| Oracle® Access Manager Integration Guide 10g (10.1.4.0.1) Part Number B25347-01 |
|
|
View PDF |
| Oracle® Access Manager Integration Guide 10g (10.1.4.0.1) Part Number B25347-01 |
|
|
View PDF |
This chapter describes the integration of Oracle Access Manager 10g (10.1.4.0.1) with the Siebel 7 e-business platform. Siebel 7 is a Web-based suite that combines customer relationship management, partner relationship management, and employee relationship management applications.
This chapter covers the following topics:
The integration of Oracle Access Manager with Siebel 7 provides a secure Web-based infrastructure for identity management for all customer applications and processes. Oracle Access Manager integrates identity and access management across Siebel 7, enterprise resources, and other domains deployed on eBusiness networks. Oracle Access Manager provides the foundation for managing the identities of customers, partners, and employees across Internet applications. These user identities are combined with security policies for protected Web interaction.
This integration adds the following features to Siebel 7 implementations:
Oracle Access Manager authentication, authorization, and auditing services for Siebel 7 applications.
Oracle Access Manager single sign-on (SSO) for Siebel 7 applications and other Oracle Access Manager-protected resources within a single domain or across multiple domains.
Oracle Access Manager authentication schemes, the following schemes provide single sign-on for Siebel 7 applications:
Basic: Users must enter a user name and password in a window supplied by the Web server.
This method can be redirected to SSL.'
Form: This method is similar to the basic challenge method, but users enter information in the custom HTML form.
You can choose the information users must provide in the form that you create.
X509 Certificates: X.509 digital certificates over SSL.
A user's browser must supply a certificate.
Integrated Windows Authentication (IWA): Users will not notice a difference between an Oracle Access Manager authentication and IWA when they log on to the desktop, open an Internet Explorer (IE) browser, request a Oracle Access Manager-protected Web resource, and complete single sign-on.
Microsoft .NET Passport: .NET Passport is a component of the Microsoft .NET framework.
The plug-in is a Web-based authentication service that provides single sign-on for Microsoft-protected Web resources.
Custom: Additional forms of authentication can be incorporated through use of the Oracle Access Manager Authentication Plug-in API.
Session timeout: Oracle Access Manager enables you to set the length of time that a user session is valid.
Ability to use the Identity System for identity management: The Identity System provides identity management features such as portal inserts, delegated administration, workflows, and self-registration to applications such as Siebel 7.
The self-registration feature for new users and customers provides flexibility in terms of how much access to provide to people upon self-registration. Identity System workflows enable a self-registration request to be routed to appropriate personnel before access is granted.
Oracle Access Manager also provides self-service, allowing users to update their own identity profiles.
This integration involves the following Siebel 7 components.
Siebel Gateway Name Server: The name server provides persistent backing of Siebel server configuration information, including definitions and assignments of component groups and component operational parameters as well as Siebel server connectivity.
Siebel Database Server: The Siebel database server contains the data used by Siebel clients.
Siebel Server and Siebel Web Server Extension: The Siebel Server along with the Siebel Web Server Extensions supports Siebel Enterprise Web Applications.
The preferred method of Web single sign-on with Siebel 7 is achieved by passing a header variable populated with an attribute value that is stored in the LDAP directory. Oracle Access Manager authentication rules permit passing the appropriate HTTP header variable to Siebel 7. The WebGate intercepts the user's HTTP request and checks for a session cookie. If the cookie does not exist or it has expired, the user is challenged for credentials. Oracle Access Manager verifies the credentials, and if the user is authenticated, the WebGate redirects the user to the requested resource and passes the required header variable to the Siebel application. The Siebel application initiates a session which is kept at the Siebel Web Engine.
Figure 6-1 illustrates a scenario where the user authenticates to an Oracle Access Manager-protected resource and is granted access to a Siebel 7 application.
Process overview: Authentication with the integration
A user attempts to access content or an application on a server.
WebGate intercepts the request.
To determine if the resource is protected, WebGate checks the Access Server for a security policy.
The security policy consists of an authentication scheme, authorization rules, and allowed operations based on authentication and authorization success or failure.
If the resource is protected, WebGate checks for the user's session cookie.
If a valid session exists, WebGate passes the header variable to the Siebel server. If a valid session does not exist, WebGate prompts the user for credentials.
If the credentials are successfully validated, Oracle Access Manager executes the actions that are defined in the security policy and sets an HTTP header variable that maps to the Siebel user ID.
WebGate redirects the user to the requested Siebel resource.
The Siebel application recognizes the Oracle Access Manager header variable, authenticates the user, and initiates a session.
The header variable is stored in the Siebel Web Engine. The user can now access any resource that is protected by Oracle Access Manager, for example, a Siebel 7 Web application, without being prompted for credentials.
If the user is not authorized, the user is denied access and redirected to another URL as determined by the organization's administrator.
Any references to specific versions and platforms in this chapter are made for demonstration purposes.
To see the supported versions and platforms for this integration, refer to Metalink, as follows.
To view information on Metalink
Go to the following URL:
Click the Certify tab.
Click View Certifications by Product.
Select the Application Server option and click Submit.
Choose Oracle Application Server and click Submit.
Complete the following steps to prepare your environment for the integration.
Task overview: Prepare your environment for integration
Install a supported directory server according to vendor instructions.
Install a supported Web server according to vendor instructions.
Configure the Web browser to allow cookies according to vendor instructions.
Proceed to "Setting Up Oracle Access Manager Single Sign-on for Siebel Application Server".
Setting up Oracle Access Manager single sign-on for Siebel 7 requires the installation and configuration of several Siebel and Oracle Access Manager components.
Install and configure Siebel 7, as described in "Setting Up Siebel 7 for integration with Oracle Access Manager".
Install Oracle Access Manager and a WebGate, and configure access control policies to protect Siebel resources, as described in "Setting up Oracle Access Manager for Integration with Siebel 7".
Test the integration, as described in "Testing Integration Between Oracle Access Manager and Siebel".
Setting up Siebel 7 for integration involves the following steps.
To set up Siebel 7 for integration with Oracle Access Manager
Install the following Siebel components, as described in the Siebel documentation:
Siebel Gateway Server
Siebel Server
Siebel Database Server
Siebel Web Server Extension
Verify that Siebel eBusiness Applications and Web Server Extension are working properly.
Ensure that the Siebel client and the Siebel server are able to communicate with each other through TCP/IP, as described in the Siebel documentation.
Add at least three users to LDAP:
Test
The Siebel Anonymous User
The Siebel Application User
In addition to your regular users, Siebel uses two user accounts from the directory: Anonymous User and Application User. You also need to create an attribute in regular user accounts for storing the Siebel database user information. See the information on creating users in the directory in the Security Guide for Siebel eBusiness Applications for details.
Add user records in the Siebel database that correspond to the registered users.
You need a record in the Siebel database that corresponds to the test user that you created in the LDAP directory. You also must confirm that the seed data record exists for the Anonymous User for your Siebel customer or partner application. This database record must match the Anonymous User that you created in the LDAP directory. See the information on adding user records in the Siebel Database in the Security Guide for Siebel eBusiness Applications for details.
Table 6-1 describes the parameters to set for the eapps.cfg file. This file contains configuration details for the Siebel Web Server Extension component. It is located in the \BIN directory where the Siebel Web Server Extension is installed (for example, C:\sea704\SWEApp). You can add these parameters to the [Default] section or to the Siebel-specific application, for example, [/esales_enu].
Oracle recommends that you add these parameters to the specific Siebel eBusiness application section.
Table 6-1 eapps.cfg Parameters
| Parameter and value | Value | Notes |
|---|---|---|
|
AnonUserName |
GuestCST |
The anonymous user is a Siebel user with very limited access. It enables a user to access a login page or a page that contains a login form. This user is defined in the Siebel database and must exist in the LDAP directory. |
|
AnonPassword |
Ldap |
The LDAP password for the anonymous user. |
|
SingleSignOn |
TRUE |
When this parameter is set to true, the Siebel Web Server Extension Engine (SWSE) operates in WebSSO mode. |
|
TrustToken |
HELLO |
In a Web single sign-on environment, this token string is a shared secret between the SWSE and the security adapter. It is a measure to protect against spoofing attacks. This setting must be the same on both the SWSE and the security chapter. |
|
UserSpecSource |
Header |
In a Web single sign-on implementation, this parameter specifies the source from which the SWSE derives the user credentials, as follows:
|
|
UserSpec |
SSO_Siebel_User |
In a Web single sign-on implementation, this variable name specifies where the SWSE looks for a user's user name in the source provided by UserSpecSource. |
The following is an example of a configured eapps.cfg file:
[/esales_enu] SingleSignOn = TRUE TrustToken = HELLO UserSpec = SSO_SIEBEL_USER UserSpecSource = Header ConnectString = siebel.TCPIP.None.None://sdchs24n336:3320/siebel/eSalesObjMgr_enu StartCommand = SWECmd=GotoView&SWEView=Home+Page+View+(eSales) WebPublicRootDir = c:\19213\eappweb\public\enu WebUpdatePassword = tieeKaYLjfUBgdi+g==
Table 6-2 describes the parameters that you specify in the Siebel Application Parameter File (for example, siebel.cfg).
Table 6-2 Siebel Application Parameter File for the Web Server Extension Component
| Parameter | Value | Description |
|---|---|---|
|
ApplicationUser |
Cn=sadmin,cn=users,dc=us,dc=oracle,dc=com |
DN of Siebel Application User |
|
ApplicationPassword |
Ldap |
LDAP password |
|
BaseDN |
Cn=users,dc=us,dc=oracle, dc=com |
LDAP directory base DN |
|
CRC |
CRC code |
|
|
CredentialsAttribute |
|
LDAP attribute used to store the user's database credentials |
|
SecAdptDllName |
Sscfldap |
Security Adapter DLL |
|
HashAlgorithm |
RSASHA1 |
Hash algorithm |
|
HashDBPPwd |
FALSE |
Should the shared database password be hashed |
|
HashUserPwd |
FALSE |
Should the user's password be hashed by Siebel |
|
Port |
389 |
LDAP server port |
|
PropagateChange |
TRUE |
Propagate user changes to an external repository |
|
PasswordExpireWarning |
30 |
Number of days before password expiry, when the user should be warned. |
|
PasswordAttributeType |
UserPassword |
LDAP attribute used to store the user's password |
|
RolesAttributeType |
LDAP attribute used to store the user's responsibilities |
|
|
ServerName |
Ldap.us.oracle.com |
LDAP Server Name |
|
SharedCredentialsDN |
Cn=sadmin,cn=users,dc=us,dc=oracle,dc= com |
DN of LDAP user storing the DB credentials |
|
SiebelUsernameAttribute Type |
Uid |
LDAP attribute used to store the user's user ID |
|
SSLDatabase |
C:\oblix-data\oid-key |
Path of the SSL database certificate file (required if LDAPS is used) |
|
SingleSignon |
TRUE |
Is single sign-on enabled |
|
TrustToken |
HELLO |
Web single sign-on trust token |
To set the Siebel Server Configuration Parameters
Log in to a Siebel employee application, such as Siebel Call Center, and make one of the following choices from the application-level menu:
To set enterprise level parameters, choose View, select Site Map, then select Server Administration and then select Enterprise Configuration.
To set server level parameters, choose View, select Site Map, then select Server Administration and then select Servers.
To set component level parameters, choose View, select Site Map, then select Server Administration and then select Components.
If you are setting parameters at the server or component level:
To set enterprise-level parameters, click the Enterprise Parameters view tab.
To set server-level parameters, click the Server Parameters view tab.
To set component-level parameters, click the Component Parameters view tab.
Because application-level parameters override enterprise level settings, Oracle recommends that you set the Siebel parameters for SSO integration at the application level.
The following screen shot illustrates setting Siebel Server configuration parameters:
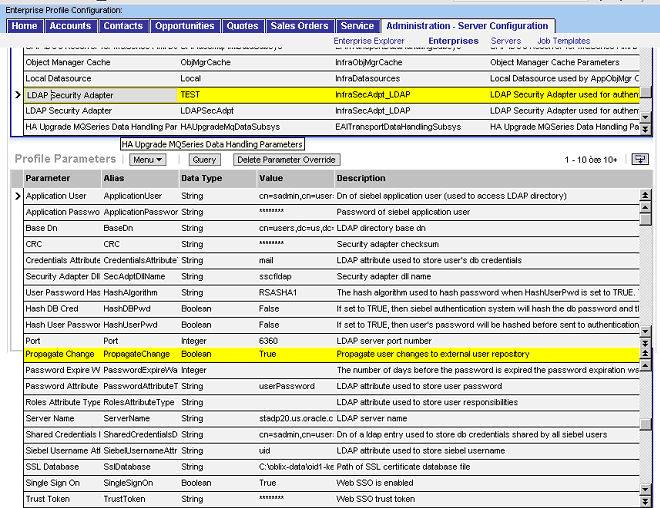
Select a parameter record, edit the Current Value field, and then click Save.
Restart the Siebel Server to allow the changes to take effect.
Setting up Oracle Access Manager for integration with Siebel 7 involves the following steps.
To set up Oracle Access Manager for the integration
Install Oracle Access Manager and ensure that you have installed a WebGate on the Web server instance supporting the Siebel Web server extension, as described in Oracle Access Manager Installation Guide
Synchronize the time on all servers where Siebel and Oracle Access Manager components are installed.
Each Siebel application has its own document directory. You can either protect each application individually or protect the higher-level directory under which the applications reside.
In the Policy Manager, create a policy domain to protect Siebel resources on Web servers where Siebel and the WebGate are installed, as described in the Oracle Access Manager Access Administration Guide
Oracle Access Manager sets header variables that are passed on to the Siebel eBusiness Application to allow access only to specified users.
In the Authorization Rule, choose Actions page of the policy domain protecting the Siebel resource, configure the action to map a Oracle Access Manager Header variable uid to the Siebel uid.
|
Note: The Header variable set in the Oracle Access Manager policy should be equal to the value of the UserSpec parameter in the eapps.cfg file. |
In the following example, the uid is mapped to the SSO_SIEBEL_USER HTTP header variable as follows:
Type: HeaderVar
Name: SSO_SIEBEL_USER
Attribute: uid
In the Authorization Rules, choose Allow Access page of the policy domain, select the Oracle Access Manager/Siebel users to whom you want to grant access to the resources that are protected by the policy domain.
After configuring the integration of Oracle Access Manager with Siebel, you should test for successful Oracle Access Manager authentication and single sign-on with Siebel 7.
The following is a test for single sign-on between a non-Siebel, Oracle Access Manager-protected Web page and Siebel Web Server Extension.
To test Oracle Access Manager single sign-on
Create an Oracle Access Manager policy domain to protect a Siebel eBusiness application (for example, eMarketing) and require basic LDAP authentication for it.
Open a Web browser and enter the URL for the IIS Web server's main page (http://hostname).
The main page is displayed. User authentication should not be required.
Access the Siebel eBusiness application URL for the IIS Web server from the same browser used in step 2.
Basic authentication should be required.
Access the Siebel eBusiness application URL for the IIS Web server from the same browser used in step 2.
Access to the Siebel eBusiness application should be allowed. The user should not be challenged for credentials.
Close the browser and open a new browser session. Access the Siebel eBusiness application URL for the IIS Web server.
Basic authentication should be required. After the user enters credentials, the Siebel eBusiness application should be displayed.
Access the demo document directory URL for the IIS Web server from the same browser user in step 5.
Repeat the previous steps for the Sun ONE Web server.
The following is a test of the Oracle Access Manager session timeout.
To test Oracle Access Manager session timeout
Configure the Oracle Access Manager session timeout to be five (5) minutes and restart the Web servers.
Open a Web browser and the IIS Web server's main page (http://hostname).
The main page is displayed. User authentication should not be required.
Access the Siebel eBusiness Application URL for the IIS Web server from the same browser used in step 2.
Basic authentication should be required. After the user enters credentials, the Siebel eBusiness application should be displayed.
Leave the browser window open and idle for more than five minutes.
Refresh the browser window using the Refresh button.
Basic authentication should be required. After the user enters credentials, the Siebel eBusiness Application should be displayed.
You can configure an expiration period for a session by setting a session timeout value in both Siebel and Oracle Access Manager. The timeout values should be the same for both applications. If you configure a timeout value for Siebel that is shorter than the one you configure for Oracle Access Manager, users can re-establish their Siebel session after it times out without providing login credentials.
The rest of this section discusses the following topics:
The following procedure describes configuring the timeout. For users to be asked to re-authenticate after the timeout limit is reached, you must also configure the same timeout value in Oracle Access Manager.
To configure the Siebel timeout
Open the eapps.cfg file.
It is located in the \BIN directory where the Siebel Web Server Extension is installed (for example, C:\sea704\SWEApp).
Modify the value for the Set SessionTimeout parameter.
Restart the Web server.
The following procedure describes configuring the timeout.
To configure the Oracle Access Manager session timeout
Log in to the Access System.
From the Access System Console, click Access System Configuration, then click AccessGate Configuration.
Search for the AccessGate that you want to configure.
Click the link for the AccessGate.
Click Modify.
Change the value of the Maximum user session time (seconds) field.
This value should be the same as the one that you set for the Siebel application.
Change the value of the Idle session time (seconds) field.
This value should be the same as the one that you set for the Siebel application.
In a Web single sign-on deployment, the user authentication and user management features are the responsibility of Oracle Access Manager. The following features in Siebel 7 are not available in a Web single sign-on environment:
User self-registration
Delegated administration
Login and logout
Change password
You can configure logout functionality for Siebel 7 users by modifying the Siebel Logout link and redirecting the users to the Oracle Access Manager logout page. By doing this, the user is logged out of Oracle Access Manager and by extension from Siebel.
You configure logout functionality from the Identity System Console. See the Oracle Access Manager Identity and Common Administration Guide for details.
The following procedures describe configuring the logout behavior.
To prepare for configuration
Create a text file that contains the HTML required to redirect the user to the Oracle Access Manager logout page.
The following is a URL example:
<a href=http://coreidserver.us.orcacle.com/access/oblix/lang/en-us/logout.html>
The following is a Javascript example:
<html>
<head>
<script language=ÓJavascriptÓ>
<!--//
window.location.href=http://coreidserver.us.oracle.com/access/oblix/lang/en-us/logout.html;
//-->
</script>
</head>
</html>
Copy the file as follows:
$siebelroot/siebsrvr\WEBTEMPL\name.swt
Where name is the name of the file that you created in the previous step, for example, coreidlogout.swt.
Stop the Siebel server process.
Start Siebel Tools.
To create a new project
In the Object Explorer window, click Project.
Select Edit.
Select New Record.
Enter the name of the file that contains the redirection information as the name for the new record.
Do not include the ".swt" extension. In the previous procedure, this name was coreidlogout.
Select Locked.
To create a Web template
In the Object Explorer window, click Web Template.
Add a new record.
Use the name of the file with the redirection information. Do not include the ".swt" extension.
In a previous procedure, an example name of coreidlogout was provided.
Enter the Project parameter.
As the name of this parameter, use the name of the file with the redirection information. Do not include the ".swt" extension.
In a previous procedure, an example name of coreidlogout was provided.
Specify Web Page Template for the Type parameter.
To create a Web template file
Expand the Web Template tree.
Click Web Template File.
Add a record that is named using the name of the file with the redirection information.
Do not include the ".swt" extension. In a previous procedure, an example name of coreidlogout was provided.
Enter the name of the file with the redirection information, including the ".swt" extension, as the Filename parameter.
To create a Web page for logout
In the Object Explorer window, click Web Page.
Add a record that is named using the name of the file with the redirection information.
Do not include the ".swt" extension. In a previous procedure, an example name of coreidlogout was provided.
Enter the name of the file with the redirection information as the Project parameter.
Do not include the ".swt" extension. In a previous procedure, an example name of coreidlogout was provided.
Select the name of the file with the redirection information as the Web Template parameter.
In a previous procedure, an example name of coreidlogout was provided.
To complete logout configuration
To lock the application project for each project where you want to modify the logout behavior, in the Object Explorer window, click Project.
Locate the appropriate project.
Select Locked.
In the Application window, select the Siebel module to be configured.
Each module must be configured separately.
Scroll to the right and locate the Logoff Acknowledgement Web Page parameter.
Make a note of this value before changing it.
Select the name of the file with the redirection information.
In a previous procedure, an example name of coreidlogout was provided.
Compile the changes.
Restart the Siebel Server and the Web server.