3 Using the Connector
Note:
This chapter provides both conceptual and procedural information about configuring the connector. It is recommended that you read the conceptual information before you perform the procedures.
This chapter is divided into the following sections:
-
Performing Provisioning Operations in Oracle Identity Manager Release 9.1.0.x and 11.1.1.x
-
Performing Provisioning Operations in Oracle Identity Manager Release 11.1.2 or Later
Performing First-Time Reconciliation
First-time reconciliation involves synchronizing lookup definitions in Oracle Identity Manager with the lookup fields of the target system, and performing full reconciliation. In full reconciliation, all existing user records from the target system are brought into Oracle Identity Manager.
The following is the sequence of steps involved in reconciling all existing user records:
Note:
In Oracle Identity Manager release 11.1.1 and 11.1.2.x, a scheduled job is an instance of a scheduled task. In this guide, the term scheduled task used in the context of Oracle Identity Manager release 9.1.0.x is the same as the term scheduled job in the context of Oracle Identity Manager release 11.1.1 or 11.1.2.x.
See Oracle Fusion Middleware System Administrator's Guide for Oracle Identity Manager for more information about scheduled tasks and scheduled jobs.
-
Perform lookup field synchronization by running the scheduled tasks provided for this operation.
See Scheduled Task for Lookup Field Synchronization for information about the attributes of the scheduled tasks for lookup field synchronization.
See Reconciliation Scheduled Tasks for information about running scheduled tasks.
-
Perform user and token reconciliation by running the scheduled tasks for user and token reconciliation.
See Reconciliation Scheduled Tasks for information about the attributes of this scheduled task.
See Reconciliation Scheduled Tasks for information about running scheduled tasks.
After first-time reconciliation, the Last Execution Timestamp attribute of the scheduled task is automatically set to the time stamp at which the reconciliation run began.
See Also:
Configuring Connection Parameters for information about the parameters of the IT resource
From the next reconciliation run onward, only target system user records that are added or modified after the time stamp stored in the scheduled task are considered for incremental reconciliation. These records are brought to Oracle Identity Manager when you configure and run the user reconciliation scheduled task.
Scheduled Task for Lookup Field Synchronization
The RSA Auth Manager Lookup Recon scheduled task is used for lookup field synchronization. Table 3-1 describes the attributes of this scheduled task. The procedure to configure scheduled tasks is described later in the guide.
See Also:
Table 1-2 for the list of lookup definitions synchronized by this scheduled task
Table 3-1 Attributes of the RSA Auth Manager Lookup Recon Scheduled Task
| Attribute | Description |
|---|---|
|
IT Resource |
Enter the name of the IT resource for the target system installation from which you want to reconcile user records. Default value: |
|
Scheduled Task Name |
This attribute holds the name of the scheduled task. If you create a copy of the scheduled task, then enter the name of the new scheduled task as the value of the Scheduled Task Name attribute. Value: |
Guidelines on Performing Reconciliation
Apply the following guideline before you perform a reconciliation run:
If there are a large number of users or tokens to be reconciled during full reconciliation, then you might encounter the InvalidSessionException exception. To work around this issue, increase the Session Lifetime setting on RSA Authentication Manager as follows:
Note:
In Chapter 5, "Known Issues and Limitations," this issue has been documented as Bug 9268577.
-
Log in to the RSA Security Console.
-
From the Access list, select Session Lifetimes and then select Manage Existing.
-
In the Session Lifetime list, open the Console/Command API Session Lifetime list and select Edit from the list.
-
Increase the maximum lifetime value according to your requirement.
-
Save the setting.
Configuring Reconciliation
This section discusses the following topics related to configuring reconciliation:
Full Reconciliation
Full reconciliation involves reconciling all existing user and token records from the target system into Oracle Identity Manager. After you deploy the connector, you must first perform full reconciliation.
To perform a full reconciliation run, ensure that there are no values for the Last Execution Timestamp, CustomReconQuery, and Group attributes and then run the scheduled task. Reconciliation Scheduled Tasks provides information about the procedure to set values for the scheduled task attributes.
The Last Execution Timestamp attribute of the scheduled task stores the time stamp at which a reconciliation run begins. During a reconciliation run, the scheduled task fetches only target system records that are added or modified after the time stamp stored in the Last Execution Timestamp attribute. In other words, after a full reconciliation run, the connector automatically switches to incremental reconciliation for subsequent reconciliation runs. However, you can perform full reconciliation whenever you want to ensure that all target system records are reconciled in Oracle Identity Manager.
Limited Reconciliation
By default, all user and token records that are added or modified after the last reconciliation run are reconciled during the current reconciliation run. You can customize this process by specifying the subset of newly added or modified records that must be reconciled. You do this by setting a filter for reconciliation.
For this connector, you set a filter (query condition) as the value of the CustomReconQuery scheduled task attribute while performing the procedure described in Reconciliation Scheduled Tasks.
Note:
In addition to the CustomReconQuery attribute, you can use the Group attribute of the scheduled task to specify the user group from which user or token records must be reconciled.
You can use the following attributes to build the filter:
-
Certificate DN
-
First Name
-
Last Name
-
Middle Name
-
User ID
You can use the following comparators to build each clause in the query condition:
-
=
-
<>
-
contains
-
endsWith
-
startsWith
A query condition can contain up to 3 clauses, and the clauses can be linked with the AND (&) and OR (|) operators.
The following are sample values for the CustomReconQuery attribute:
-
User ID contains doWith this query condition, all records of users whose user IDs contain the string
doare reconciled. -
First Name = John & Last Name endsWith oe | Last Name StartsWith DoWith this query condition, the following records are reconciled:
-
Users whose first name is
Johnand last name ends in the stringoe. -
Users whose last name starts with the string
Do.
-
-
Certificate DN <> CN,OU,OWith this query condition, all records of users whose certificate DN is not equal to
CN,OU,Oare reconciled.
Batched Reconciliation
During a reconciliation run, all changes in the target system records are reconciled into Oracle Identity Manager. Depending on the number of records to be reconciled, this process may require a large amount of time. In addition, if the connection breaks during reconciliation, then the process would take longer to complete.
You can configure batched reconciliation to avoid such problems.
To configure batched reconciliation, you use the FullRecon Batch Size user reconciliation scheduled task attribute. This attribute is used to specify the number of records that must be included in each batch fetched from the target system.
Suppose you specify 20 as the value of the FullRecon Batch Size attribute. Suppose that 314 user records were created or modified after the last reconciliation run. These 314 records would be reconciled in batches of 20 records each.
You specify values for the FullRecon Batch Size attribute by following the instructions described in Reconciliation Scheduled Tasks.
Reconciliation Scheduled Tasks
When you run the Connector Installer, the scheduled tasks for user and token reconciliation are automatically created in Oracle Identity Manager.
The following sections provide information about the attributes of these reconciliation scheduled tasks:
RSA Auth Manager User Recon
Table 3-2 describes the attributes of the scheduled task for user and token reconciliation.
See Also:
Oracle Identity Manager Design Console Guide for information about adding and removing scheduled task attributes
Table 3-2 Attributes of the RSA Auth Manager User Recon Scheduled Task
| Attribute | Description |
|---|---|
|
CustomReconQuery |
Enter the query condition that must be applied during the reconciliation run. This is one of the attributes that are used to implement limited reconciliation. Limited Reconciliation describes this feature. |
|
Group |
Enter the name of the group on the target system that you want to use for the reconciliation run. Only users or tokens from the group that you specify are considered for the reconciliation run. This is one of the attributes that are used to implement limited reconciliation. Limited Reconciliation describes this feature. |
|
Identity Source |
Enter the name of the identity source that must be used during the reconciliation run. The identity source can be the internal database, an external database, or an LDAP solution. You must enter the name of the identity source displayed on the Identity Source page of the RSA Security Console. Default value: |
|
IsDeleteAllowed |
Enter |
|
IsTokenReconAllowed |
Enter When you set the value of this attribute to |
|
IT Resource |
Enter the name of the IT resource from which you want to reconcile user data. Default value: |
|
Last Execution Timestamp |
This attribute holds the time stamp at which the last user reconciliation run started. A value is automatically entered in this attribute after each reconciliation run. You can set the value of this attribute to |
|
Scheduled Task Name |
This attribute holds the name of the scheduled task. Default value: Note: You must not change the value of this attribute. However, if you create a copy of the scheduled task, then enter the name of the new scheduled task as the value of the Scheduled Task Name attribute. |
|
Token Resource Object |
Enter the name of the token resource object that must be used during the reconciliation run. This attribute is used only if you set the IsTokenReconAllowed attribute to Default value: |
|
User Resource Object |
Enter the name of the user resource object that must be used during the reconciliation run. Default value: |
|
FullRecon Batch Size |
Enter the number of records that must be included in each batch fetched from the target system. If you do not want to implement batched reconciliation, then specify nodata. Default value: |
RSA Auth Manager Token Recon
Table 3-3 describes the attributes of the scheduled task for token reconciliation.
Note:
Reconciliation of token deletion on the target system is automatically processed by this scheduled task.
Table 3-3 Attributes of the RSA Auth Manager Token Recon Scheduled Task
| Attribute | Description |
|---|---|
|
CustomReconQuery |
Enter the query condition that must be applied during the reconciliation run. This is one of the attributes that are used to implement limited reconciliation. Limited Reconciliation describes this feature. See Full Reconciliation for information about using this attribute to perform a full reconciliation run. |
|
Group |
Enter the name of the group on the target system that you want to use for the reconciliation run. Only users or tokens from the group that you specify are considered for the reconciliation run. See Full Reconciliation for information about using this attribute to perform a full reconciliation run. |
|
Identity Source |
Enter the name of the identity source that must be used during the reconciliation run. The identity source can be the internal database, an external database, or an LDAP solution. Default value: |
|
IT Resource |
Enter the name of the IT resource from which you want to reconcile user data. Default value: |
|
Last Execution Timestamp |
This attribute holds the time stamp at which the last user reconciliation run started. A value is automatically entered in this attribute after each reconciliation run. See Full Reconciliation for information about using this attribute to perform a full reconciliation run. |
|
Scheduled Task Name |
This attribute holds the name of the scheduled task. Default value: Note: You must not change the value of this attribute. However, if you create a copy of the scheduled task, then enter the name of the new scheduled task as the value of the Scheduled Task Name attribute. |
|
Token Resource Object |
Enter the name of the token resource object that must be used during the reconciliation run. This attribute is used only if you set the IsTokenReconAllowed attribute to Default value: |
Configuring the Scheduled Tasks
This section describes the procedure to configure scheduled tasks. You can apply this procedure to configure the scheduled tasks for lookup field synchronization and reconciliation.
Table 3-4 lists the scheduled tasks that you must configure.
Table 3-4 Scheduled Tasks for Lookup Field Synchronization and Reconciliation
| Scheduled Task | Description |
|---|---|
|
This scheduled task is used for lookup field synchronization. |
|
|
This scheduled task is used for user reconciliation. |
|
|
This scheduled task is used for token reconciliation. |
To configure a scheduled task:
-
Depending on the Oracle Identity Manager release you are using, perform one of the following steps:
-
For Oracle Identity Manager release 9.1.0.x:
-
Log in to the Administrative and User Console.
-
Expand Resource Management, and then click Manage Scheduled Task.
-
-
For Oracle Identity Manager release 11.1.1:
-
Log in to the Administrative and User Console.
-
On the Welcome to Oracle Identity Manager Self Service page, click Advanced in the upper-right corner of the page.
-
On the Welcome to Oracle Identity Manager Advanced Administration page, in the System Management region, click Search Scheduled Jobs.
-
-
For Oracle Identity Manager release 11.1.2.x:
-
Log in to Oracle Identity System Administration.
-
In the left pane, under System Management, click Scheduler.
-
-
-
Search for and open the scheduled task as follows:
-
If you are using Oracle Identity Manager release 9.1.0.x, then:
-
On the Scheduled Task Management page, enter the name of the scheduled task as the search criteria and then click Search.
-
In the search results table, click the edit icon in the Edit column for the scheduled task.
-
On the Scheduled Task Details page where the details of the scheduled task that you selected is displayed, click Edit.
-
-
If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x, then:
-
On the Welcome to Oracle Identity Manager Advanced Administration page, in the System Management region, click Search Scheduled Jobs.
-
On the left pane, in the Search field, enter the name of the scheduled job as the search criterion. Alternatively, you can click Advanced Search and specify the search criterion.
-
In the search results table on the left pane, click the scheduled job in the Job Name column.
-
-
-
Modify the details of the scheduled task. To do so:
-
If you are using Oracle Identity Manager release 9.1.0.x, then on the Edit Scheduled Task Details page, modify the following parameters, and then click Continue:
-
Status: Specify whether you want to leave the task in the enabled state. In the enabled state, the task is ready for use.
-
Max Retries: Enter an integer value in this field. This number represents the number of times Oracle Identity Manager must attempt to complete the task before assigning the ERROR status to the task. The default value is 1.
-
Next Start: Use the date editor to specify the date when you want the task to run. After you select a date value in the date editor, you can modify the time value that is automatically displayed in the Next Start field.
-
Frequency: Specify the frequency at which you want the task to run.
-
-
If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x, then on the Job Details tab, you can modify the following parameters:
-
Retries: Enter an integer value in this field. This number represents the number of times the scheduler tries to start the job before assigning the Stopped status to the job.
-
Schedule Type: Depending on the frequency at which you want the job to run, select the appropriate schedule type.
Note:
See Oracle Fusion Middleware System Administrator's Guide for Oracle Identity Manager for detailed information about schedule types.
In addition to modifying the job details, you can enable or disable a job.
-
-
-
Specify values for the attributes of the scheduled task. To do so:
Note:
-
Attribute values are predefined in the connector XML file that you import. Specify values only for those attributes that you want to change.
-
Attributes of the scheduled task are discussed in Reconciliation Scheduled Tasks.
-
If you are using Oracle Identity Manager release 9.1.0.x, then on the Attributes page, select the attribute from the Attribute list, specify a value in the field provided, and then click Update.
-
If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x, then on the Job Details tab, in the Parameters region, specify values for the attributes of the scheduled task.
-
-
After specifying the attributes, perform one of the following:
-
If you are using Oracle Identity Manager release 9.1.0.x, then click Save Changes to save the changes.
Note:
The Stop Execution option is not available in the Administrative and User Console. If you want to stop a task, then click Stop Execution on the Task Scheduler form of the Design Console.
-
If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x, then click Apply to save the changes.
Note:
The Stop Execution option is available in the Administrative and User Console. You can use the Scheduler Status page to either start, stop, or reinitialize the scheduler.
-
Guidelines on Performing Provisioning
Apply the following guidelines while performing provisioning:
-
When you try to provision a multivalued attribute, such as a role or group, if the attribute has already been set for the user on the target system, then the status of the process task is set to
Completedin Oracle Identity Manager. If required, you can configure the task so that it shows the statusRejectedinstead ofCompleted. See Oracle Identity Manager Design Console Guide for information about configuring process tasks. -
The value that you enter in the Pin field must be 4 through 8 characters long and contain only numeric values.
Assigning Software Tokens to Users
To assign a software token to a user:
-
Import the software token file into RSA Authentication Manager. See the "Import Tokens" section in RSA Security Console Help for information about the procedure.
-
Assign the software token to the user. See Performing Provisioning Operations in Oracle Identity Manager Release 9.1.0.x and 11.1.1.x for information about the procedure.
-
Send the software token to the user either by token file or CT-KIP. See the "Distribute Software Tokens" section in RSA Security Console Help for information about the procedure.
Performing Provisioning Operations in Oracle Identity Manager Release 9.1.0.x and 11.1.1.x
Provisioning a resource for an OIM User involves using Oracle Identity Manager to create an RSA Authentication Manager account or token for the user.
When you install the connector on Oracle Identity Manager release 11.1.1, the direct provisioning feature is automatically enabled. This means that the process form is enabled when you install the connector.
If you have configured the connector for request-based provisioning, then the process form is suppressed and the object form is displayed. In other words, direct provisioning is disabled when you configure the connector for request-based provisioning. If you want to revert to direct provisioning, then perform the steps described in Switching Between Request-Based Provisioning and Direct Provisioning on Oracle Identity Manager Release 11.1.1.
The following are types of provisioning operations:
See Also:
Oracle Identity Manager Connector Concepts for information about the types of provisioning
This section discusses the following topics:
Direct Provisioning
To provision a resource by using the direct provisioning approach:
Note:
This procedure describes the Create User provisioning operation. The procedure for the Update User provisioning operation is similar to this one.
-
Log in to the Administrative and User Console.
-
From the Users menu:
-
Select Create if you want to first create the OIM User and then provision an RSA Authentication Manager account to the user.
-
Select Manage if you want to provision an RSA Authentication Manager account or token to an existing OIM User.
Note:
You must provision an account before you can provision a token to a user.
-
-
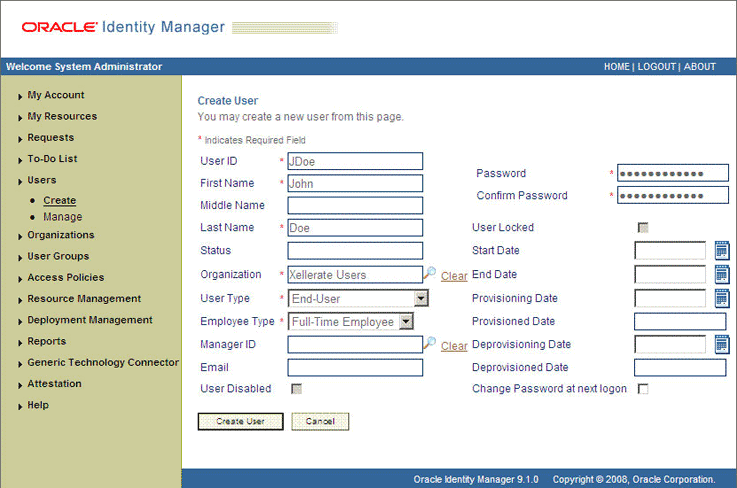
If you select Create, then on the Create User page, enter values for the OIM User fields and then click Create User. Figure 3-1 shows the Create User page.
-
If you select Manage, then search for the OIM User and select the link for the user from the list of users displayed in the search results.
-
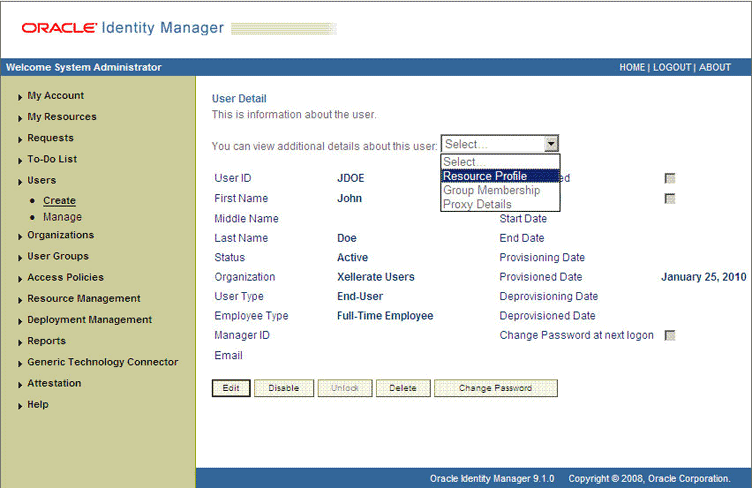
On the User Detail page, select Resource Profile from the list at the top of the page. Figure 3-2 shows the User Detail page.
-
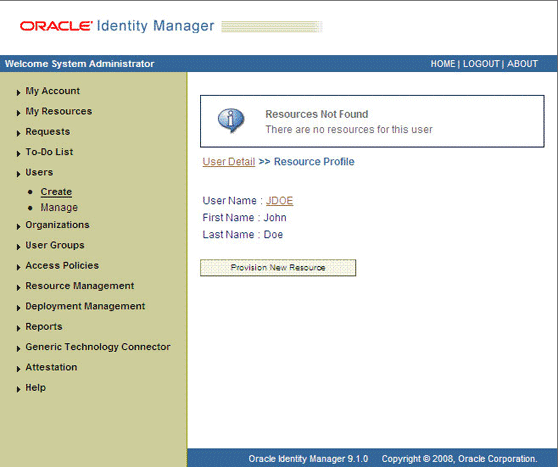
On the Resource Profile page, click Provision New Resource. Figure 3-3 shows the Resource Profile page.
-
On the Step 1: Select a Resource page, select RSA Auth Manager User from the list and then click Continue. Figure 3-4 shows the Step 1: Select a Resource page.
Figure 3-4 Step 1: Select a Resource Page
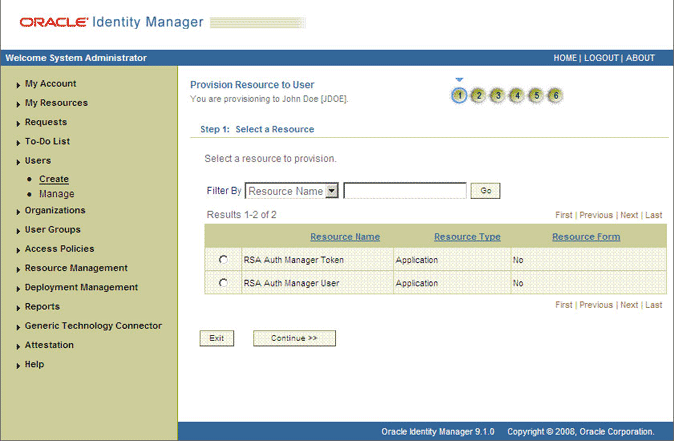
Description of "Figure 3-4 Step 1: Select a Resource Page"
-
On the Step 2: Verify Resource Selection page, click Continue. Figure 3-5 shows the Step 2: Verify Resource Selection page.
Figure 3-5 Step 2: Verify Resource Selection Page
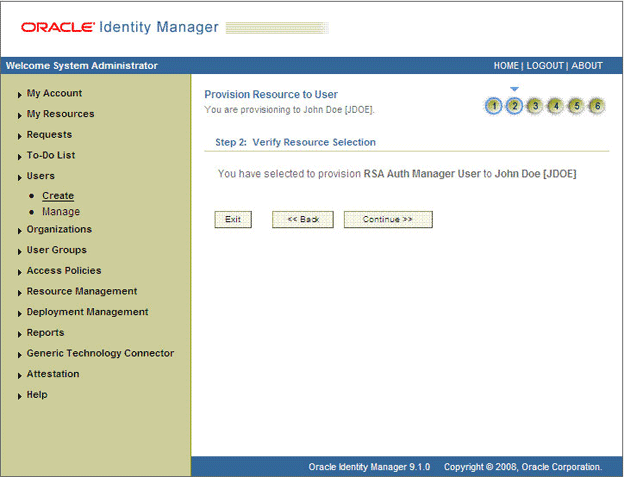
Description of "Figure 3-5 Step 2: Verify Resource Selection Page"
-
On the Step 5: Provide Process Data for RSA Auth Manager User Details page, enter the details of the account that you want to create on the target system and then click Continue.
Table 3-5 describes the fields on the user process form.
Table 3-5 Fields on the User Process Form
Field Description Server Instance
Select the IT resource representing the target system installation on which you want to perform the provisioning operation.
Identity Source
Select the identity source in which you want to perform the provisioning operation.
Security Domain
Select the security domain in which you want to perform the provisioning operation.
First Name
Enter the first name of the user.
Middle Name
Enter the middle name of the user.
Last Name
Enter the last name of the user.
User ID
Enter a user ID for the user.
Password
Enter a password for the user.
Certificate DN
Enter the subject line of the certificate issued to the user for authentication.
Account Start Date
Select the date from which the account must be activated.
This field is used in conjunction with the Account Start Hours and Account Start Minutes fields.
Account Start Hours
Select the time (in hours) at which the account must be activated.
This field is used in conjunction with the Account Start Date and Account Start Minutes field.
Account Start Minutes
Select the time (in minutes) at which the account must be activated.
This field is used in conjunction with the Account Start Date and Account Start Hours field.
Account Expire Date
Select the date at which the account must be closed.
This field is used in conjunction with the Account Expire Hours and Account Expire Minutes fields.
Account Expire Hours
Select the time (in hours) at which the account must be closed.
This field is used in conjunction with the Account Expire Date and Account Expire Minutes field.
Account Expire Minutes
Select the time (in minutes) at which the account must be closed.
This field is used in conjunction with the Account Expire Date and Account Expire Hours field.
Fixed Passcode Allowed
Select this check box if you want to allow the user to use a fixed passcode.
For authentication purposes, a passcode is an alternative to a password. A user enters a passcode along with the PIN displayed on the token. With a fixed passcode, a user need not use the PIN.
Fixed Passcode
Enter the passcode. The value entered in this field is accepted only if you select the Fixed Passcode Allowed check box.
Clear Incorrect Passcode
Select this check box if you want to clear the count of previous incorrect authentication attempts stored in RSA Authentication Manager. This check box is used only for Update User operations.
A policy defined in RSA Authentication Manager specifies the number of incorrect authentication attempts after which the user is locked out of the system. As the administrator, you can select the Clear Incorrect Passcode check box to clear the count and unlock the user.
Clear Windows Passcode
As part of an offline authentication policy, if Microsoft Windows password integration is enabled, then Microsoft Windows passwords of users are stored in RSA Authentication Manager. For authentication, users only need their Windows user name and RSA SecurID passcode.
If you select the Clear Windows Passcode check box, then the saved copy of the user's Windows password is deleted and the user has to reenter the Windows password at next logon.
Default Shell
If RSA Authentication Manager is running on a UNIX platform, then use the Default Shell field to specify a default shell or home directory for the user. The specified directory must exist on the target system for the operation to succeed.
Sample value:
/bin/jdoeFigure 3-6 shows the user details added.
Figure 3-6 Step 5: Provide Process Data for RSA Auth Manager User Page
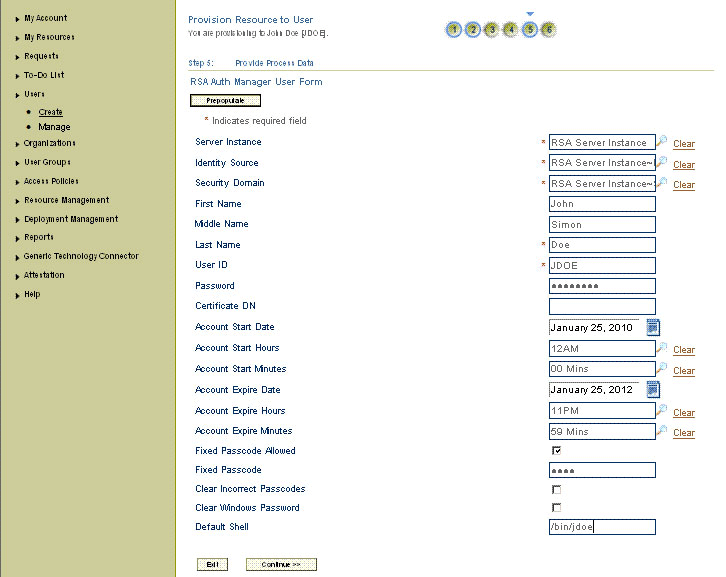
Description of "Figure 3-6 Step 5: Provide Process Data for RSA Auth Manager User Page"
If you are performing a token provisioning operation, then enter values for the fields listed in Table 3-6.
Table 3-6 Fields on the Token Process Form
Field Description Server Instance
Select the IT resource representing the target system installation on which you want to perform the provisioning operation.
User ID
Enter a user ID for the user.
User Identity Source
Select the identity source in which you want to perform the provisioning operation.
Token Serial Number
Enter the serial number of the token that you want to assign to the user.
Notes
Enter comments for this operation.
Pin
Enter the Pin for the token.
Token Lost
Select this field if the token device assigned to the user is lost. Otherwise, deselect this field.
Figure 3-7 shows the same page for tokens.
Figure 3-7 Step 5: Provide Process Data for RSA Auth Manager Token Form Page
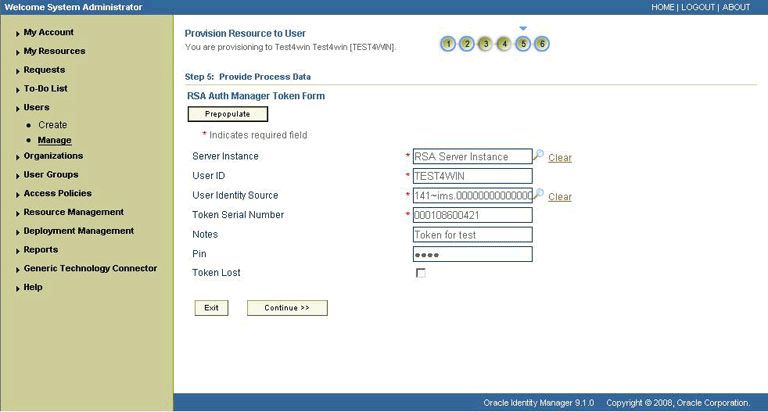
Description of "Figure 3-7 Step 5: Provide Process Data for RSA Auth Manager Token Form Page"
-
On the Step 5: Provide Process Data page, search for and select a role for the user on the target system and then click Continue. Figure 3-8 shows this page. The page for selecting a group for the user is similar to this page.
Figure 3-8 Step 5: Provide Process Data for RSA Auth Manager Role Page
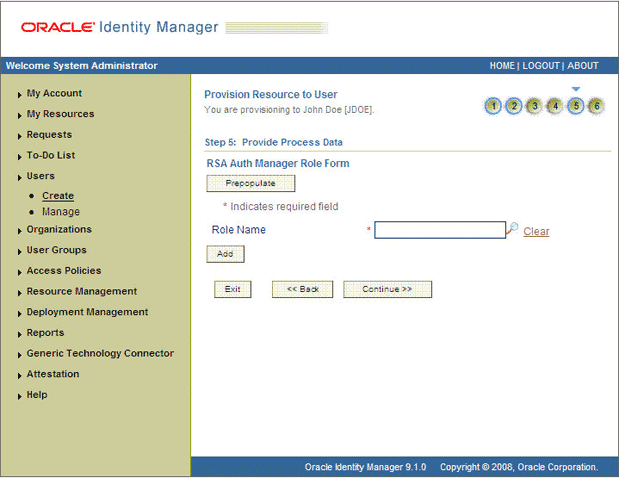
Description of "Figure 3-8 Step 5: Provide Process Data for RSA Auth Manager Role Page"
-
On the Step 6: Verify Process Data page, verify the data that you have provided and then click Continue.
Figure 3-9 shows the Step 6: Verify Process Data page for the user resource.
Figure 3-9 Step 6: Verify Process Data Page
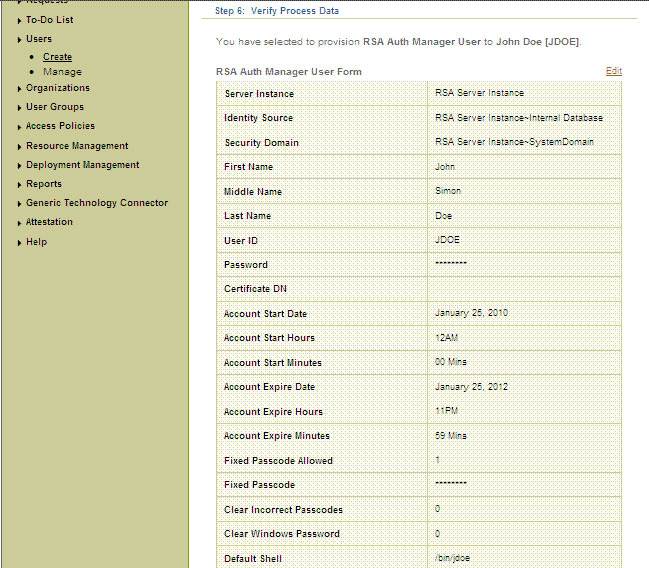
Description of "Figure 3-9 Step 6: Verify Process Data Page"
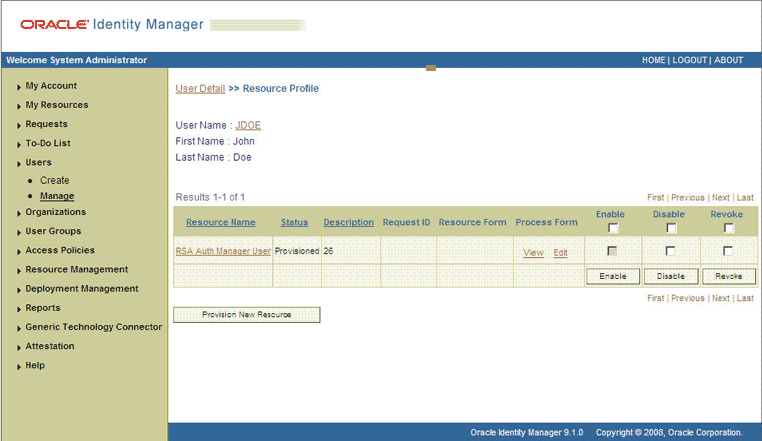
The Resource Profile page is displayed. Figure 3-10 shows this page. The resource that you provisioned is displayed on this page.
Request-Based Provisioning
Note:
The information provided in this section is applicable only if you are using Oracle Identity Manager release 11.1.1.
A request-based provisioning operation involves both end users and approvers. Typically, these approvers are in the management chain of the requesters. The following sections discuss the steps to be performed by end users and approvers during a request-based provisioning operation:
Note:
The procedures described in these sections are built on an example in which the end user raises or creates a request for provisioning a target system account. This request is then approved by the approver.
End User's Role in Request-Based Provisioning
The following steps are performed by the end user in a request-based provisioning operation:
See Also:
Oracle Fusion Middleware User's Guide for Oracle Identity Manager for detailed information about these steps
-
Log in to the Administrative and User Console.
-
On the Welcome page, click Self-Service in the upper-right corner of the page.
-
On the Welcome to Identity Manager Self Service page, in the Request region, click Create Request.
-
On the Request Beneficiary page, select Request for Others, and then click Next.
-
From the Request Template list, select Provision Resource, and then click Next.
-
On the Select Users page, specify a search criterion in the fields to search for the user that you want to provision the resource, and then click Search. A list of users that match the search criterion you specify is displayed in the Available Users list.
-
From the Available Users list, select the user to whom you want to provision the resource.
If you want to create a provisioning request for more than one user, then from the Available Users list, select users to whom you want to provision the account.
-
Click Move or Move All to include your selection in the Selected Users list, and then click Next.
-
On the Select Resources page, click the arrow button next to the Resource Name field to display the list of all available resources.
-
From the Available Resources list, select one of the following, move it to the Selected Resources list, and then click Next:
-
If you want to provision an RSA Authentication Manager account, then select RSA Auth Manager User.
-
If you want to provisioning an RSA Authentication Manager token, then select RSA Auth Manager Token.
Note:
The RSA Auth Manager User has to be provisioned before RSA Auth Manager Token.
-
-
On the Resource Details page, enter details of the resource to be provisioned, and then click Next.
-
On the Justification page, you can specify values for the following fields, and then click Finish.
-
Effective Date
-
Justification
On the resulting page, a message confirming that your request has been sent successfully is displayed along with the Request ID.
-
-
If you click the request ID, then the Request Details page is displayed.
-
To view details of the approval, on the Request Details page, click the Request History tab.
Approver's Role in Request-Based Provisioning
The following are steps performed by the approver in a request-based provisioning operation:
The following are steps that the approver can perform:
-
Log in to the Administrative and User Console.
-
On the Welcome page, click Self-Service in the upper-right corner of the page.
-
On the Welcome to Identity Manager Self Service page, click the Tasks tab.
-
On the Approvals tab, in the first section, you can specify a search criterion for request task that is assigned to you.
-
From the search results table, select the row containing the request you want to approve, and then click Approve Task.
A message confirming that the task was approved is displayed.
Switching Between Request-Based Provisioning and Direct Provisioning on Oracle Identity Manager Release 11.1.1
Note:
It is assumed that you have performed the procedure described in Configuring Request-Based Provisioning.
On Oracle Identity Manager release 11.1.1, if you want to switch from request-based provisioning to direct provisioning, then:
-
Log in to the Design Console.
-
Disable the Auto Save Form feature as follows:
-
Expand Process Management, and then double-click Process Definition.
-
Search for and open the RSA Auth Manger User process definition.
-
Deselect the Auto Save Form check box.
-
Repeat Steps 2.a through 2.d with the following difference:
While performing Step 2.b, search for and open the RSA Auth Manager Token process definition.
-
On Oracle Identity Manager release 11.1.1, if you want to switch from direct provisioning back to request-based provisioning, then:
-
Log in to the Design Console.
-
Enable the Auto Save Form feature as follows:
-
Expand Process Management, and then double-click Process Definition.
-
Search for and open the RSA Auth Manager User process definition.
-
Select the Auto Save Form check box.
-
Repeat Steps 2.a through 2.d with the following difference:
While performing Step 2.b search for and open the RSA Auth Manager Token process definition.
-
-
If you want to enable end users to raise requests for themselves, then:
-
Expand Resource Management, and then double-click Resource Objects.
-
Search for and open the RSA Auth Manager User resource object.
-
Select the Self Request Allowed check box.
-
Repeat Steps 3.a through 3.d with the following difference:
While performing Step 3.b search for and open the RSA Auth Manager Token process definition.
-
Performing Provisioning Operations in Oracle Identity Manager Release 11.1.2 or Later
To perform provisioning operations in Oracle Identity Manager release 11.1.2 or later:
-
Log in to Oracle Identity Administrative and User console.
-
Create a user. See the "Managing Users" chapter in Oracle Fusion Middleware User's Guide for Oracle Identity Manager for more information about creating a user.
-
On the Account tab, click Request Accounts.
-
In the Catalog page, search for and add to cart the application instance created in Creating an Application Instance and then click Checkout.
-
Specify value for fields in the application form and then click Ready to Submit.
-
Click Submit.
-
If you want to provision entitlements, then:
-
On the Entitlements tab, click Request Entitlements.
-
In the Catalog page, search for and add to cart the entitlement, and then click Checkout.
-
Click Submit.
-