The syntax of the command line is as follows:
audit {-a|-t} [bid]audit is the name of the executable created when the audit.c program is compiled. The -a option requests that account balances be retrieved; the -t option specifies the teller balance. If no branch identifier, bid, is included on the command line, the default is to retrieve the total account or teller balance for all the branches of the bank. If the branch identifier is included, a balance of the type specified is retrieved for that branch only.
Preliminaries
Before a client program is ready to join the application, some preliminary processing may be called for to take advantage of BEA TUXEDO system capabilities.
Client Naming
An application can associate both a usrname and a cltname with an execution of a client process. Values furnished for these names are combined by the BEA TUXEDO system with the logical machine identifier (LMID) of the machine where the process runs, in order to establish a unique identification for the process. It is left to the discretion of application developers and programmers to work out ways of acquiring the value for the fields. Once acquired they are passed to tpinit() in a TPINIT buffer. Some possible ways are shown in later examples.
Note:
If the process is running outside the administrative domain of the application, that is, if it is running on a workstation connected to the administrative domain, the LMID used is the one for the machine used by the workstation client to access the application.
Once a client process is uniquely identified, client authentication can be implemented, out-of-band messages can be sent to a specific client or to groups of clients via tpnotify(3c) and tpbroadcast(3c), and detailed statistical information can be gathered via tmadmin(1).
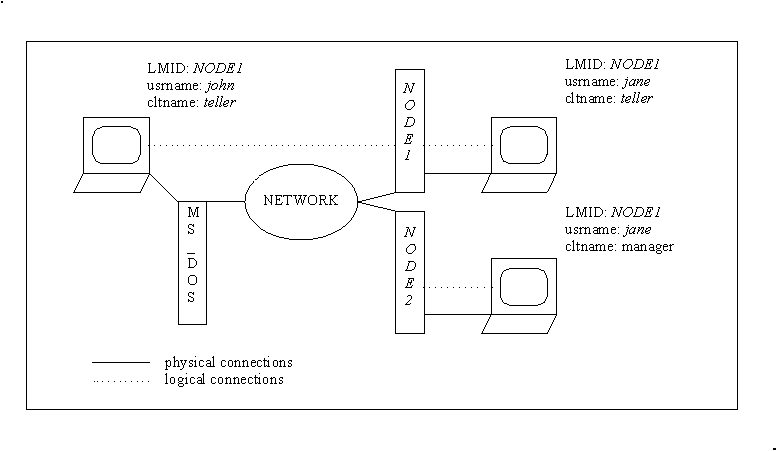
Figure 2-1 shows an example of how names might be associated with clients accessing an application. In the example, the application uses the cltname field to indicate a job function.
Figure 2-1 Client Naming
Unsolicited Notification
Unsolicited notification refers to any communication with a client that is not an expected response to a service request (or an error code). The example that comes to mind is a broadcast message to announce that the world is coming to an end in five minutes. Within the client program there are three things you may want to do to handle such messages: