









|
This section covers the following topics:
In addition to the Administration Console, AquaLogic Enterprise Security includes another user interface, the Entitlements Management Tool. The Entitlements Management Tool can be used by business users to manage roles, users and groups, and entitlements. This user interface enables you to manage your users' entitlements based on the Roles Based Access Control (RBAC) model. The Entitlements Management Tool enables business users to answer questions like "what entitlements does a user have?" or "which users are allowed to access a given resource?"
The Entitlements Management Tool implements a hierarchical RBAC model. In this model, there is a seniority relationship between roles: senior roles inherit the permissions of their juniors and junior roles inherit members of their parents. In this way, data is inherited in both directions, with membership moving down and permissions moving up the tree. Using a hierarchical model makes it possible to aggregate permissions associated with users.
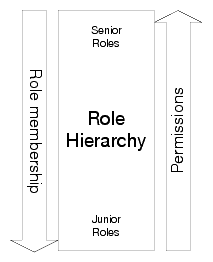
The Entitlements Management Tool displays which permissions and roles are assigned directly and which are inherited.
Four important concepts to understand in the ALES RBAC Model are:
Roles are defined to represent job functions in an organization (for example, teller or executive VP of Finance). A role's collection of permissions (and permission sets) represent the set of entitlements for a role - all of the actions that a role can take within a system. Roles can have attributes that will be available to the authorization system at runtime. Attributes follow the RBAC inheritance model from the child to the parent, so a parent role will have all the attributes of its child roles. Users and groups are assigned to roles via membership rules. A user or group can be assigned directly to a role, or conditionally assigned to a role.
Permissions are named objects that represent an action on a resource. Permission sets are named hierarchical objects that are collections of permissions. Under the inheritance model of the permission set hierarchy, parent permission sets inherit permissions and attributes from their children. Like roles, permissions and permission sets can have attributes that will be available to the authorization system at runtime. Permissions can either be assigned directly to a role, or to a permission set that is in turn assigned to a role. Attributes follow the RBAC inheritance model from the child to the parent, so a parent permission set will have all the attributes of its child permissions or permission sets.
Separation of duties constraints define exclusive relationships between roles. A separation of duties constraint allows you to say, for example: If a user has the role auditor he can not also have the role of trader. At runtime, the system will not allow a user to have both roles at the same time and thereby prevent a user from having incompatible permissions.
The Entitlements Management Tool provides the following functions:
Use the Roles node in the Entitlements Management Tool to:
For more information, see Working with Roles.
Use the Permissions node in the Entitlements Management Tool to:
For more information, see Working with Permissions and Permission Sets
Use the Separation of Duties node in the Entitlements Management Tool to:
For more information, see Separation of Duties Constraints
Use the Reports node in the Entitlements Management Tool to:
For more information, see Generating Reports
Before you can use the Entitlements Management Tool, you need to do the following:
Before you can use the Entitlements Management Tool, you need to load the policies that govern access to and use of the tool. To load these policies:
policyloader), load the policies using the edited load.entitlements.conf file, using a command like the following: ..\..\bin\policyloader.bat <bea_home>\ales26-admin\entitlements\policy\load.entitlements.conf
For more information about the Policyloader utility, see Importing Policy Data.
asi, then select user. rolesadmin, and click the Edit button to set a new password for this user. rbacadmin, permissionsadmin, reportingadmin).The procedure for deploying the Entitlements Management Tool Web application depends on which servlet container you are using:
entitlementsadministration application.<host>\<bea_home>\ales26-admin\entitlements\wls8.entitlementsadministration.war and click Next.entitlementsadministration.war, from <bea_home>\ales26-admin\entitlements\tomcat\ to <bea_home>\ales26-admin\asiDomain\applications\.This section describes how to configure a Security Service Module to use the RBAC model.
grant(any, //app/policy/resourcename, //role/Everyone) if
rbac_eval_action_resource_in_entitlements(entitlements,sys_privilege);
asiadmin security configuration.asiadmin security configuration.
The Entitlements Management Tool is a browser-based web application. You can access it at this URL:
https://<hostname>:7010/entitlementsadministration
Like the ALES Administration Console, the Entitlements Management Tool supports only the Microsoft Internet Explorer browser.
When you use the Entitlements Management Tool to make changes, the tool's Save Changes and Revert Changes buttons become active. The Entitlements Management Tool uses a transactional change model; after you have made all the changes you need to make and click Save Changes, all the changes are committed in a single transaction. If the changes require it, they are distributed through the ALES Business Logic Manager.
The Entitlements Management Tool defines the following roles by default that limit access to the tool:
The following users are defined by default, with the following roles:
The Entitlements Management Tool enables you to create hierarchies of roles. In a hierarchical role system, you can create a tree of roles, with each parent node in the tree possessing all the permissions of its child roles.
To view all the roles defined in your ALES security realm, in the left panel of the Entitlements Management Tool, expand Entitlements Management > All Roles. The Roles summary page displays a role's entitlements, with separate columns indicating which permissions are directly assigned, inherited from child roles, or denied to this role.
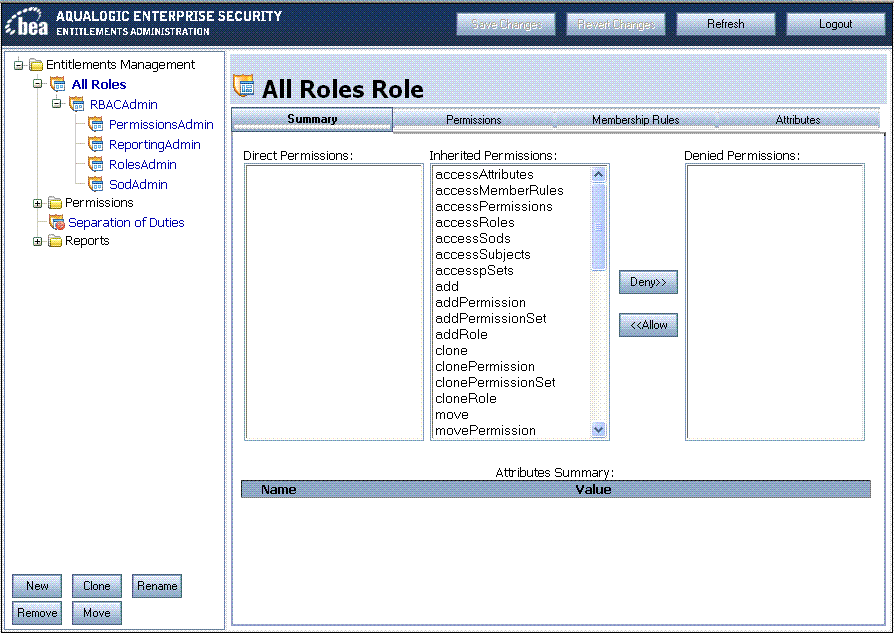
To assign a permission to a role:
To assign a permission set to a role:
The New Member Rule page appears. In the Subject tab, you can select the users or groups to include (using the Grant option) or exclude (using the Deny option) from the new role. Use the Add and Remove buttons to specify the users or groups covered by the grant or deny rule and click OK.
In the Conditions field, enter one or more attribute-based conditions, such as:
if subject.location = "New York"
This member rule will apply only if the subject has the specified attribute name/value pair.
You can assign attributes to roles. An attribute is a name/value pair that will be available to the ALES authorization system at run time. Assigning an attribute enables the creation of authorization policies based on the attribute value.
To assign an attribute to a role:
You can use the Entitlements Management Tool to move, clone, delete, modify, or rename roles.
The role you moved, including all its child roles, is now a child of a different parent in the roles hierarchy.
The role you cloned, including all its child roles, is now a child of a different parent in the roles hierarchy, while the original remains in its original place in the roles hierarchy. You then may want to modify the new cloned role to fit its purpose, including renaming the role.
You can use the Entitlements Management Tool to manage user and group identities in your ALES security realm. The Identity node in the Entitlements Management Tool presents user and group information on three tabs:
By default, the Identity node has a single child identity directory, named asi. You can use the New and Remove buttons to add or delete other identity directories.
For more information about identities in ALES, see Identities.
To view all the users defined in your ALES security realm, in the left panel of the Entitlements Management Tool, expand Entitlements Management > Identity > asi. The Users tab displays user names, the groups each user is a member of, and attributes assigned to each user.
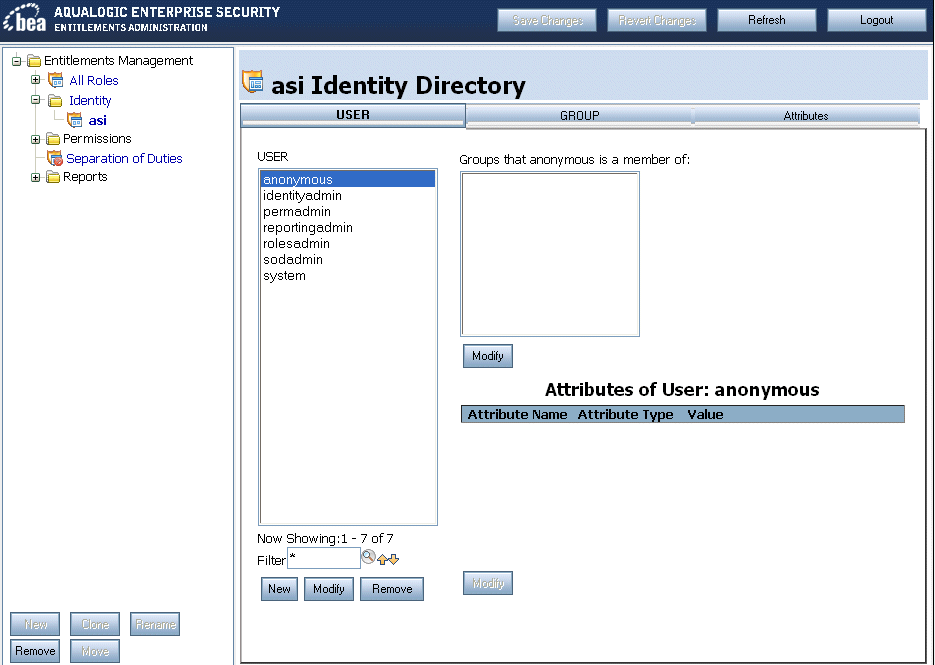
You can use this page to add or remove users and to specify which groups a user is a member of.
To view all the groups defined in your ALES security realm, in the left panel of the Entitlements Management Tool, expand Entitlements Management > Identity > asi and click the Groups tab. You can use the Groups tab to add or remove groups and view a group's members and attributes.
To view all the identity attributes defined in your ALES security realm, in the left panel of the Entitlements Management Tool, expand Entitlements Management > Identity > asi and click the Attributes tab. You can use the Attributes tab to define identity attributes, which you can then assign to users. You can also modify or remove attributes.
To modify the value of an attribute for a user or group:
For more information about identity attributes, see Identity Attributes and Understanding Identity Attributes in the Administration Console help.
Permissions can be assigned to roles directly or be assigned to permission sets that are then assigned to roles. A permission set is a hierarchical collection of permissions that can be assigned to roles. A child permission set can only have one parent, but a permission set or permission can be assigned to many roles. In addition, permissions can be assigned to many permission sets.
Grouping permissions into permission sets can greatly ease the task of administering roles and policies. Since individual permissions are so specific and small-grained, a given role might require a large number of individual permissions. By grouping permissions into a permission set, it can be easier to create and maintain roles and permissions that correspond to business tasks.
To view all the permission sets defined in your ALES security realm, in the left panel of the Entitlements Management Tool, expand Entitlements Management > Permissions > All Permission Sets. The Permission Sets summary page displays a permission set's entitlements, with separate columns indicating which permissions are directly assigned or inherited from child sets. The Permissions tab enables adding or removing permissions in a permission set, while the Attributes tab enables assigning attributes to a permission set, as described in Assigning Permission Attributes.
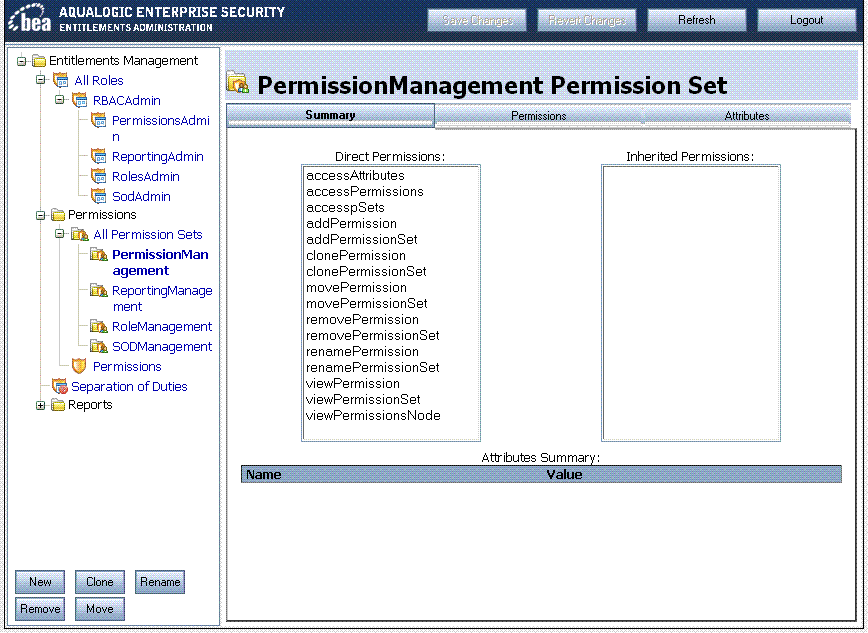
To create a new permission set:
By default, the Entitlements Management Tool has no permission sets defined, and the only level of the permission set hierarchy is the All Permission Sets node. After you create one or more permission sets, you can modify the permission set hierarchy in a number of ways:
You can assign attributes to permissions and permission sets. An attribute is a name/value pair that will be available to the ALES authorization system at run time. Assigning an attribute enables the creation of authorization policies based on the attribute value.
To assign an attribute to a permission or permission set:
Separation of duties constraints are used to prevent conflicts of interest in a role based system. Without separation of duties constraints, the hierarchical role model can give users permissions associated with conflicting roles. For example, suppose you have a trading system with Trader and TradeAuditor roles, both reporting to a VP. Without a separation of duties constraint, users with the VP role would inherit both the Trader and TradeAuditor entitlements. To ensure that the same user could not be the originator of a trade and the approver of the same trade, you can create a separation of duties constraint to that specifies that users with the TradeAuditor role cannot also have the Trader role.
Separation of duties places constraints on the assignment of users to roles so that membership in one role can preclude membership in another. The Separation of Duties node in the Entitlements Management Tool enables you to select a defined role (which we will refer to as "the constrained role") and then specify which other roles are denied to subjects who have the constrained role.
To create a new separation of duty constraint:
The Modify Separation of Duty page displays.
The Find Conflict button allows you to find any conflicting role assignment policies in the system based on the separation of duties defined. If any conflicting roles exist, you need to modify your role assignments to eliminate the conflicts.
The Reports node of the Entitlement Management Tool enables you to generate reports about subjects, roles, permissions, and permission sets in your security realm. The following reports are available:
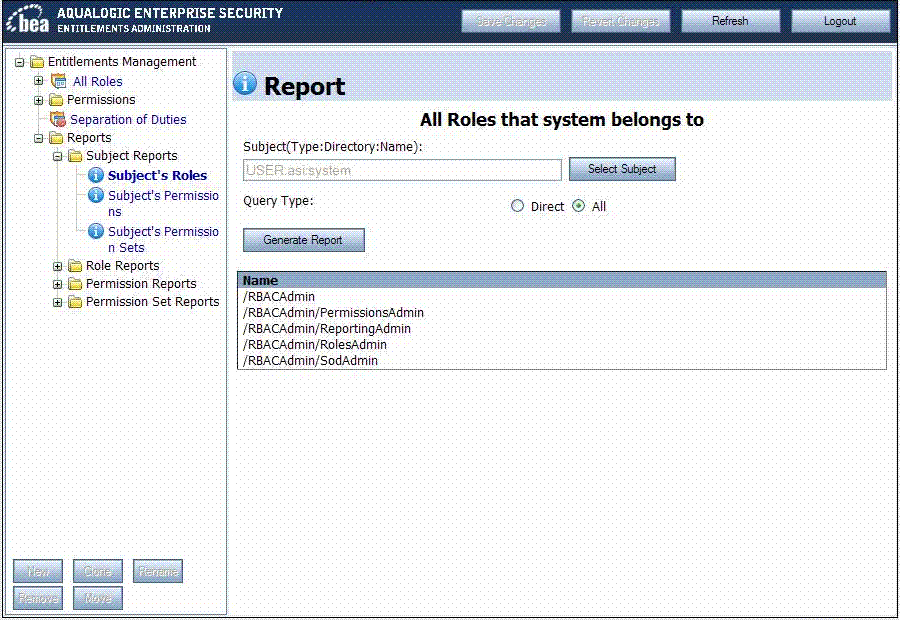
To generate a Subject's Roles report:
The Report page appears in the right panel.
The Reports page lists all the roles your selected Subject has.
Generating any of the other reports is essentially the same.


|