Run-time Administration
Domains integrates with an existing BEA TUXEDO application by adding entries for domain gateways groups and gateway servers in the TUXCONFIG file. The existing tmconfig(1) and tmadmin(1) commands can be used to add this new configuration dynamically to a running BEA TUXEDO application. The tmadmin command can also be used to list the information contained in the Bulletin Board for Domains gateway groups and their gateways.
In addition to tmadmin(1), a new administrative command, dmadmin(1), is provided. This command provides administrators with the run-time administration capabilities to maintain the Domains configuration and active gateway groups. Figure 3-1 shows the relationship between administrative commands and servers.
Figure 3-1 Domains Run-Time Administration
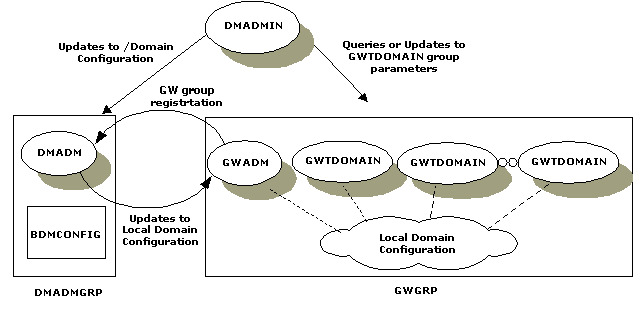
Figure 3-1 shows the components of the Domains administrative subsystem: the dmadmin(1) command, the Domains administrative server, DMADM(5), the gateway group administrative server, GWADM(5), the gateway process, GWTDOMAIN(5), and the Domains configuration file, BDMCONFIG. The dmadmin command can be used by the administrator to update the BDMCONFIG file while the BEA TUXEDO application is running. The command acts as a front-end process that translates administrative commands to service requests to the DMADMIN service, which is a generic administrative service advertised by the DMADM server. The DMADMIN service invokes the validation, retrieval, or update functions provided within the DMADM server to maintain the BDMCONFIG file. The DMADM server also provides a registration service to gateway groups. This registration service is requested by GWADM servers as part of their initialization procedure. The registration service downloads the configuration information required by the requesting gateway group. The DMADM server maintains the list of registered gateway groups, and propagates to these groups any changes made to the configuration.
Note:
The gateway process, GWTDOMAIN(5), which provides connectivity to remote gateway processes, focuses on throughout of messages between BEA TUXEDO domains. This process is not get involved in Domains administration.
Figure 3-1 also shows some of the functionality provided by the GWADM server. This server registers with the DMADM server to obtain the configuration information used by the corresponding gateway group. The GWADM accepts queries from dmadmin to obtain run-time statistics or to change the run-time options of the corresponding gateway group. Periodically, the GWADM server sends an "I-am-alive" message to the DMADM server. If no reply is received from the DMADM server, the GWADM server registers again. This mechanism makes sure the GWADM server always has the latest copy of the Domains configuration for its group.
Another run-time feature is the capability to specify gateway parameters when a gateway group is booted. This capability requires the use of the CLOPT parameter when the GWADM server is defined in the *SERVERS section of the TUXCONFIG file.
The main capabilities of the run-time administration feature are as follows: