1 About the Connector
Oracle Identity Manager automates access rights management, security, and provisioning of IT resources. Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with external, identity-aware applications. This guide discusses the connector that enables you to use RSA Authentication Manager as a managed (target) resource of Oracle Identity Manager.
Note:
At some places in this guide, RSA Authentication Manager has been referred to as the target system.
In the account management (target resource) mode of the connector, information about users created or modified directly on the target system can be reconciled into Oracle Identity Manager. In addition, you can use Oracle Identity Manager to perform provisioning operations on the target system.
This chapter contains the following sections:
Certified Components
Table 1-1 lists the deployment requirements for the connector.
Table 1-1 Certified Components
| Item | Requirement |
|---|---|
|
You can use one of the following releases of Oracle Identity Manager:
|
|
|
RSA Authentication Manager 7.1 with SP3 or later. |
|
|
JDK |
The JDK requirement is as follows:
See Setting Values for JAVA_OPTIONS Parameters if you are using JDK 1.6. |
Certified Languages
The connector supports the following languages:
-
Arabic
-
Chinese Simplified
-
Chinese Traditional
-
Danish
-
English
-
French
-
German
-
Italian
-
Japanese
-
Korean
-
Portuguese (Brazilian)
-
Spanish
See Also:
For information about supported special characters supported by Oracle Identity Manager, see one of the following guides:
-
For Oracle Identity Manager release 9.1.0.x:
-
For Oracle Identity Manager release 11.1.1 and 11.1.2.x:
Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager
Connector Architecture
During user provisioning, adapters carry provisioning data submitted through the process form to the target system. RSA APIs accept provisioning data from the adapters, carry out the required operation on the target system, and return the response from the target system to the adapters. The adapters return the response to Oracle Identity Manager.
Token provisioning operations are performed in the same manner. A separate set of Oracle Identity Manager adapters is used during token provisioning operations.
If an operation involves provisioning of an RSA Authentication Manager account, token, role, or group, then the GUID of the object created on the target system is brought back to Oracle Identity Manager. For accounts and tokens, the GUID is stored in a hidden field on the process or child form and is used during update operations.
During reconciliation, the RSA Auth Manager User Recon scheduled task establishes a connection with the target system and sends reconciliation criteria to the RSA APIs. The APIs extract user records that match the reconciliation criteria and hand them over to the scheduled task, which brings the records to Oracle Identity Manager.
Note:
In Oracle Identity Manager release 11.1.1, a scheduled job is an instance of a scheduled task. In this guide, the term scheduled task used in the context of Oracle Identity Manager release 9.1.0.x is the same as the term scheduled job in the context of Oracle Identity Manager release 11.1.1 and 11.1.2.x.
See Oracle Fusion Middleware System Administrator's Guide for Oracle Identity Manager for more information about scheduled tasks and scheduled jobs.
The RSA Auth Manager User Recon scheduled task can be configured to reconcile token data. Alternatively, you can use the RSA Auth Manager Token Recon scheduled task for token reconciliation.
Note:
A maximum of 3 tokens can be assigned to a user on RSA Authentication Manager. This upper limit is also applied in Oracle Identity Manager.
Each user or token record fetched from the target system is compared with RSA users or RSA tokens provisioned to OIM Users. If a match is found, then the update made to the user or token on the target system is copied to the RSA user or RSA token in Oracle Identity Manager. If no match is found, then the user ID of the record is compared with the user ID of each OIM User. If a match is found, then data fetched from the target system user or token record is used to provision an RSA user or RSA token to the OIM User.
Figure 1-1 shows the connector integrating RSA Authentication Manager with Oracle Identity Manager.
Figure 1-1 Architecture of the Connector for RSA Authentication Manager
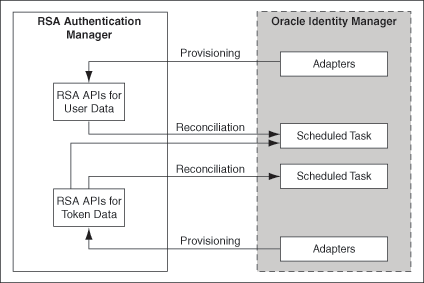
Description of "Figure 1-1 Architecture of the Connector for RSA Authentication Manager"
Features of the Connector
The following are features of the connector:
-
Support for Reconciliation and Provisioning of RSA Authentication Manager Accounts and Tokens
-
Mapping Standard and Custom Attributes for Reconciliation and Provisioning
Support for Reconciliation and Provisioning of RSA Authentication Manager Accounts and Tokens
You can use the connector to reconcile and provision RSA Authentication Manager accounts and tokens. The connector provides separate process forms and resource objects for user and token operations.
In RSA Authentication Manager, a user can be assigned up to 3 tokens. The connector enables the same feature in Oracle Identity Manager.
Mapping Standard and Custom Attributes for Reconciliation and Provisioning
You can create mappings for attributes that are not included in the list of default attribute mappings. These attributes can be custom attributes that you add on the target system.
See Chapter 4, "Extending the Functionality of the Connector" for more information.
Full and Incremental Reconciliation
In full reconciliation, all records are fetched from the target system to Oracle Identity Manager. In incremental reconciliation, only records that are added or modified after the last reconciliation run are fetched into Oracle Identity Manager.
You can switch from incremental to full reconciliation at any time after you deploy the connector. See Full Reconciliation for more information.
Batched Reconciliation
You can break down a reconciliation run into batches by specifying the number of records that must be included in each batch.
See Batched Reconciliation for more information.
Limited (Filtered) Reconciliation
To limit or filter the records that are fetched into Oracle Identity Manager during a reconciliation run, you can specify the subset of added or modified target system records that must be reconciled.
See Limited Reconciliation for more information.
Enabling and Disabling Accounts
Account Start and Account Expire are two user attributes on the target system. For a particular user on the target system, if the Account Expire date is less than the current date, then the account is in the Disabled state. Otherwise, the account is in the Enabled state. When the record of this user is reconciled into Oracle Identity Manager, the user's state (RSA resource) in Oracle Identity Manager matches the user's state on the target system. In addition, through a provisioning operation, you can set the value of the Account Expire date to the current date or a date in the past.
Note:
The Enabled or Disabled state of an account is not related to the Locked or Unlocked state of the account.
Reconciliation of Deleted User Records
The IsDeleteAllowed attribute of the RSA Auth Manager User Recon scheduled task is used to enable reconciliation of deleted user records. If you set the value of this attribute to yes, then the following events take place during a reconciliation run:
-
GUIDs of all existing users on Oracle Identity Manager are brought to the target system.
-
Each GUID brought from Oracle Identity Manager is matched against the GUIDs on the target system.
-
If a match is not found, then it is assumed that the user has been deleted on the target system. For this deleted user, the RSA Authentication Manager resource assigned to the corresponding OIM User is revoked. For each user resource that is revoked, the associated token resources are automatically revoked.
SOAP-Based Communication with the Target System
The connector supports SSL-secured SOAP-based communication between Oracle Identity Manager and the target system.
Configuring Connection Parameters provides more information.
Specifying Accounts to Be Excluded from Reconciliation
You can specify a list of accounts that must be excluded from all reconciliation operations. Data from accounts whose user IDs you specify in the exclusion list is not fetched to Oracle Identity Manager during reconciliation.
See Setting Up the Lookup.RSA.AuthManager.ExclusionList Lookup Definition for more information.
Transformation and Validation of Account Data
You can configure validation and transformation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning. The following sections describe the procedure:
Support for Setting a PIN and the Token Lost Attribute
From this release onward, you can use the connector to set the following:
-
A PIN for the token that is assigned to a user.
-
The Token Lost attribute when the token device is lost.
Lookup Definitions Used During Connector Operations
Lookup definitions used during connector operations can be categorized as follows:
Lookup Definitions Synchronized with the Target System
During a provisioning operation, you use a lookup field on the process form to specify a single value from a set of values. For example, you use the Identity Source lookup field to select an identity source during a provisioning operation performed through the Administrative and User Console. When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are automatically created in Oracle Identity Manager. Lookup field synchronization involves copying additions or changes made to the target system lookup fields into the lookup definitions in Oracle Identity Manager.
Note:
-
The target system allows you to use special characters in lookup fields. However, in Oracle Identity Manager, special characters are not supported in lookup definitions.
-
You use the RSA Auth Manager Lookup Recon scheduled task to synchronize these lookup definitions. Scheduled Task for Lookup Field Synchronization describes this scheduled task.
The following Oracle Identity Manager lookup definitions are synchronized with target system lookup fields:
Lookup.RSA.AuthManager.Group
The Lookup.RSA.AuthManager.Group lookup definition holds details of user groups defined on RSA Authentication Manager. You populate this lookup definition through lookup field synchronization performed using the RSA Auth Manager Lookup Recon scheduled task.
The following is the format of entries in this lookup definition:
-
Code Key:
IT_RESOURCE_KEY~GROUP_GUIDIn this format:
-
IT_RESOURCE_KEYis the key assigned to the IT resource on Oracle Identity Manager. -
GROUP_GUIDis the GUID of the group on the target system.
-
-
Decode:
IT_RESOURCE_NAME~GROUP_NAMEIn this format:
-
IT_RESOURCE_NAMEis the name assigned to the IT resource on Oracle Identity Manager. -
GROUP_NAMEis the name of the group on the target system.
-
The following table shows sample entries in this lookup definition:
| Code Key | Decode |
|---|---|
|
1~ ims.34590df69e3714ac01625e5d14325154 |
RSA Server Instance~Demo Agent4 Group |
|
1~ ims.6ddf54f39e3714ac0178e4628bbcd7f8 |
RSA Server Instance~Group111 |
|
1~ ims.6ddf93069e3714ac0173ec0a3d673569 |
RSA Server Instance~Group222 |
Lookup.RSA.AuthManager.IdentitySource
See Also:
In RSA Authentication Manager, an identity source can be the default internal database, an LDAP-based solution, or a database. The Lookup.RSA.AuthManager.IdentitySource lookup definition holds details of the identity sources configured for your target system installation.
The following is the format of entries in this lookup definition:
-
Code Key:
IT_RESOURCE_KEY~IDENTITY_SOURCE_GUIDIn this format:
-
IT_RESOURCE_KEYis the key assigned to the IT resource on Oracle Identity Manager. -
IDENTITY_SOURCE_GUIDis the GUID of the identity source on the target system.
-
-
Decode:
IT_RESOURCE_NAME~IDENTITY_SOURCE_NAMEIn this format:
-
IT_RESOURCE_NAMEis the name assigned to the IT resource on Oracle Identity Manager. -
IDENTITY_SOURCE_NAMEis the name of the identity source on the target system.
-
The following table shows sample entries in this lookup definition:
| Code Key | Decode |
|---|---|
|
1~ ims.000000000000000000001000d0011000 |
RSA Server Instance~Internal Database |
Lookup.RSA.AuthManager.SecurityDomain
In the RSA Authentication Manager context, security domains represent the internal business units, such as departments, of the organization. These security domains are organized in a hierarchy.
The Lookup.RSA.AuthManager.SecurityDomain lookup definition stores the GUID and name of these security domains.
The following is the format of entries in this lookup definition:
-
Code Key:
IT_RESOURCE_KEY~SECURITY_DOMAIN_GUIDIn this format:
-
IT_RESOURCE_KEYis the key assigned to the IT resource on Oracle Identity Manager. -
SECURITY_DOMAIN_GUIDis the GUID of the security domain on the target system.
-
-
Decode:
IT_RESOURCE_NAME~SECURITY_DOMAIN_NAMEIn this format:
-
IT_RESOURCE_NAMEis the name assigned to the IT resource on Oracle Identity Manager. -
SECURITY_DOMAIN_NAMEis the name of the security domain on the target system.
-
The following table shows sample entries in this lookup definition:
| Code Key | Decode |
|---|---|
|
1~ims.000000000000000000001000e0011000 |
RSA Server Instance~SystemDomain |
|
1~ims.6de7d3c19e3714ac017cfd3c69eec20e |
RSA Server Instance~Domain1 |
|
1~ims.6e3dc8939e3714ac02019a05130a8285 |
RSA Server Instance~Domain2 |
Lookup.RSA.AuthManager.AdminRole
On RSA Authentication Manager, an administrative role is a collection of permissions that can be assigned to an administrator. It determines the level of control the administrator has over users, user groups, and other entities.
The Lookup.RSA.AuthManager.AdminRole lookup definition stores details of administrative roles. The following is the format of entries in this lookup definition:
-
Code Key:
IT_RESOURCE_KEY~ROLE_GUIDIn this format:
-
IT_RESOURCE_KEYis the key assigned to the IT resource on Oracle Identity Manager. -
ROLE_GUIDis the GUID of the role on the target system.
-
-
Decode:
IT_RESOURCE_NAME~ROLE_NAMEIn this format:
-
IT_RESOURCE_NAMEis the name assigned to the IT resource on Oracle Identity Manager. -
ROLE_NAMEis the name of the role on the target system.
-
The following table shows sample entries in this lookup definition:
| Code Key | Decode |
|---|---|
|
1~ ims.000000000000000000001000e0031000 |
RSA Server Instance~SuperAdminRole |
|
1~ ims.000000000000000000001000e0031001 |
RSA Server Instance~TrustedRealmAdminRole |
Lookup.RSA.AuthManager.LookupReconMapping
The Lookup.RSA.AuthManager.LookupReconMapping lookup definition holds the names of lookup definitions that are synchronized with the target system when you run the RSA Auth Manager Lookup Recon scheduled task.
Table 1-2 shows the entries in this lookup definition.
Preconfigured Lookup Definitions
Table 1-3 describes the other lookup definitions that are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed.
Table 1-3 Preconfigured Lookup Definitions
| Lookup Definition | Description of Values | Method to Specify Values for the Lookup Definition |
|---|---|---|
|
On the Administrative and User Console, these lookup definitions are used to populate the Account Start Time and Account Expire Time lookup fields of the user process form. You use these lookup fields to select the time (in hours and minutes). Figure 3-6 shows the lookup fields for these lookup definitions on the Administrative and User Console. |
You must not modify these lookup definitions. |
|
|
This lookup definition is used during full reconciliation. |
You must not modify this lookup definition. |
|
|
This lookup definition holds connector configuration entries that are used during reconciliation and provisioning. |
Some of the entries in this lookup definition are preconfigured. Setting Up the Configuration Lookup Definition in Oracle Identity Manager provides information about the entries for which you can set values. |
|
|
This lookup definition stores values that are used internally by the connector. The connector development team can use this lookup definition to make minor configuration changes in the connector. |
You must not modify this lookup definition. |
|
|
This lookup definition holds entries that are used to format date values so that they are compatible with the date format used on the target system. This lookup definition is used during provisioning. |
You must not modify this lookup definition. |
|
|
This lookup definition holds user IDs of target system accounts for which you do not want to perform reconciliation and provisioning. |
You can enter user IDs in this lookup definition. See Setting Up the Lookup.RSA.AuthManager.ExclusionList Lookup Definition for more information. |
|
|
The connector uses the RemoteCommandTargetBean API of the target system to establish connections with the target system. The Lookup.RSA.AuthManager.ITResourceMapping lookup definition maps some of the IT resource parameters with parameters of this API. |
See Mapping New Connection Properties for information about existing entries and the procedure to add new entries in this lookup definition. |
|
|
This lookup definition holds mappings between the user process form fields and single-valued user attributes on the target system. |
This lookup definition is preconfigured. Table 1-9 lists the default entries in it. You can add entries in this lookup definition if you want to map new target system attributes for provisioning. See Adding New User or Token Attributes for Provisioning for more information. |
|
|
This lookup definition holds mappings between process form fields and multivalued target system attributes. It is used during provisioning. |
This lookup definition is preconfigured. Table 1-10 lists the default entries in it. |
|
|
This lookup definition holds mappings between resource object fields and multivalued target system attributes. It is used during reconciliation. |
This lookup definition is preconfigured. Table 1-5 lists the default entries in it. You can add entries in this lookup definition if you want to map new multivalued target system attributes for provisioning. |
|
|
This lookup definition holds mappings between the token process form fields and token attributes on the target system. It is used during provisioning. |
This lookup definition is preconfigured. Table 1-11 lists the default entries in it. You can add entries in this lookup definition if you want to map new target system attributes for provisioning. See Adding New User or Token Attributes for Provisioning for more information. |
|
|
This lookup definition holds mappings between the user resource object fields and single-valued user attributes on the target system. It is used during reconciliation. |
This lookup definition is preconfigured. Table 1-4 lists the default entries in it. You can add entries in this lookup definition if you want to map new target system attributes for reconciliation. See Adding New User or Token Attributes for Reconciliation for more information. |
|
|
This lookup definition holds mappings between the token resource object fields and token attributes on the target system. It is used during provisioning. |
This lookup definition is preconfigured. Table 1-8 lists the default entries in it. You can add entries in this lookup definition if you want to map new target system attributes for reconciliation. See Adding New User or Token Attributes for Reconciliation for more information. |
|
|
This lookup definition is used to configure transformation of token attribute values that are fetched from the target system during token reconciliation. |
You manually create entries in this lookup definition. See Configuring Transformation of Data During Reconciliation for more information. |
|
|
This lookup definition is used to configure transformation of user attribute values that are fetched from the target system during user reconciliation. |
You manually create entries in this lookup definition. See Configuring Transformation of Data During Reconciliation for more information. |
|
|
This lookup definition is used to configure validation of token attribute values that are sent to the target system during provisioning. |
You manually create entries in this lookup definition. See Configuring Validation of Data During Reconciliation and Provisioning for more information. |
|
|
This lookup definition is used to configure validation of token attribute values fetched from the target system during reconciliation. |
You manually create entries in this lookup definition. See Configuring Validation of Data During Reconciliation and Provisioning for more information. |
|
|
This lookup definition is used to configure validation of user attribute values that are sent to the target system during provisioning. |
You manually create entries in this lookup definition. See Configuring Validation of Data During Reconciliation and Provisioning for more information. |
|
|
This lookup definition is used to configure validation of user attribute values that are fetched from the target system during reconciliation. |
You manually create entries in this lookup definition. See Configuring Validation of Data During Reconciliation and Provisioning for more information. |
Connector Objects Used During Reconciliation
See Also:
One of the following guides for conceptual information about reconciliation:
-
For Oracle Identity Manager release 9.1.0.x: Oracle Identity Manager Connector Concepts
-
For Oracle Identity Manager release 11.1.1 and 11.1.2.x: Oracle Fusion Middleware User's Guide for Oracle Identity Manager
The following sections describe connector objects used during reconciliation:
User Attributes for Reconciliation
The Lookup.RSA.AuthManager.UserReconAttrMap lookup definition holds single-valued attribute mappings for user reconciliation. The Code Key column holds the names of resource object fields. The format of values in the Decode column is as follows:
METHOD_NAME;PRINCIPAL_TYPE;ATTRIBUTE_TYPE;RETURN_TYPE_OF_METHOD;RESOURCE_OBJECT_FIELD_TYPE;DTO_ATTRIBUTE_NAME
In this format:
-
METHOD_NAMEis the name of the method on the target system that fetches values from the attribute. This method belongs to one of the following APIs:The
getorisprefix of the method name is not included in the Decode value. -
RETURN_VALUE_OF_METHODis the data type of the values returned by the method. -
PRINCIPAL_TYPEcan be eitherIMSorAMdepending on whether the attribute is an Identity Management Services attribute or an Authentication Manager attribute.See Also:
Target system documentation for information about differences between Identity Management Services and Authentication Manager attributes
-
RETURN_TYPE_OF_METHODis the data type of the values fetched by the method. The return type is specified in the Javadocs for the API. -
RESOURCE_OBJECT_FIELD_TYPEcan beText,Boolean,Lookup,orDate. -
DTO_ATTRIBUTE_NAMEis the name of the attribute in the PrincipalDTO or AMPrincipalDTO API.
Table 1-4 lists the entries in this lookup definition.
Table 1-4 Entries in the Lookup.RSA.AuthManager.UserReconAttrMap Lookup Definition
| Code Key | Decode |
|---|---|
|
User ID |
userID;IMS;Core;String;Text;LOGINUID |
|
Certificate DN |
certificateDN;IMS;Core;String;Text;CERTDN |
|
Account Start Date |
accountStartDate;IMS;Core;Date;Date |
|
Account Expire Date |
accountExpireDate;IMS;Core;Date;Date |
|
Clear Incorrect Passcodes |
clearBadPasscodes;AM;Core;boolean;CheckBox |
|
Clear Windows Password |
ClearWindowsLoginPassword;AM;Core;boolean;CheckBox |
|
Identity Source |
identitySourceGuid;IMS;Core;String;Lookup |
|
Security Domain |
securityDomainGuid;IMS;Core;String;Lookup |
|
Default Shell |
defaultShell;AM;Core;String;Text |
|
User GUID |
Guid;IMS;Core;String;String |
|
Fixed Passcode Allowed |
staticPasswordSet;AM;Core;boolean;CheckBox |
|
First Name |
firstName;IMS;Core;String;Text;FIRST_NAME |
|
Last Name |
lastName;IMS;Core;String;Text;LAST_NAME |
|
Middle Name |
middleName;IMS;Core;String;Text;MIDDLE_NAME |
The Lookup.RSA.AuthManager.UserReconChildAttrMap lookup definition holds multivalued attribute mappings for user reconciliation. Table 1-5 lists the entries in this lookup definition.
The following is the format of entries in this lookup definition:
-
Code Key: Name of the field on the resource object
-
Decode: The value is in the following format:
CHILD_TABLE_NAME_IN_RESOURCE_OBJECT;METHOD_NAME;RETURN_VALUE_OF_METHOD;FIELD_TYPE_ON_PROCESS_FORMIn this format:
-
CHILD_TABLE_NAME_IN_RESOURCE_OBJECTis the name of the child table in the resource object. -
METHOD_NAMEis the name of the method of the com.rsa.admin.data.GroupDTO or com.rsa.admin.data.AdminRoleDTO API on the target system that fetches values from the attribute. Thegetprefix is not included in the name of the method. -
RETURN_VALUE_OF_METHODis the data type of the values returned by the method. -
FIELD_TYPE_ON_PROCESS_FORMcan beBoolean, Lookup, Text,orRadioButton,depending on the type of child form field.
-
Token Attributes for Reconciliation
The Lookup.RSA.AuthManager.TokenReconAttrMap lookup definition holds single-valued attribute mappings for token reconciliation. The Code Key column holds the names of resource object fields. The format of values in the Decode column is as follows:
METHOD_NAME;API_NAME;ATTRIBUTE_TYPE;METHOD_RETURN_TYPE;PROCESS_FORM_FIELD_TYPE
In this format:
-
METHOD_NAMEis the name of the method on the target system that fetches values from the attribute. This method belongs to one of the following APIs:The
getorisprefix of the method name is not included in the Decode value. -
ATTRIBUTE_TYPEcan be one of the following:-
Replace
ATTRIBUTE_TYPEwithCoreif the attribute is a standard RSA Authentication Manager attribute. -
Replace
ATTRIBUTE_TYPEwithExtendedif the attribute is a custom attribute.
-
-
METHOD_RETURN_TYPEis the data type of the value fetched by the method. The return type is specified in the Javadocs for the API. -
PROCESS_FORM_FIELD_TYPEcan be eitherTextorCheckbox.
Table 1-6 lists the entries in this lookup definition.
Reconciliation Rule for User Reconciliation
See Also:
For generic information about reconciliation matching and action rules, see one of the following guides:
-
For Oracle Identity Manager release 9.1.0.x: Oracle Identity Manager Connector Concepts
-
For Oracle Identity Manager release 11.1.1 and 11.1.2.x: Oracle Fusion Middleware User's Guide for Oracle Identity Manager
The following is the process matching rule for user reconciliation:
Rule name: RSA AuthManager UserRecon
Rule element: (User Login Equals User ID) OR (User GUID Equals User GUID)
The first rule component is used to reconcile accounts that are newly created on the target system. In this rule component:
-
User Login is the User ID field on the OIM User form.
-
User ID is the User ID field of RSA Authentication Manager.
The second rule component is used to reconcile updates to accounts that are already reconciled from the target system. In this rule component:
-
User GUID to the left of "Equals" is the User GUID of the RSA user resource assigned to the OIM User.
-
User GUID to the right of "Equals" is the User GUID of the account on the target system.
After you deploy the connector, you can view the user reconciliation rule by performing the following steps:
-
Log in to the Oracle Identity Manager Design Console.
-
Expand Development Tools.
-
Double-click Reconciliation Rules.
-
Search for RSA AuthManager UserRecon. Figure 1-2 shows the reconciliation rule for user reconciliation.
Figure 1-2 Reconciliation Rule for User Reconciliation
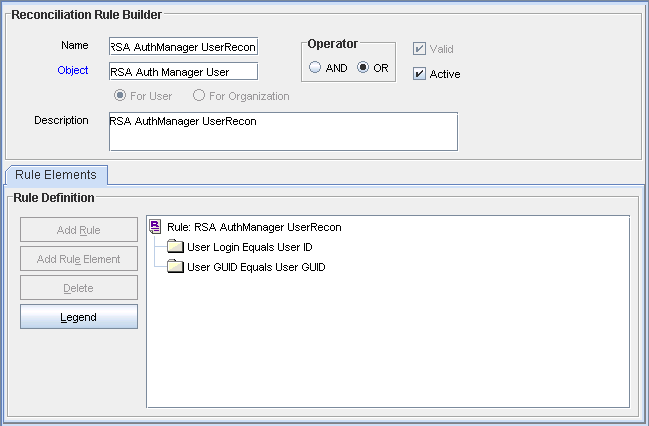
Description of "Figure 1-2 Reconciliation Rule for User Reconciliation"
Reconciliation Rule for Token Reconciliation
See Also:
For generic information about reconciliation matching and action rules, see one of the following guides:
-
For Oracle Identity Manager release 9.1.0.x: Oracle Identity Manager Connector Concepts
-
For Oracle Identity Manager release 11.1.1 and 11.1.2.x: Oracle Fusion Middleware User's Guide for Oracle Identity Manager
The following is the process matching rule for token reconciliation:
Rule name: RSA AuthManager TokenRecon
Rule element: (User Login Equals User ID) OR (User GUID Equals User GUID)
In the first rule component:
-
User Login is the User ID field on the OIM User form.
-
User ID is the User ID field of RSA Authentication Manager.
In the second rule component:
-
User GUID to the left of "Equals" is the User GUID of the RSA token resource assigned to the OIM User.
-
User GUID to the right of "Equals" is the User GUID of the resource on the target system.
This rule supports the following scenarios:
-
You can provision multiple RSA Authentication Manager token resources to the same OIM User, either on Oracle Identity Manager or directly on the target system.
-
You can change the user ID of a user on the target system.
This is illustrated by the following use cases:
-
Use case 1: You provision an RSA account for an OIM User, and you also assign a token for the user directly on the target system.
During the next reconciliation run, application of the first rule condition helps match the resource with the record.
-
Use case 2: An OIM User has an RSA token. You then change the user ID of the user on the target system.
When the first rule condition is applied, no match is found. Then, the second rule condition is applied and it is determined that a second account has been given to the user on the target system. Details of this second account are linked with the OIM User by the reconciliation engine.
After you deploy the connector, you can view the reconciliation rule for target resource reconciliation by performing the following steps:
-
Log in to the Oracle Identity Manager Design Console.
-
Expand Development Tools.
-
Double-click Reconciliation Rules.
-
Search for RSA AuthManager TokenRecon. Figure 1-3 shows the reconciliation rule for token reconciliation.
Figure 1-3 Reconciliation Rule for Token Reconciliation
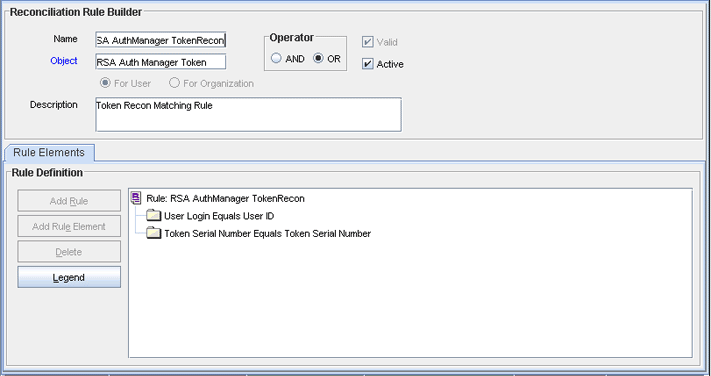
Description of "Figure 1-3 Reconciliation Rule for Token Reconciliation"
Reconciliation Action Rules for Target Resource Reconciliation
Table 1-7 lists the action rules for target resource reconciliation.
Table 1-7 Action Rules for Target Resource Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Assign to Administrator With Least Load |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions. For information about modifying or creating reconciliation action rules, see one of the following guides:
-
For Oracle Identity Manager release 9.1.0.x: Oracle Identity Manager Design Console Guide
-
For Oracle Identity Manager release 11.1.1 and 11.1.2.x: Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager
After you deploy the connector, you can view the reconciliation action rules for target resource reconciliation by performing the following steps:
-
Log in to the Oracle Identity Manager Design Console.
-
Expand Resource Management.
-
Double-click Resource Objects.
-
Search for and open the RSA Auth Manager User resource object.
-
Click the Object Reconciliation tab, and then click the Reconciliation Action Rules tab. The Reconciliation Action Rules tab displays the action rules defined for this connector. Figure 1-4 shows the reconciliation action rule for target resource reconciliation.
Figure 1-4 Reconciliation Action Rules for Target Resource Reconciliation
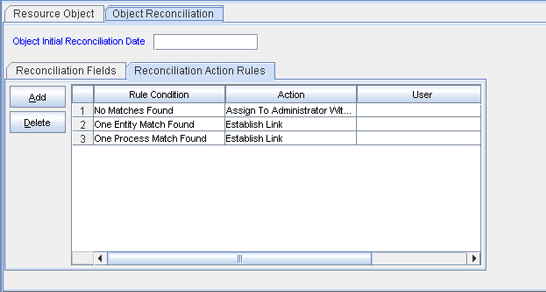
Description of "Figure 1-4 Reconciliation Action Rules for Target Resource Reconciliation"
Connector Objects Used During Provisioning
See Also:
For conceptual information about provisioning, see one of the following guides:
-
For Oracle Identity Manager release 9.1.0.x: Oracle Identity Manager Connector Concepts
-
For Oracle Identity Manager release 11.1.1 and 11.1.2.x: Oracle Fusion Middleware User's Guide for Oracle Identity Manager
The following sections describe connector objects used during provisioning:
Provisioning Functions
Table 1-8 lists the provisioning functions that are supported by the connector. The Adapter column gives the name of the adapter that is used when the function is performed.
Table 1-8 Supported User Provisioning Functions
| Function | Adapter |
|---|---|
|
Create user |
RSAMCREATEUSER |
|
Update user |
RSAMUPDATEUSER |
|
Enable or disable user |
RSAMENABLEUSER and RSAMDISABLEUSER |
|
Assign or remove user from a group |
RSAMADDGROUP and RSAMREMOVEGROUP |
|
Add or remove role from user |
RSAMADDROLE and RSAMREMOVEROLE |
|
Delete user |
RSAMDELETEUSER |
|
Assign token to user |
RSAMASSIGNTOKEN |
|
Update token |
RSAMUPDATETOKEN |
|
Enable or disable token |
RSAMENABLETOKEN and RSAMDISABLETOKEN |
|
Revoke token from user |
RSAMREVOKETOKEN |
|
Update PIN |
RSAMUPDATETOKEN |
|
Update Token Lost |
RSAMUPDATETOKEN |
User Attributes for Provisioning
The Lookup.RSA.AuthManager.UserAttrMap lookup definition maps process form fields with single-valued target system attributes. The Code Key column holds the names of process form fields. The format of values in the Decode column is as follows:
METHOD_NAME;PRINCIPAL_TYPE;ATTRIBUTE_TYPE;METHOD_INPUT_TYPE;DTO_ATTRIBUTE_NAME
In this format:
-
METHOD_NAMEis the name of the method on the target system that fetches values from the attribute. This method belongs to one of the following APIs:The
setprefix of the method name is not included in the Decode value. -
PRINCIPAL_TYPEcan be eitherIMSorAMdepending on whether the attribute is an Identity Management Services attribute or an Authentication Manager attribute.See Also:
Target system documentation for information about differences between Identity Management Services and Authentication Manager attributes
-
ATTRIBUTE_TYPEcan be one of the following:-
Replace
ATTRIBUTE_TYPEwithCoreif the attribute is a standard RSA Authentication Manager attribute. -
Replace
ATTRIBUTE_TYPEwithExtendedif the attribute is a custom attribute.
-
-
METHOD_INPUT_TYPEis the data type of the value sent to the method.The return type is specified in the Javadocs for the API. -
DTO_ATTRIBUTE_NAMEis the name of the attribute in the PrincipalDTO or AMPrincipalDTO API.
Table 1-9 lists the entries in this lookup definition.
Table 1-9 Entries in the Lookup.RSA.AuthManager.UserAttrMap Lookup Definition
| Code Key | Decode |
|---|---|
|
Default Shell |
defaultShell;AM;Core;String |
|
Fixed Passcode Allowed |
staticPasswordSet;AM;Core;boolean |
|
First Name |
firstName;IMS;Core;String;FIRST_NAME |
|
Last Name |
lastName;IMS;Core;String;LAST_NAME |
|
Middle Name |
middleName;IMS;Core;String;MIDDLE_NAME |
|
User ID |
userID;IMS;Core;String;LOGINUID |
|
Certificate DN |
certificateDN;IMS;Core;String;CERT_DN |
|
Password |
Password;IMS;Core;String;PASSWORD |
|
Account Start Date |
accountStartDate;IMS;Core;Date;START_DATE |
|
Account Expire Date |
accountExpireDate;IMS;Core;Date;EXPIRATION_DATE |
|
Fixed Passcode |
staticPassword;AM;Core;String |
|
Clear Incorrect Passcodes |
clearBadPasscodes;AM;Core;boolean |
|
Clear Windows Password |
ClearWindowsLoginPassword;AM;Core;boolean |
|
Identity Source |
identitySourceGuid;IMS;Core;String;IDENTITY_SOURCE |
|
Security Domain |
securityDomainGuid;IMS;Core;String;OWNER_ID |
The Lookup.RSA.AuthManager.UserChildAttrMap lookup definition holds multivalued attribute mappings for user reconciliation. Table 1-5 lists the entries in this lookup definition.
The following is the format of entries in this lookup definition:
Code Key: CHILD_FORM_NAME
Decode: API_NAME;METHOD_NAME
Token Attributes for Provisioning
The Lookup.RSA.AuthManager.TokenAttrMap lookup definition maps process form fields with single-valued target system attributes. The Code Key column holds the names of process form fields. The format of values in the Decode column is as follows:
METHOD_NAME;API_NAME;ATTRIBUTE_TYPE;METHOD_INPUT_TYPE
In this format:
-
METHOD_NAMEis the name of the method on the target system that fetches values from the attribute. This method belongs to one of the following APIs:The
setprefix of the method name is not included in the Decode value. -
ATTRIBUTE_TYPEcan be one of the following: -
METHOD_INPUT_TYPEis the data type of the value sent to the method. This data type is specified in the Javadocs for the API.
Table 1-11 lists the entries in this lookup definition.
Roadmap for Deploying and Using the Connector
The following is the organization of information in the rest of this guide:
-
Chapter 2, "Deploying the Connector" describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Chapter 3, "Using the Connector" describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
-
Chapter 4, "Extending the Functionality of the Connector" describes procedures that you can perform if you want to extend the functionality of the connector.
-
Chapter 5, "Known Issues and Limitations" lists known issues and limitations associated with this release of the connector.