The Agent Development Kit simplifies this work by providing automated code generation and additional features that allow you to build an agent quickly and reliably.
You do not need to understand the SNMP or SMUX protocol in depth to build an SNMP agent with this Agent Development Kit. We do recommend that you read the RFC documents listed below.
A necessary step in building an agent or subagent is defining the manageable features of the resource in an SNMP-compliant MIB. To do this, you should have some knowledge of Abstract Syntax Notation One (ASN.1), as defined in the International Organization for Standardization (ISO) standards. This product also presupposes that the user is familiar with the C programming language.
The Agent Development Kit is compliant with the following Internet standards:
RFC 1155 - Structure of Management Information
RFC 1157 - Simple Network Management Protocol
RFC 1212 - Concise MIB Definitions
RFC 1213 - Management Information Base (MIB II)
RFC 1227 - SNMP Multiplex (SMUX)
Information on obtaining these RFC documents can be found in the "SNMP Information" appendix in the Agent Integrator Reference Manual.
The Manager/Agent Model
The Agent Development Kit software is based on the manager/agent model described in the ISO network management standards. In this model, a network manager exchanges monitoring and control information about network and system resources with distributed software processes called agents.
Any system or network resource that is manageable through this exchange of information is a managed resource. This could be a software resource, such as a message queue or TUXEDO application, or a hardware resource such as a router or NFS file server.
Agents function as "collection devices" that typically gather and send data about the managed resource in response to a request from a manager. In addition, agents often have the ability to issue unsolicited reports to managers when they detect, or "trap," certain predefined thresholds or events on a managed resource. In SNMP terminology, these unsolicited event reports are called trap notifications.
A manager relies upon a database of definitions and information about the properties of managed resources and the services the agents support - this comprises the management information base (MIB). When new agents are added to extend the management domain of a manager, the manager must be provided with a new MIB component that defines the manageable features of the resources managed through that agent. The manageable features of resources, as defined in an SNMP-compliant MIB, are called managed objects. When the heterogeneous components of an enterprise's distributed systems are defined within a common MIB on the management station, this provides a unified perspective and single access point for managing systems made up of diverse hardware and software components from numerous vendors.
In order to provide manageability of a resource, an agent must have access to instrumentation in the managed resource. This consists of some means of obtaining current values of the manageable features of that resource, or a means of modifying those values. This might consist of operating system calls, or an application's application programming interface (API) that provides status and performance information about that application.
Master Agents and Subagents
In the SNMP architecture, each managed object can be managed through only one SNMP agent, and each host may have only one agent communicating with an SNMP manager. The original SNMP management solution allowed for only a single monolithic agent to carry out all management responsibilities on a given network node (IP address). This solution was soon discovered to be too inflexible to provide for effective management of increasingly complex systems. In addition to the agents typically provided by computer manufacturers for hardware and operating system information, agents are also being produced by vendors of other products, such as agents for SQL database systems. Complex and heterogeneous systems thus require the ability to accommodate multiple agents on a single network node.
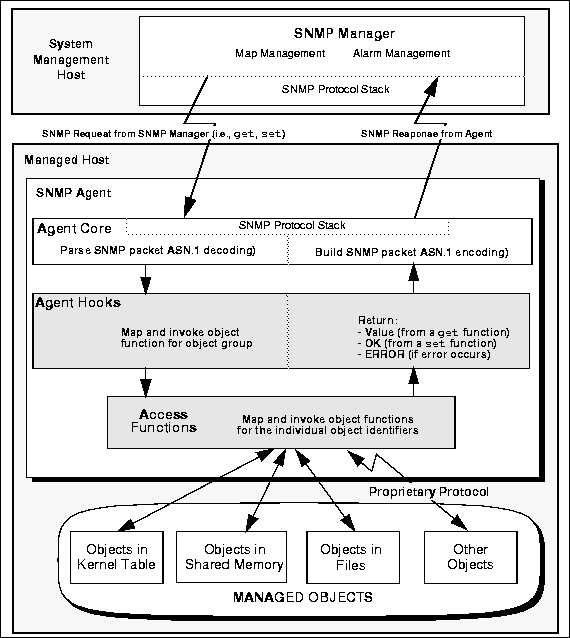
The SNMP architecture was thus extended to allow a single master agent to communicate with subagents, allowing multiple agents to cooperate in managing diverse hardware and software components on a single host. This master agent functionality is provided by the BEA Manager Agent Integrator software. The extended SNMP Manager/Agent model is illustrated in Figure 2-1.
One of the most popular protocols used for communication between an SNMP master agent and subagents is the SNMP Multiplex (SMUX) protocol, defined in RFC 1227.
However, no standardized solution has emerged for coordination of multiple non-SMUX SNMP agents on a single host. Master agents that "speak" SMUX protocol to subagents are typically able to communicate only with SMUX-compliant subagents, and cannot communicate with non-SMUX SNMP agents running on the same host.
The BEA Agent Integrator is an intelligent master agent that provides a comprehensive solution for orchestration of diverse agents and subagents.
The Agent Integrator is a master agent that can run on the same node with monolithic SNMP agents and SMUX subagents, allowing multiple agents and subagents from any vendor to cooperate in the management of system components. The multiple SNMP agents and SMUX subagents communicate with SNMP managers through the Integrator and appear as a single SNMP agent to any SNMP manager.
In its communication with SMUX subagents (and non-SMUX SNMP agents running on the same host), the master agent acts as a proxy for the manager. The master agent distributes requests from the manager to specific SNMP agents or subagents, and receives the responses from the individual agents and forwards those responses back to the manager (as illustrated in Figure 2-1).
Figure 2-1 SNMP Architecture

Refer to the Agent Integrator Reference Manual for more information on the Agent Integrator.
The Agent Development Kit is a software development kit for the creation of SMUX subagents or SNMP agents for management of system resources, as defined in private MIBs. Subagents created using the Agent Development Kit are also capable of running as a stand-alone SNMP agent. The Agent Development Kit is fully compliant with RFC 1212, Concise MIB Definitions.
Managed Objects and Object Identifiers
The manager sees the data it manages as a collection of managed objects, represented in ASN.1 notation. The ASN.1 notation defines the data that the manager and the agent exchange. ASN.1 is a formal language described in the ISO 8824 and 8825 standards.
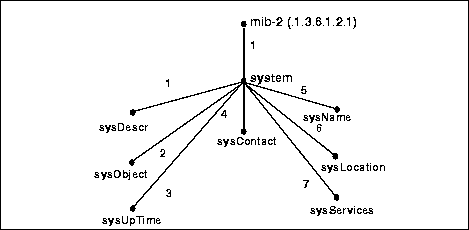
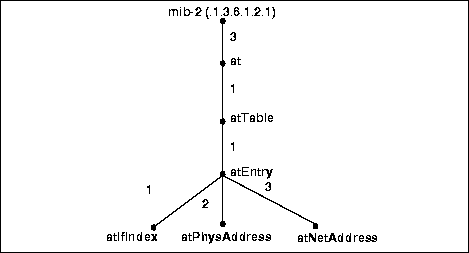
The managed objects comprise the management information base (MIB). Each object in the MIB has an object identifier (OID), which the manager uses to request its value from the agent. The OID is a sequence of integers that uniquely identify a managed object by defining a path to that object through a tree-like structure, which is often called the OID tree or registration tree. When an SNMP agent wishes to access a specific object, it traverses the OID tree to find the object.
The following diagram illustrates the OID tree for the BEA private MIB. Each BEA private MIB object that the SNMP agent software manages has a unique object identifier, using a prefix of .1.3.6.1.4.1.140 to identify it as an object in the BEA private MIB. This number sequence defines the path to this branch of the OID tree, represented by dashed lines in Figure 2-2.
Figure 2-2 Object Identification Scheme
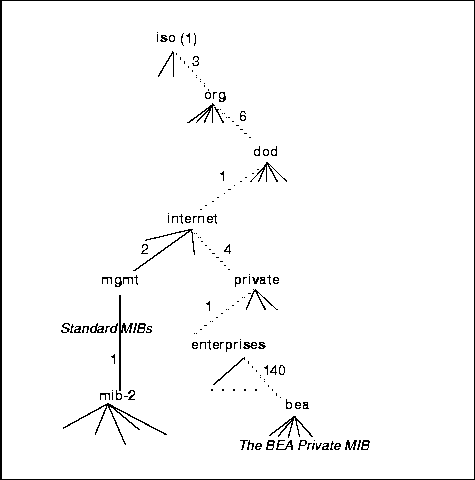
All standard MIBs reside under mgmt (.1.3.6.1.2) in this diagram - for example, MIB II (.1.3.6.1.2.1). The distinction between the standard and private MIBs is that of control over the object definitions. Standard MIBs are those that have been approved by the Internet Activities Board (IAB). MIBs defined unilaterally by equipment and software vendors are initially defined as private MIBs under private.enterprises. A branch within the private.enterprises subtree is allocated to each vendor that registers for an enterprises object identifier. For a complete listing of objects in the BEA private MIB in ASN.1 notation, read the file bea.asn1 in the Agent Development Kit distribution.
MIB Groups
A MIB group is a collection of managed objects, and is itself represented by the name or OID of a node in the OID tree. Groups may contain other groups. For example, bea is a MIB group that is a member of the private.enterprises MIB group.
The nodes in the OID tree that are not groups - the base level of the OID tree - are the "leaves" of the OID tree. For example, in the following diagram: