAS Portal installation, or created using OracleAS Portal. To configure the custom built provider, you must deploy it on the first middle-tier, and register it to OracleAS Portal, using the M1 URL (http://m1.abc.com:7777/<webApp>/providers/<providerName>. To configure it to work in the multiple middle-tier environment, you must perform the following steps:
Configure the custom built provider to use a shared Preference Store. Refer to the steps in the section, Configuring Portal Tools Providers in the Multiple Middle-Tier Environment, in this document.
More information on configuring the database Preference Store can be found in the PDK article titled "Installing the DBPreferenceStore Sample (V2)", located at http://portalstudio.oracle.com/pls/ops/docs/FOLDER/COMMUNITY/PDK/jpdk/v2/doc/dbPreferenceStore/installing.db.preference.store.v2.html, on Portal Center at http://portalcenter.oracle.com.
Copy the ORACLE_HOME/j2ee/OC4J_Portal/applications/<webApp>/WEB-INF/providers/<providerName>/provider.xml from M1 to M2.
Click Edit Registration for the provider on the Providers tab of the Navigator, under Registered Providers. Then click the Connection tab, and change the first part of the provider registration URL from http://m1.abc.com:7777/ to http://lbr.abc.com
Verify that the custom built provider works properly through the LBR, by going to the test pages at the URL http://lbr.abc.com:80/<webApp>/providers/<providerName>
Configuring Load Balanced Session-Based Web Providers
To configure session-based Web providers, front-ended by a Load Balancing Router (LBR), the login frequency should be set to "Once Per User Session", on the provider information page, and the Load Balancing Router configured to do cookie-based routing. To set the login frequency, take the following steps:
Log in to OracleAS Portal. Click the Administer tab. On the Portal Builder page, click the Portlets tab.
Enter the provider information name in the field under Edit a Provider Registration, under Remote Providers.
Click Edit. On the Edit Provider Registration page, click the Connection tab. Set the Login Frequency to "Once Per User Session" under User/Session Information
Refer to the specific documentation of your LBR for information on how to configure an LBR to do cookie-based routing.
The Session Binding feature in OracleAS Web Cache is used to bind user sessions to a given origin server to maintain state for a period of time. Although almost all components running in a default OracleAS Portal middle-tier are stateless, session binding is required for two reasons:
The Web Clipping Studio, used by both the OracleAS Web Clipping Portlet and the Web Page Data Source of OmniPortlet, uses HTTP session to maintain state, for which session binding must be enabled. Refer to Appendix I, "Administering Web Clipping" for more information about Web Clipping.
Enabling session binding forces all the user requests to go to a given OracleAS Portal middle-tier, resulting in a better cache hit ratio for the portal cache. Refer to Section 1.3.2, "Understanding Portal Cache" for details on the portal cache.
|
Note: Regardless of whether you have configured an LBR in your topology, you must enable session binding in OracleAS Web Cache, if you have more than one middle-tier. In this configuration OracleAS Portal does not require session binding to be set up on the LBR. |
To make OracleAS Web Cache bind the portal user session to the OracleAS Portal middle-tier, perform the following steps:
In OracleAS Web Cache Manager on either M1, or M2, click Session Binding under Origin Servers, Sites, and Load Balancing.
In the Session Binding page, select the LBR site name (lbr.abc.com:80) in the table, and then click Edit Selected.
From the Please select a session drop-down list, change the session value to Any Set-Cookie.
From the Please select a session binding mechanism drop-down list, select Cookie-based.
Click Submit to apply the new settings to the site lbr.abc.com:80.
To save your configuration changes, click Apply Changes at the top of the page.
On the Cache Operations page, click Propagate to propagate the changes.
Click Restart to restart OracleAS Web Cache on M1 and M2.
To verify that your complete configuration is working as expected, perform the following steps:
To clear the contents stored in OracleAS Web Cache, restart M1 and M2, as follows:
Access the Application Server Control Console, typically located at http://m1.abc.com:1812.
Click the M1 instance.
Click Restart All.
Repeat the steps for M2.
Test access to OracleAS Portal through the LBR, by completing the following steps:
Access the OracleAS Portal home page at http://lbr.abc.com/pls/portal.
Click the portal login link.
Click some links in the portal.
Confirm that content is getting cached in OracleAS Web Cache. To do this, access the OracleAS Web Cache Manager on M1 as described in Oracle Application Server Web Cache Administrator's Guide.
Under Monitoring, click Popular Requests. Select Cached from the Filter Objects drop-down list, and click Update. If you accessed OracleAS Portal, you will see portal content (For example, URLs that contain /pls/portal).
Perform some simple page edits in OracleAS Portal, like adding a portlet to a page and make sure that the new content shows up. If the new content does not display properly, or if you see errors, OracleAS Web Cache invalidation is misconfigured.
The Oracle HTTP Server supports the configuration of virtual hosts. Virtual hosts allow a single machine to appear as any number of different sites. You can, for example, configure a machine to represent both www.abc.com, as well as www.xyz.com. Another example would be configuring a machine to represent both my.oracle.com, as well as oraclepartnernetwork.oracle.com. To configure virtual hosts with Oracle Application Server Portal, you must set this up on the Oracle HTTP Server. Additional Oracle Application Server Web Cache and Oracle Application Server Single Sign-On configuration is also required.
|
Note: If your intent is simply to change the hostname of your middle-tier, refer to the Oracle Application Server Administrator's Guide. |
Let's assume that your server name is www.abc.com, and you connect to OracleAS Portal at http://www.abc.com:7779/pls/portal. The IP address of the machine that the middle-tier is installed on is 196.12.67.8.
You want to access OracleAS Portal at http://www.abc.com:7779/pls/portal, using the real server name, as well as http://www.xyz.com:7779, using a virtual hostname, where both URLs resolve to the same IP address.
In this example, port 7779 is the OracleAS Web Cache listening port, and port 7778 is the Oracle HTTP Server listening port.
Let's also assume that the OracleAS Single Sign-On is installed on a different machine with the IP address 123.45.67.8, and accessed at the URL http://www.login.com:7777/pls/orasso.
|
Notes:
|
Figure 5-5 illustrates the previously described configuration. OracleAS Web Cache and the Oracle Application Server are shown as residing on the same middle-tier machine, although they can exist on different machines.
|
Note: The domain nameswww.abc.com, www.xyz.com, and www.login.com must be valid domain names, and you must be able to ping them.
|
To configure the virtual host, perform the following steps in the specified order:
You must create virtual hosts entries in the httpd.conf file for the virtual host name www.xyz.com, as well as for the real server name www.abc.com. To define the virtual hosts, use Oracle Enterprise Manager 10g Application Server Control Console to perform the following steps:
Once you have finished this step, do the following:
To create the virtual host for www.xyz.com:
Access the Oracle Enterprise Manager 10g Application Server Control Console.
Typically the Application Server Control Console is located at http://www.xyz.com:1812. Refer to Chapter 7, "Monitoring and Administering OracleAS Portal" for more information about using the Application Server Control Console.
Click the link for the middle-tier where OracleAS Portal is installed.
Click the HTTP Server link.
Click the Virtual Hosts link.
Click the Create button in the Virtual Hosts page.
On the Introduction page, click Next to create a new virtual host, using the Virtual Host Creation wizard.
On the General page, provide the information listed in Table 5-2.
Click Next.
On the Addresses Page, provide the following information in the Server Name field for your virtual host:
www.xyz.com
Select the option Listen on all the main server IP addresses.
Click Next.
On the Ports page, select Listen on a specific port, and select the Oracle HTTP Server listening port, 7778 in our example, from the port drop-down list.
Click Next.
On the Error Log page, select all default values.
Click Next.
Review the summary on the Summary page.
Click Finish.
When prompted to restart Oracle HTTP Server, click No.
Ensure that your server name, www.xyz.com, is listed in the table.
Click the Administration link.
Click Advanced Server Properties.
Select httpd.conf.
Add the Port and the Rewrite directives in the VirtualHost container, as follows (shown in bold text):
NameVirtualHost *:7778
<VirtualHost *:7778>
ServerName www.xyz.com
Port 7779
ServerAdmin you@your.address
RewriteEngine On
RewriteOptions inherit
</VirtualHost>
Click Apply.
When asked to restart Oracle HTTP Server, click No.
To create the virtual host for www.abc.com:
Follow steps 1 through 8 in Section 5.4.1.1, "Create the Virtual Host for www.xyz.com".
On the Addresses Page (Step 9), provide the following information in the Server Name field for your virtual host:
www.abc.com
Follow steps 10 through 24 in Section 5.4.1.1, "Create the Virtual Host for www.xyz.com".
When prompted to restart the Oracle HTTP Server, click Yes.
After configuring virtual hosts for www.abc.com and www.xyz.com, take a look at your httpd.conf file, using Application Server Control Console, as follows:
Access the Oracle Enterprise Manager 10g Application Server Control Console.
Click the link for the application server where OracleAS Portal is installed.
Click the HTTP Server link.
Click the Administration link.
Click Advanced Server Properties.
Select httpd.conf.
Your httpd.conf file should have the following new section:
NameVirtualHost *:7778 <VirtualHost *:7778> ServerName www.xyz.com Port 7779 ServerAdmin you@your.address RewriteEngine On RewriteOptions inherit </VirtualHost> <VirtualHost *:7778> ServerName www.abc.com Port 7779 ServerAdmin you@your.address RewriteEngine On RewriteOptions inherit </VirtualHost>
Entries for the virtual hosts can vary depending on the existing content of the httpd.conf file, but you must have virtual host entries for both www.abc.com and www.xyz.com.
|
Note: Thehttpd.conf file can also be updated manually. The file can be edited manually, to contain the right VirtualHost directives, as shown previously.
To synchronize the manual configuration changes done on the middle-tier, run
Finally, restart Oracle HTTP Server, by running the following command from
|
The site www.abc.com is already defined in OracleAS Web Cache. Additionally, you must create a site alias in OracleAS Web Cache, to make the multiple virtual hosts transparent to the OracleAS Metadata Repository. Note that www.abc.com must be set up as a site, while www.xyz.com must be defined as a site alias. This way, invalidation messages sent to OracleAS Web Cache invalidate content that is cached for both sites.
|
See Also: Oracle Application Server Web Cache Administrator's Guide for information about setting up a site alias. |
For Single Sign-On in the Oracle Application Server Single Sign-On to work properly, it must always be referenced by any partner application with the same hostname in the URL. This is because cookies are sent back only to the host that generated them. So, in the preceding example, the OracleAS Single Sign-On must always be referenced as http://www.login.com. Therefore, you must register www.abc.com, and www.xyz.com as partner applications. To do this:
Add a partner application entry for www.abc.com, by running the script ptlconfig, as follows:
ptlconfig -dad portal -sso -host www.abc.com -port 7779
Add a partner application entry for www.xyz.com, by running the script ptlconfig, as follows:
ptlconfig -dad portal -sso -host www.xyz.com -port 7779
Run ssoreg to register the secured request with OracleAS Single Sign-On by configuring it as a partner application for www.abc.com. ssoreg is located on the middle-tier in MID_TIER_ORACLE_HOME/sso/bin.
The following example illustrates the usage of ssoreg on UNIX:
MID_TIER_ORACLE_HOME/sso/bin/ssoreg.sh -site_name www.abc.com -mod_osso_url http://www.abc.com:7779 -config_mod_osso TRUE -oracle_home_path MID_TIER_ORACLE_HOME -config_file MID_TIER_ORACLE_HOME/Apache/Apache/conf/osso/osso.conf -admin_info cn=orcladmin
On Windows, you must run ssoreg.bat instead. Refer to Oracle Application Server Single Sign-On Administrator's Guide for more information.
Register the secured request with OracleAS Single Sign-On by configuring it as a partner application for www.xyz.com, using the virtual host mode of ssoreg, as shown in the following example:
MID_TIER_ORACLE_HOME/sso/bin/ssoreg.sh -site_name www.xyz.com -mod_osso_url http://www.xyz.com:7779 -config_mod_osso TRUE -oracle_home_path MID_TIER_ORACLE_HOME -config_file MID_TIER_ORACLE_HOME/Apache/Apache/conf/osso/osso_xyz.conf -admin_info cn=orcladmin -virtualhost
Note that the -config_file parameter refers to the file osso_xyz.conf.
You must edit the Virtual Host container for www.xyz.com as follows (changes shown in bold).
<VirtualHost *:7778>
ServerName www.xyz.com
Port 7779
ServerAdmin you@your.address
RewriteEngine On
RewriteOptions inherit
OssoConfigFile MID_TIER_ORACLE_HOME/Apache/Apache/conf/osso/osso_xyz.conf
OssoIpCheck off
</VirtualHost>
Refer to the information on registering mod_osso in the Oracle Application Server Single Sign-On Administrator's Guide.
To verify that the virtual hosts are set up correctly, connect to OracleAS Portal using either of the following URLs:
http://www.abc.com:7779/pls/portal
http://www.xyz.com:7779/pls/portal
You should get a login screen at http://www.login.com on the first login and must be able to log in successfully. A subsequent login from the other virtual host should result in a successful single sign-on without a prompt for login credentials.
You can configure OracleAS Portal to use proxy servers to connect to providers and Web sites outside of your firewall.
|
Notes:
|
To specify a proxy server:
In the Services portlet, click Proxy Settings.
The Services portlet is on the Administer tab of the Builder page.
In the HTTP Proxy Host field, enter the address for the HTTP proxy server that you want to use to access applications outside your firewall, for example, myproxy.mycompany.com. Do not prefix http:// to the proxy server name.
In the Port field, enter the port number for the proxy server. The port number defaults to 80 if no value is specified.
|
Note: Contact your server administrator for the names of servers running proxy software and their port numbers. |
Click Add.
You can now use this proxy server for connections between the portal and Web providers. You can also use this proxy for other connections, for example, to connect to the URLs specified for URL items.
In the Select Proxy section, choose the proxy server you want to use for such connections. Choose None if you do not want to use a proxy server for non-provider connections.
In the No Proxy Servers for Domains beginning with field, enter the domains for which the proxy server should not be used.
|
Note: The domains must begin with a period (.), for example,mycompany.com. Separate multiple domains with a comma (,).
|
Click OK.
You'll find additional information about how to set up proxy servers in the paper "A Primer on Proxy Servers," on OTN, http://www.oracle.com/technology/.
A reverse proxy server is a host process that is used as part of a firewall architecture to isolate the internal hosts from the externally accessible host(s). It does this by providing a proxy through which external requests must pass to access internal services. Typically, a proxy server takes the form of a dual-homed host. This means that it is a host with two network interface cards. One interface connects to the external network, and the other interface connects to the internal network, or demilitarized zone (DMZ) of the firewall.
Figure 5-6 shows an architecture in which the browser accesses the server through the hostname that is published by the proxy server. The proxy server then forwards the request to the actual host within the firewall.
|
Caution: For this configuration to work properly, you must first configure OracleAS Single Sign-On to work with the reverse proxy server. Information on deploying OracleAS Single Sign-On with a proxy server can be found in the Oracle Application Server Single Sign-On Administrator's Guide. |
Figure 5-6 Reverse Proxy Server Configuration
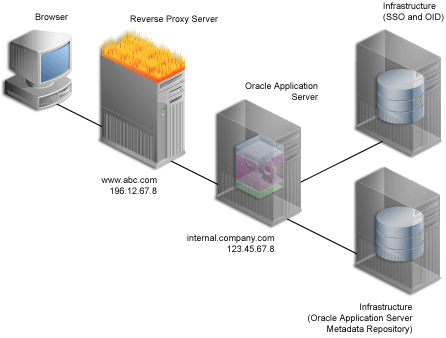
For this example, let's assume the following:
| Property | Value |
|---|---|
| External server name | www.abc.com
|
| External server port | 80
|
| OracleAS Web Cache server name (internal server) | internal.company.com
|
| OracleAS Web Cache listening port (internal server) | 7777
|
| OracleAS Web Cache administration port (internal server) | 4000
|
| OracleAS Web Cache invalidation port (internal server) | 4001
|
|
Note: The name and port values used in this section are for illustration purposes only and you will need to substitute these with your own. |
Complete these steps to configure OracleAS Portal for the architecture shown in Figure 5-6 in the order specified:
On the middle-tier, set the ServerName directive to point to the server name of the reverse proxy, so that self-referential URLs rendered on OracleAS Portal pages are valid for the browser. To do this, perform the following steps:
Define a virtual host, using the Create Virtual Host wizard, as explained in Section 5.4.1.1, "Create the Virtual Host for www.xyz.com", with the following exceptions:
Define a virtual host, using the Create Virtual Host wizard, as explained in Section 5.4.1.1, "Create the Virtual Host for www.xyz.com", with the following exceptions:
To improve performance, and to ensure that seeded providers work correctly, the local HOSTS file must be used to resolve domain names that are not normally visible to the internal network. For more information about this loopback connection, refer to Section 1.2.2.2, "How Does Communication Flow in OracleAS Portal?".
For example, the Oracle Application Server host for internal.company.com makes requests to itself, but the URLs that it is requesting are referring to www.abc.com. You must create host entries in the local HOSTS file on that machine, allowing it to resolve this name within the firewall. The hosts entry for this example should include the following lines:
# This is a sample HOSTS file used by Microsoft TCP/IP # for Windows NT/2000. 127.0.0.1 localhost 123.45.67.8 www.abc.com
If you do not provide these entries in the local HOSTS file, then you need to set the Oracle Application Server host to recognize a proxy server that would take the request out to the Internet and back in through the reverse proxy (www.abc.com), or configure the reverse proxy server's internal interface to respond to www.abc.com.
|
Note: On some platforms, such as HP, there is a file that indicates the search order that should be applied to the sources for IP name mapping. For the preceding example to work, if such a file exists on your platform, make sure that it specifies the local hosts file to be checked for IP mapping, before any DNS servers. |
Typically, the hostname and port number, by which OracleAS Portal is addressed, uses the OracleAS Web Cache hostname and port number. This is because, in a simple configuration, browser requests go directly to OracleAS Web Cache. However, in a configuration that has a reverse proxy server front-ending OracleAS Web Cache, the hostname and port number defined should reflect that of the reverse proxy server.
In this configuration, you want OracleAS Web Cache invalidation messages to be sent directly to the OracleAS Web Cache host, as opposed to the reverse proxy server. In the scenario where your published hostname is different from the hostname used for OracleAS Web Cache invalidation, you can use the Portal Dependency Settings file, to establish these settings.
To configure this appropriately, perform the following steps:
Edit iasconfig.xml (located by default in ORACLE_HOME/portal/conf) and specify a new property, InvalidationHost, within the WebCacheDependency element. The InvalidationHost property should point to the OracleAS Web Cache host. A sample WebCacheDependency entry in iasconfig.xml would look like this:
<WebCacheDependency ContainerType="IASInstance" Name="iAS-1" InvalidationHost="internal.company.com"/>
To prevent access to Oracle Enterprise Manager 10g from the outside, the Oracle Enterprise Manager 10g link provided by OracleAS Portal needs to be changed back to point to the internal server. To do this, edit iasconfig.xml and:
Add a new IASInstance element pointing to the OracleAS Web Cache host. This element should contain the EMComponent entry.
Set the EMDependency entry to point to the internal server.
An example is shown here:
<IASInstance Name="iAS.internal.company.com" Host="internal.company.com"> <EMComponent ConsoleHTTPPort="1814" SSLEnabled="false"/> </IASInstance> <PortalInstance DADLocation="/pls/portal" SchemaUsername="portal" SchemaPassword="@Beyh8p2bOWELQCsA5zRtuYc=" ConnectString="cn=iasdb,cn=oraclecontext">
<EMDependency ContainerType="IASInstance" Name="iAS.internal.company.com"/> </PortalInstance>
Run ptlconfig (typically located in the directory MID_TIER_ORACLE_HOME/portal/conf) as shown in the following example:
ptlconfig -dad portal -site -wc -em
Optionally, re-register the Wireless gateway URL with the load-balancer's address. See Section 5.10, "Configuring OracleAS Wireless" for more information.
|
See Also:
|
To configure the seeded providers (WebClipping and OmniPortlet), and locally hosted Web providers, you must take the following steps:
Log in to OracleAS Portal as the administrator (for example, PORTAL).
Click the Administer tab.
Click the Portlets sub-tab.
In the Remote Providers portlet, enter WEBCLIPPING in the Name field.
Click Edit.
Click the Connection tab.
In the URL field, change the URL from:
http://www.abc.com:80/portalTools/webClipping/providers/webClipping
to:
http://www.abc.com:7777/portalTools/webClipping/providers/webClipping
Click OK to commit the change.
When you register locally hosted Web providers (such as the JPDK Sample provider), you need to register them using HTTP as the protocol, www.abc.com as the hostname, and 7777 as the port number. This restriction only applies to locally hosted Web providers (that is, Web providers running on the same middle-tier as OracleAS Portal).
For example, to register the JPDK Sample provider, the URL is:
http://www.abc.com:7777/jpdk/providers/sample
|
Note: If your infrastructure is located on a separate machine than your OracleAS Portal middle- tier, you need to add the following to your/etc/host file:
where |
Register the www.abc.com domain name on a domain name server on the Internet, with IP address 196.12.67.8.
|
Note: In order for OracleAS Portal to work with a reverse proxy server, the reverse proxy server must preserve the incoming Host HTTP request header from the client. If this is not the default setting in your proxy server, refer to the configuration manual of the reverse proxy to set this. For example, if you are using mod_proxy in Apache 2.0, you will need to set the ProxyPreserveHost directive to On. |
You can now access OracleAS Portal at http://www.abc.com/pls/portal.
|
Notes:
|
Oracle Application Server Web Cache offers caching, page assembly, and compression features. OracleAS Web Cache accelerates the delivery of both static and dynamic Web content, and provides load balancing and failover features for Oracle Application Server. For an overview of how caching works in OracleAS Portal, refer to Section 1.3, "Understanding Caching in OracleAS Portal".
This section discusses how to configure OracleAS Portal to work with OracleAS Web Cache.
This section contains the following topics:
In previous releases, you had to use OracleAS Web Cache Manager to configure OracleAS Web Cache. In this release, you have two choices:
You can use Oracle Enterprise Manager 10g Application Server Control Console to configure OracleAS Web Cache along with other Oracle Application Server components. Refer to Oracle Application Server Web Cache Administrator's Guide for more information.
You can continue to use standalone tool OracleAS Web Cache Manager. Refer to Oracle Application Server Web Cache Administrator's Guide for more information.
These interfaces enable you to update to the OracleAS Web Cache configuration file, webcache.xml.
Use the Application Server Control Console to change OracleAS Web Cache settings that OracleAS Portal uses, such as the hostname, and the invalidation port number. You configure these settings on the Portal Web Cache Settings page.
When you change OracleAS Web Cache properties in the Portal Web Cache Settings page, the properties are saved to iasconfig.xml, but not to the webcache.xml file. You must either navigate back to the Web Cache Administration page in Application Server Control Console, or click the Web Cache Administration link to start OracleAS Web Cache Manager to make the appropriate changes.
|
See Also: Section 7.3.3, "Portal Web Cache Settings" for a detailed description of how to use the Portal Web Cache Settings page. |
From the OracleAS Portal user interface, you can perform various other tasks to manage Portal content cached in OracleAS Web Cache. You can either clear the entire Portal content cached in OracleAS Web Cache, or clear content for each Portal user.
|
Caution: Clearing the cache results in cache misses on subsequent requests and may degrade the portal's performance until the cache is repopulated. |
You may want to clear the cache if a user's group membership has changed, to remove the cache entries for that user, so that he or she has new privileges. Similarly, if you change a user or group's privileges on an object, you can clear the cache entries for that object.
To clear the entire cache, or to clear the cache for a particular user, you must be the portal administrator. To clear the cache for a particular portal object, you must have at least Manage privileges on the object.
The following sections describe the actions that can be performed using OracleAS Portal in more detail:
You can clear the entire Web Cache by performing the following steps:
In the Services portlet, click Global Settings.
By default, the Services portlet is on the Portal sub-tab of the Administer tab on the Portal Builder page.
Click the Cache tab.
Select Clear The Entire Web Cache.
Click Apply or OK to clear the cache.
|
Note: This clears all the page URLs and style sheets but not the Portal images. |
You can clear the cache for a particular user by performing the following steps:
In the Services portlet, click Global Settings.
By default, the Services portlet is on the Portal sub-tab of the Administer tab on the Portal Builder page.
Click the Cache tab.
In the Clear Cache For User field, enter the name of the user for whom you want to clear the cache.
|
Note: If you are not sure of the user name, click the Browse Users icon and select from the list provided. |
Click Apply or OK to clear the cache for the specified user.
|
Note: Alternatively, you can clear the cache for a particular user by editing the user's portal profile. |
With invalidation-based caching, a cache entry is purged when the portal or a provider sends a message informing OracleAS Web Cache that the object has changed (for example, when an item is edited). However you can also set an expiry time for cache entries. A cache entry that reaches this time limit is purged, even if OracleAS Web Cache has not received an invalidation message for it.
|
Note: To set the expiry time for invalidation-based cache entries, you must be the portal administrator. |
To set the expiry time for invalidation-based cache entries:
In the Services portlet, click Global Settings.
By default, the Services portlet is on the Portal sub-tab of the Administer tab on the Portal Builder page.
Click the Cache tab.
In the Maximum Expiry Time field, enter the maximum amount of time (in minutes) a cache entry should remain in the cache before being purged.
Click OK.
You can clear cache entries for page groups, pages, page templates, portlets in the Portlet Repository, Portal database providers, and Portal database provider components, by performing the following steps:
In the Navigator, drill down to the object with which you want to work.
For page groups, pages, and page templates, click Properties, then click the Access tab.
For Portal database providers, and Portal database provider components, click Grant Access.
For portlets, click Edit Root Page next to the Portlet Repository page group, drill down to the page that contains the portlet, edit the portlet, and click the Access tab.
Click Clear Cache.
Click OK.
Sometimes, the cache invalidation queue can grow excessively large as a result of user actions. For example, repeated granting of security privileges on a page to a group with a large number of members will place one soft invalidation in the queue for every user for every grant.
Some soft invalidations may not be necessary, but OracleAS Portal may not be able to determine this. For example, if a group's privileges on a page are upgraded from View to Fully Customize, and no member of the group has viewed the page yet, then no invalidation is necessary. However, Portal does not have a record of who has viewed the page. Therefore, it proceeds with the soft invalidation configured to use the security change.
The Portal administrator can check the number of soft invalidations in the queue by executing the following query in SQL*PLUS as the Portal schema owner:
select count(1) from wwutl_cache_inval_msg$ where process_type=2;
The Portal administrator can check the total number of invalidations, hard or soft, in the queue by executing the following query in SQL*PLUS as the Portal schema owner:
select count(1) from wwutl_cache_inval_msg$;
The number of rows in the table wwutl_cache_inval_msg$ that can be considered excessive depends, to some extent, on the speed of the infrastructure running the database. Typically, 50000 messages will slow down the soft invalidation job, and sending 50000 invalidation messages to OracleAS Web Cache will introduce a network load, as OracleAS Portal communicates with the OracleAS Web Cache invalidation port.
If the soft invalidations are found to be unnecessary, the Portal administrator can perform the following query in SQL*PLUS as the Portal schema owner:
delete from wwutl_cache_inval_msg$ where process_type=2;
This removes soft invalidations from the queue.
If the soft invalidations are necessary but there is an excessively large number, the Portal administrator can clear the cache invalidation queue using the following command:
truncate table wwutl_cache_inval_msg$;
The Portal administrator should then clear the entire cache through the Portal UI as described in Section 5.7.3.1, "Clearing the Entire Web Cache".
OracleAS Portal uses invalidation messages to expire objects in the cache. You can use the cachjsub.sql script to configure the frequency at which the invalidation job executes. Refer to Section C.1, "Managing the Invalidation Message Processing Job Using cachjsub.sql" for more information and instructions on how to run cachjsub.sql.
You can deploy OracleAS Web Cache on a dedicated server that front-ends one or more OracleAS Portal middle-tier servers. OracleAS Web Cache performs well even on commodity hardware, so a dedicated deployment does not have to be costly in terms of hardware expenditure. In general, it is recommended to use a computer with 1 GB of memory. Both the cache server and middle-tier server need to use a high speed network card to ensure site performance. For an overview of how caching works in OracleAS Portal, refer to Section 1.3, "Understanding Caching in OracleAS Portal".
To set up this topology, the administrator of the Web site needs to disable the OracleAS Web Cache that was installed on the same computer as OracleAS Portal middle-tier, and set up a new OracleAS Web Cache instance on a dedicated server. Figure 5-7 illustrates the topology where OracleAS Portal uses a dedicated OracleAS Web Cache instance.
Figure 5-7 OracleAS Portal Using a Dedicated OracleAS Web Cache instance
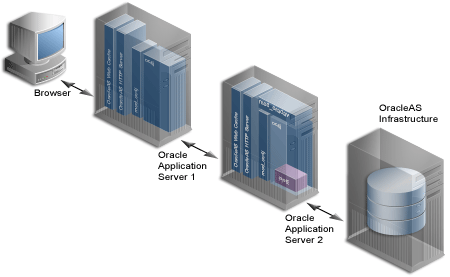
For the OracleAS Portal middle-tier, you must install OracleAS Infrastructure first, and then the Portal and Wireless middle-tier.
After installing the OracleAS Infrastructure and middle-tier on their respective servers, install J2EE and Web Cache middle-tier on the dedicated server.
You can also install a standalone version of OracleAS Web Cache from: http://www.oracle.com/technology/software/products/ias/web_cache/index.html
Oracle Universal Installer automatically configures and starts OracleAS Portal middle-tier and OracleAS Web Cache on the same computer during the OracleAS Portal and Wireless middle-tier installation. You need to disable the OracleAS Web Cache installed on the OracleAS Portal middle-tier computer that is not used, and configure the dedicated OracleAS Web Cache installed on a different computer to communicate with OracleAS Portal middle-tier.
Configuring a dedicated OracleAS Web Cache for Web site: www.company.com, port number: 7777 involves the following six tasks:
Task 1: Verify That the OracleAS Web Cache on the Dedicated Server Is Running
Task 2: Configure OracleAS Web Cache on the Dedicated Server
Task 3: Stop the Unused OracleAS Web Cache on the Middle-Tier Server
Task 4: Configure OracleAS Portal Middle-Tier with OracleAS Web Cache Settings
Task 5: Configure Virtual Host Settings for Oracle HTTP Server
To properly configure OracleAS Web Cache on the dedicated server, OracleAS Web Cache needs to be up and running. Refer to the Oracle Application Server Administrator's Guide for information on how to start, stop, restart, and view the status of OracleAS Web Cache on the Application Server Control Console home page.
You must manually configure OracleAS Web Cache on the dedicated server to properly deliver content to OracleAS Portal middle-tier on a different computer. You must make appropriate changes in Origin Servers page from OracleAS Web Cache Manager, (Origin Servers, Sites, and Load Balancing > Origin Servers) and the Listen Ports page (Ports > Listen Ports).
To properly configure OracleAS Web Cache, installed on the dedicated server, you will need the origin server information from the OracleAS Web Cache installed on the same computer as OracleAS Portal middle-tier.
To modify the origin server properties setting from the dedicated OracleAS Web Cache instance:
Make a backup copy of the webcache.xml file, located in the ORACLE_HOME/webcache directory.
In OracleAS Web Cache Manager on the dedicated computer, click Origin Server under Origin Servers, Sites, and Load Balancing.
In the Origin Servers page, select the Host and click Edit.
Modify the Application Web Servers properties for the dedicated OracleAS Web Cache using the value copied from the same page on the OracleAS Web Cache instance that was installed on the middle-tier computer. Use the online help for guidance on changing the default Application Web Servers properties.
Click OK.
Click Restart Web Cache.
You must manually configure OracleAS Web Cache on the dedicated server to create a site definition that includes a host name www.company.com, and a listening port number 7777. You must make appropriate changes in the Site Definitions page from OracleAS Web Cache Manager (Origin Servers, Sites, and Load Balancing > Site Definitions).
This task is optional. To save resources on the OracleAS Portal middle-tier server, follow the instructions in Oracle Application Server Administrator's Guide to stop the unused cache on the middle-tier server. This cache instance will not be used for this deployment option.
OracleAS Portal middle-tier needs to know the OracleAS Web Cache Listen ports, the invalidator username, invalidator password settings, and so on. You need to apply the new hostname and port number of the dedicated OracleAS Web Cache to OracleAS Portal middle-tier by modifying these settings in the Portal Web Cache Settings page:
From the Application Server home page on the Application Server Control Console in Oracle Enterprise Manager 10g, click Portal in the System Components section. The OracleAS Portal Home page appears.
Click the Portal Web Cache Settings link from the Administration section. The Portal Web Cache Settings page appears.
On the Portal Web Cache Settings page, modify the Published Host field with proper host name: www.company.com, modify the Listening Port field with proper port number 7777.
Review the other Web Cache Settings, like Invalidation Host, to match the cache information on the dedicated server and click Apply. A confirmation page appears. See the online help for guidance on changing the default ports and password settings.
You must create virtual host entries in the httpd.conf file of the Oracle HTTP Server that is part of the OracleAS Portal middle-tier, with the dedicated OracleAS Web Cache settings. In this example, you will set up virtual host name www.company.com and port number 7777 (same as the dedicated OracleAS Web Cache Listen port). The virtual host name and port number must be consistent with the site definition value defined in OracleAS Web Cache. To do this, perform the following tasks:
Configure Virtual Hosts Settings, as follows:
From the Application Server home page on the OracleAS Portal middle-tier server, on the Application Server Control Console, click HTTP_Server in the System Components section.
The HTTP Server Home page is displayed.
Click the Virtual Hosts tab.
Click Create.
On the Introduction page, click Next to create a new virtual host, using the Virtual Host Creation wizard.
On the Create Virtual Host: General page, choose name-based for Virtual Host Type, click Next.
On the Create Virtual Host: Addresses page, enter www.company.com in the Server Name field for your virtual host.
Select the Listen on all the main server IP addresses option, and click Next.
On the Create Virtual Host: Ports page, select Listen on a specific port, and select the Oracle HTTP Server Listen port, for example, 7778, from the port list.
Click Next, and click Next again on the Create Virtual Host: Error Log page.
Review the summary on the Summary page, and then click Finish. A Confirmation page appears.
When prompted to restart the Oracle HTTP Server, click No.
Ensure that your server name, www.company.com, is listed in the table.
Configure the newly created Virtual Host, as follows:
Click the Administration tab from the HTTP Server Home page.
Click Advanced Server Properties.
Click httpd.conf.
Add the Port and the Rewrite directives in the VirtualHost container, as follows (shown in bold text):
NameVirtualHost *:7778
<VirtualHost *:7778>
ServerName www.company.com
Port 7777
RewriteEngine On
RewriteOptions inherit
</VirtualHost>
Click Apply.
When prompted to restart Oracle HTTP Server, click Yes.
You can verify the configuration by performing basic tests, such as navigating the Web site, or removing a portlet.
Oracle Application Server 10g enables you to change the OracleAS Infrastructure services (either Oracle Identity Management or OracleAS Metadata Repository) that a middle-tier uses. You can use this feature, for example, to move middle-tiers (and their applications) from stage to production. If you are changing the OracleAS Metadata Repository that your OracleAS Portal uses, then you will also need to move application-specific data stored in the stage OracleAS Metadata Repository to an OracleAS Metadata Repository in the production environment. Changing the Infrastructure services is convenient, if you need additional computers for the production environment. In a single step, you add a computer that already has a middle-tier and deployed applications. For instructions on how to change the Infrastructure Services used by a middle-tier instance, refer to the Oracle Application Server Administrator's Guide.
|
Note: By default, an OracleAS Portal middle-tier is made up of one portal instance. Both the DAD name and the OracleAS Metadata Repository schema name for this instance are portal. You can only change the Infrastructure services of this default OracleAS Portal instance in the previously described way. |
If Oracle Application Server Wireless is configured with OracleAS Portal during the middle-tier installation, the middle-tier installation registers the Portal on the OracleAS Wireless service. In case of multiple middle-tier installs, the first configured OracleAS Wireless service URL is stored in the OracleAS Portal instance. You can change this to your choice of OracleAS Wireless service by running the portalRegistrar script in the Oracle Application Server middle-tier selected for the OracleAS Wireless service:
On UNIX:
ORACLE_HOME/wireless/bin/internal/portalRegistrar.sh
On Windows:
ORACLE_HOME\wireless\bin\internal\portalRegistrar.bat
Specify the following arguments when running the portalRegistrar script:
admin_user - User name of the Oracle Application Server administrator (typically orcladmin).
url - The URL to the device portal. For example, http://lbr.abc.com).
Usage Example
ORACLE_HOME/wireless/bin/internal/portalRegistrar.sh orcladmin http://lbr.abc.com
|
Note: If you did not configure OracleAS Wireless during installation, you can use Application Server Control Console to deploy OracleAS Wireless on the middle-tier. Refer to Section 7.2.2, "Using Application Server Control Console to Configure OracleAS Portal" for similar steps used to configure OracleAS Portal. |
For information about changing the OracleAS Portal schema password, refer to the Oracle Application Server Administrator's Guide.
|
Note: By default, an OracleAS Portal middle-tier is made up of one portal instance. Both the DAD name and the OracleAS Metadata Repository schema name for this instance are portal. You can only change the schema password of this default OracleAS Portal instance in the previously described way. |